As we enter 2025, organizations are prioritizing their identity security with the best IAM tools. With sophisticated cyber threats, the global IAM market is projected to reach $24.1 billion by 2025. As a result, we need better and more robust identity security solutions that not just protect but prevent.
In this blog, we have compiled a list of the top-notch IAM tools in 2025.
What Are IAM Tools?
Definition and Purpose of IAM Tools
Identity and Access Management (IAM) tools are technologies and processes designed to manage digital identities and control access to critical information and resources within an organization. These tools ensure that the right individuals access the right resources at the right times, enhancing security and operational efficiency.
Role of IAM Tools in Managing Digital Identities and Securing Access to Sensitive Resources
IAM tools play a pivotal role in managing digital identities by:
- Creating, maintaining, and monitoring user identities throughout their lifecycle.
- Enforcing policies to ensure compliance with regulatory standards.
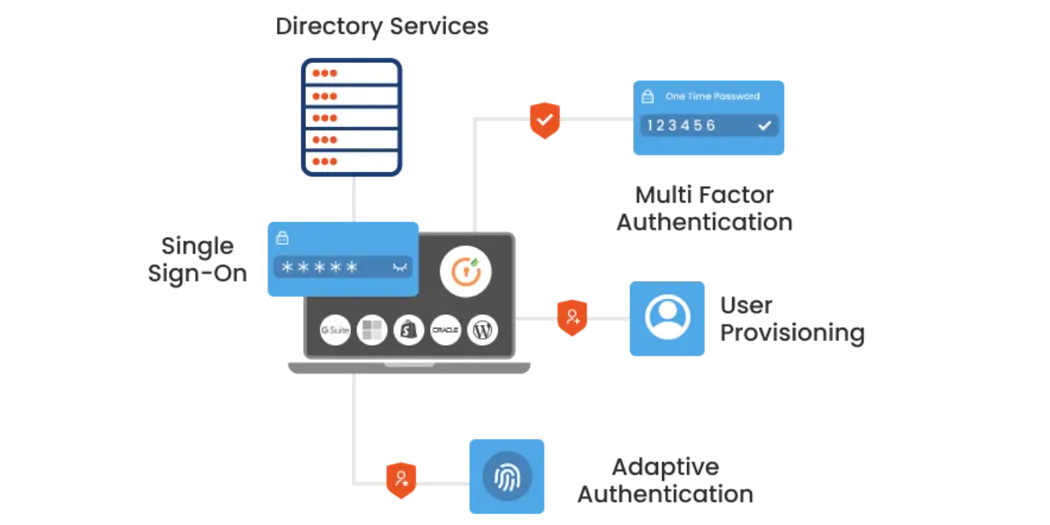
- Providing single sign-on (SSO) capabilities to streamline user access across multiple systems.
In terms of securing access to sensitive resources, IAM tools:
- Implement multi-factor authentication (MFA) to add an extra layer of security.
- Offer role-based access control (RBAC) to restrict access based on user roles.
- Continuously monitor and analyze user activities to detect and respond to potential security threats.
These functionalities help organizations protect their sensitive data and maintain a secure, efficient, and compliant IT environment.
8 Standout Features Every IAM Tool Must Have
- Single Sign-On (SSO): Allows users to authenticate once and access multiple applications without repeated logins, enhancing convenience and reducing password fatigue.
- Multi-Factor Authentication (MFA): Adds a layer of security by requiring two or more verification factors, such as passwords, smartphones, or biometric data.
- Identity Governance and Administration (IGA): Manages user identities through provisioning, de-provisioning, and ensuring compliance with policies and regulations.
- Role-Based Access Control (RBAC): Restricts system access based on user roles, ensuring users have necessary permissions while minimizing unauthorized access. Access Request Workflow Automation: Automates the process of requesting, approving, and granting access to resources, reducing administrative overhead.
- Integration with Cloud and On-Premise Systems: Provides seamless integration with both cloud-based and on-premise systems, maintaining consistent security policies and user experiences.
- Self-Service Features: Allows users to manage passwords, update personal information, and request access to resources without IT assistance, reducing IT workload.
- Reporting and Audit Logs: Provides detailed insights into user activities and security events, enabling organizations to monitor compliance and respond to security incidents.
These features are essential for managing digital identities and securing access to sensitive resources in complex IT environments.
5 Best IAM Tools for Top-notch Identity Security in 2025
miniOrange
miniOrange has been recognized as one of the best IAM tools in Gartner Peer insights and by G2. Its powerful IAM solutions provide high-quality security and outperform the uptime for some of the popular IAM tools on the market.
- Key Features:
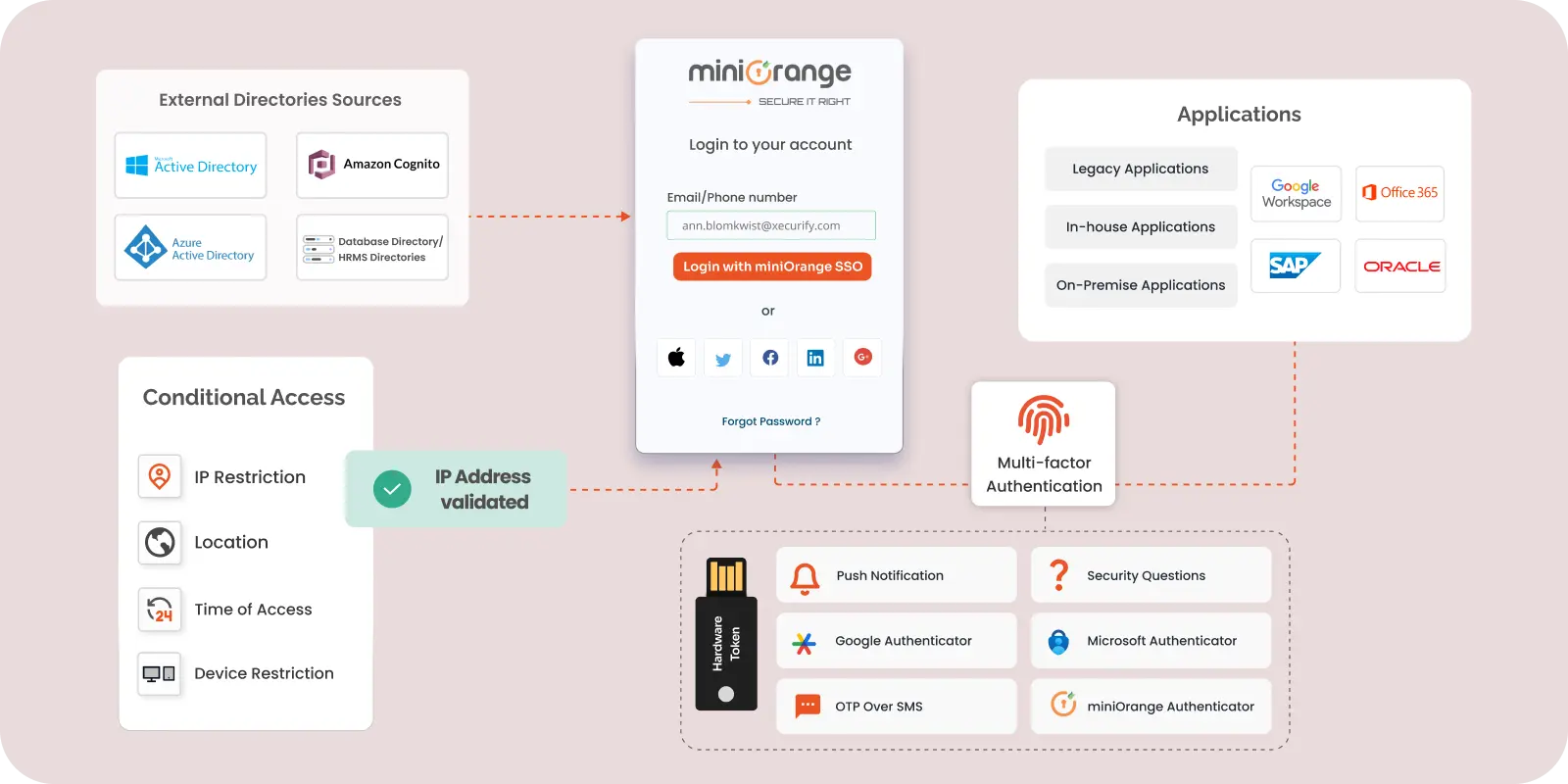
miniOrange IAM tool offers a suite of comprehensive security features. At its identity and access management core, Single Sign-On (SSO) capabilities enable users to securely access multiple applications through a unified login process, while multi-factor authentication (MFA) strengthens security by implementing various authentication methods. The platform stands out with its adaptive risk-based authentication, which dynamically adjusts security measures based on user risk profiles.
The platform excels in modernizing legacy systems through its Legacy Apps Authentication feature, which brings contemporary authentication methods to traditional on-premise applications. Passwordless authentication enhances the user experience by eliminating password-related complexities while maintaining security. miniOrange's versatility extends to its integration capabilities with external directories, including Active Directory, LDAP, and AWS Cognito, making it adaptable to diverse enterprise environments. The implementation of a Zero Trust Security Model demonstrates its commitment to comprehensive security, requiring verification for all users and devices regardless of location.
- Advantages of miniOrange:
Pros include its flexible deployment options, supporting both cloud and on-premises installations to suit various organizational needs. The platform's user-friendly interface simplifies complex security processes, making it accessible for administrators and end-users alike. Its cost-effectiveness compared to other enterprise solutions, combined with responsive technical support, makes it particularly appealing to small, medium-sized businesses as well as enterprises with rare use cases. The solution's scalability ensures it can grow alongside organizational needs with the highest uptime of 99.8%, while its robust compliance features help meet various regulatory requirements.
Okta
- Standout Features:
Okta is a comprehensive identity and access management platform offering essential security features. Its Single Sign-On (SSO) simplifies application access through unified credentials, while Multi-Factor Authentication (MFA) strengthens security with multiple verification layers. The platform automates user lifecycle management through efficient provisioning and deprovisioning capabilities. With over 7,000 pre-built integrations, it seamlessly connects with various applications and infrastructure providers. Okta leverages AI and machine learning through User Behavior Analytics to identify suspicious activities and potential security threats, enhancing its protective capabilities.
- Cons:
Okta has several cons: its complexity can be overwhelming for smaller organizations without dedicated IT support. Additionally, the cost is higher compared to some competitors, which can be a significant barrier. Furthermore, the learning curve requires considerable time and training to fully utilize all features, making it challenging for users to adapt quickly.
OneLogin
- OneLogin Features:
OneLogin offers several features: Single Sign-On (SSO) provides one-click access to all applications, both cloud-based and on-premises. Multi-Factor Authentication (MFA) adds an extra layer of security with various authentication methods like biometrics, OTPs, and personal security questions. Cloud Directory centralizes user management and integrates with on-premises directories like Microsoft Active Directory. User provisioning automates user onboarding and offboarding, ensuring appropriate access rights. Risk-Based Authentication uses machine learning to assess risk and adjust authentication requirements dynamically. Policy-Driven Password Security enforces strong password policies to enhance security. Context-aware security grants access based on user context such as location, device, and behavior.
- OneLogin Benefits:
OneLogin offers several benefits, as it improves productivity by allowing employees to access all necessary applications with a single set of credentials. It enhances security by protecting sensitive corporate data with robust authentication and access control. Additionally, it easily scales with your organization's growth, supporting a wide range of applications and users.
Ping Identity
- Standout Features:
Ping Identity offers standout features such as Single Sign-On (SSO), which enables users to access multiple applications with a single set of credentials, improving productivity and reducing password fatigue. Multi-Factor Authentication (MFA) provides robust security by requiring multiple forms of verification. Passwordless authentication enhances user experience and security by eliminating the need for passwords. AI-Driven Identity Services use artificial intelligence to deliver secure, seamless user experiences. Hybrid and Multi-Cloud Support works across various environments, including cloud, hybrid, and on-premises. Comprehensive Identity Management manages identity and profile data at scale.
- Cons:
Some users find the platform complex to set up and manage, which can be a significant challenge. Additionally, the cost can be prohibitive, especially for smaller organizations that may have limited budgets. Integration with existing systems and third-party applications also requires considerable effort, adding to the overall complexity and potential expense. These factors can make the platform less accessible and more difficult to implement for some organizations.
ForgeRock
- Standout Features/USP:
ForgeRock offers standout features such as a unified platform that combines access management, identity management, user-managed access, directory services, and an identity gateway. It handles identities for users, devices, and things at the internet scale, providing comprehensive capabilities including AI-driven identity and access management (IAM) and identity governance and administration (IGA). ForgeRock offers flexibility with SaaS, self-managed software, and hybrid deployment options. It is trusted by leading global brands like BBC, Toyota, and Philips.
- Cons:
ForgeRock has several cons that organizations should consider. The platform can be complex to set up and configure, especially for first-time users, which may require significant time and expertise. Additionally, ForgeRock is resource-intensive, necessitating substantial resources for full deployment and ongoing maintenance. This can be a challenge for organizations with limited IT resources. Furthermore, there is a steep learning curve for administrators and developers, who may need extensive training and experience to fully understand and utilize all the features and capabilities of the platform. These factors can make ForgeRock a demanding solution for some organizations.
CyberArk Identity Security
- Standout Features:
CyberArk Identity Security offers intelligent privilege controls to secure human and machine identities by enforcing least privilege and continuous identity threat detection. It seamlessly integrates identity security across applications, infrastructure, and data, providing multi-cloud support to protect identities. The platform automates the identity lifecycle, enhancing operational efficiency, and enforces strict authorization controls through a zero trust approach to ensure only authorized access.
- Cons:
CyberArk Identity Security has a few notable drawbacks. Firstly, its deployment and management can be complex, necessitating skilled personnel to handle the intricacies. Additionally, the cost of CyberArk is higher compared to some of its competitors, which might be a consideration for budget-conscious organizations. Lastly, some users have reported challenges when integrating CyberArk with third-party solutions, which can pose difficulties in achieving seamless interoperability.
Benefits of Using IAM Tools
- Better Security: Enhances protection with features like MFA, reducing risks of unauthorized access.
- Operational Efficiency: Automates user management processes, saving time and reducing administrative workload.
- Regulatory Compliance: Ensures adherence to industry standards and regulations, avoiding fines and penalties.
- Improved User Experience: Provides seamless access with SSO and self-service features, boosting user satisfaction.
- Scalability: Grows with your organization, adapting to increasing demands and complexity.
- Centralized Control: Offers unified management of identities and access across all systems, ensuring consistency and control.
IAM tools provide a comprehensive solution for managing digital identities and securing access, delivering significant benefits to your organization.
Choosing the Right IAM Tool for Your Business
- Identify Needs: Assess organization size, industry, and specific IAM requirements.
- Scalability: Ensure the tool can grow with your business.
- Integration: Confirm compatibility with existing systems.
- User Experience: Choose user-friendly solutions with self-service options.
- Security: Evaluate security measures and compliance.
- Cost: Balance budget with required IAM capabilities.
- Vendor Support: Research reputation and support services.
- Trial: Test features and gather internal feedback.
Selecting the right IAM tool enhances security and aligns with business needs. Connect with miniOrange to find the right IAM tool and solution for your business.
The Futures of IAM Tools
- Artificial Intelligence Integration: Enhanced AI and machine learning for advanced threat detection and adaptive security measures.
- Biometric Authentication: Increased use of biometric data (fingerprints, facial recognition) for more secure and user-friendly authentication.
- Blockchain Technology: Implementation of blockchain for decentralized and tamper-proof identity management.
- Zero Trust Security Model: Adoption of zero trust principles, continuously verifying users and devices before granting access.
- Enhanced User Privacy: Greater emphasis on user privacy and data protection, aligning with evolving regulations.
- Unified Identity Management: Consolidation of identity management across cloud, on-premise, and IoT environments for seamless user experiences.
- Automation and Orchestration: More automation in identity governance and administration to reduce human error and improve efficiency.
IAM tools will continue to evolve, addressing emerging security challenges and improving user experience. Let me know if you need more information!
Frequently Asked Questions (FAQs)
1. What are the main security features of the top IAM tools in 2025?
In 2025, organizations are enhancing their Identity and Access Management (IAM) strategies with key security features such as Multi-Factor Authentication (MFA), Single Sign-On (SSO), and Zero Trust Architecture, which collectively reduce unauthorized access risks and streamline the user experience. Advanced capabilities like AI and machine learning integration automate threat detection, while role-based access control (RBAC) and privilege access management (PAM) ensure that access rights are appropriately managed. Additionally, Identity Governance and Administration (IGA) supports compliance processes, and real-time monitoring alerts administrators to suspicious activity. Tools like miniOrange leverage these features to bolster security and enhance the user experience across the organization.
2. How do IAM tools integrate with cloud services like AWS and Google Workspace?
miniOrange offers effective Identity and Access Management (IAM) tools that seamlessly integrate with AWS and Google Workspace. For AWS, it provides single sign-on (SSO) and multi-factor authentication (MFA) for enhanced security, along with automated user provisioning and over 6,000 pre-built integrations. In Google Workspace, miniOrange employs SAML and SCIM protocols for user synchronization, applies MFA for secure access, and centralizes user management from a single console. These integrations lead to improved security, increased efficiency in administrative tasks, and scalability to adapt to organizational growth, ultimately simplifying identity management across both platforms.
3. Which IAM tool has the best integration capabilities with other systems?
miniOrange stands out for its exceptional integration capabilities with over 6,000 pre-built integrations that facilitate seamless Single Sign-On (SSO), Multi-Factor Authentication (MFA), and user provisioning across various applications. This extensive integration ecosystem allows organizations to easily connect both cloud-based and on-premise systems without the need for individual maintenance, streamlining user management. Additionally, miniOrange supports standard protocols like SAML and SCIM, enabling smooth synchronization with external identity providers. Its ability to provide custom connections for legacy applications further enhances its versatility, making miniOrange a top choice for organizations seeking robust IAM solutions with superior integration capabilities.
4. How do IAM Tools ensure compliance with regulations like HIPAA and GDPR?
IAM tools ensure compliance with regulations like HIPAA and GDPR by implementing robust access control policies, identity lifecycle management, and regular audits. These tools facilitate data protection by design, ensuring that user access is managed responsibly and transparently throughout the identity lifecycle, from creation to de-provisioning. Regular access reviews help maintain the principle of least privilege, while automated identity provisioning minimizes human error in granting and revoking access rights. Additionally, comprehensive identity governance frameworks establish and enforce policies related to user management and data protection, which are essential for meeting regulatory requirements and avoiding legal repercussions. Overall, IAM solutions play a critical role in safeguarding sensitive information and maintaining compliance with industry regulations.
5. What are the advantages of using machine learning in IAM tools?
The integration of machine learning in Identity and Access Management (IAM) tools offers several significant advantages. Firstly, it enhances security by enabling proactive threat detection, as machine learning models can analyze user behavior and identify anomalies that may indicate security breaches. Additionally, machine learning automates identity management processes, streamlining authentication and authorization, which reduces the administrative burden on security teams. This technology also facilitates risk-based authentication, allowing IAM systems to adapt access controls based on real-time assessments of user behavior and context. Overall, leveraging machine learning in IAM tools leads to improved security, efficiency, and user experience.
Author



Leave a Comment