Although the terms Federated Identity Management (FIM) and Single Sign-On (SSO) are frequently used interchangeably, they are not similar. Single sign-on enables access to apps and resources within a single domain. Federated identity management enables Single Sign-On (SSO) into applications across multiple domains or organizations.
What is Federated Identity Management (FIM)?
Federated Identity Management (FIM) is a structure between organizations or organizational domains that allows users to access multiple networks with the same credentials (digital identity). Simply put, FIM is a single login, multiple-access method. For example, a domain can refer to a business unit, a smaller subsidiary, or a small company (small, medium, or large).
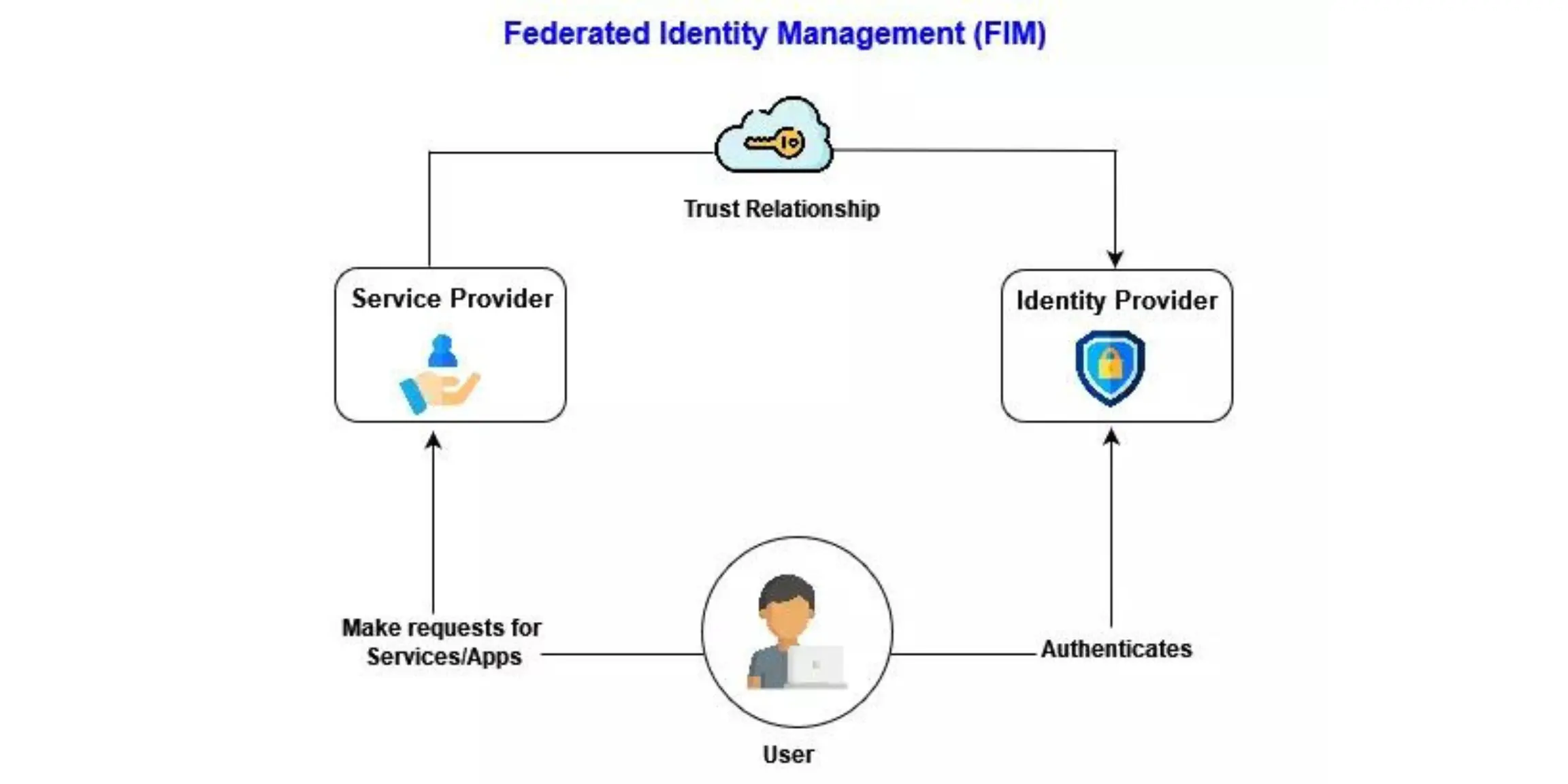
For FIM to function properly, all domains involved must have mutual trust. Each domain has its own identity management system. On the other hand, all interconnected domains are linked to a centralized third-party platform that stores and manages user access credentials and establishes the trust relationships required for FIM to function. We’re talking about a third-party platform, also known as an Identity Provider or Identity Broker. This Identity Provider/Broker controls access to a variety of service providers (here domain). An FIM structure does not have to have only one Identity Provider. The Federated Identity Management arrangement can be formed across the enterprise by several Identity Providers/Brokers.
Federated Identity Management is a service that connects users’ identities across several domains. Users will only need to authenticate on one domain once these two domains are federated. The reason for this is that the FIM system includes a second security domain that trusts the users’ first (Primary) domain authentication and grants them unrestricted access.
OpenID, OpenAuthorization, and Shibboleth are part of the Federated Identity Management (FIM) system, which is based on the Organization for the Advancement of Structured Information Standards like SAML (Security Assertion Markup Language).
How does federated identity management work?
FIM works in a way, considering there are three security Domains (A, B, and C) and a unified Identity provider integrated with an FIM structure. User credentials are stored and managed by the Identity Provider, which is the home domain. Now when a particular user tries to log into any of the service provider Domain services (A,B,C), they don’t have to provide credentials to the service provider (A,B,C). Instead, the Identity provider authenticates the user, and all service Providers trust IDP to validate these credentials and provide them access.
The process of FIM here is possible because FIM partners (A,B,C) send each other authorization messages. These messages can be transferred using SAML or any similar sort of Extensible Markup Language Standard.
What are common federated identity management use cases?
When administering applications that require access to resources across various security domains, the requirement for FIM arises.
Here are a few examples of how FIM might be used:
- New users are added to the system after a merger or acquisition.
- External partners or vendors want access to organizational resources.
- Users from a commercial identity provider or a government agency.
- If the user’s credentials come from a national identity provider.
What is SSO?
Single Sign-On (SSO) is an authentication process in which a user is provided access to multiple applications and/or websites by using only a single set of login credentials (such as username and password). This prevents the need for the user to log separately into the different applications.
The user credentials and other identifying information are stored and managed by a centralized system called Identity Provider (IdP). The Identity Provider is a trusted system that provides access to other websites and applications.
Single Sign-On (SSO) based authentication systems are commonly used in enterprise environments where employees require access to multiple applications/websites of their organizations. In this scenario, the Single Sign-On service provider uses the organization’s directory, such as Microsoft Active Directory, Azure Active Directory, or a directory provided by the Single Sign-On solution itself for authenticating users and providing access to the various applications/websites.
What is the difference between SSO and FIM?
Single Sign-On (SSO) is an important component of FIM, but it is not the same thing as FIM. Although there is no necessity for Federated Identity Management when configuring SSO, FIM significantly relies on SSO implementation to authenticate users across domains.
The main distinction between SSO and FIM is that whereas FIM provides single access to several applications across various organizations, SSO is meant to authenticate a single credential across diverse systems within one organization.
SSO allows users to access numerous systems inside a single organization using a single set of login credentials. SSO is a token-based authentication system, which means that instead of a password, users are identified by a token.
The Federated Identity Management System allows users to access applications, services, and networks that are federated in a group using the same credentials. SSO allows a user to log into numerous apps within the same organization with a single set of credentials. FIM, on the other hand, allows users to access many apps and systems across multiple enterprises in a single step.
Unlike SSO, FIM sends credentials to the FIM system, which is a home domain identity provider, rather than to a web application.
What are the benefits and drawbacks of federated identity management?
FIM (Federated Identity Management) has its own benefits and drawbacks.
Benefits of FIM:
When numerous companies collaborate on a project, FIM makes it simple for everyone involved to exchange and access resources across all domains. It also streamlines the organization’s authentication and authorization process. Integrating FIM does not imply that all federated domain administration will be managed by a single administrator. Each organization’s administrators can still manage access to their own domains. Federated Identity Management System allows a single user to define permissions and access levels across multiple systems in multiple security domains.This streamlines identification and access management operations while reducing their workload.
FIM also addresses all of the challenges that frequently develop and impede users from quickly gaining access to the resources they demand. Users benefit from the FIM Login system because they can safely access systems across domains without having to log in multiple times. FIM helps users save time, reduce login friction, and increase productivity in an indirect way.
FIM aids in the simplification of data administration, privacy, and compliance, as well as the reduction of storage costs.
Drawbacks of FIM:
One of the most significant disadvantages of FIM is the cost of implementing and modifying current systems and applications. Another issue that federation members face is that they must develop policies that meet the security needs of all federated members. Negotiation can be difficult and time-consuming in order to reach a final conclusion, as each organization has its own set of needs and rules.
Another issue that may arise is that if a participating organization is a member of one or more federations, its policies should reflect each federation’s regulations and criteria.If a corporation joins many federations, this becomes considerably more complicated and time-intensive.
FIM service by miniOrange
As one becomes more familiar with FIM technology, the question of which firms provide the finest FIM services emerges. There are many, but choosing the best Federated Identity Management service provider can be difficult.
So, in order to arrive at a specific conclusion, you must consider a few key factors.
This includes the following:
Flexible Pricing: Because implementing an FIM can be costly, you should choose a solution that handles pricing based on your needs and requirements.
Multiple Structured Information Standards (SAML, Open ID, etc.) are supported, giving your architecture a lot of flexibility.
Technical Support: Because FIM can get a little complicated at times, you’ll need reliable, fast help if you get stuck in the middle of integration or run into any other issues.
Multiple IDP support: As previously stated, the Federated Identity Management system is all about managing Identity Providers, thus when choosing a service, make sure the FIM service provider you choose has a good stock of IDP support.
In light of all of these factors, miniOrange is a top-tier security solution that has been offering IAM and Federated Identity Management services for many years.
If you have any doubts or questions about FIM, How is it Implemented? What will be the cost to implement for your organization? What will the technical implementation look like? Feel free to reach us at idpsupport@xecurify.com. We will help you out in the best way possible.
Further Reading
Author




Leave a Comment