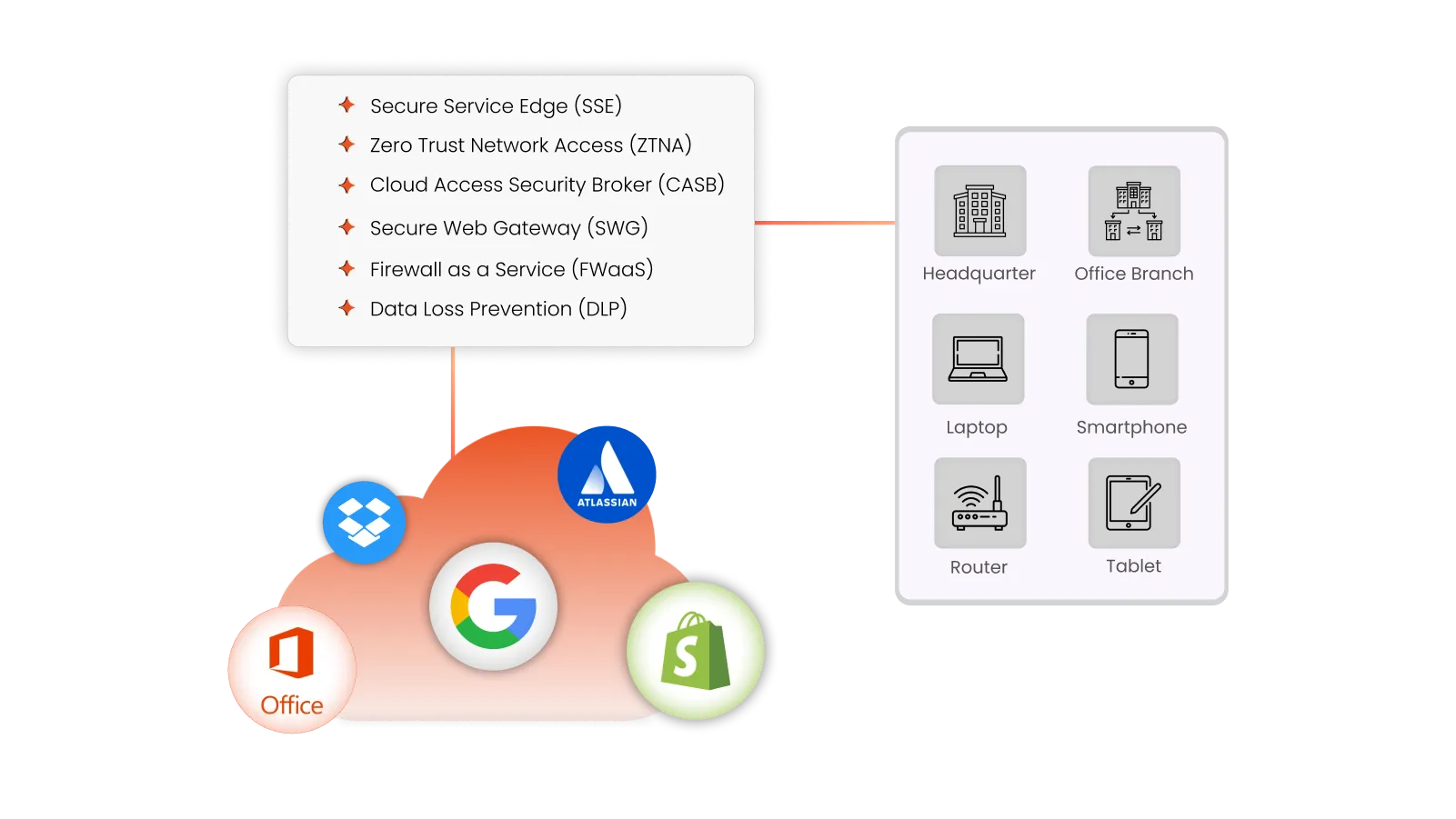
What is Data Loss Prevention (DLP)?
Data Loss Prevention (DLP) is all about keeping your business data safe from getting leaked, lost, or accessed without admin permission. It protects, identifies, analyzes, and blocks unauthorized data transfers within the network and through connected devices and outbound emails. DLP enforces company policies, preventing users from sharing confidential information. It further allows organizations to set USB restrictions to protect sensitive information at every stage of operations.
What is USB blocking or USB endpoint protection?
USB blocking, also known as USB blocker or USB endpoint protection, is a smart way to secure your company data from unauthorized devices and peripherals. It works by controlling access to devices connected through USB ports, such as pen drives, laptops, mobile phones, printers, and docking stations.
Data Loss Prevention (DLP) solution provide USB enable/disable features to allow only whitelisted USBs—whether it’s USB 2.0 or USB 3.0—to access resources and block everything else to protect sensitive data. It protects a wide range of devices and USB connections on your computer, ensuring your data remains intact and secure. It operates by setting up specific rules about how USB ports can be used, allowing organizations to manage their data security better.
Why do organizations need DLP USB blocking?
When it comes to data security, every person in an organization can be a potential risk. USB data leaks are one of the easiest ways insiders can steal critical information. Whether it’s an accidental mistake or a malicious act, anyone inside the organization can use a USB device to transfer important data from a company, causing serious harm to a company’s reputation and client trust.
For example, an insider threat can launch a BadUSB attack where a malicious USB injects harmful software into your network. This can be prevented using endpoint protector USB blockers like DLP solutions that stop unauthorized USB devices from connecting to company systems.
How does USB blocking or USB data protection work?
USB blocking is all about setting rules that determine how each USB port on a computer reacts when an external USB device is plugged in. Essentially, it decides if that device can access or share information with the computer.
Companies often use DLP systems to whitelist or blacklist devices, manage access policies, and block USB ports in Windows to control usage effectively.To keep track of what's happening, companies maintain records of USB usage and can physically block ports if needed. These steps help stop data theft, protect against malware, and ensure they’re following data protection laws. Overall, USB data protection is crucial for keeping an organization safe.
What are the Benefits of USB Blocking with DLP?
USB blocking can help organizations in several important ways:
1. Monitor USB Usage : Organizations can track how USB drives and other peripherals, like laptops and smartphones, are connected to their systems. This means they can see who accessed each drive, what actions they took, and when and where these activities occurred.
2. Spot Unusual USB Activity : If there’s an unexpected increase in file transfers to USB drives, organizations get instant email alerts. This proactive feature can even block USB ports to prevent any risky actions, ensuring that everything stays under control.
3. Prevent Data Theft, Loss, and Leaks : To protect sensitive business information, companies can restrict users from copying important files onto USB drives. This significantly lowers the risk of data leaks and keeps confidential information safe.
4. Safe Mode Protection : When a computer is in Safe Mode, the USB blocking solution can stop unauthorized devices from connecting. Authorized devices can still connect normally, providing a layer of safety during these vulnerable times.
5. Block Malware : USB devices can be carriers of harmful viruses that could infect business networks. By blocking these devices, organizations protect their systems from dangerous software, ensuring a healthier IT environment.
6. Protect Sensitive Data : USB blocking safeguards sensitive information, like Personally Identifiable Information (PII) and Intellectual Property (IP). This prevents unauthorized access and helps maintain data confidentiality.
7. Time-bound Exceptions : Organizations can set specific time frames for when an employee is allowed to use the USB devices. This allows for better control over when sensitive data can be transferred or viewed. It also monitors and logs every activity that is happening, adding another layer of data security.
8. Prevent Unauthorized Transfers : USB drives make it easy to transfer large amounts of data. Without restrictions, employees might accidentally or intentionally move confidential information, which could lead to serious data breaches. USB blocking helps prevent this.
9. Granular Control : Organizations can create detailed policies regarding USB device use. This means they can customize security measures to meet their specific needs, ensuring that they have the right level of protection for every situation.
Features of USB Block Solutions:
USB Whitelist A USB whitelist is a smart way to boost security by allowing only certain approved devices to connect to your system. By limiting access, you can keep pesky malware and unauthorized data transfers at bay. Only trusted devices can touch your important information, so you can rest easy knowing that your data is safe from unwanted intruders.
USB Device Management Good USB device management helps organizations keep track of all USB devices connected to their networks. With good management, you can monitor how these devices are used and enforce your security policies. Plus, it allows you to automate regular checks, which is essential for protecting against data breaches. This proactive approach not only secures your data but also helps ensure you stay compliant with industry regulations.
Which endpoints are protected with USB blocking?
USB blocking can be done in two ways:
1. USB & Peripheral Port Control : This method disables USB ports entirely, preventing all USB devices from being used. This includes things like USB drives, external hard drives, printers, and more. When USB ports are blocked, employees can’t transfer data or communicate through those ports, which boosts security. It helps prevent risks like unauthorized data transfers, malware infections, and other security threats that come from using removable storage.
Here’s the list of peripherals it supports:
- Desktops and Laptops : These are the most common devices for USB blocking since employees often use them. They usually have several USB ports, making them easy targets for data breaches.
- Mobile Devices : USB blocking can also apply to work smartphones and tablets. This keeps sensitive data safe, especially when employees are working remotely.
- Servers : Blocking USB ports on servers is crucial because they store sensitive information. If someone connects an unauthorized USB device, it could lead to serious security problems.
- Point of Sale (POS) Systems : In retail, POS systems can be targets for cybercriminals. USB blocking protects transaction data and customer information by stopping unauthorized data transfers.
2. Access Restriction : This involves setting rules for how USB ports can be used based on an organization’s policies. Access Restriction can be further categorized into multiple types:
- Write Access Restriction : This prevents users from copying or saving data to USB drives. So, users can’t transfer data from their computers to USB devices.
- Read Access Restriction : Sometimes, organizations block users from reading data from USB devices. This stops unauthorized data extraction.
- Device Class Restriction : USB devices fall into different categories, like storage devices, printers, or keyboards. With this restriction, organizations can block certain types of devices to avoid data leaks. For example, they might stop mass storage devices from connecting.
- Device Whitelisting : Here, only approved USB devices can connect to a computer. If a device isn’t on the list, it gets blocked.
- Device Blacklisting : This is the opposite of whitelisting. Organizations can create a list of specific USB devices that are not allowed, and any device on that list is blocked from connecting.
- Time-Based Access Restrictions : Some USB-blocking solutions let organizations set specific times when USB devices can or cannot connect. This gives them more control over USB access.
Conclusion
Blocking USB devices helps reduce risks from unauthorized storage and malware, giving organizations more control over their data flow. Data Loss Prevention (DLP) solutions make it easy to put this security measure in place.
With an endpoint protector USB blocker solution like DLP, companies can keep an eye on USB activity, ensure compliance, and protect against data theft. On top of that, USB blocking can boost productivity. It prevents distractions, stops unauthorized software from being installed, and lowers the chance of system disruptions from malware-infected devices.
That said, it’s important to apply USB blocking carefully, keeping the company’s needs in mind. Striking the right balance between security and usability is key—too much control can frustrate employees or slow down business operations.
Additional Resources
Author


Leave a Comment