Introduction
What is a CASB?
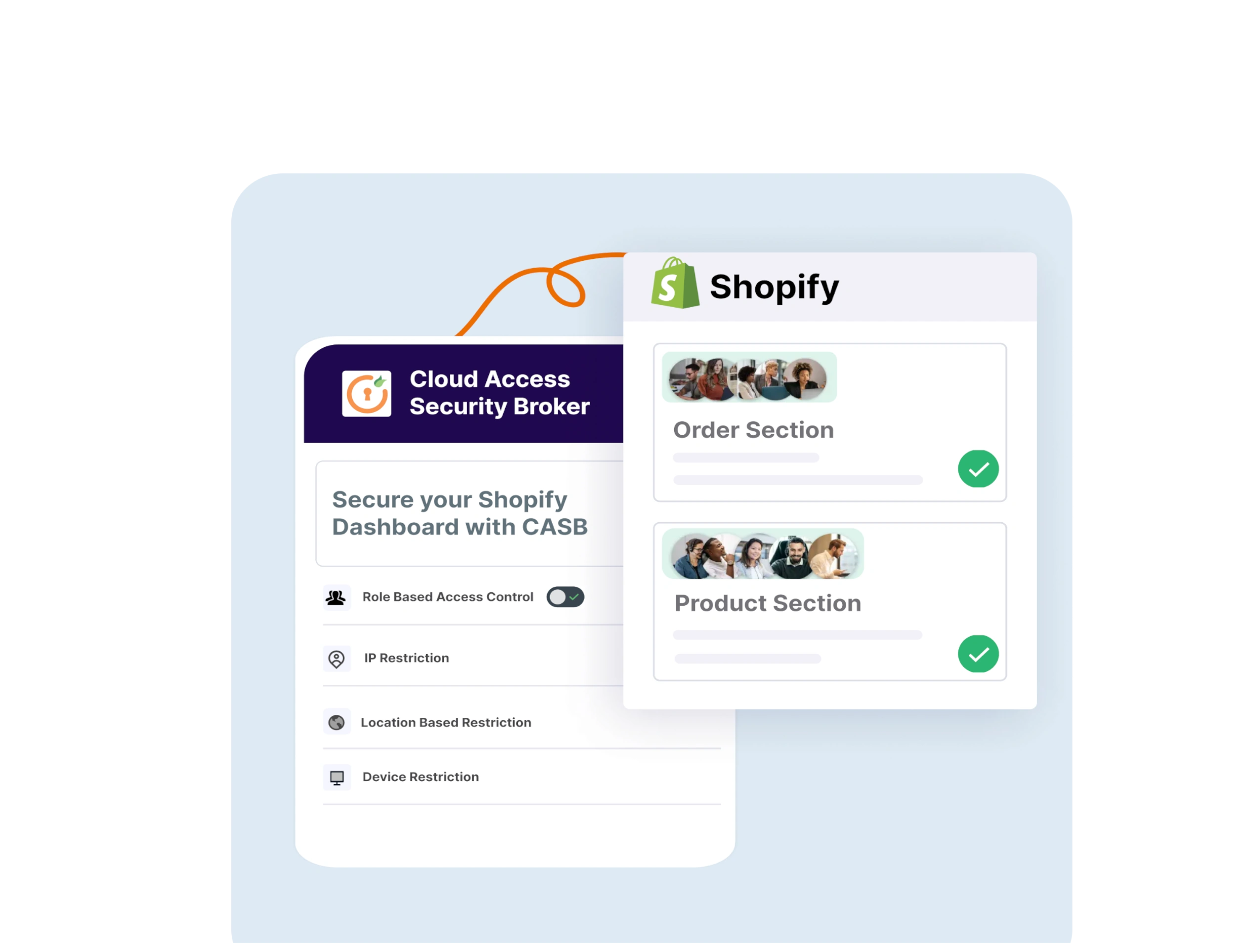
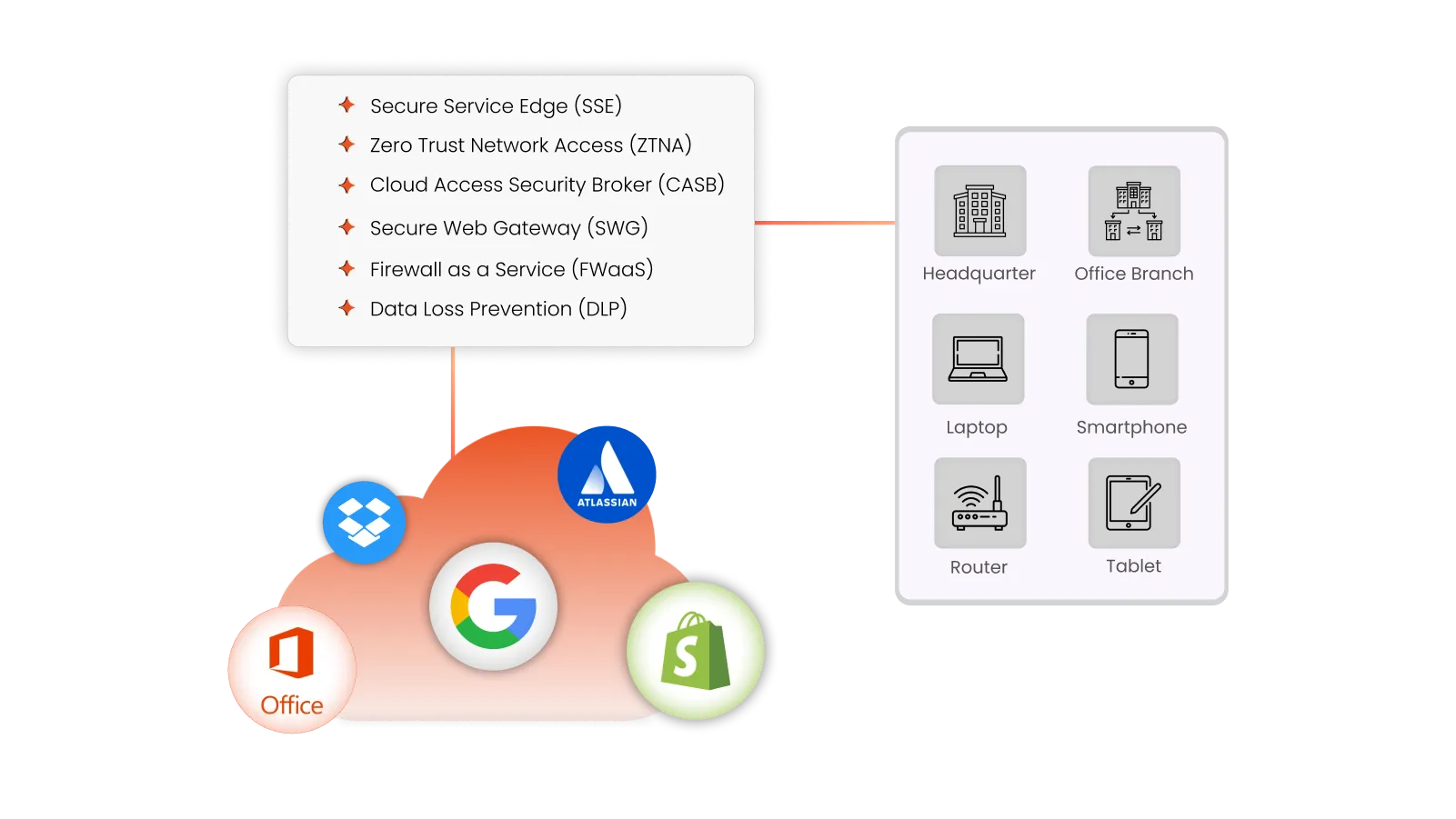
CASB, or Cloud Access Security Broker, is an advanced solution to protect on-premise apps and cloud apps from threat vectors and data breaches to prevent apps from incoming cyber attacks. A CASB continuously monitors all your cloud and on-premise apps to monitor for suspicious user activity, which might be inconsistent with the app usage and potential malware attacks.
CASBs are a standard industry tool for securing data and controlling user access permissions as well. With a CASB in place, you can achieve industry security certifications like HIPPA and GDPR to guarantee data protection.
Let’s see why exactly you need an AWS CASB security solution for your AWS environment.
Why do I need a CASB for my AWS environment security?
Here’s why you need a CASB security solution for your AWS environment:
- Data Breach Protection: AWS CASB is designed to protect and regulate information flow from users and apps. They actively monitor app permissions and user actions to check for potential data breaches when the information flows out of the scope of app security.
- Malware Detection and Threat Protection: AWS CASB defends against malware and software targeting your storage applications to prevent unauthorized data hardening to safeguard from threat vectors over your AWS applications.
- Control User Access Permissions: To control the over-sharing of user access to cloud apps, AWS CASB can monitor and even restrict access to certain AWS services and applications from users in order to control access permissions to prevent data infringement.
- User Risk Score Assessment: For each suspicious user activity, a threat score is assigned to the user profile. Once the user risk score crosses a threshold, all access and permissions are cut off, and now the user won’t be able to access any of the AWS cloud services until authorized by the SOC administrator.
- Generate Security Reports: AWS CASB can generate and display security reports to show threats it protected your AWS services from over a time period. These reports help the SOC teams gain insights and make necessary developments in improving security and boosting company productivity.
- Compliance Inclusion: By being compliant with industry-standard security practices, an AWS CASB ensures your business is safe from threats and that no unauthorized party will ever gain access to your application data stored on the AWS environment.
How does a CASB solution work to secure my AWS components?
Let’s understand how exactly AWS CASB works to secure your AWS applications and services.
Let’s say a company is using an internal use case app hosted on AWS for daily communication and services. The company has enabled an IP restriction security feature with a CASB (Cloud Access Security Broker) and has whitelisted all the IP address ranges of the company network. Suppose now there are 2 users: John and Robert in the organization. John is on the company network and Robert is not on the company network.
The admin can allow or block users with AWS security restrictions.
Since John is on the company network, the AWS CASB solution will whitelist his IP address. Hence, he will be authorized to use the AWS application.
Since Robert is not on the company network, the AWS CASB solution will not whitelist his IP address. Hence, he will not be authorized to access the AWS application.
Conclusion
In this blog, we will discuss how AWS CASB works to secure your AWS environment to safeguard against Malware Attacks and Data breaches. CASB stands as the best security check to find security loopholes, fix overutilization of resources, monitor user actions, provide deep visibility, enable compliance inclusion, and configure custom security rules for user access permissions, data breach, and threat protections.
So if you are on the market looking for an AWS CASB solution to secure your cloud and on-prem apps from malware attacks and other threats. miniOrange is the go-to solution at the most competitive pricing on the CASB market and provides a globally recognized support team in your geolocation.
So what are you waiting for? Shoot us a query at info@xecurify.com and we will get right back to you!
Additional Resources
Check out more solutions from miniOrange,
Author


Leave a Comment