Contents
SAML SSO for JSM Customers using Shibboleth3 as IDP
You can now allow External Customers to login into Jira Service Management (previously Jira Service Desk or JSD) via SSO! Integration with various customer portals like Atlassian Service Management and access tickets with the help of SAML SSO for JSM Customers.
Download And Installation
- Log into your Jira instance as an admin.
- Navigate to the settings and Click on Apps.
- Locate SAML SSO for JSM Customers.
- Click on free trial to begin a new trial SAML SSO for JSM Customers.
- On menu bar click on Apps. Locate SAML SSO for JSM Customers .
Step 1: Setup Shibboleth3 as Identity Provider
- In conf/idp.properties, uncomment and set 'idp.encryption.optional' to true.
eg. idp.encryption.optional = true - In conf/metadata-providers.xml, configure Service Provider like below.
- In conf/saml-nameid.properties, uncomment and set default NameID as Email Address like this
- In conf/saml-nameid-xml, search for shibboleth.SAML2NameIDGenerators. Uncomment the shibboleth.SAML2AttributeSourcedGenerator bean and comment all other ref beans.
- Make sure you have defined AttributeDefinition in conf/attribute-resolver.xml.
- Make sure you have AttributeFilterPolicy defined in conf/attribute-filter.xml.
- Restart the Shibboleth server.
- You need to configure these endpoints in the miniOrange plugin.
<MetadataProvider xmlns:samlmd="urn:oasis:names:tc:SAML:2.0:metadata"
id="miniOrangeInLineEntity" xsi:type="InlineMetadataProvider" sortKey="1">
<samlmd:EntityDescriptor ID="entity" entityID="<SP-EntityID / Issuer from Service Provider Info tab in plugin.>"
validUntil="2020-09-06T04:13:32Z">
<samlmd:SPSSODescriptor AuthnRequestsSigned="false" WantAssertionsSigned="true"
protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<samlmd:NameIDFormat>
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
</samlmd:NameIDFormat>
<samlmd:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
Location="<ACS (AssertionConsumerService) URL from Step1 of the plugin under Identity Provider Tab.>"
index="1" />
</samlmd:SPSSODescriptor>
</samlmd:EntityDescriptor>
</MetadataProvider>
idp.nameid.saml2.default=urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
<!-- SAML 2 NameID Generation -->
<util:list id="shibboleth.SAML2NameIDGenerators">
<!--<ref bean="shibboleth.SAML2TransientGenerator" /> -->
<!-->ref bean="shibboleth.SAML2PersistentGenerator" /> -->
<bean parent="shibboleth.SAML2AttributeSourcedGenerator"
p:format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress"
p:attributeSourceIds="#{ {'email'} }" />
</util:list>
<!-- Note: AttributeDefinitionid must be same as what you provided in attributeSourceIds in conf/saml-nameid.xml -->
<resolver:AttributeDefinitionxsi:type="ad:Simple" id="email" sourceAttributeID="mail">
<resolver:Dependency ref="ldapConnector" />
<resolver:AttributeEncoderxsi:type="enc:SAML2String" name="email" friendlyName="email" />
</resolver:AttributeDefinition >
<resolver:DataConnector id="ldapConnector" xsi:type="dc:LDAPDirectory" ldapURL="%{idp.authn.LDAP.ldapURL}"
baseDN="%{idp.authn.LDAP.baseDN}" principal="%{idp.authn.LDAP.bindDN}"
principalCredential="%{idp.authn.LDAP.bindDNCredential}">
<dc:FilterTemplate>
<!-- Define you User Search Filter here -->
<![CDATA[ (&(objectclass=*)(cn=$requestContext.principalName)) ]]>
</dc:FilterTemplate>
<dc:ReturnAttributes>*</dc:ReturnAttributes>
</resolver:DataConnector>
<afp:AttributeFilterPolicy id="ldapAttributes">
<afp:PolicyRequirementRulexsi:type="basic:ANY"/>
<afp:AttributeRuleattributeID="email">
<afp:PermitValueRulexsi:type="basic:ANY"/>
</afp:AttributeRule>
</afp:AttributeFilterPolicy>
| IDP Entity ID | https://<your_domain>/idp/shibboleth |
| Single Login URL | https://<your_domain>/idp/profile/SAML2/Redirect/SSO |
| Single Logout URL | https://<your_domain>/idp/shibboleth |
| X.509 Certificate | The public key certificate of your Shibboleth server |
Step 2. Setup JSM as Service provider
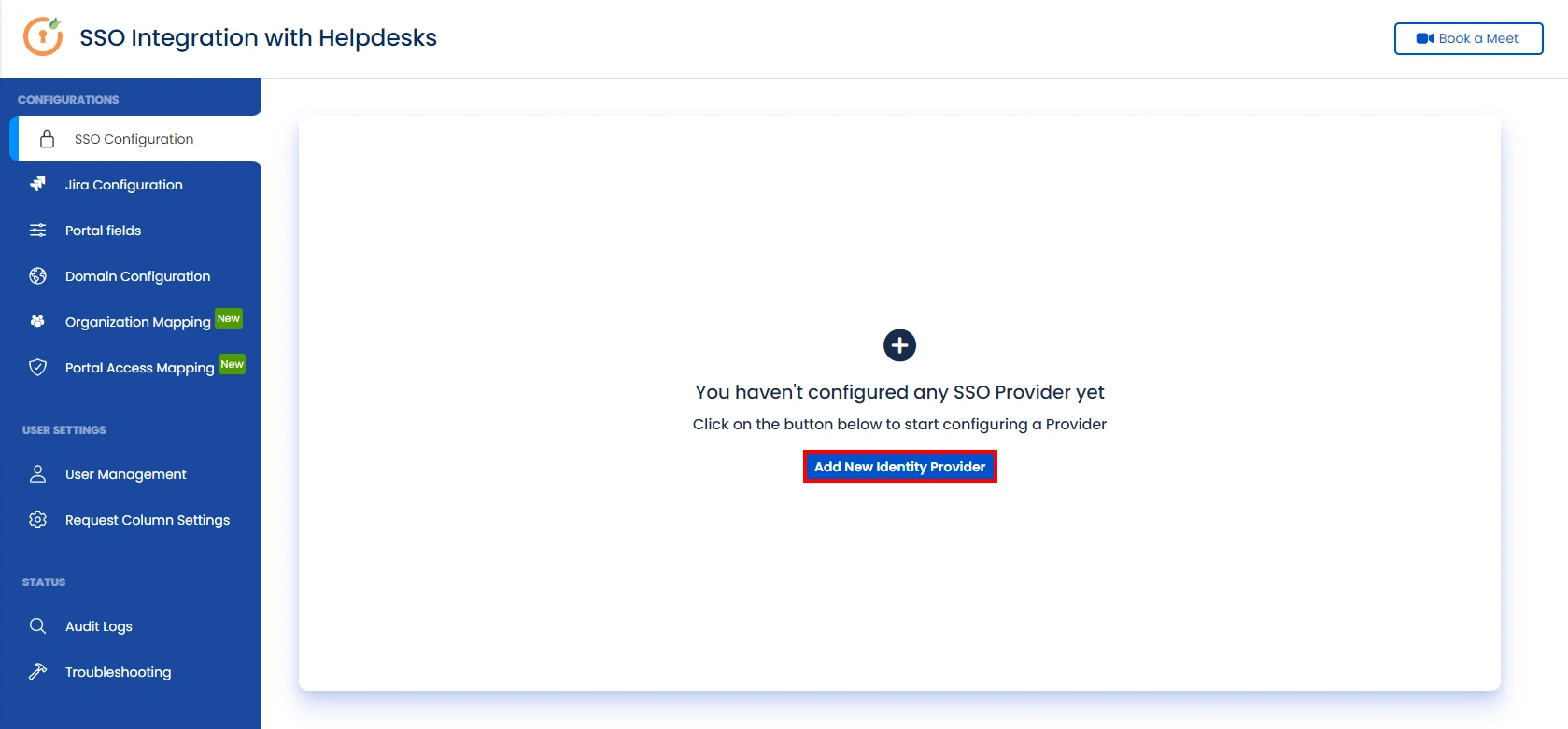
- Go to the Manage Apps -> click Getting started under SSO Integration with Helpdesk then click on the Add New Identity Provider.
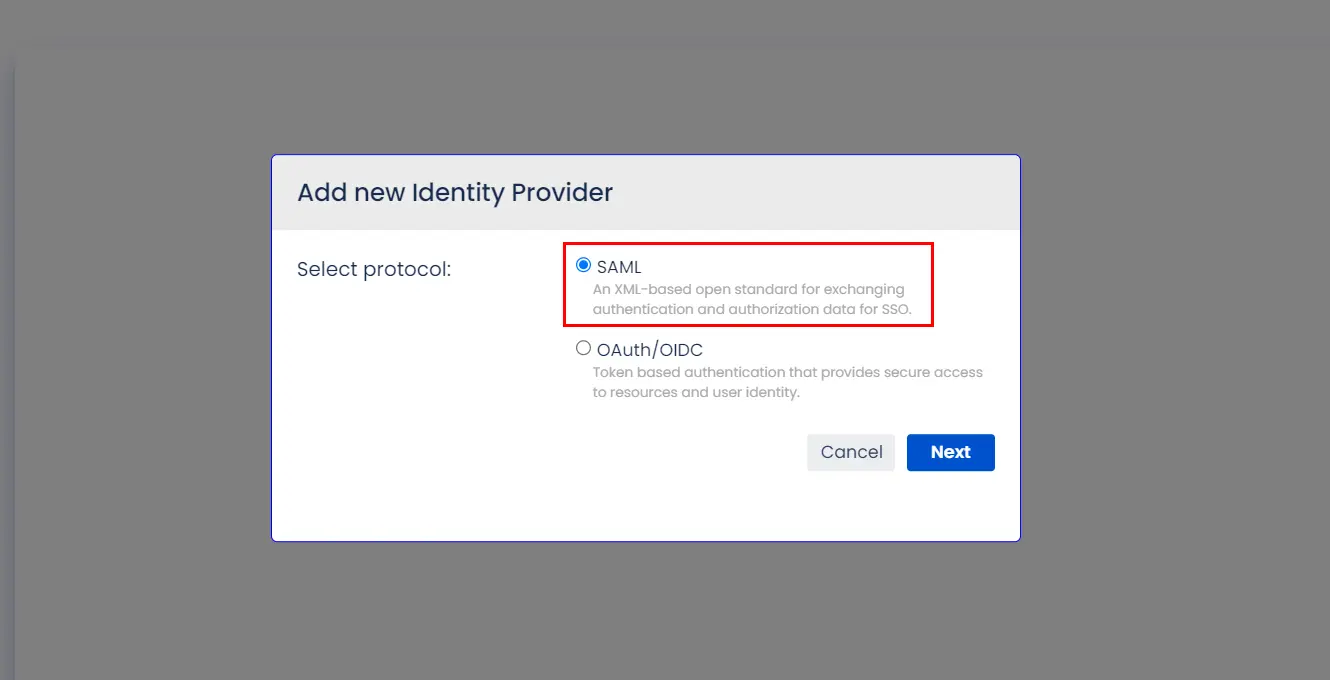
- Select SAML and click on the next button.
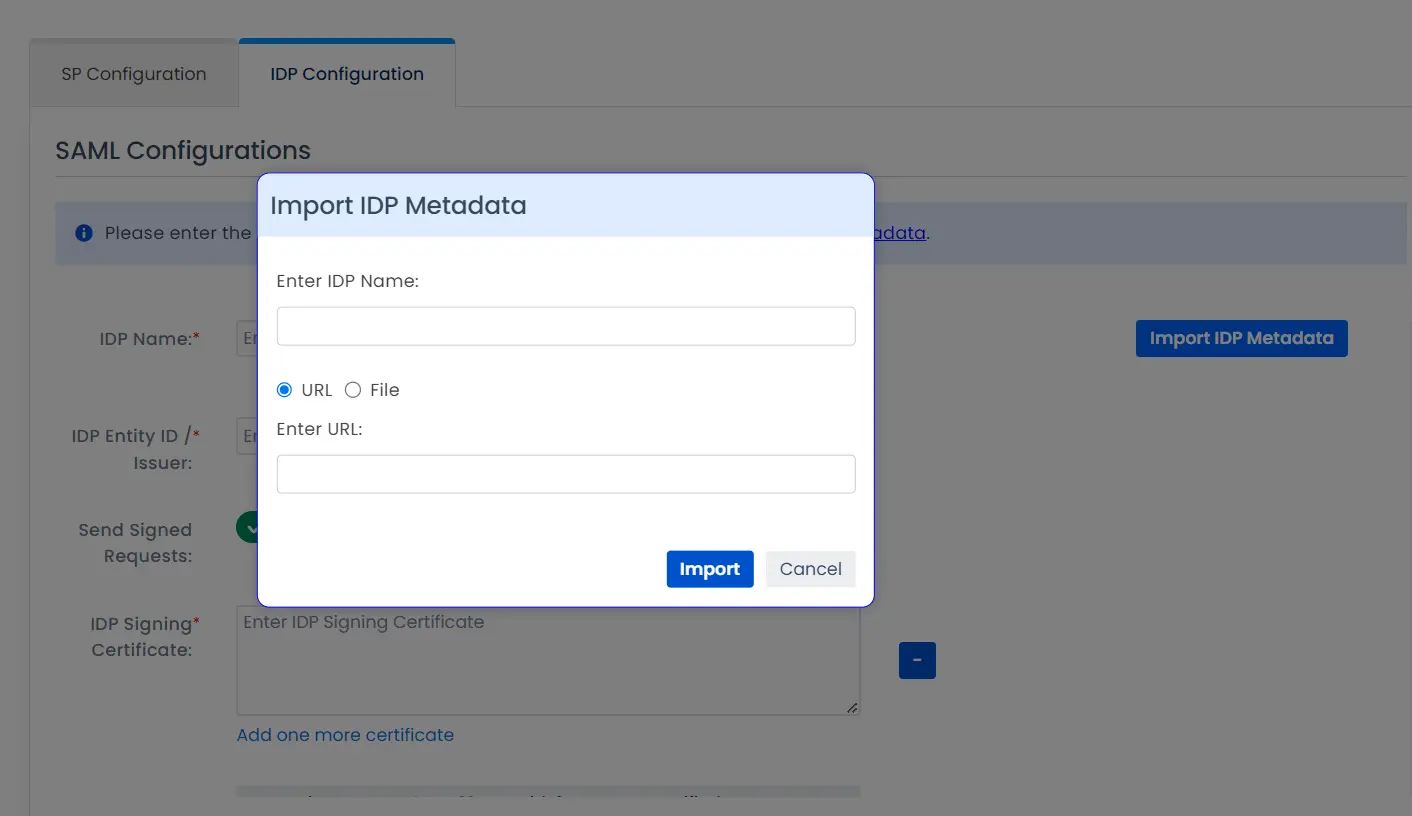
- Click on Import IDP Metadata.
- Enter IDP name.
- Choose IDP metadata URL / File: Enter your metadata URL / File
- Click Import
A. By Metadata URL :
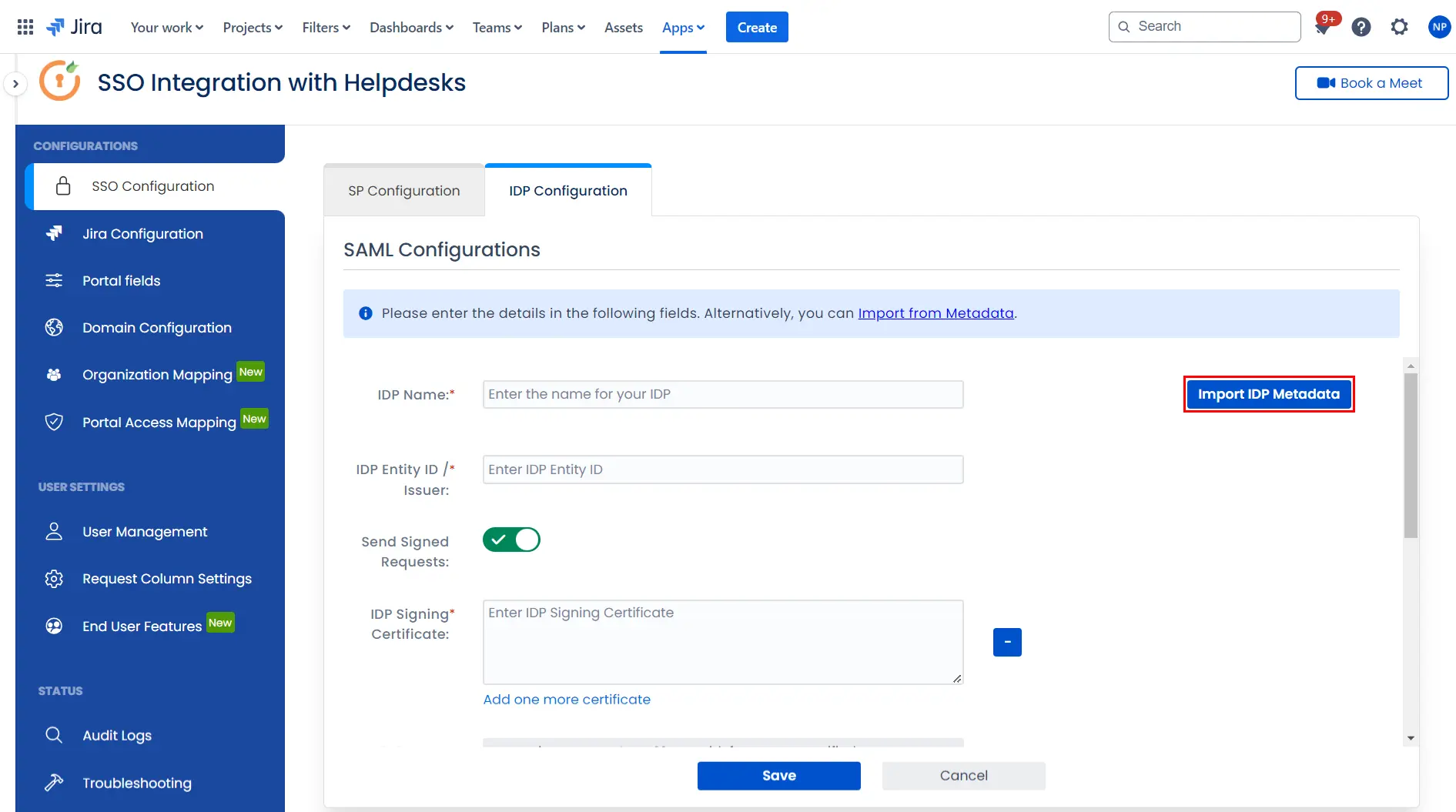
To configure the IDP manually, you will need to have the following details from your IDP's metadata.
- IDP Entity ID
- Single Sign On URL
- Single Logout URL
- X.509 Certificate
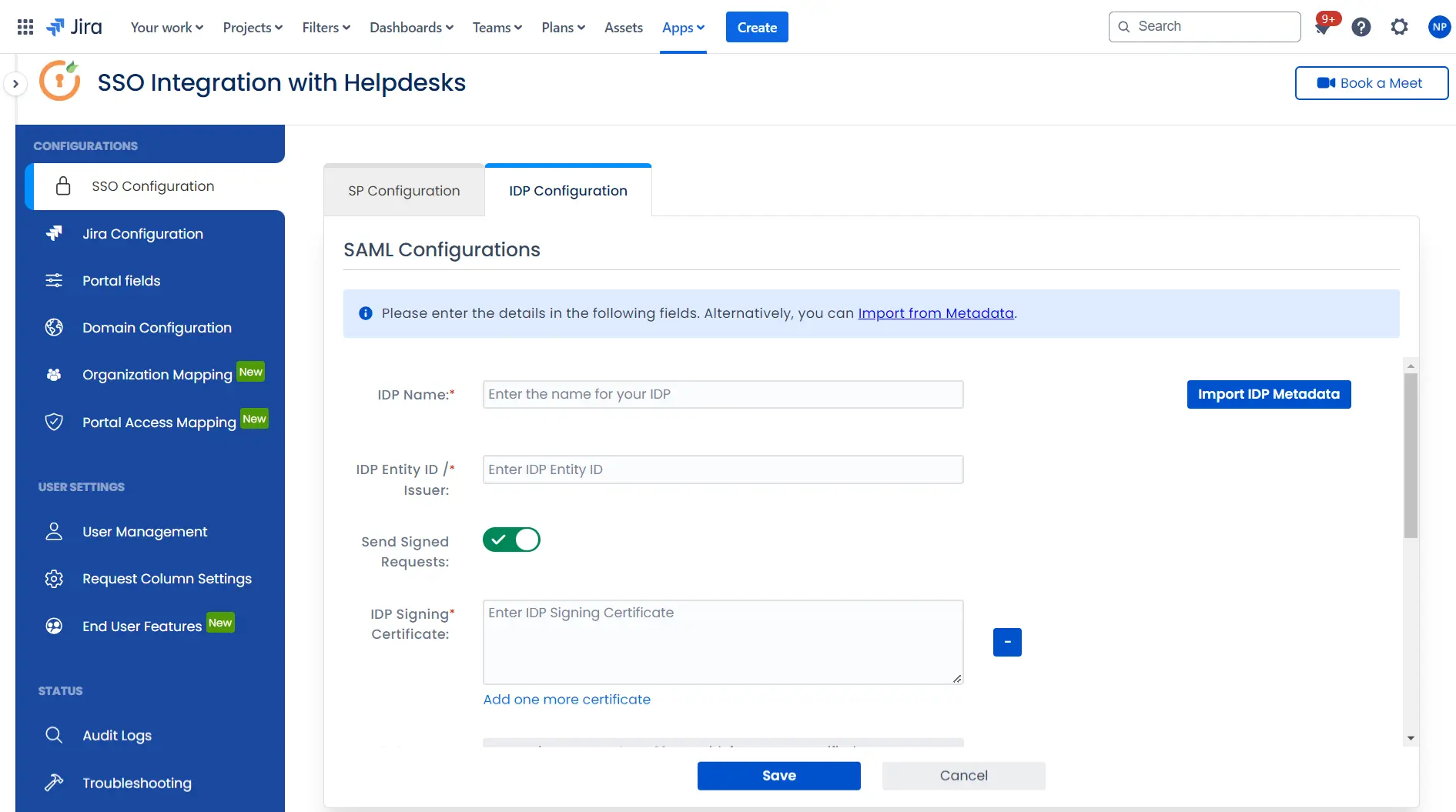
Once you have added the IDP metadata, click on Save. If the IDP has been added successfully, Click on the Test Configuration button to test if the IDP was added successfully.
Step 3: Integrate Atlassian HelpDesk with JSM SSO
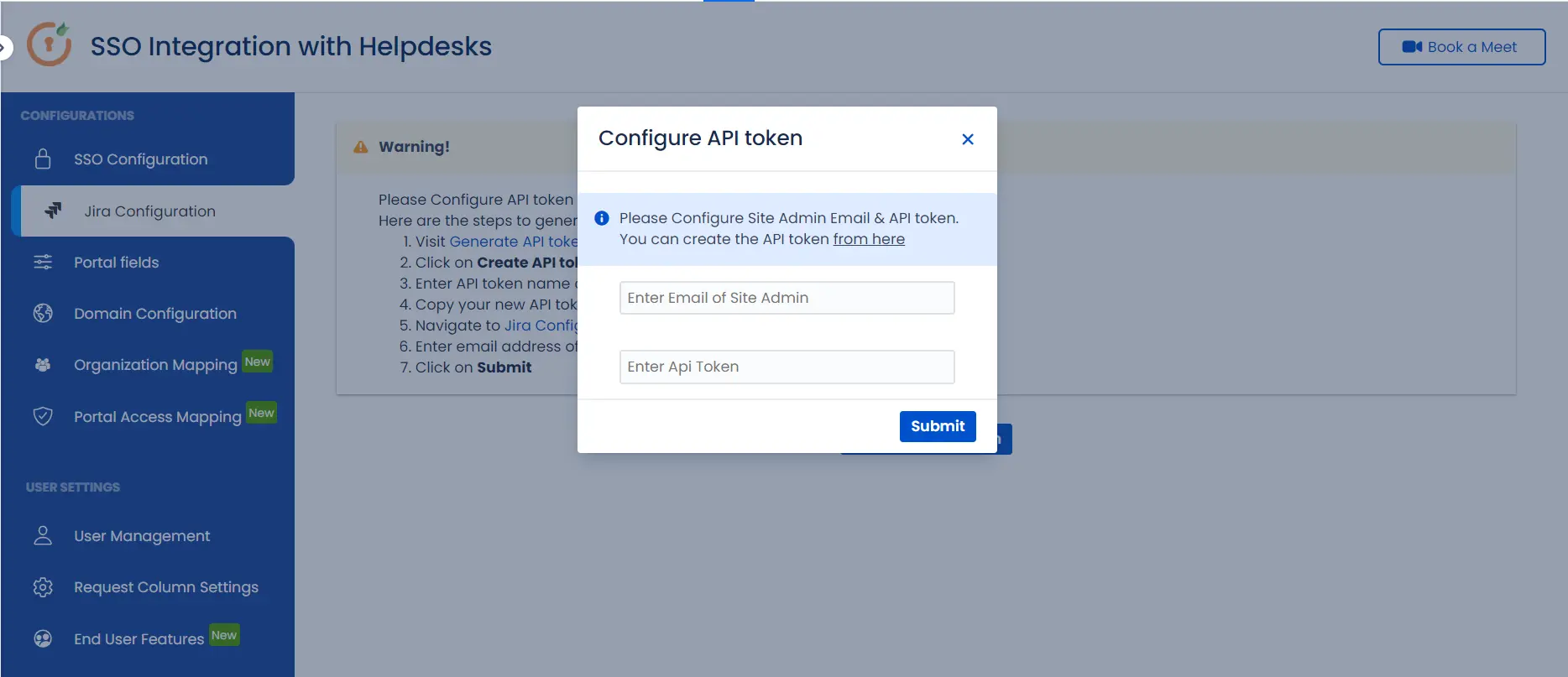
- Click on the Configure API Token and configure the Service Account API token with the email.
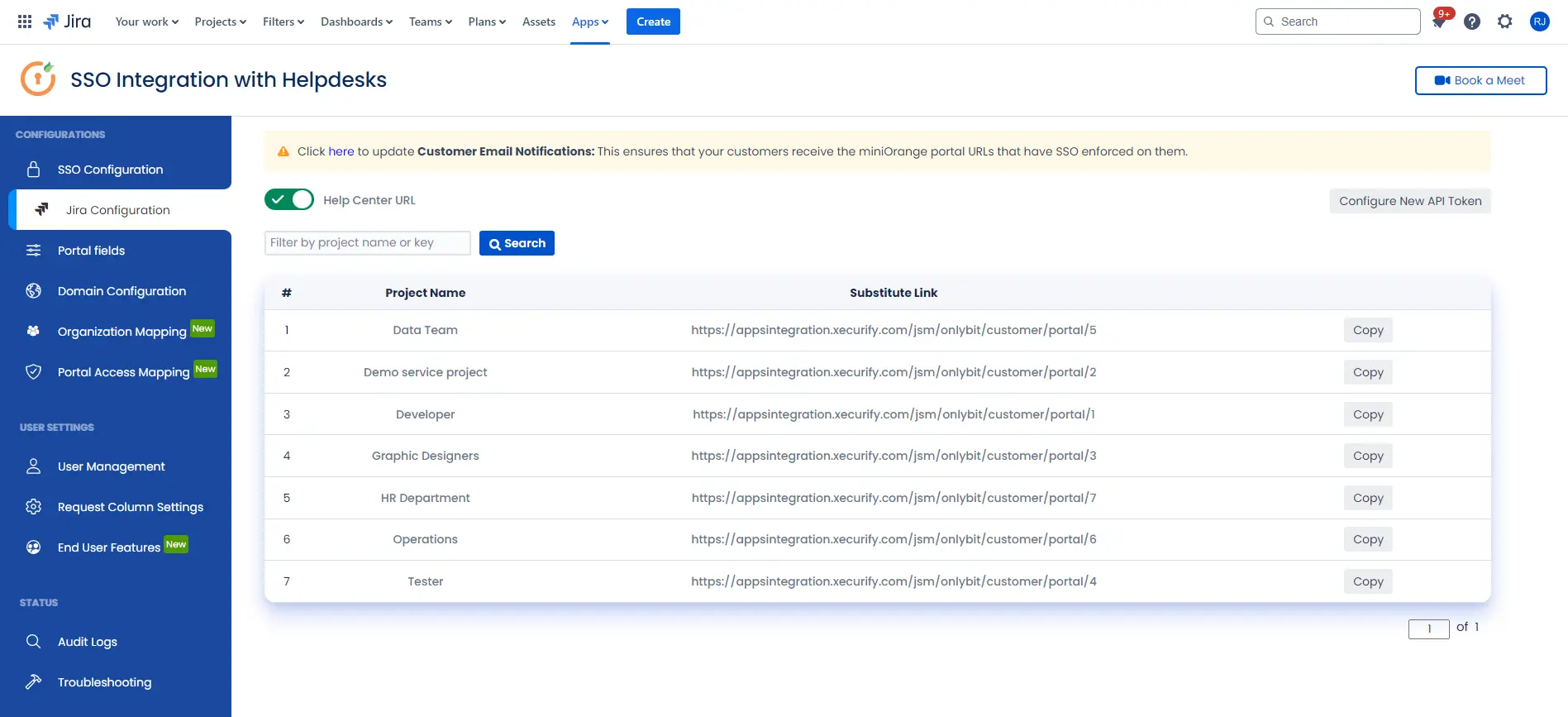
- After successful configuration of API token all the service desk projects with respective links will be displayed. These substituted links will be used by customers for accessing particular projects with SSO.
- Copy any of the substitute links you see for your portals and try accessing it in a private browser window. You would be automatically redirected to your Identity Provider for authentication and would be allowed access to the portal only after successful authentication.
 Hi! Do you need help with this guide?
Hi! Do you need help with this guide?
Thank you for your response. We will get back to you soon.
Something went wrong. Please submit your query again

Recommended Add-Ons

Two Factor Authentication
Enable 2FA/MFA for users & groups and let users configure 2FA during their first login.
Know More
User Sync SCIM Provisioning
Synchronize users, groups & directory with SCIM & REST APIs for Server/DC.
Know More
API Token Authentication
Secure your JIRA Data Center/Server REST API using API Tokens.
Know MoreBitbucket Git Authentication App | Kerberos/NTLM Apps | Word/PDF Exporter | WebAuthn | SonarQube SSO | Jenkins SSO
If you don't find what you are looking for, please contact us at support-atlassian@miniorange.atlassian.net or raise a support ticket here.

