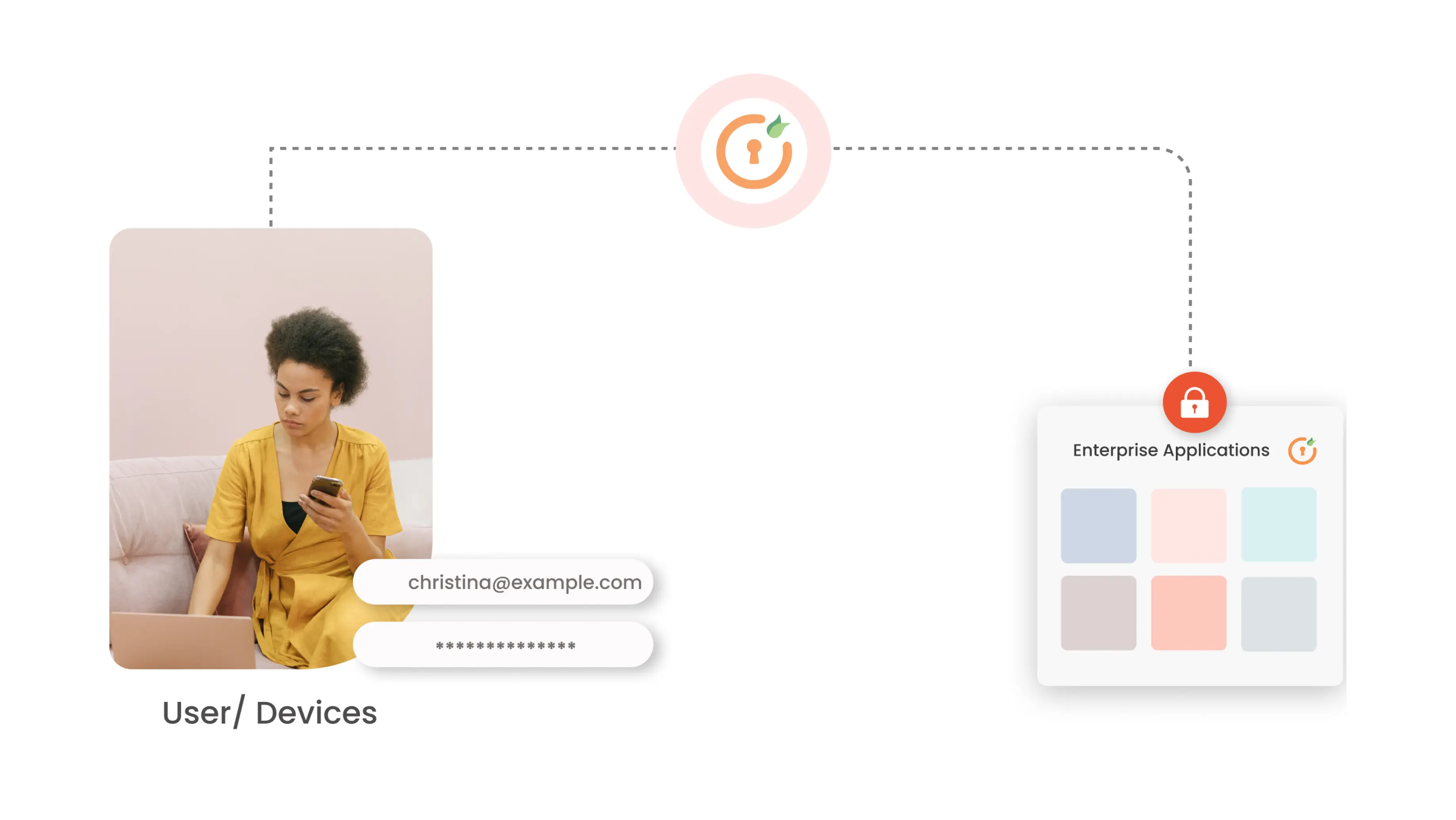
Enterprise SSO is a Single Sign-On solution that enables the end-users to securely access all of the enterprise’s applications with a single click. It allows users to access multiple applications on cloud or On-premise platforms with a single sign-in prompt, without compromising on the security.
Also, it enables enterprises to strengthen their security measures by implementing 2FA or Adaptive MFA for added security.
Enterprise SSO Solution allows enterprises to set up one-click access to all of their enterprise applications for their users.
Need for Enterprise SSO?
Typically, a user needs to access multiple applications simultaneously for their daily tasks. Re-entering Login credentials to every application for signing in can be a time-consuming task and reduce productivity. Also, Managing separate login credentials for multiple tasks can be tedious and overwhelming at times.
This often leads to users using the same login credentials for multiple applications or having weak passwords. This gives rise to security issues/vulnerabilities and defeats the purpose of having login credentials. An estimated 81% of data breaches are due to poor password security or stolen credentials.
Employee management can be made easy using Enterprise SSO. User restriction with SSO can also be enabled by the administrator.
Benefits of Enterprise SSO
SSO Solutions ensures improved user Experience and productivity without compromising security.
- Security - As users need to remember only a single set of login credentials for accessing all of the enterprise’s applications, they can have complex passwords. These passwords will be hard to guess and will reduce the risk of a security breach. Enabling 2FA or Adaptive MFA further will further add to the security, reducing the risk of a security breach.
- Improved User experience - Users can access all Cloud and On-Premise applications of the enterprise with a single sign-in prompt, reducing time spent re-entering login credentials for each application. Also, it ensures time spent re-entering passwords to each of the applications and boosts productivity.
- Access Privilege - Privileged Access to critical systems can be managed for various user groups, allowing access only to the applications or within the applications that are required by the user. It reduces the risk of a particular user group accessing critical systems, which increases the security for our critical system and its data. It reduces the load on system administrators to have a check on everything for the restricted user group.
- Audit Reports - Audit report gives detailed logs of login and access requests to the various applications and resources that can be used to identify resource access requests and usage. and analyze suspicious activities.
- Eliminating help desks - Username, Password, and access management can be easily ensured with help of enterprise SSO eliminating the need for help desks in the organization and ensuring a smooth user experience.
How Enterprise SSO works?
An SSO system can be divided into the following 2 components.
Identity Provider (IDP) – it is a digital service that creates and manages a user’s digital identity and identity attributes.
Service provider (SP) – It is a digital service that receives and accepts Authentication assertion from the Identity Provider (IDP).
SSO works on the basis of a trust relationship between the Service provider and Identity provider. This Trust is established by exchanging certificates between the SP and IDP. Different Authentication protocols like SAML, OAuth, OpenID etc. can be used to validate user credentials and authenticate users, but they all follow the same basic underlying pattern, Identity Provider (IDP) provides signed authentication assertion to Service Provider (SP), and the Service provider validates the authentication based on the trust relationship with the IDP.
These assertions are small collections of information in a structured order and do not contain any of the user credential data like username, passwords, etc. This way users get authenticated to the Service provider without sharing their credentials.
When a user tries to login into an application, they are prompted to sign in using the login credentials, if they are not already logged in. Once the user is logged in, a session is created in the IDP. Now, when a user navigates to any of the remaining applications, they are logged into the remaining applications without being prompted to log in using the existing session. Thus SSO improves user experience, helps boost productivity, and reduces time spent re-entering login credentials to each application.
SSO solution also improves user experience from system administrator/manager as its providers are a one-stop solution for managing User ID and application access to the user.
Let’s take an example for better understanding of how SSO Solution improves user experience and management. Let’s say
Sam is a system administrator in ABC Enterprises, with an SSO solution in place for all their enterprise applications and services. A new employee, Jane, joins the organization, and Sam is responsible to help new users set up accounts for company applications, and grant or revoke access to various applications to existing users.
With the SSO solution, Sam can easily create a user Id for Jane in the organization’s SSO solution and grant her access to required applications. Using this user ID Jane can easily login into any of the allowed applications with a single login prompt. Once logged in, Jane can view all applications from her user dashboard and simplify login into other applications from the dashboard, or by navigating to the application URL. Jane’s login experience with the SSO solution will look like this:
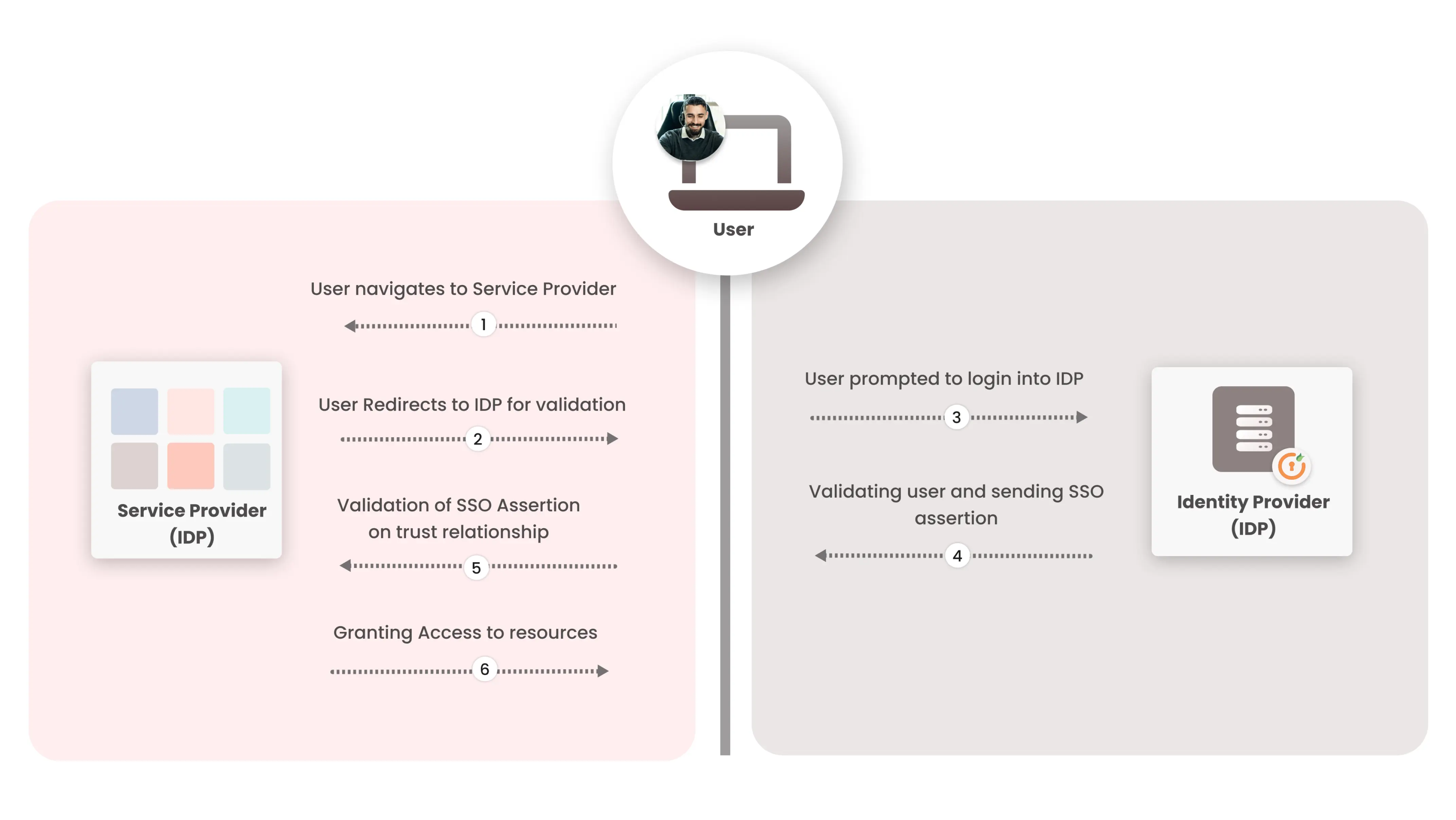
- Jane navigates to the Application she wishes to login into.
- The application/Service Provider redirects her to Identity Provider for authentication.
- As Jane is not already logged in, she is prompted to login using her login credentials.
- If 2Fa or MFA has been enabled for the SSO, Jane will be prompted for the OTP or other configured secondary authentication.
- Once the Identity provider validates the user Id, it sends back the SSO assertion confirming the validation to the Service Provider.
- Service providers validate the assertion received from the IdP (on the basis of the trust relationship) and grant Jane access to the resource or application.
- Now the user can access all the other applications/websites from the Service Provider configured for SSO.
If at a later stage Jane leaves the company, Sam is responsible for revoking her access from all of the applications. Sam can easily do so by deleting here User ID from the SSO user list. This way Sam can easily manage application access for users from granting access to any application to revoking access to all applications from a single stop.
Setting up SSO for your enterprise
The process of Setting up SSO varies based on user requirements and associated applications, but with a vast library of 5000+ pre-integrated apps, customization, and support for all SSO protocols, the miniOrange IDP solution is a beneficial choice. Few of the reason that makes it an optimal choice for Enterprises are:
- Inbuilt integration with Legacy Apps such as Active Directory, Siteminder, Unix, RADIUS, etc.
- Support for OpenID, OAuth, SAML, ADFS and WS FED protocols.
- Support for remote Logins such as Radius VPN, Website Protection, ADFS, Windows, Citrix
- The solution is not limited to corporate apps only, you can add your own personal apps.
- Both Cloud and on-premise hosting can be ensured according to your use case.
You can create a free trial account with miniOrange to test the SSO solution from here.
Author





Leave a Comment