Contents
SAML SSO for JSM Customers with Multiple IDP’s
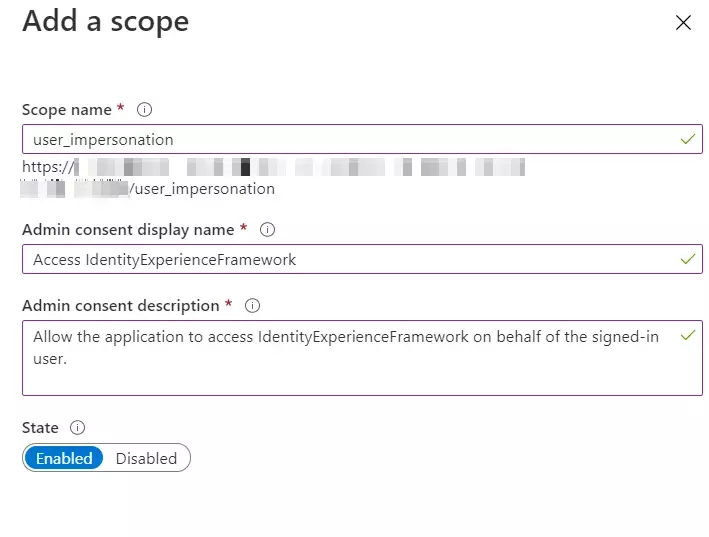
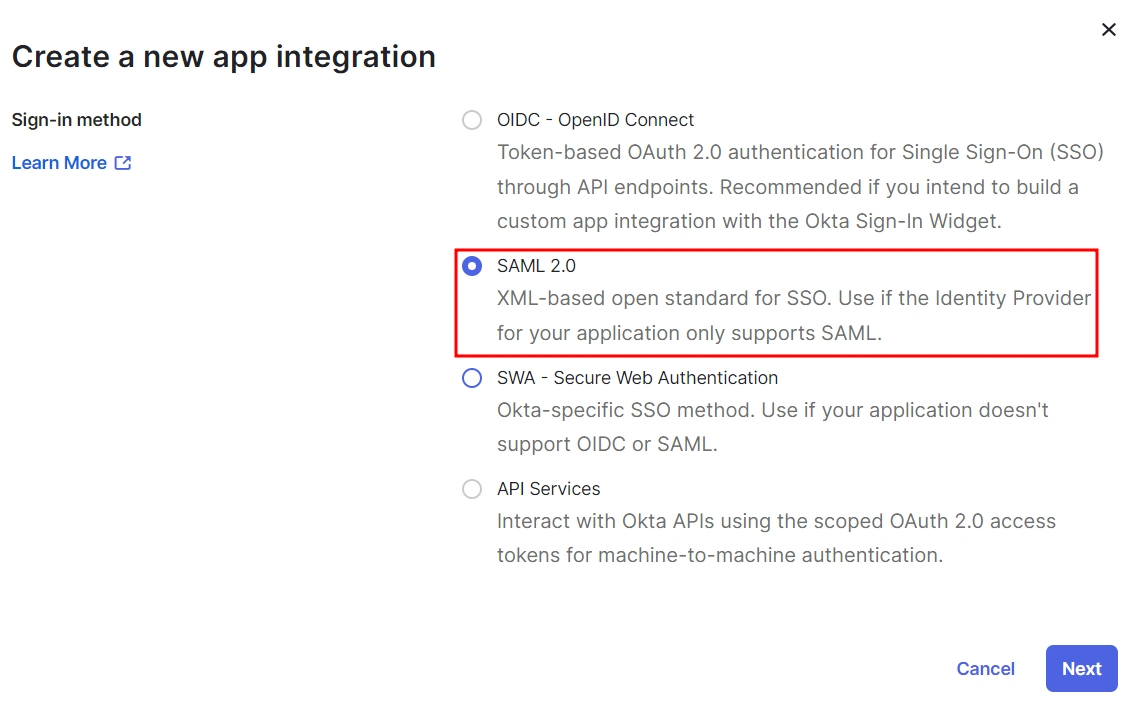
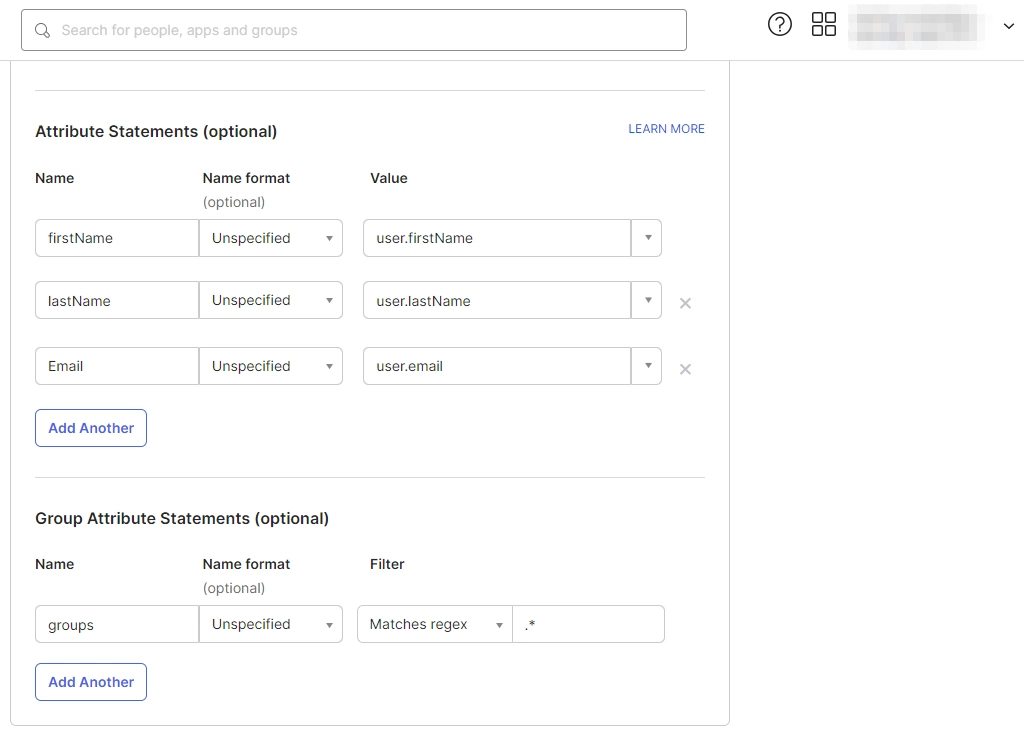
Choose IDPs for Helpdesk integration
You can select a maximum of 3 IDPs
If you are looking for instructions on configuring Helpdesk SSO with a single IDP, please refer
to this
page instead.
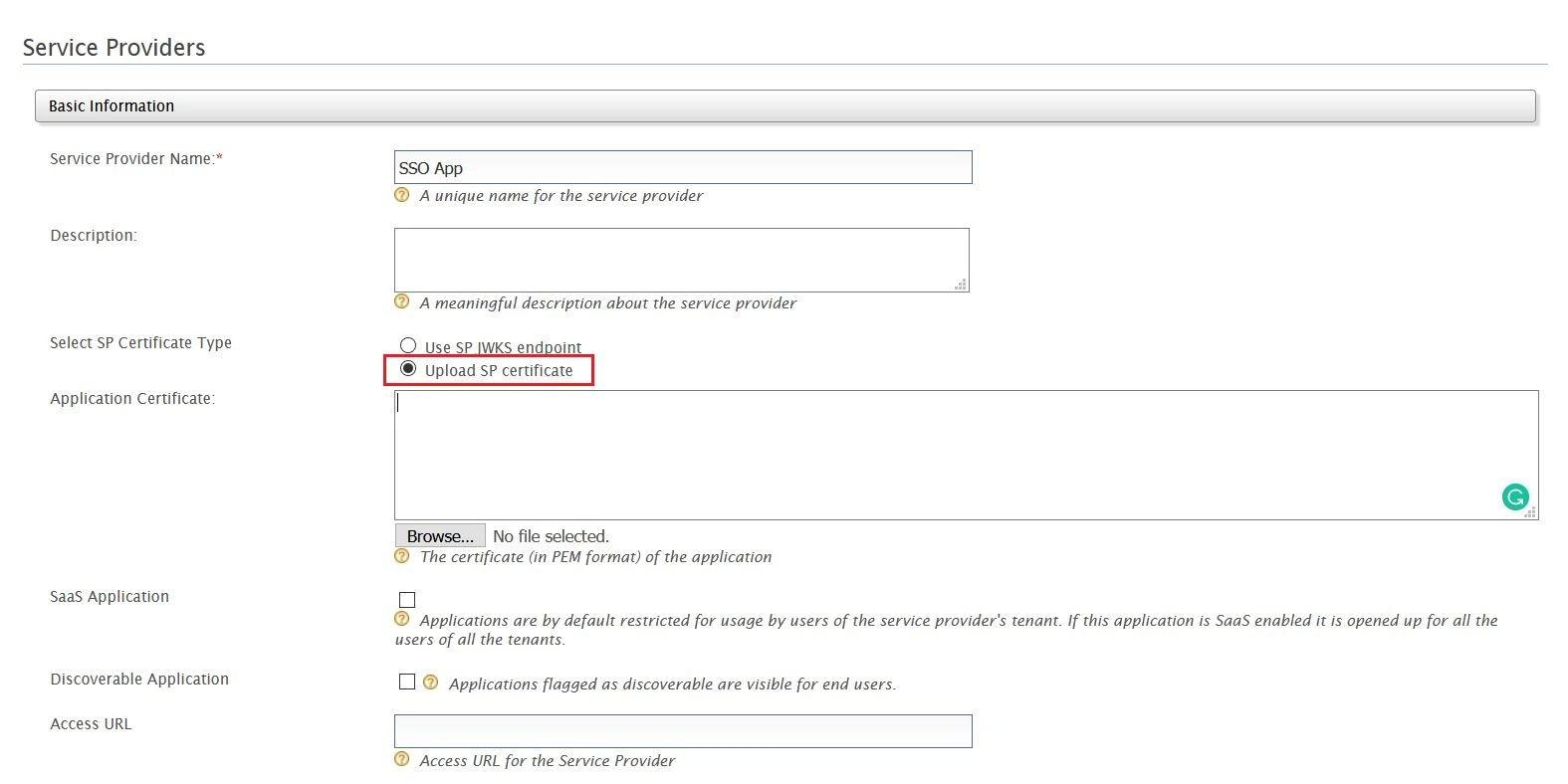
You can now allow External Customers to login into Jira Service Management (previously Jira Service Desk or JSD) via SSO! SAML SSO for JSM Customers allows you to use your existing IDP to sign into Jira Service Management (Jira Service Desk or JSD) and it also supports multiple IDP's.
This guide will walk you through the process of configuring Jira Helpdesk with multiple identity providers. However, if you are looking for instructions on configuring Helpdesk SSO with a single IDP, please refer to this page instead.
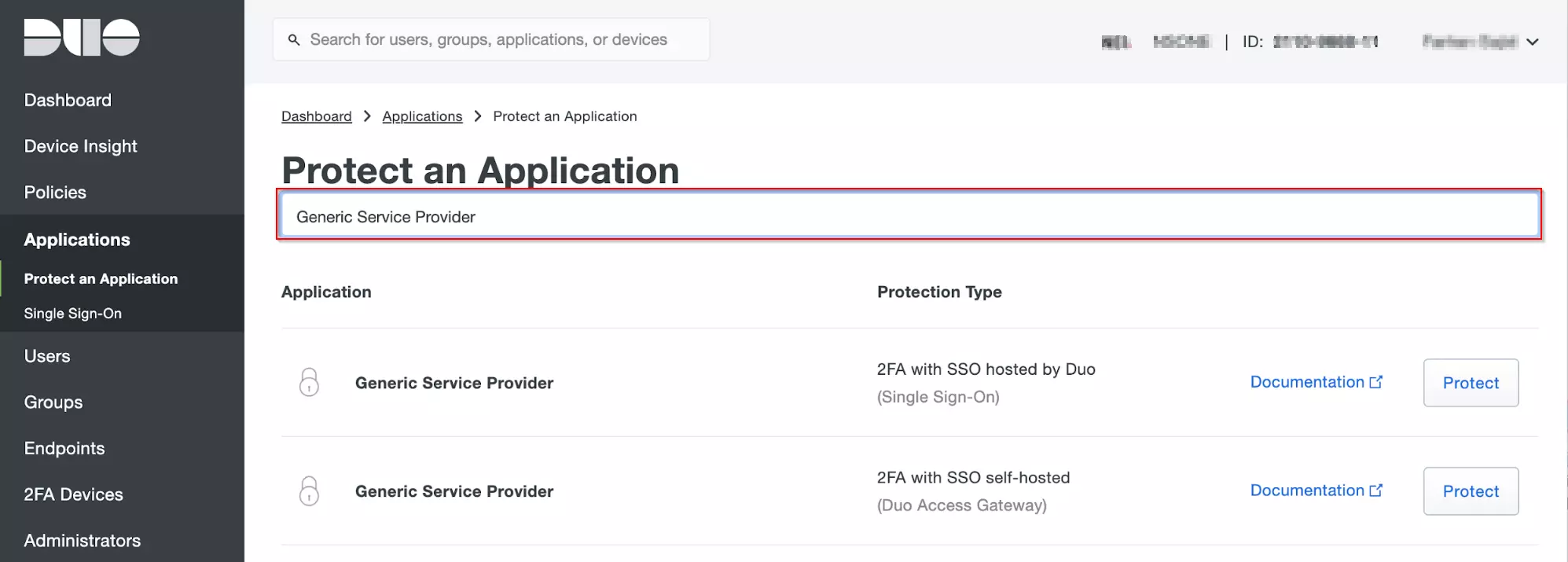
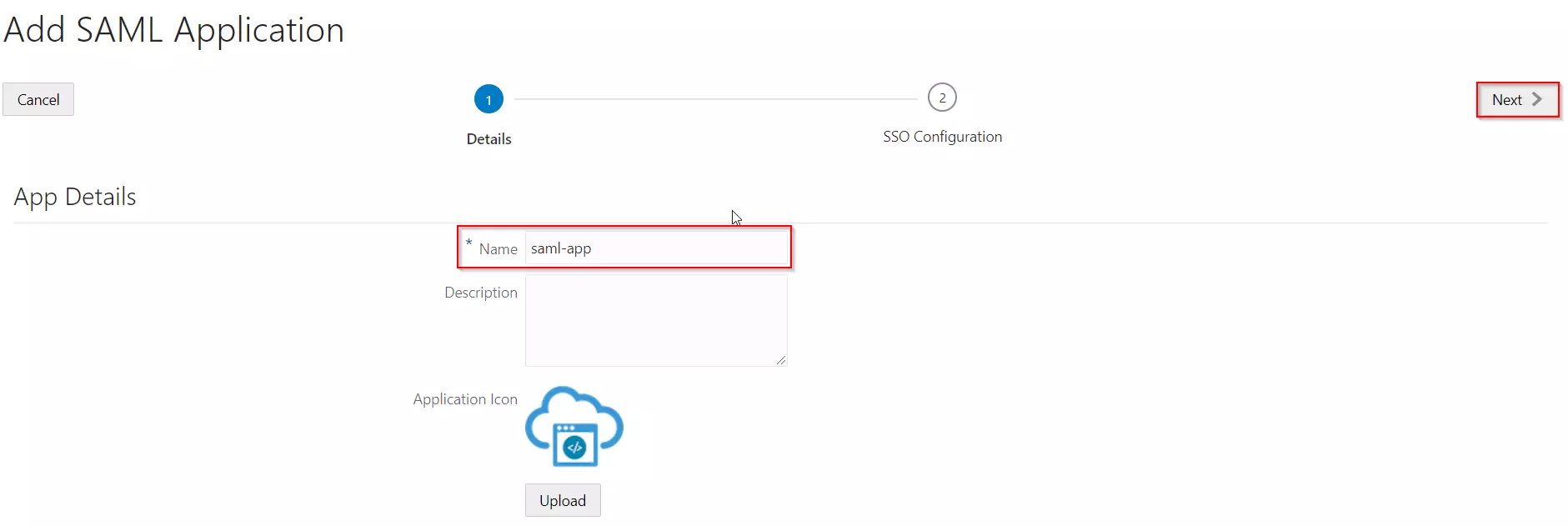
Download And Installation
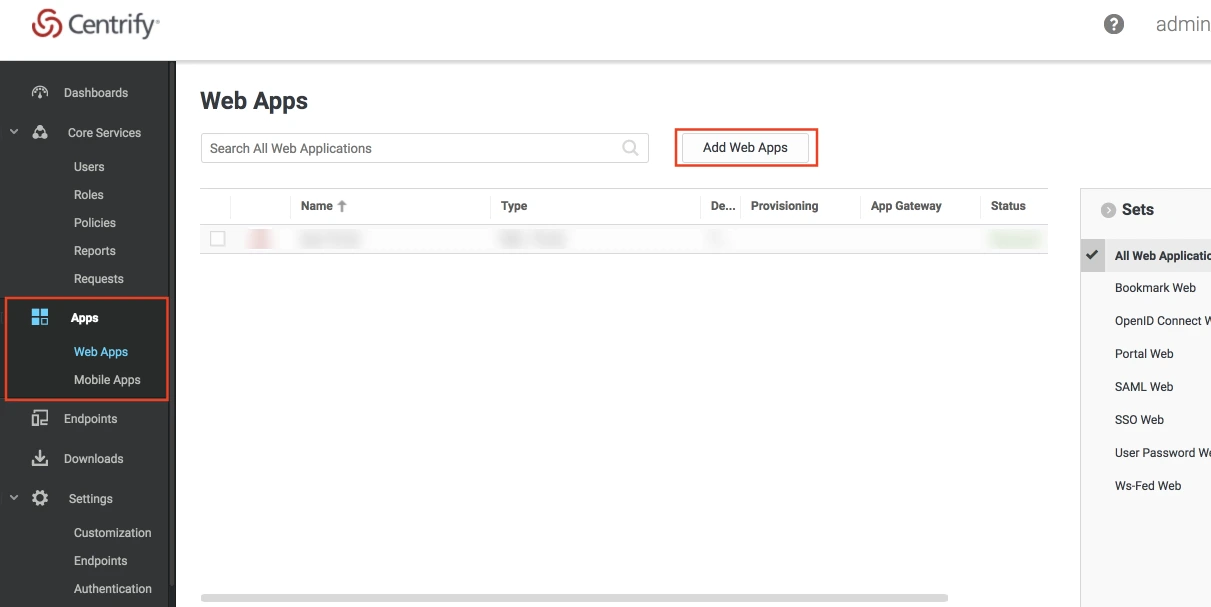
- Log into your Jira instance as an admin.
- Navigate to the settings and Click on Apps.
- Locate SAML SSO for JSM Customers.
- Click on free trial to begin a new trial SAML SSO for JSM Customers.
- On menu bar click on Apps. Locate SAML SSO for JSM Customers to start configuring SSO for customers.
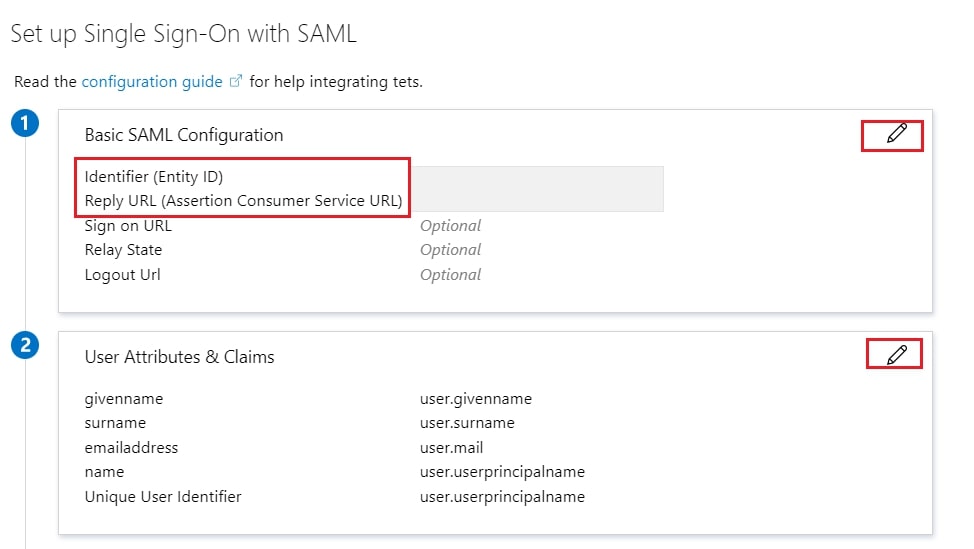
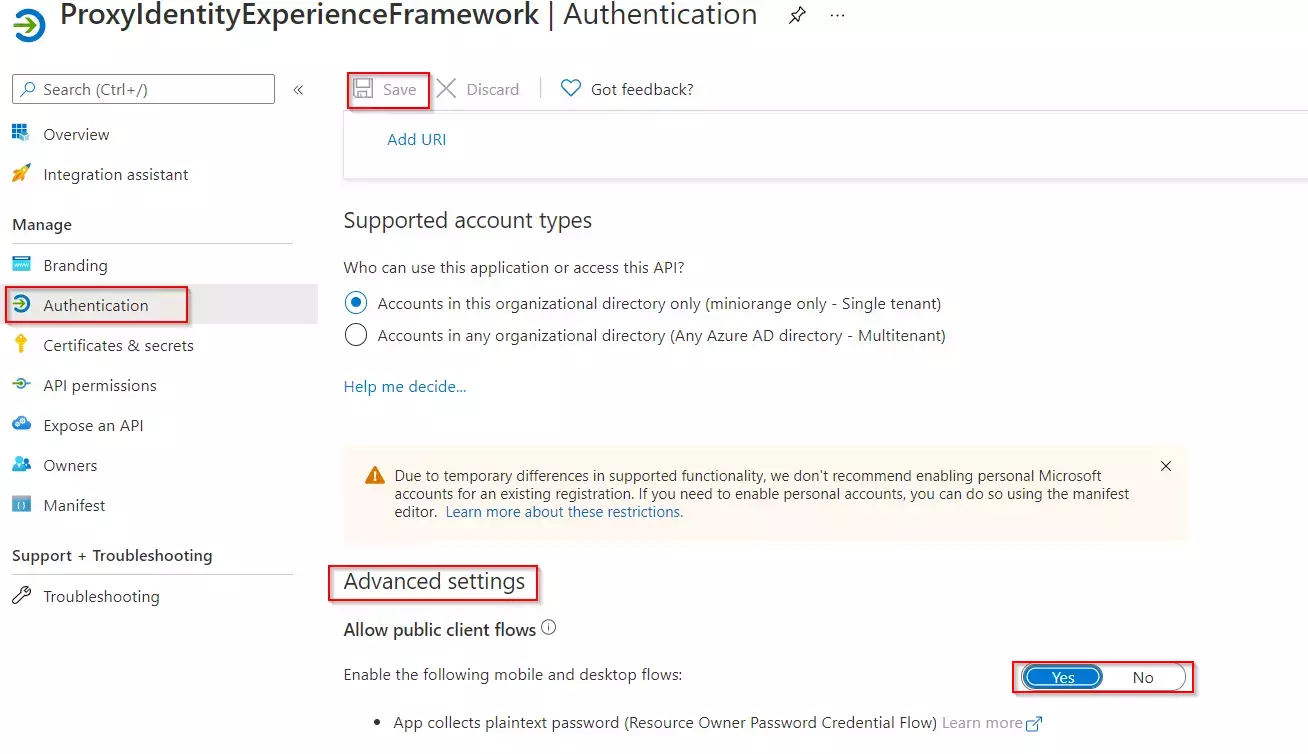
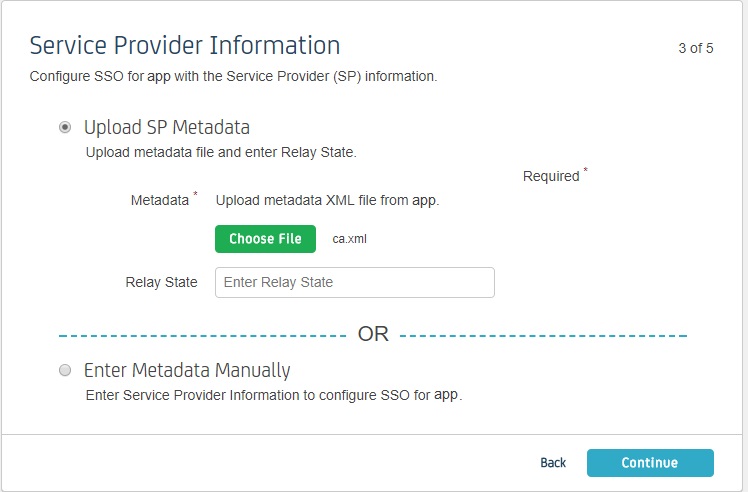
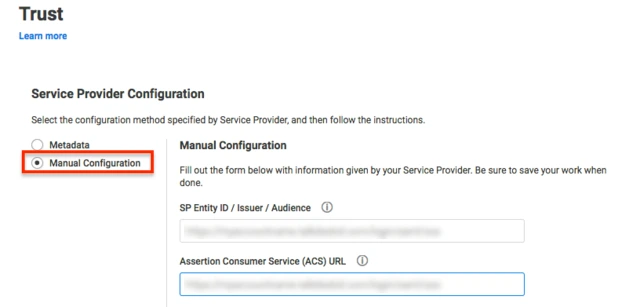
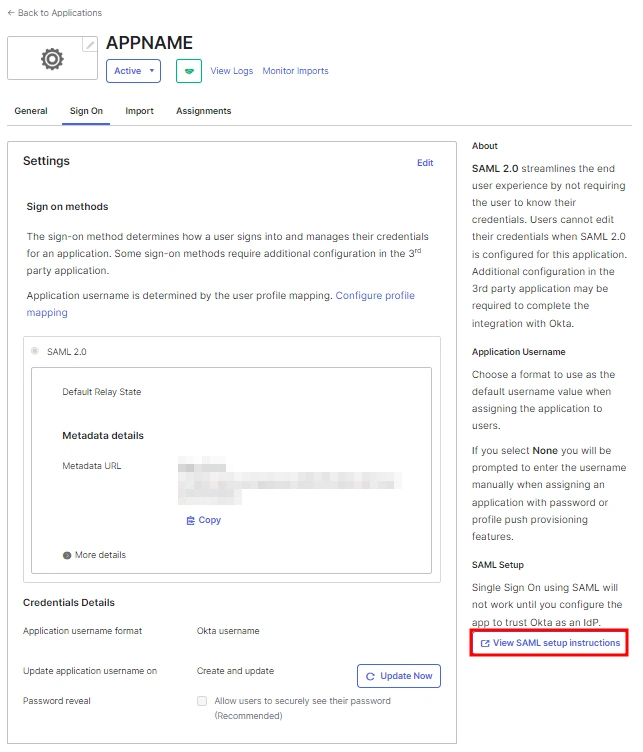
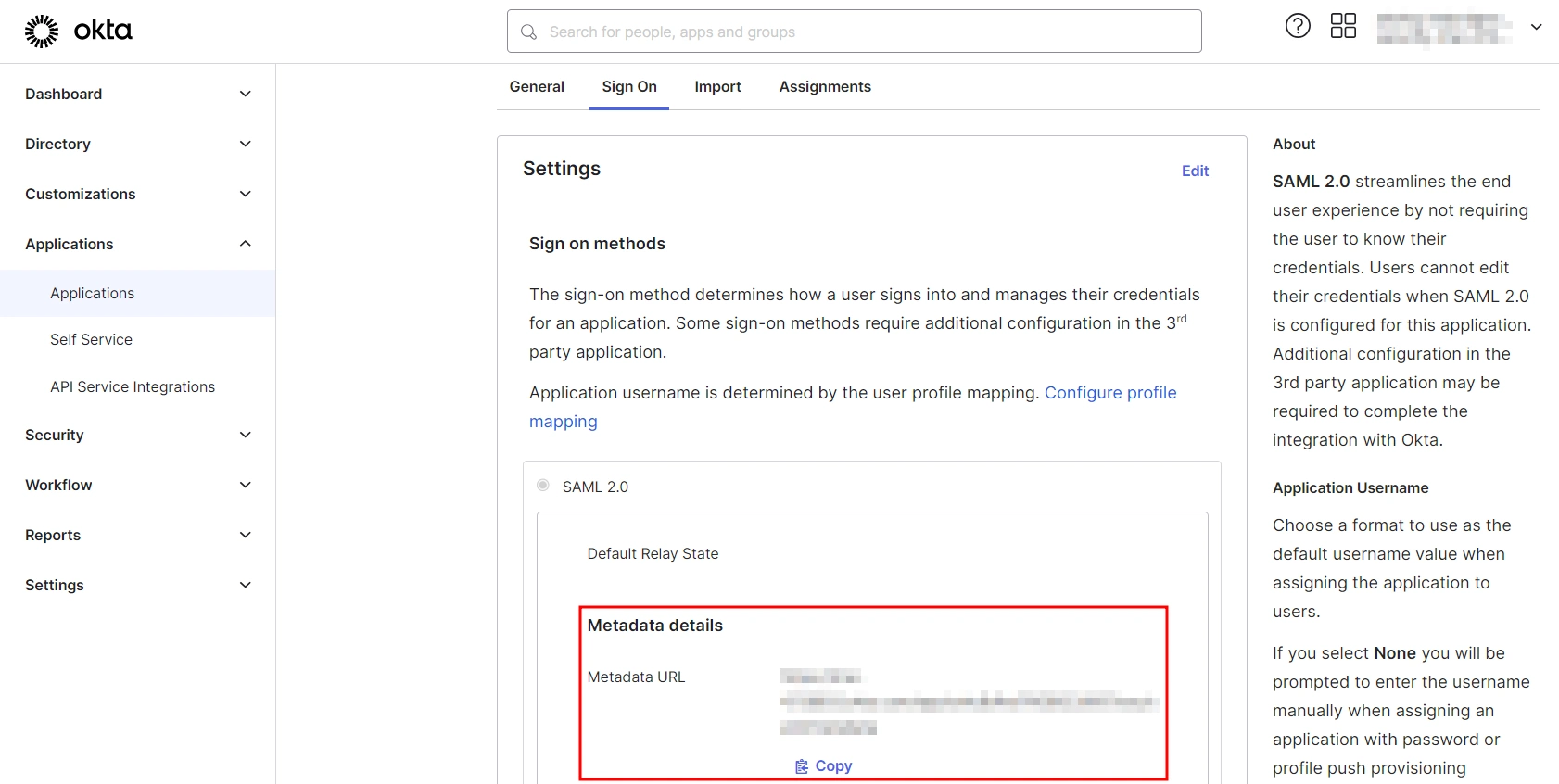
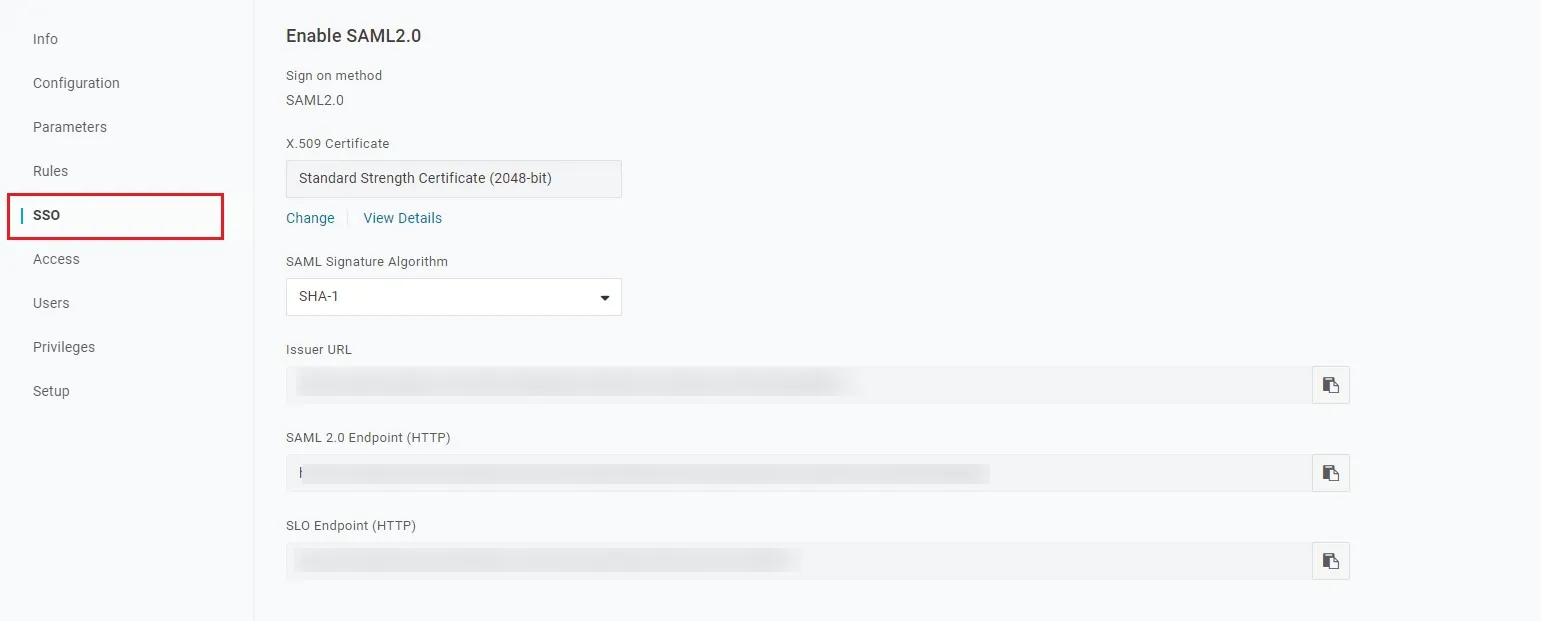
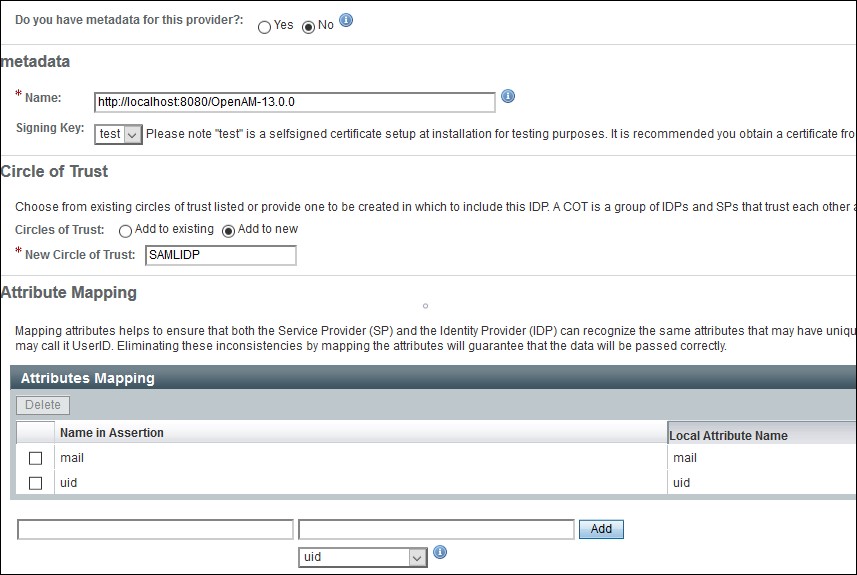
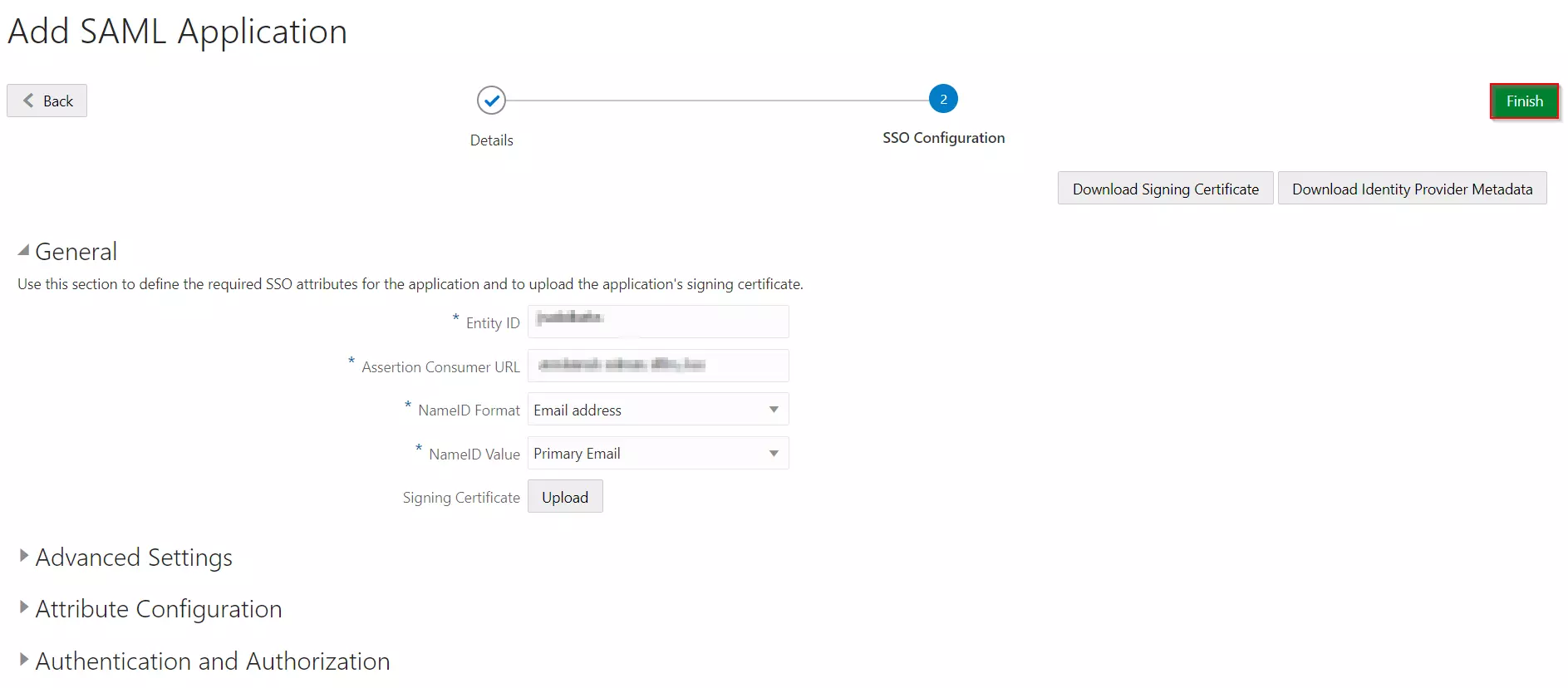
Step 1: Get metadata from miniOrange
- Login to miniOrange Admin Dashboard
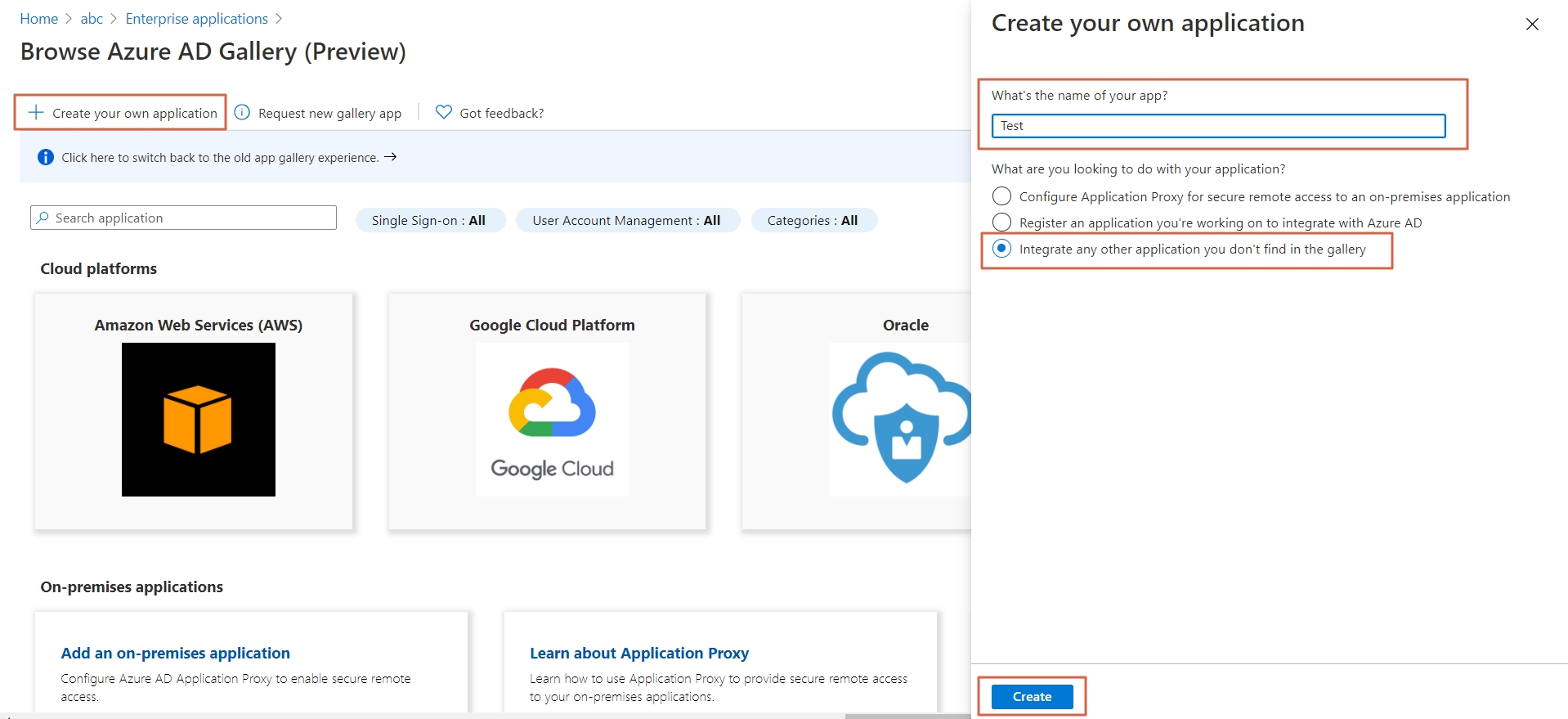
- Go to Identity Providers and click on Add Identity Provider button from top right corner.
- Click on Click here link from the alert box.
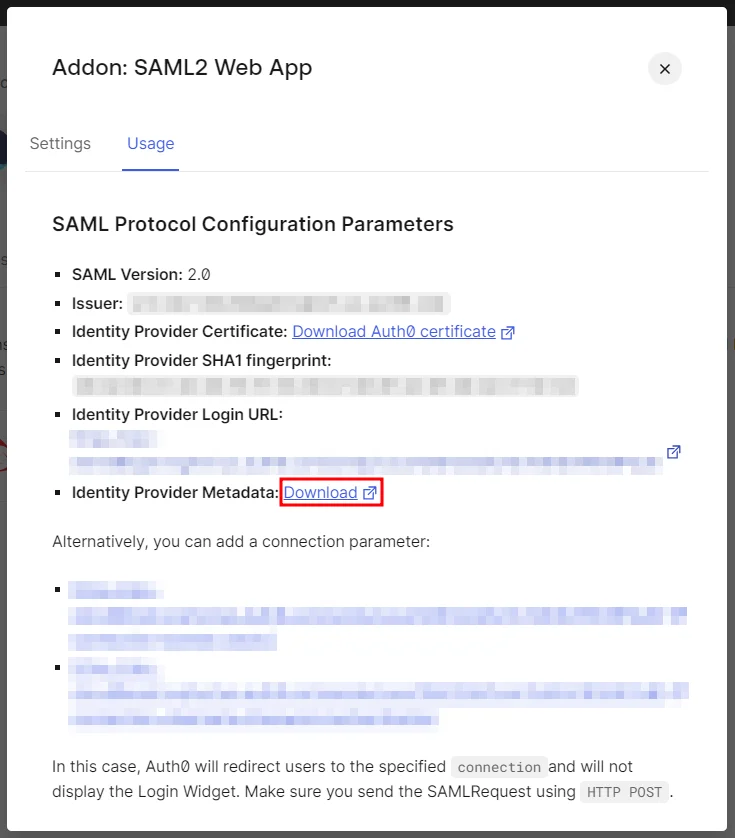
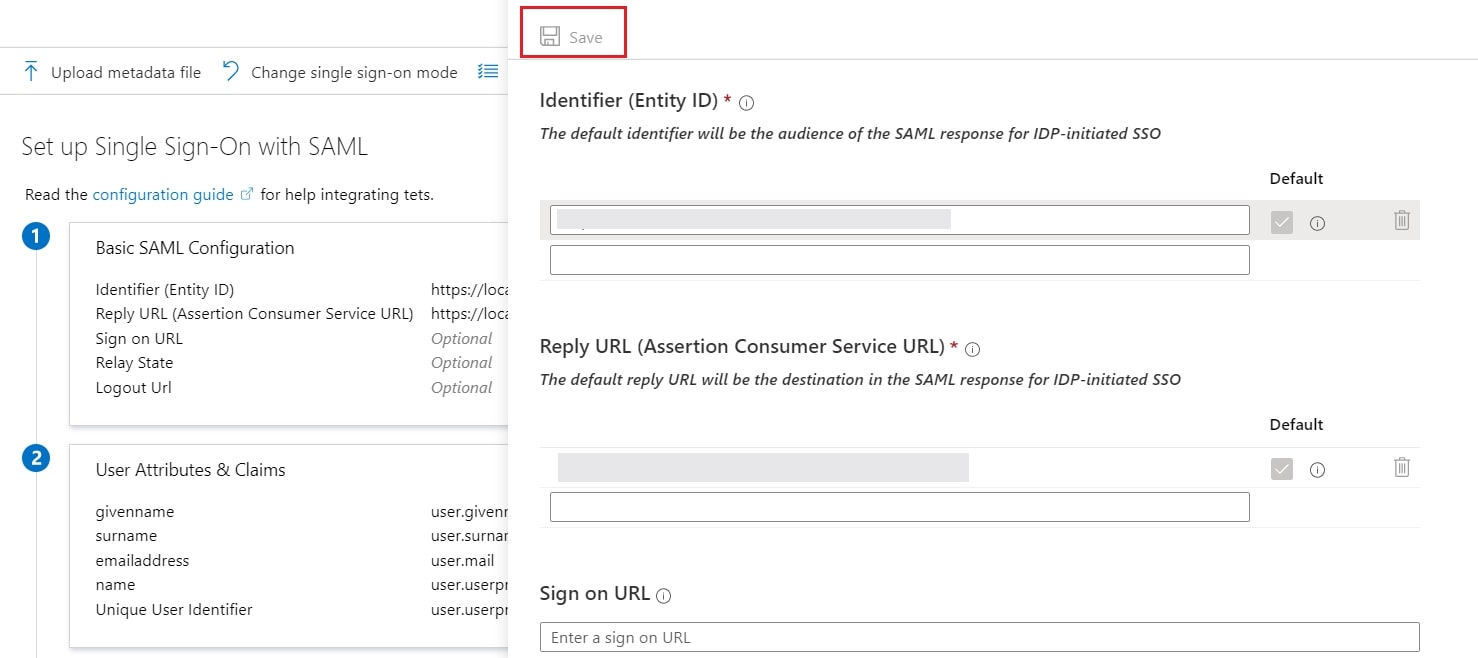
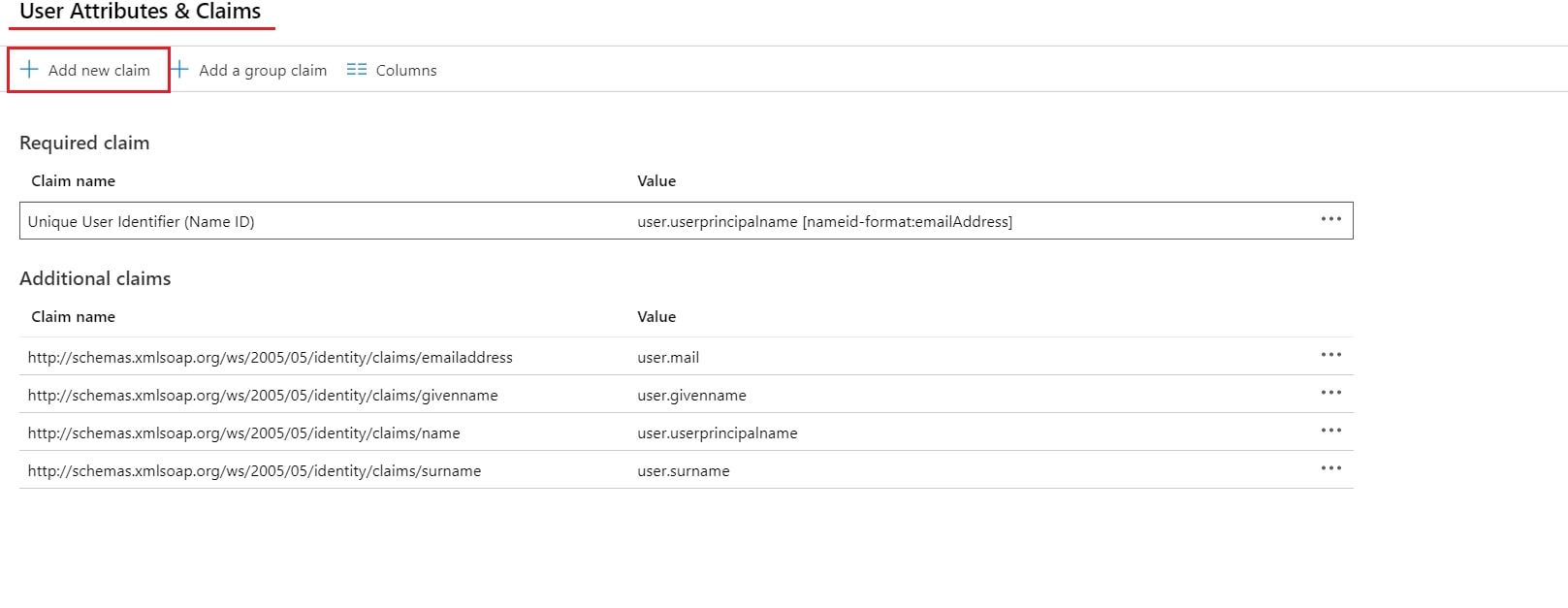
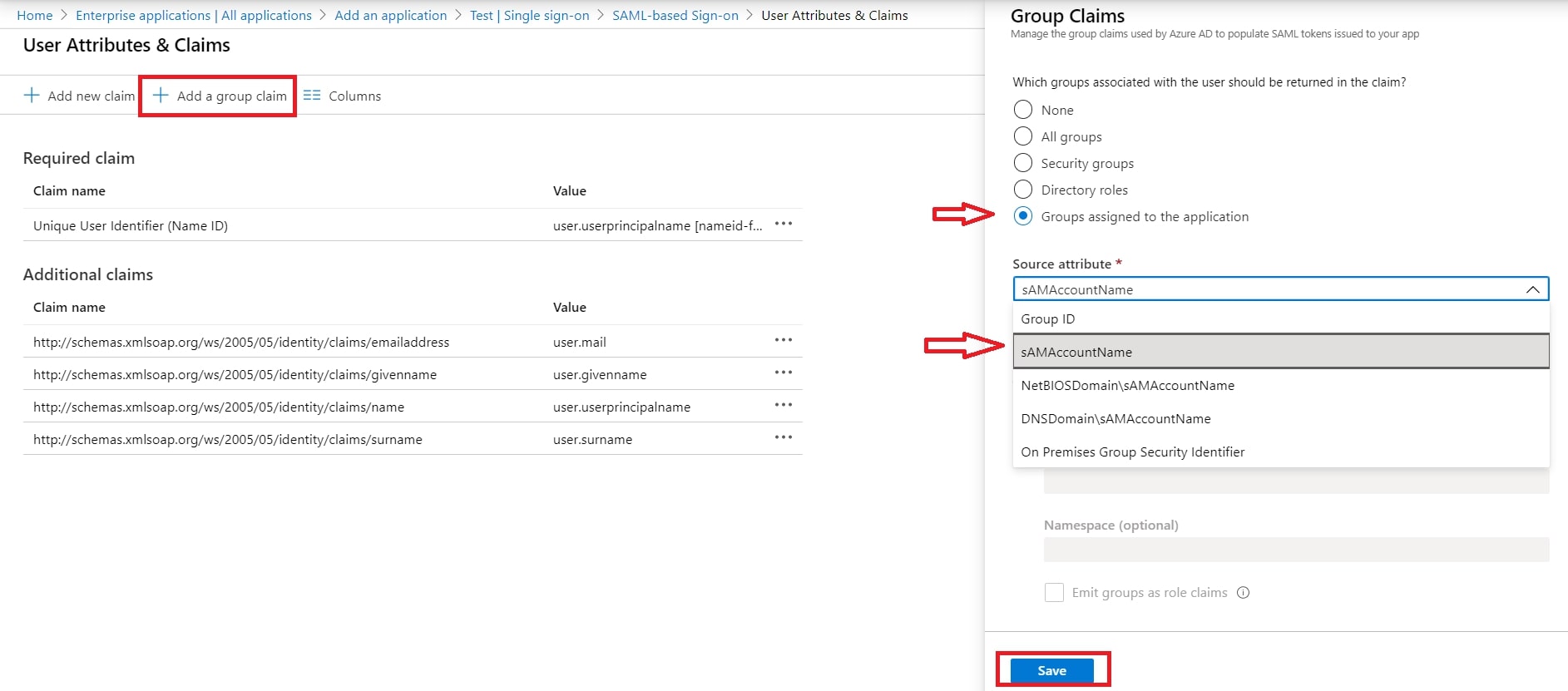
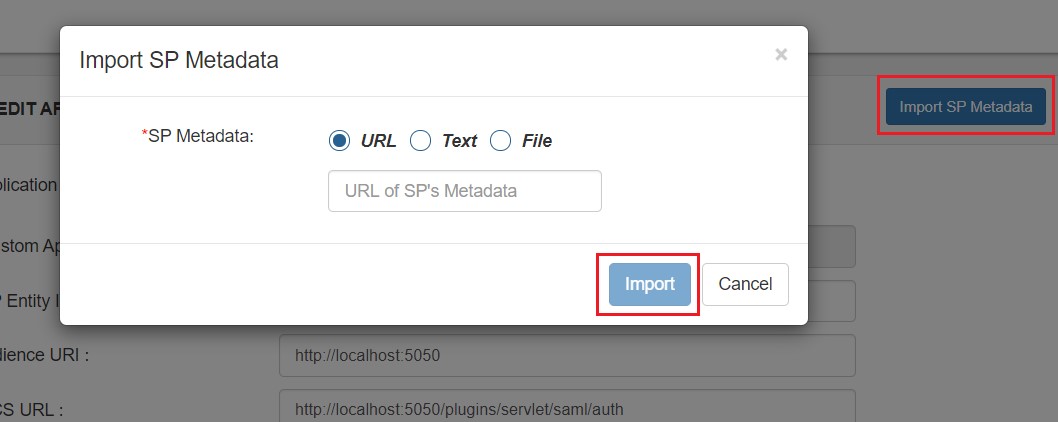
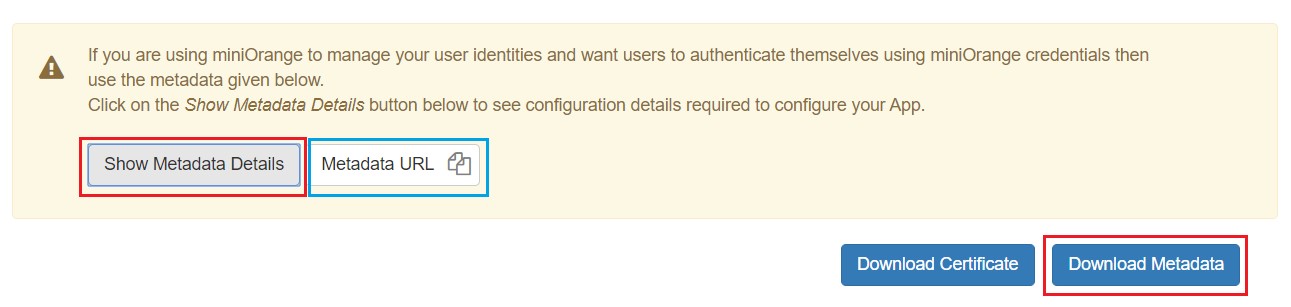
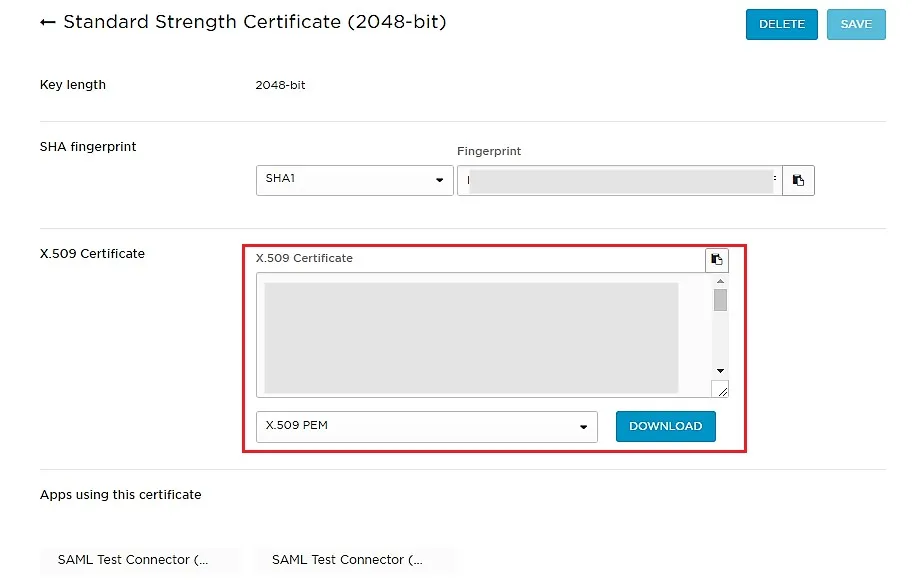
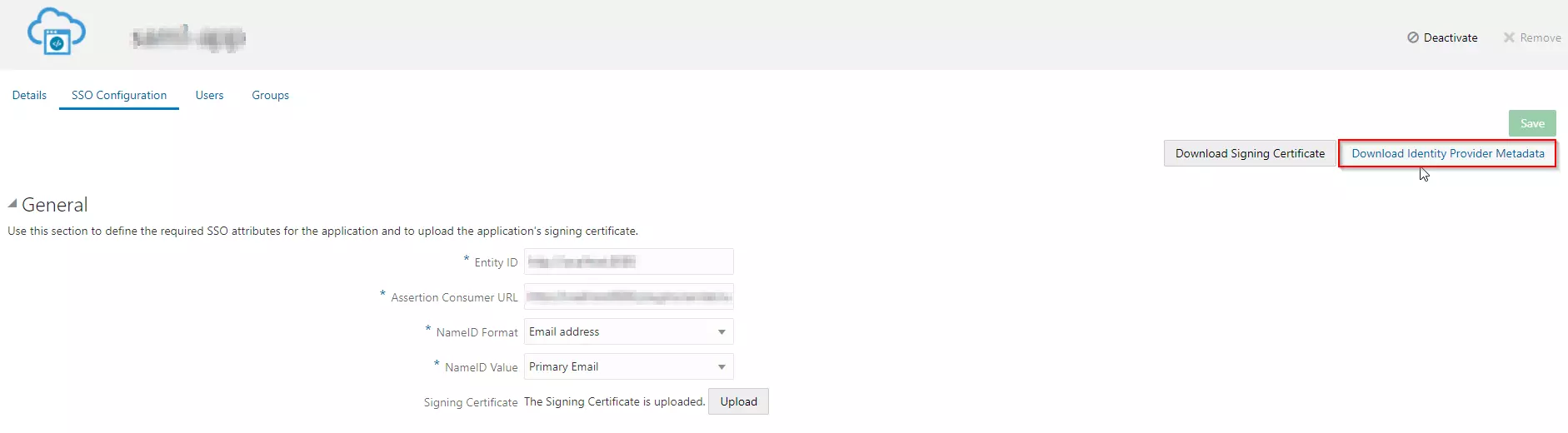
- Now, click on Show Metadata Details under FOR SP - INITIATED SSO heading. You can use the following metadata details to add an app inside your IDP.



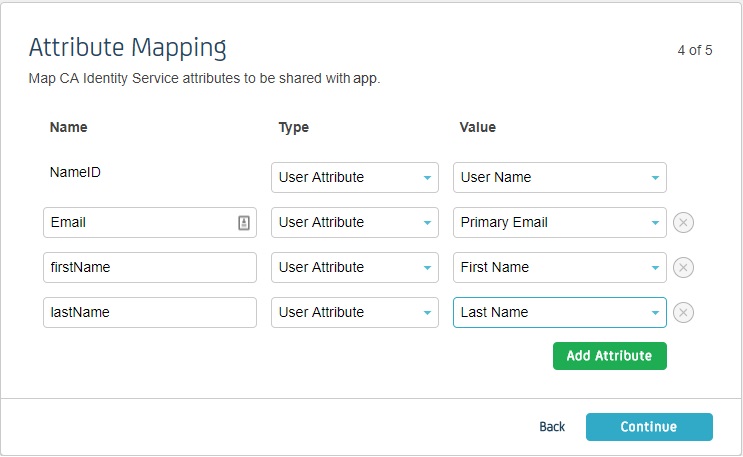
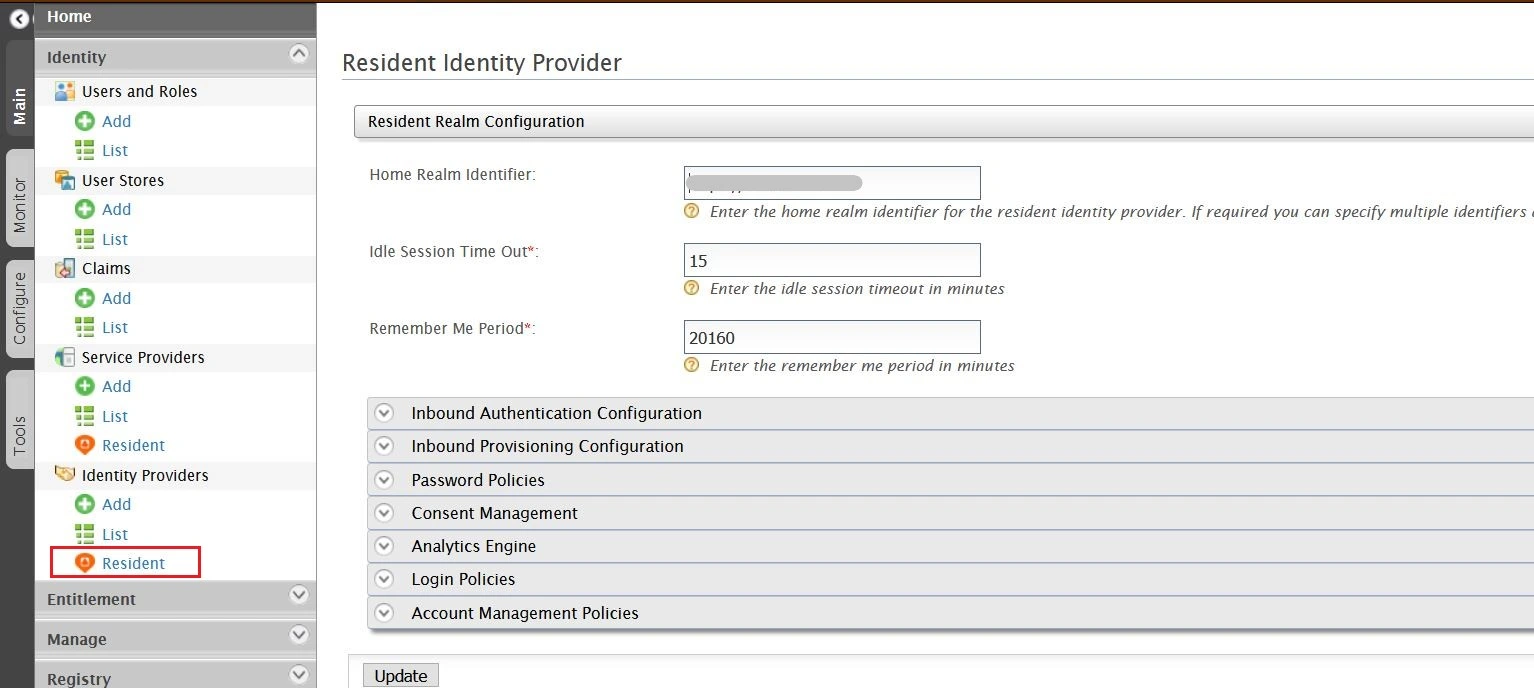
Step 2: Configure IDP inside miniOrange
- Login to miniOrange Admin Dashboard
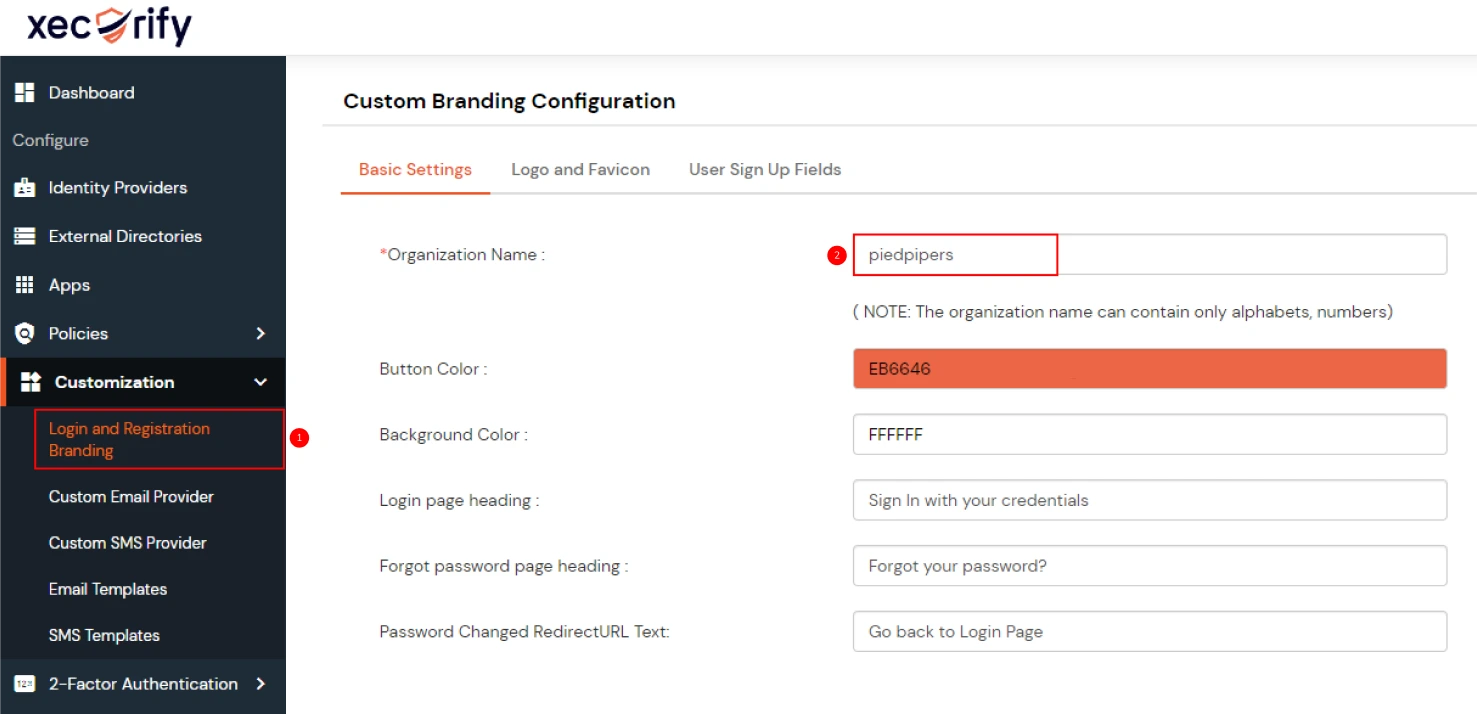
- From the left sidebar, expand Customization and click on Login and Registratin Branding.
- Here you can change the Organization Name. This will change all your custom urls from login.xecurify.com to the organization-name.xecurify.com. For e.g. we have used name piedpipers, so our custom urls will be changed as piedpipers.xecurify.com
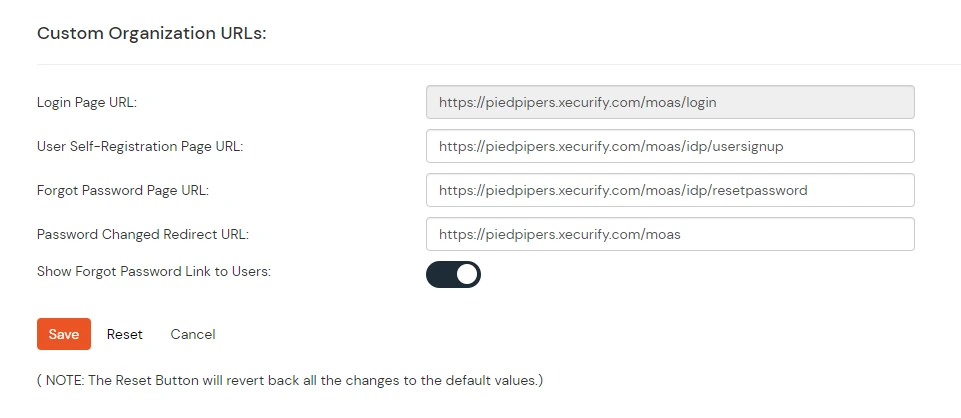
- Once you have changed the oraganization name and saved. you can see the changed urls under Custom Organization URLs section near Save button.
- Go to Identity Providers and click on Add Identity Provider button from top right corner.
- Enter the following details and click on Save button.
- Click on Save button.
Note : Changing the organization name is a mandatory step, and once you've made the change, you cannot revert back to login.xecurify.com. Therefore, it's crucial to choose your new organization name carefully. Additionally, it's important to note that you cannot use an organization name that is already being used by someone else.

| IDP Name | Enter IDP name here. |
| IDP Entity ID | Enter IDP Entity ID / Issuer ID from the Identity Provider info. |
| SAML SSO Login URL | Enter Single Sign On url provided by Identity Provider. |
| X.509 Certificate | Enter the cetificate provided by Identity Provider. |
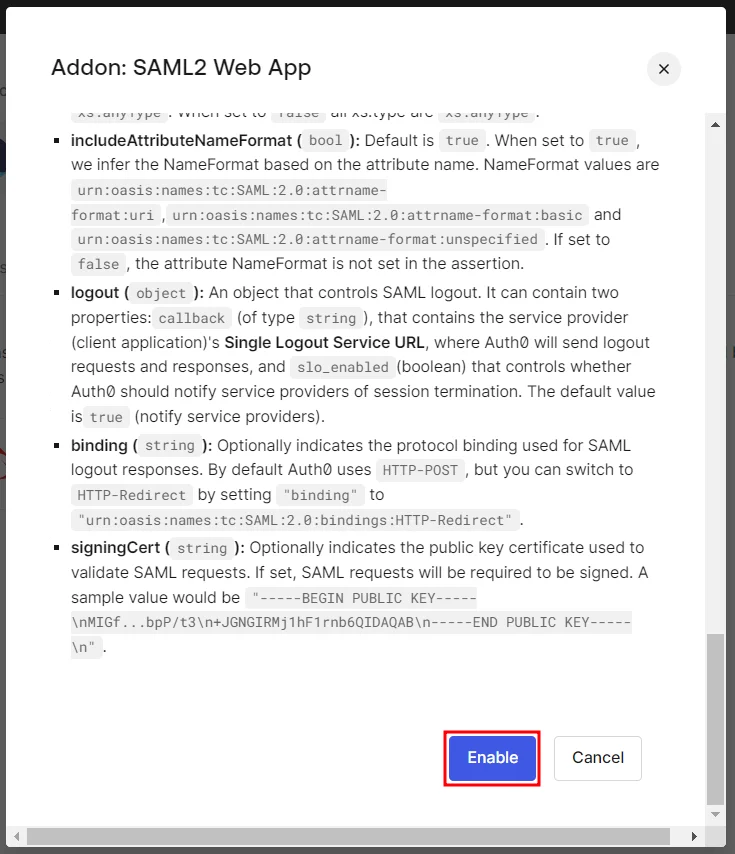
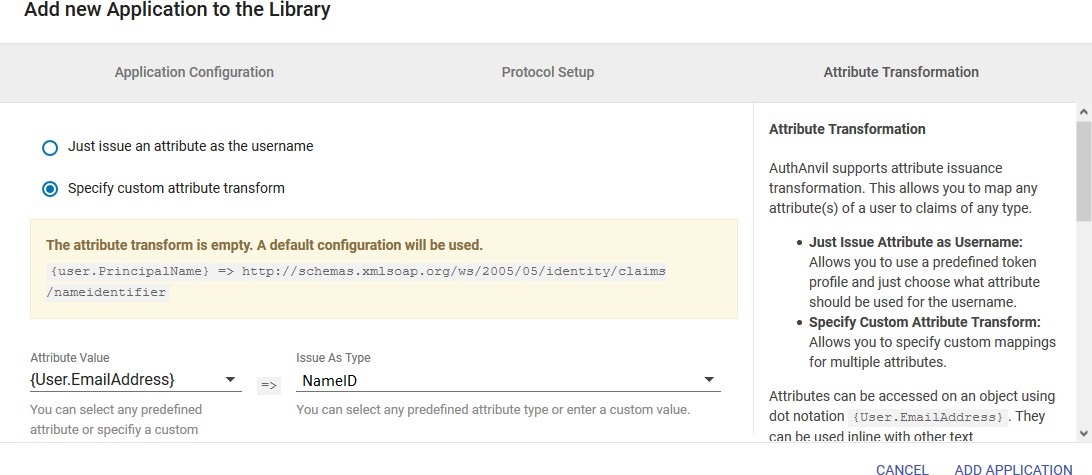
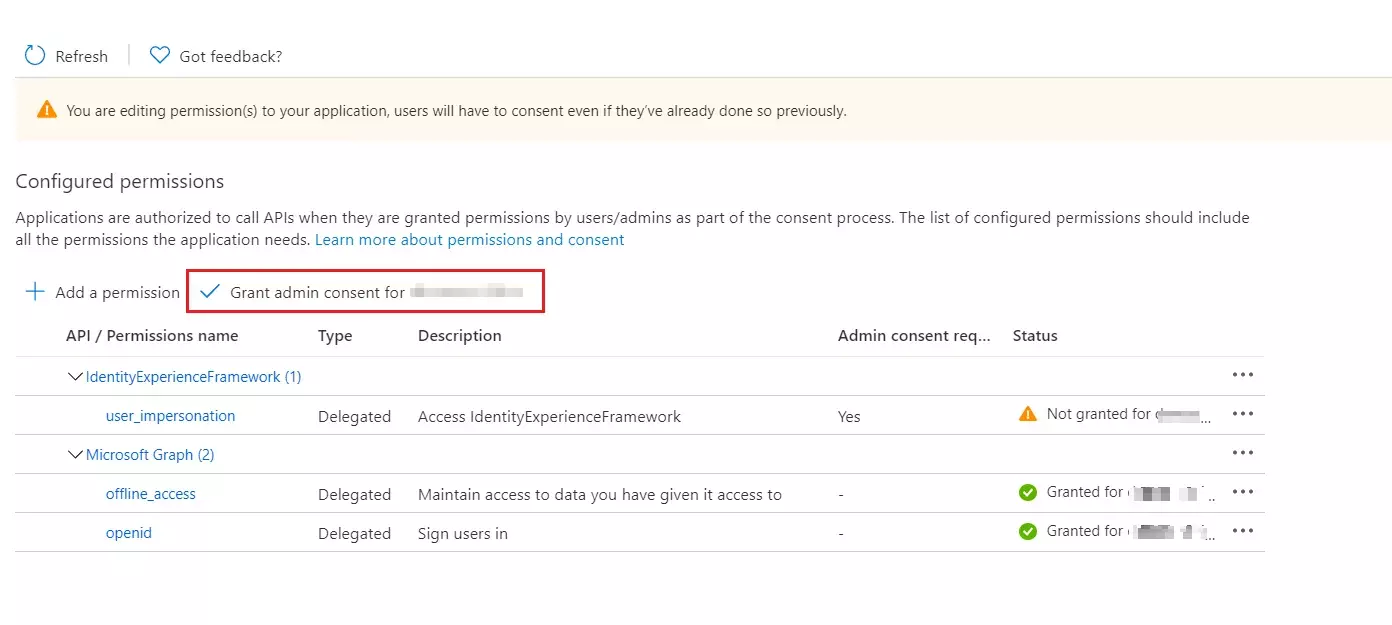
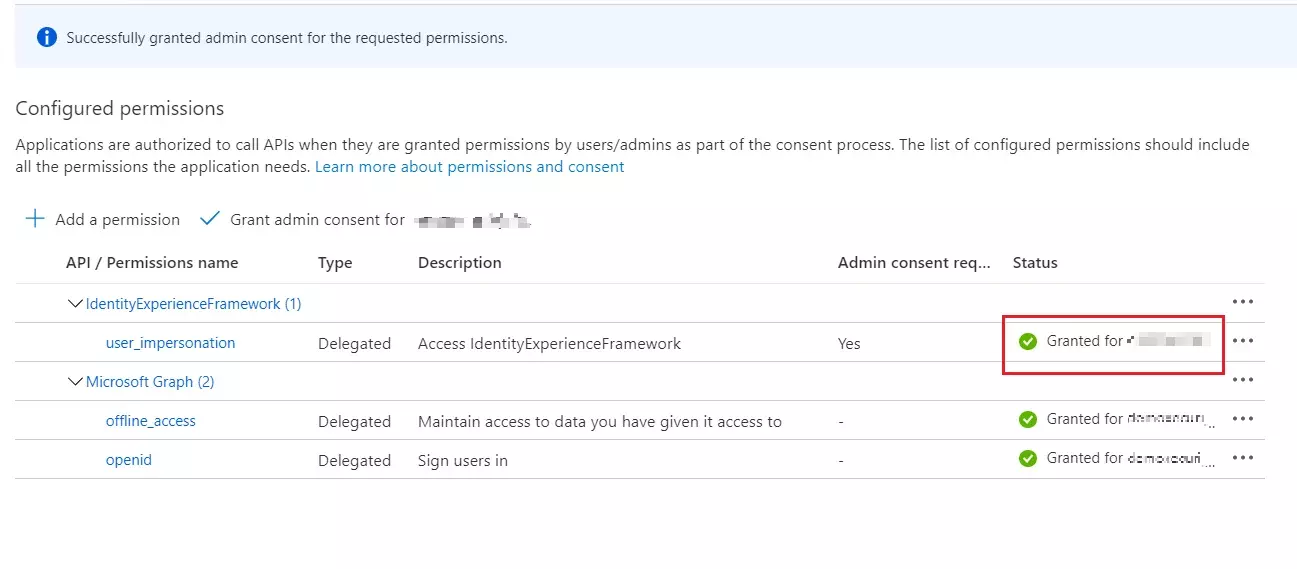
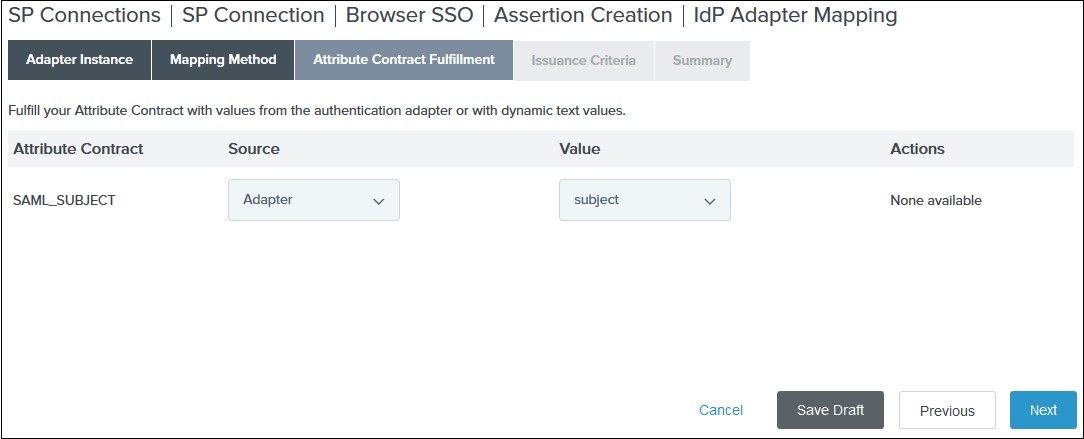
Please make sure that you enable the options Enable for EndUser Login and
Show IdP to Users
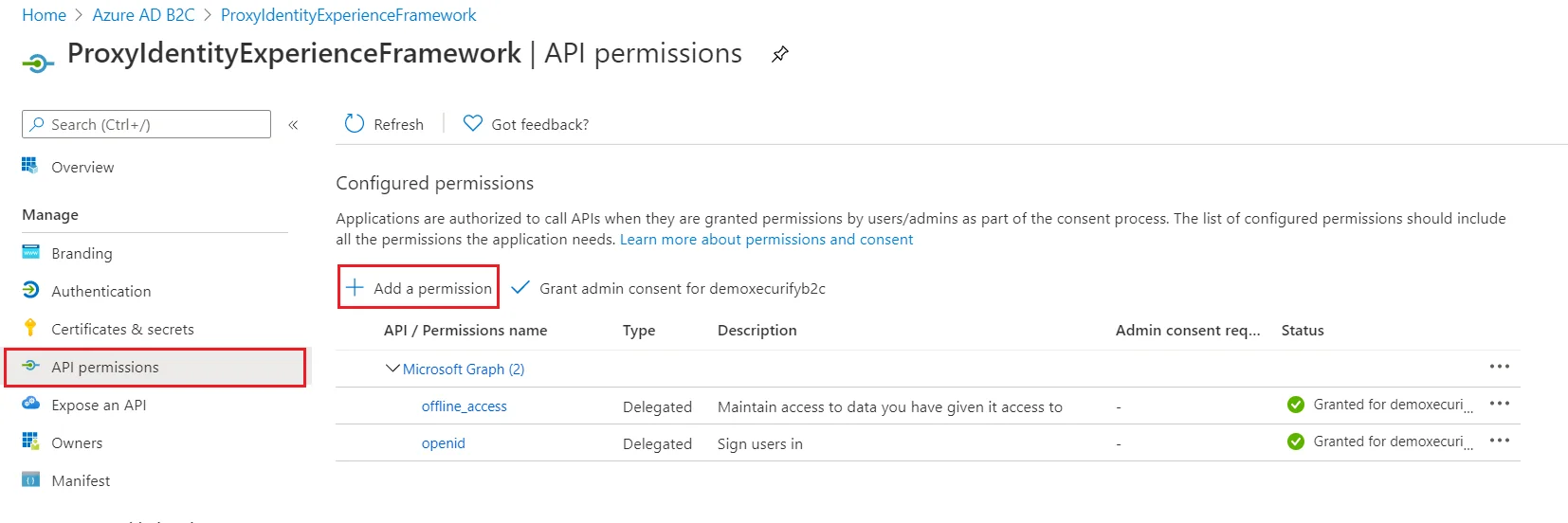
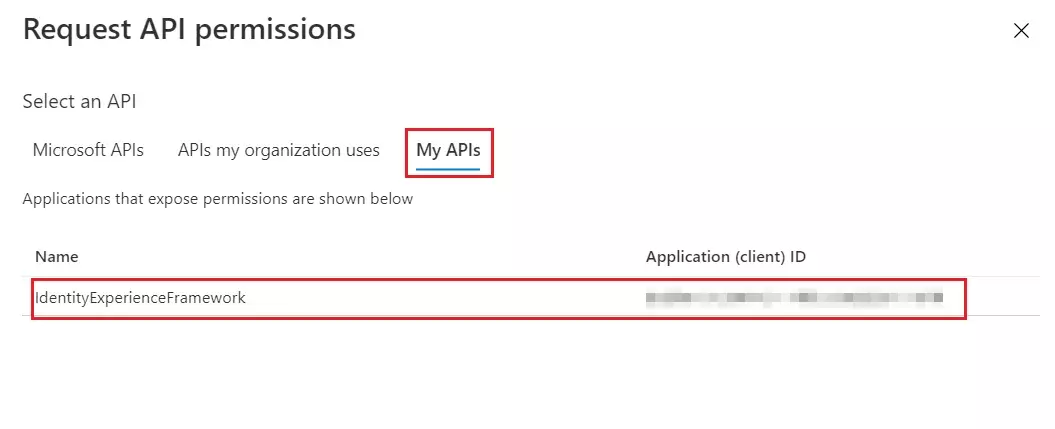
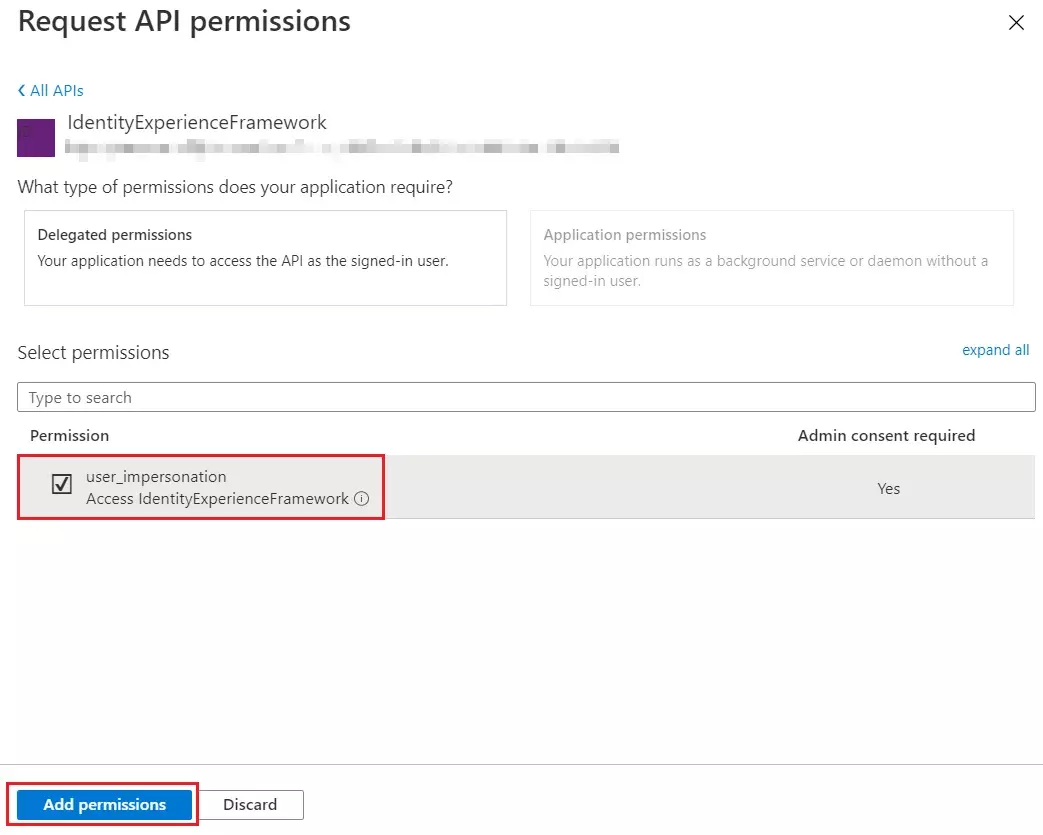
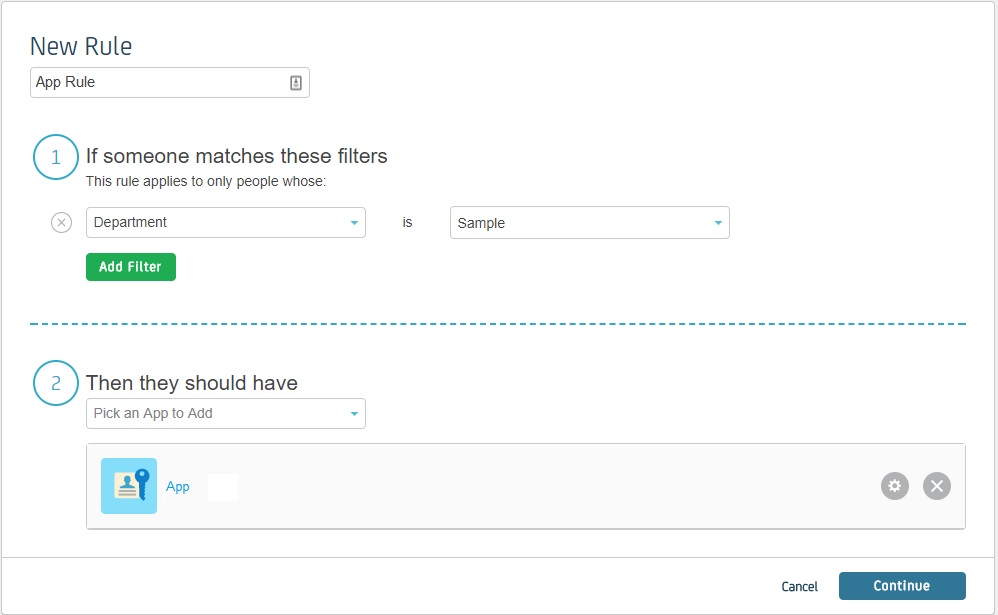
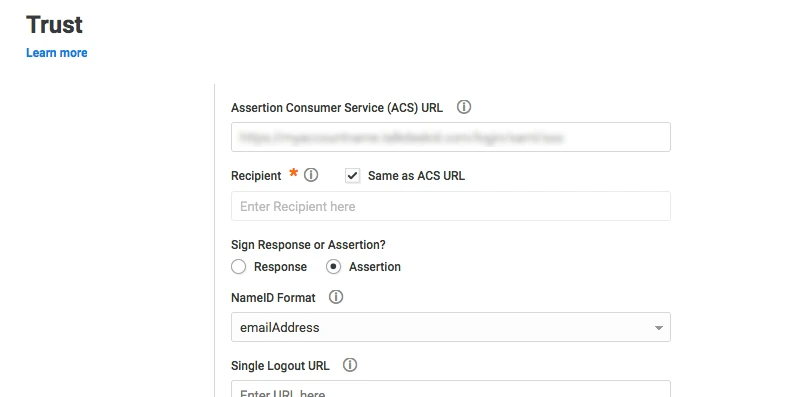
Step 3: Configure Selected IDPs
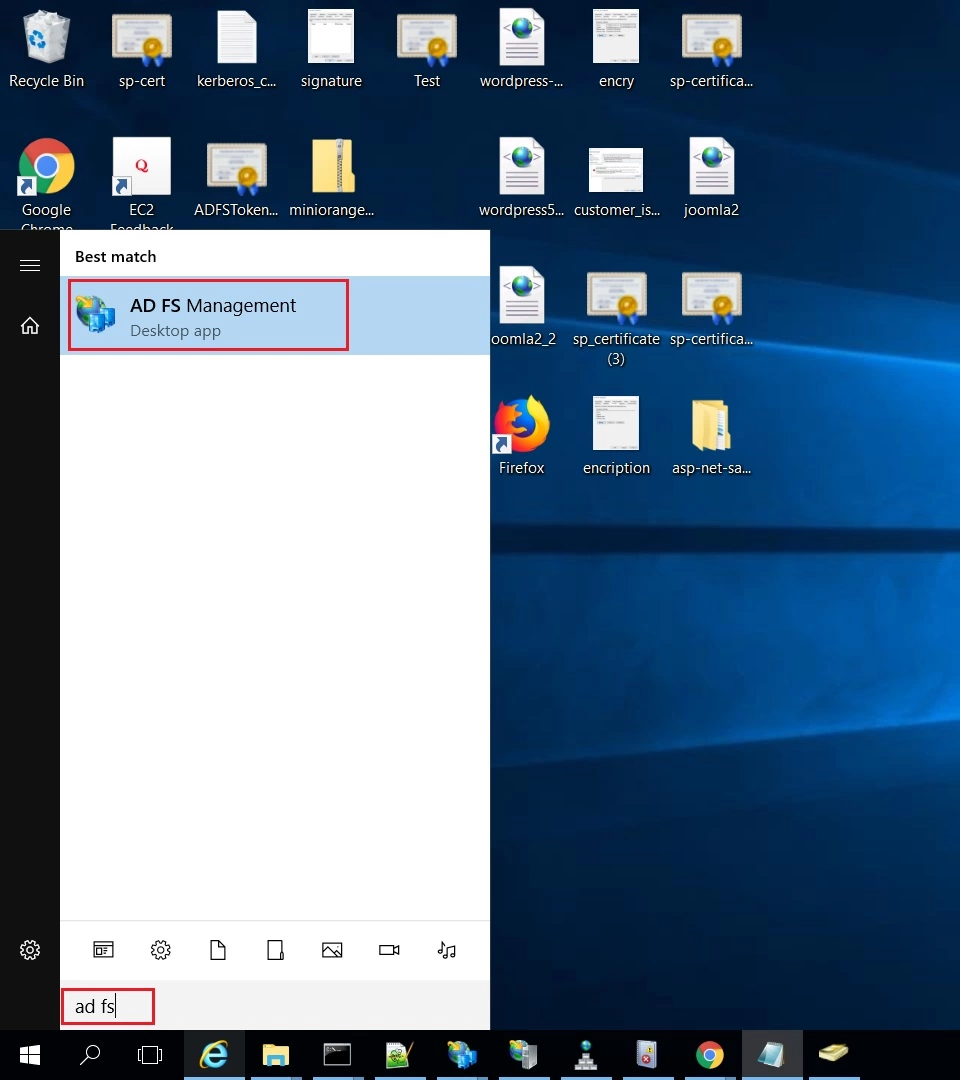
Step 1: Setup ADFS as Identity Provider
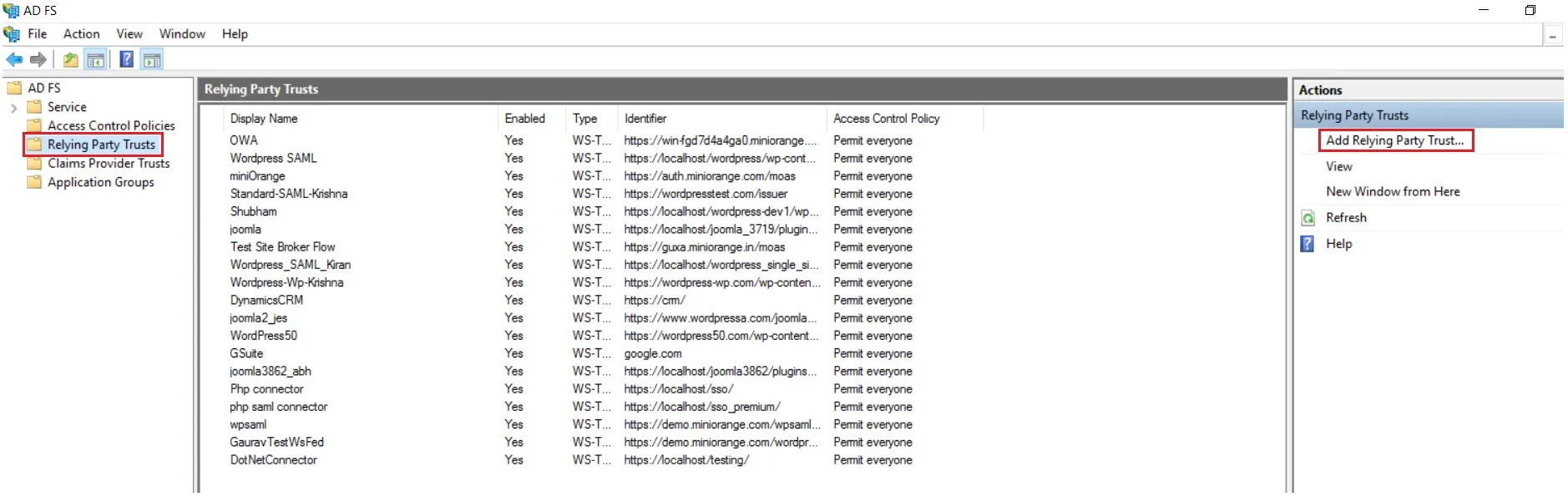
- On ADFS, search for ADFS Management application.
- After opening the AD FS Management, select Relying Party Trust & then click on Add Relying Party Trust.
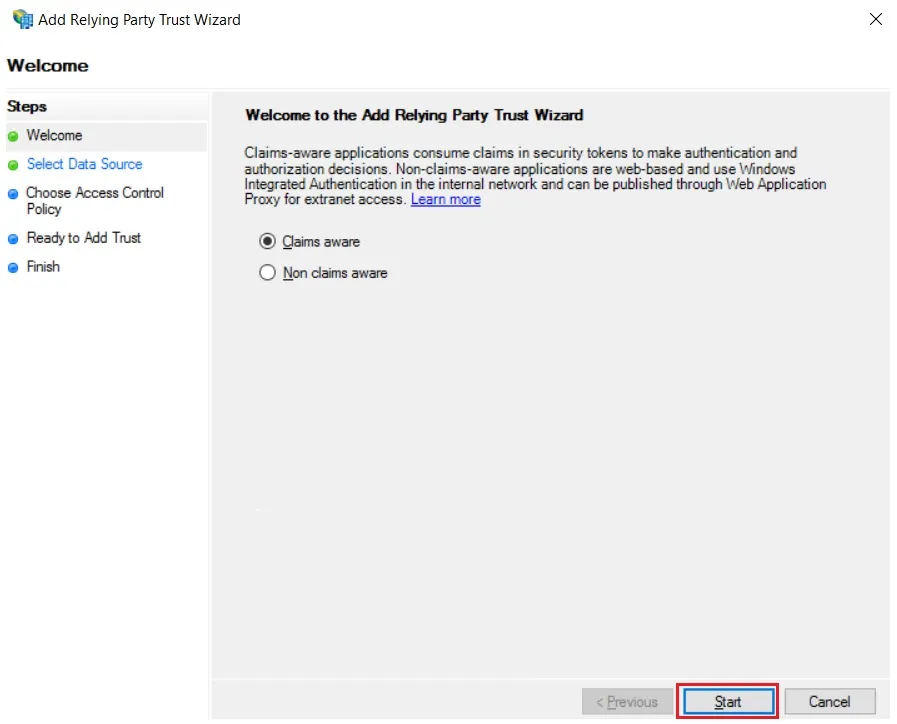
- Click the Start button from the Relying Party Trust Wizard pop up. But before that please make sure Claims Aware is selected.
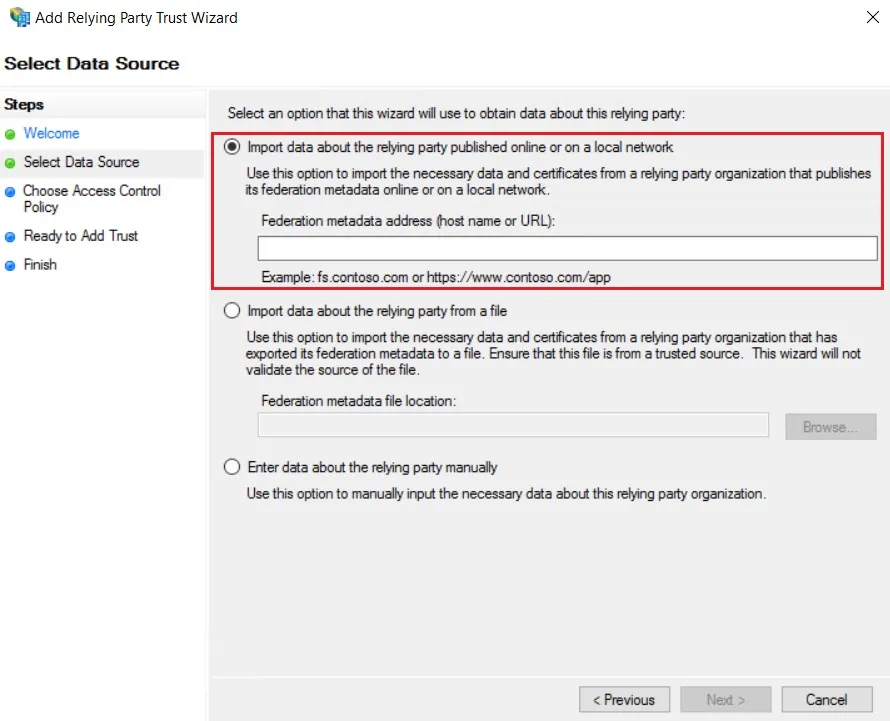
- Select the options for adding a relying party trust.
- In Select Data Source: Import data about the relying party published online or on the local network option & then add URL in Federation metadata address.
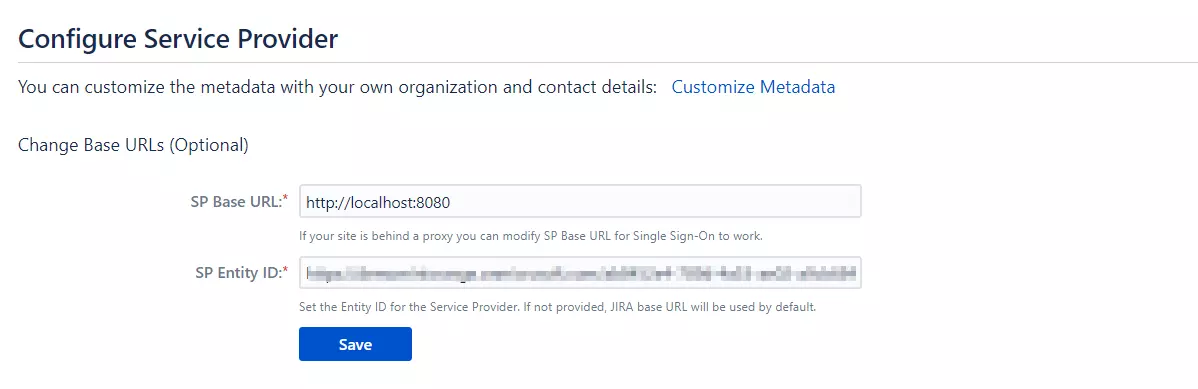
- Skip step-5 to step-8 & start configuring from step-9. Navigate to Service Provider Info tab from the plugin for getting SP Meatadata URL.
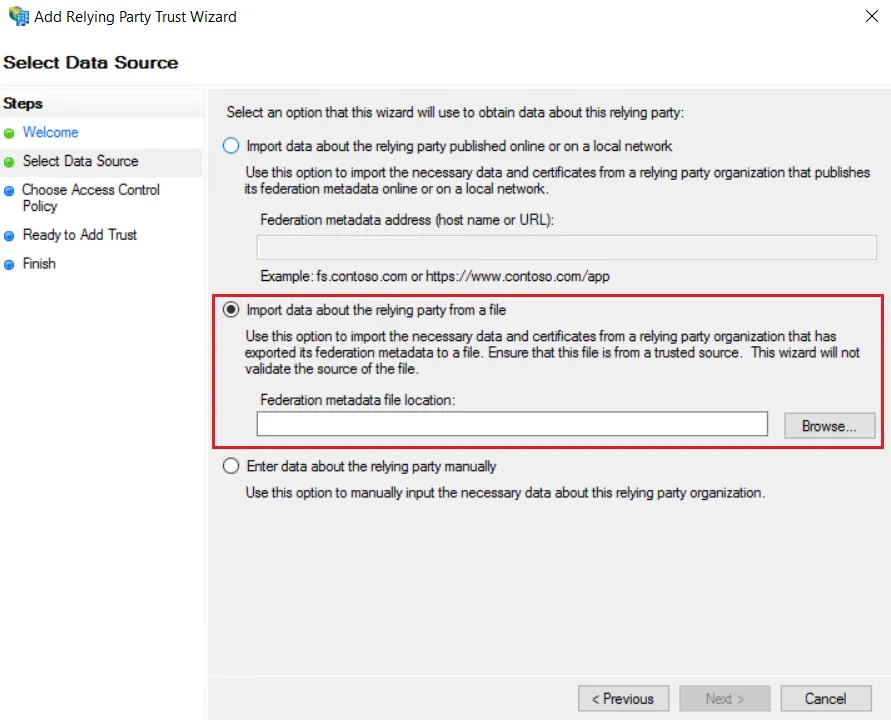
- In Select Data Source: Import data about the relying party from a file option & then browse the metadata file.
- Skip step-5 to step-8 & start configuring from step-9.
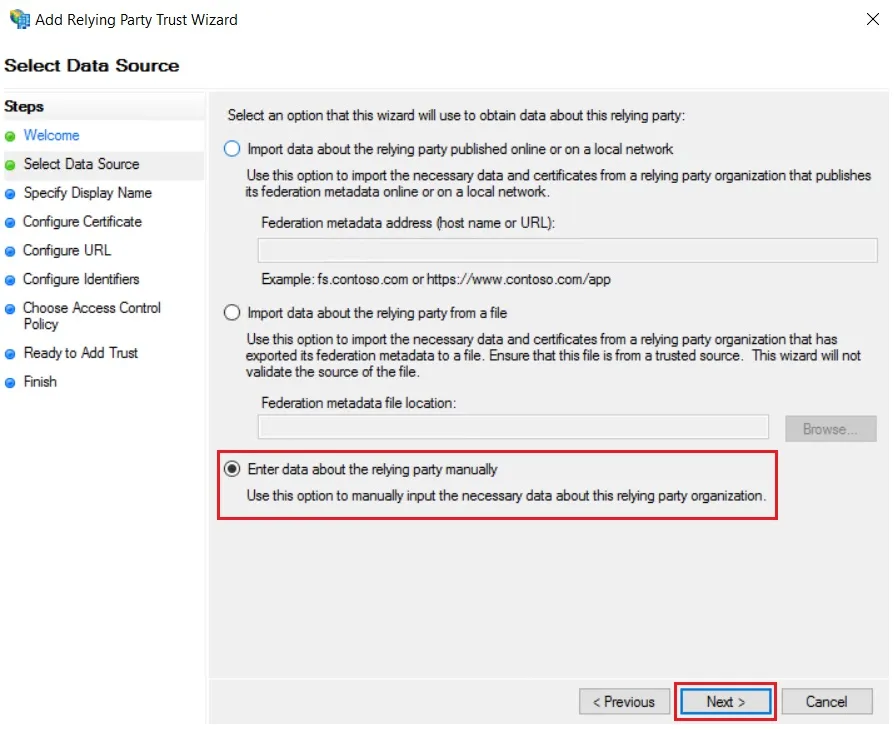
- In Select Data Source: Enter Data about the relying party manually & Click on Next.
- Enter Display Name & Click Next.
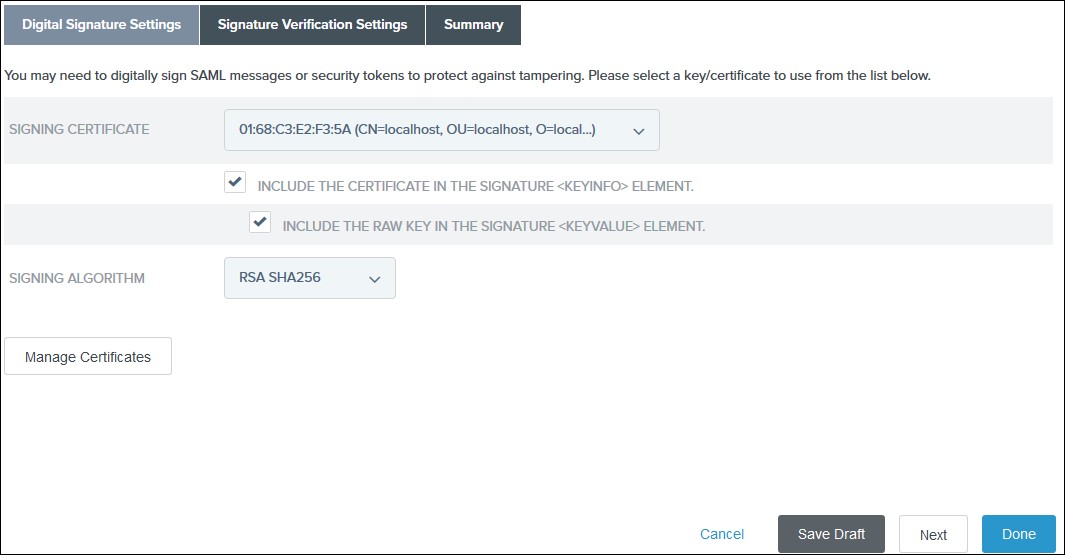
- Upload the certificate & click next. Download the certificate from plugin & use the same certificate to upload on ADFS.
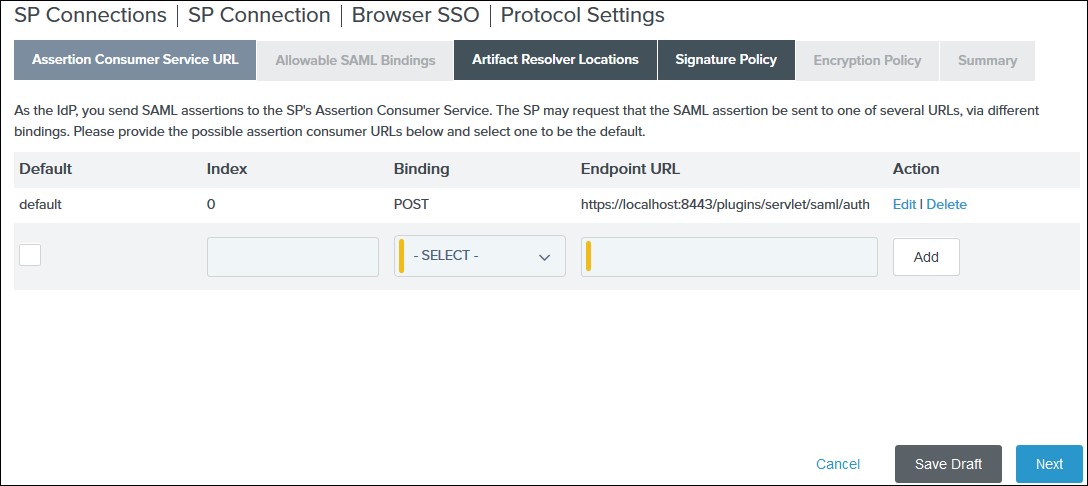
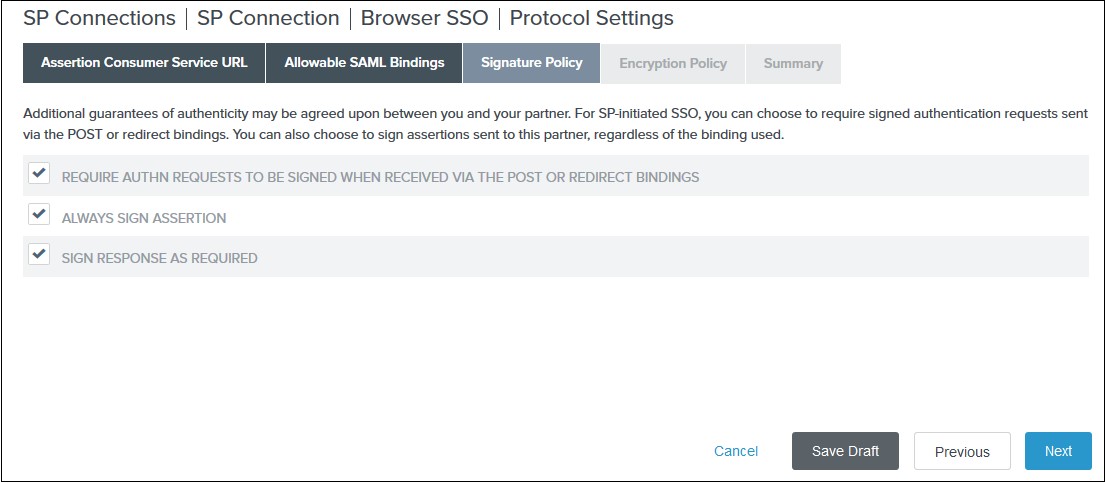
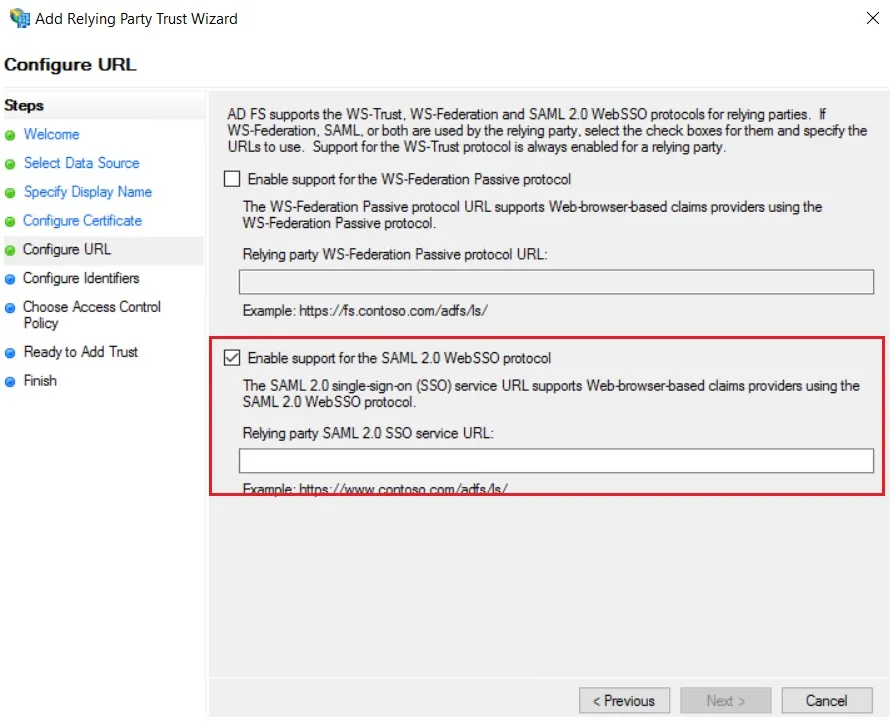
- Select Enable support for the SAML 2.0 WebSSO protocol & Enter ACS URL from the plugins Service Provider Info Tab. Click Next.
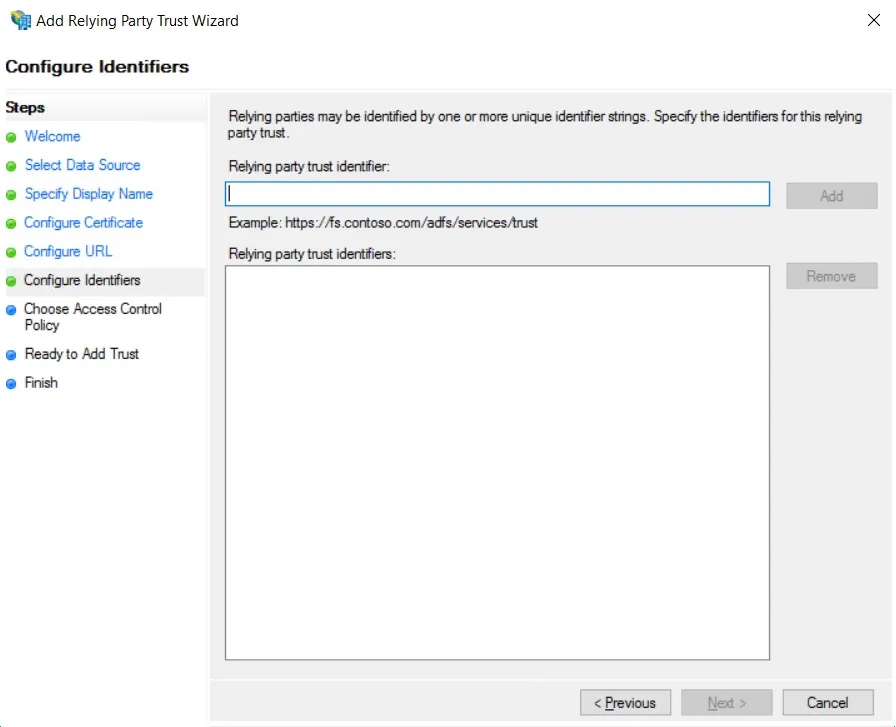
- Add Entity ID from plugins Service Provider Info Tab as Relying party trust identifier then click Add button & then click Next.
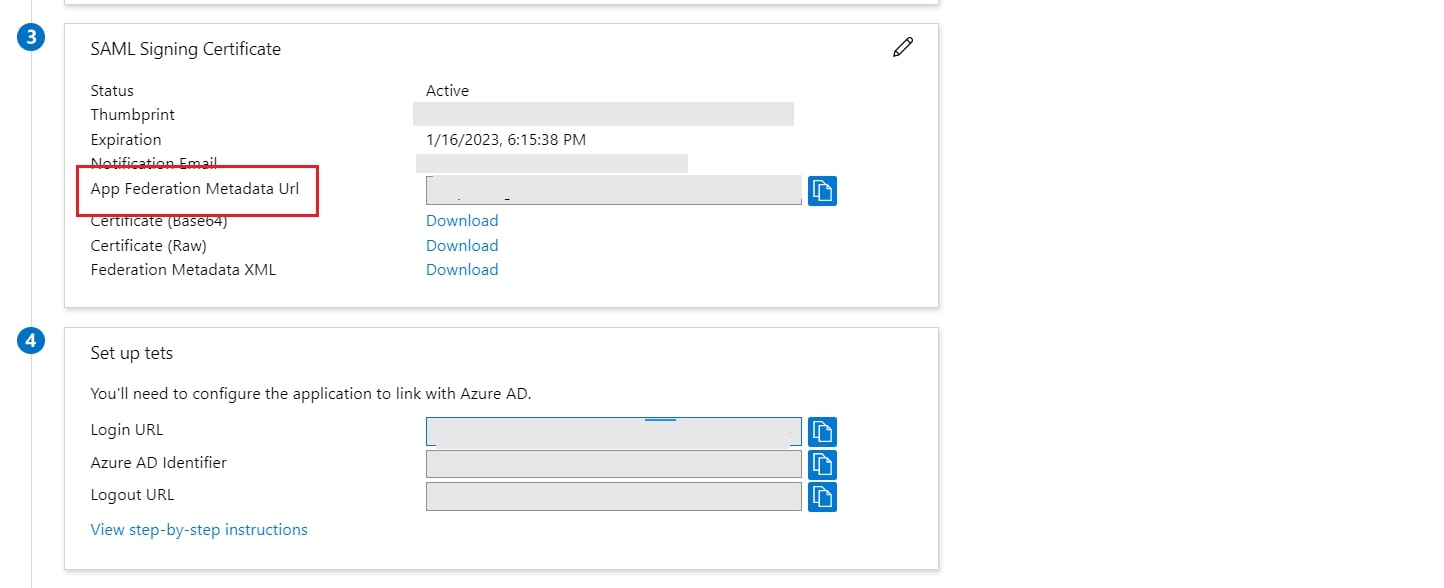
- Also download the Signing certificate from Service Provider Info Tab from the plugin.
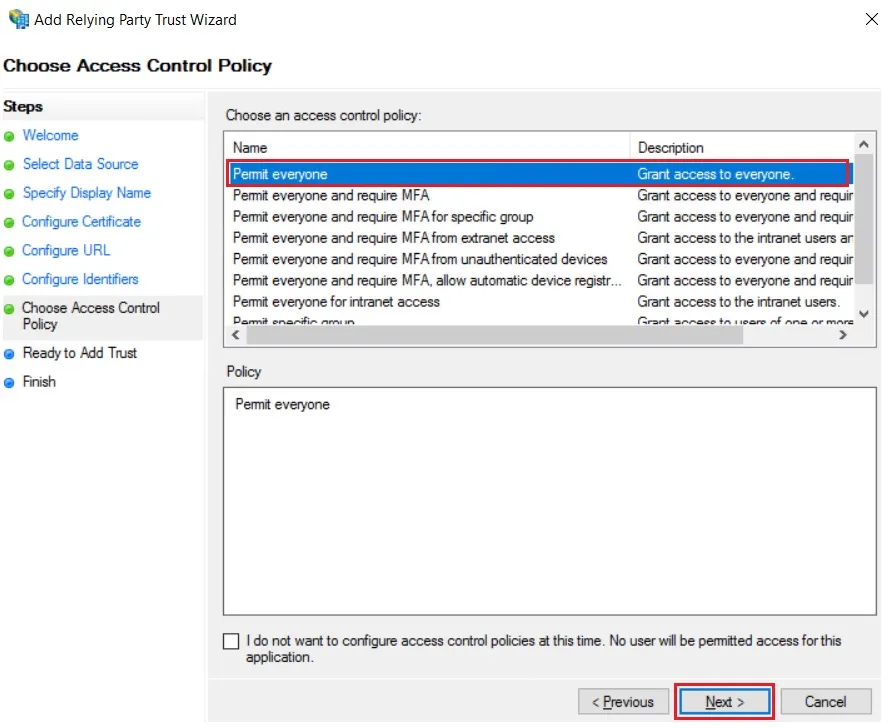
- Select Permit everyone as an Access Control Policy & click on Next.
- Click the Next button from Ready to Add Trust & click Close.
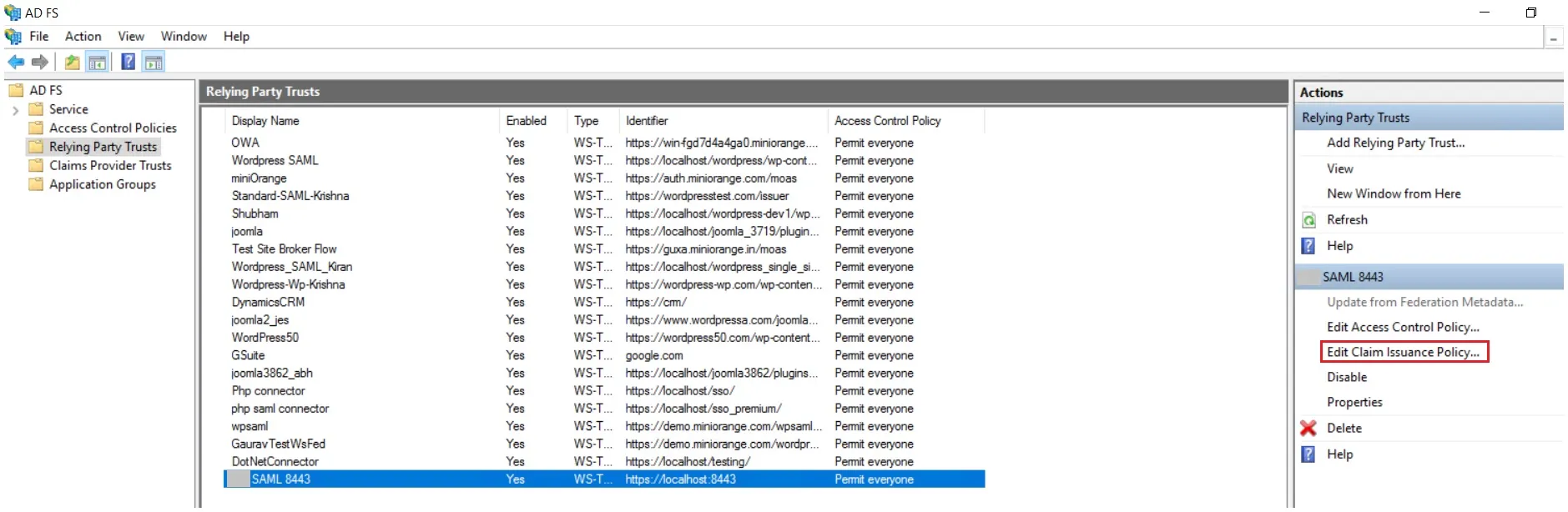
- It will show you the list of Relying Party Trusts. Select the respective application & click on Edit Claim Issuance Policy.
- Click on Add Rule button.
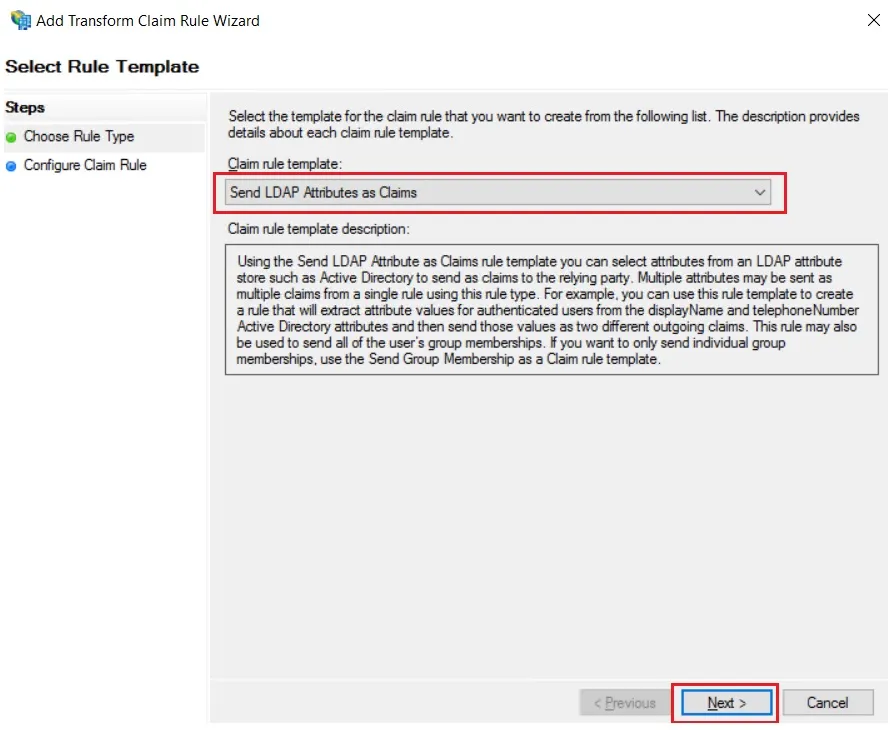
- Select Send LDAP Attributes as Claims & click on Next.
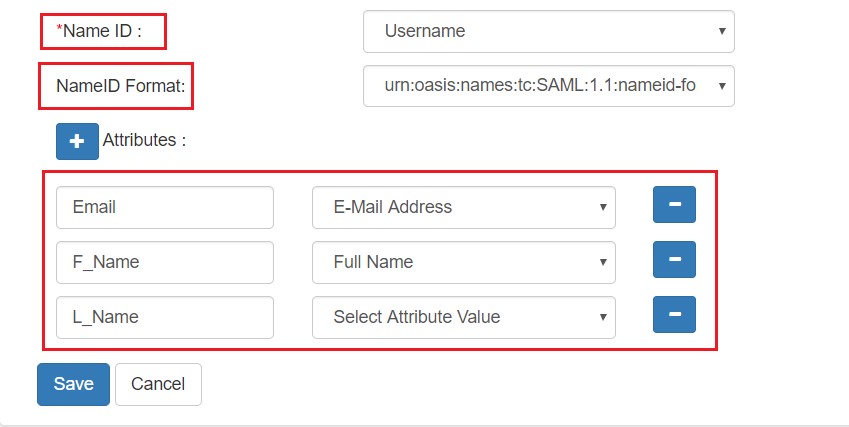
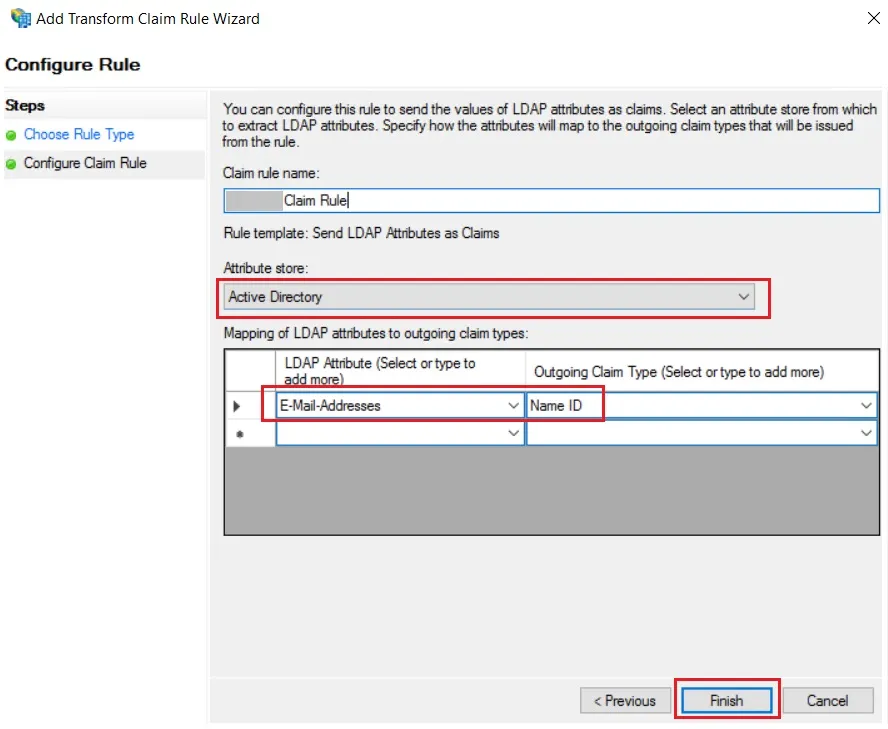
- Enter the following details & click on Finish.
- Click Apply Ok.
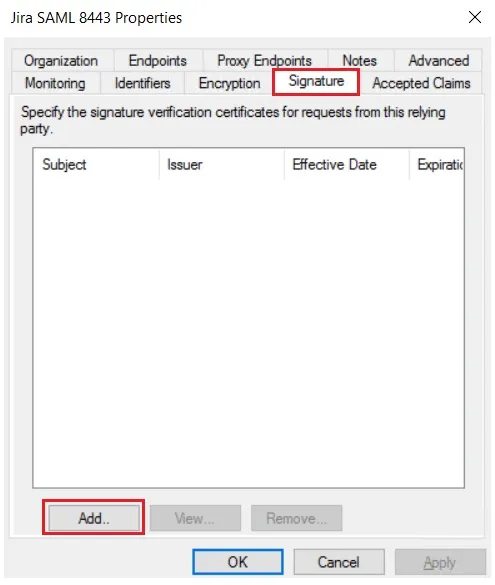
- Select property of the application & add the certificate downloaded from the add-on.
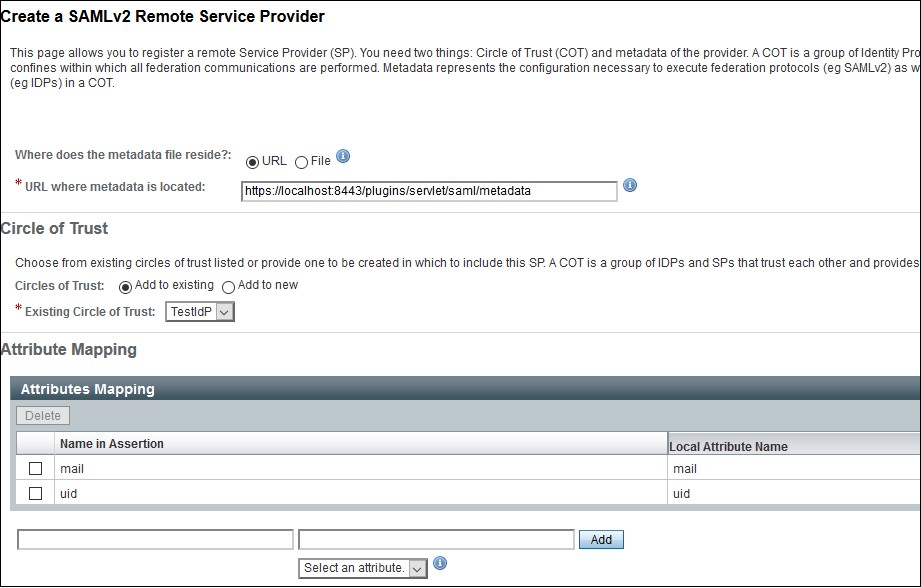
 Using Metadata URL
Using Metadata URL
 Using Metadata XML file
Using Metadata XML file
 Using Manual configuration
Using Manual configuration
| Claim rule name: | Attributes |
| Attribute Store: | Active Directory |
| LDAP Attribute: | E-Mail-Addresses |
| Outgoing Claim Type: | Name ID |
×
![]()