FIDO stands for Fast Identity Online. It is a compliance protocol that uses Public Key Authentication with asymmetric cryptography. FIDO compliance offers users the advantage of passwordless login experiences across various devices. This approach not only enhances security but also speeds up the login process. By adopting this futuristic method, users can enjoy a seamless and improved login experience.
Why FIDO2?
The Problem of Weak Passwords and Data Breaches
Weak passwords are a major vulnerability, leading to frequent data breaches. FIDO2 addresses this by eliminating passwords altogether and using strong cryptographic keys for authentication. This significantly enhances security, making it much harder for attackers to gain unauthorized access. It's a game-changer in the fight against cyber threats.
FIDO2 and its Importance
FIDO2 is a groundbreaking authentication standard that eliminates the need for passwords, using strong cryptographic keys instead. This enhances security by making it extremely difficult for attackers to gain unauthorized access. Its importance lies in
- Providing a more secure,
- User-friendly, and
- Scalable solution for online authentication.
It significantly reduces the risk of data breaches.
What is FIDO2 and How Does It Work?
Defining FIDO2 and its Core Components
FIDO2 (Fast IDentity Online 2) is an open standard for user authentication that aims to eliminate the need for passwords by using strong cryptographic keys. This enhances security and user experience by making it extremely difficult for attackers to gain unauthorized access.
Core Components of FIDO2:
1. WebAuthn: A web standard published by the World Wide Web Consortium (W3C) that defines a standard web API for creating and using strong, attested cryptographic credentials in web applications.
2. CTAP (Client to Authenticator Protocol): A protocol developed by the FIDO Alliance that allows external devices (like security keys or smartphones) to communicate with a client (like a web browser) for authentication purposes.
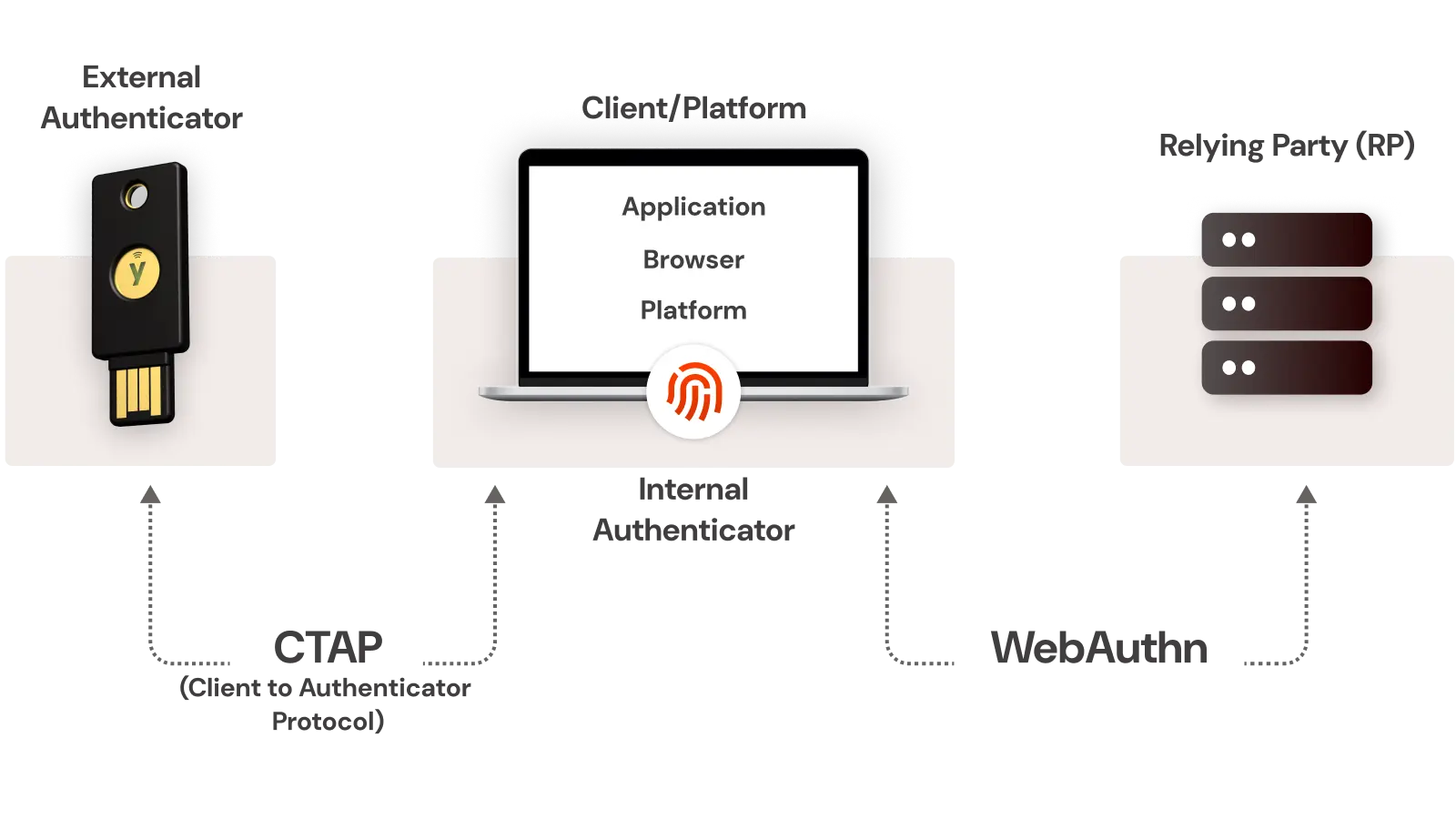
The FIDO Alliance, a consortium of tech giants including Microsoft, Google, and PayPal, along with the World Wide Web Consortium (W3C), are the primary organizations behind the development and promotion of FIDO2.
FIDO2 has set a benchmark for online authentication by providing a more secure, user-friendly, and scalable solution.
Public Key Cryptography and FIDO2 Authentication Process
Public key cryptography uses a pair of keys—one public and one private—to encrypt and decrypt data, ensuring secure communication. FIDO2 authentication enhances security by using hardware-based authenticators and public key cryptography to verify user identity without relying on passwords. This combination provides a robust defense against phishing and other cyber threats.
Types of Authenticators (Built-in vs. External)
Choosing the right authenticator depends on the balance between security and convenience. For everyday use, built-in authenticators like biometrics are great. For high-security needs, external authenticators like hardware tokens are preferable.
Built-in Authenticators
1. Biometric Authentication: Uses unique biological traits like fingerprints, facial recognition, or iris scans. It's highly secure and convenient since it's integrated into devices like smartphones and laptops.
2. Password/PIN: Traditional method where users enter a secret code. It's simple but less secure due to vulnerability to attacks like phishing and brute force.
3. Device-based Authentication: Utilizes the device itself as an authenticator, such as a trusted device or a hardware token embedded in the device.
External Authenticators
1. Hardware Tokens: Physical devices like USB keys (e.g., YubiKey) that generate a one-time password (OTP) or use cryptographic keys. They offer high security but can be inconvenient to carry around.
2. Software Tokens: Apps like Google Authenticator, Microsoft Authenticator, miniOrange Authenticator, and Authy that generate OTPs. They are convenient and secure but rely on the security of the device they are installed on.
3. Smart Cards: Physical cards with embedded chips used for authentication. They are secure and often used in corporate environments but require card readers.
4. SMS/Email OTP: Sends a one-time password to the user's phone or email. It's easy to use but less secure due to risks like SIM swapping and email hacking.
Key Differences
| Aspect | Built-in Authenticators | External Authenticators |
|---|---|---|
| Convenience | Highly convenient, integrated into devices | May require additional hardware or steps |
| Security | Generally secure, but varies (e.g., passwords are less secure) | Typically higher security, especially hardware tokens |
| Usability | User-friendly, no extra devices needed | Might need users to carry additional hardware |
FIDO2 and Biometric Authentication
FIDO2 is an open authentication standard that enables passwordless login using biometrics or security keys. It combines the WebAuthn API and CTAP protocol to provide strong, phishing-resistant authentication. Biometric authentication in FIDO2 leverages unique physical characteristics like fingerprints or facial features for user verification. This approach enhances security by eliminating password-related vulnerabilities and improving the user experience. FIDO2 with biometrics is increasingly adopted by major platforms and services to strengthen identity protection.
FIDO2 vs. FIDO vs. WebAuthn
| Aspect | FIDO | FIDO2 | WebAuthn |
|---|---|---|---|
| Purpose | Authentication standard for passwordless login | Improved version of FIDO includes WebAuthn | Web standard for passwordless authentication |
| Year Introduced | 2013 | 2018 | 2018 |
| Passwordless | Yes | Yes | Yes |
| Biometric support | Limited | Yes | Yes |
| Browser integration | No | Yes | Yes |
| Hardware token support | Yes | Yes | Yes |
| Web compatibility | Limited | Yes | Yes |
| Mobile compatibility | Yes | Yes | Yes |
| Desktop compatibility | Limited | Yes | Yes |
Benefits and Use Cases of FIDO2
Advantages of FIDO2
- Significantly improves security by eliminating password-related vulnerabilities as passwords are not involved.
- Enhances user experience through faster, easier logins
- Reduces costs associated with password management and resets
- Protects user privacy by keeping biometric data on the user's device
FIDO2 Use Cases and Case Studies
Major tech companies like Google, Microsoft, and Facebook have implemented FIDO2 for secure, passwordless logins. Banks and financial institutions, including Bank of America, PayPal, and Mastercard, use FIDO2 to reduce fraud and enhance security. Government agencies, such as the UK government and the U.S. Department of Defense, have adopted FIDO2 for secure access and data protection. Popular email providers, e-commerce platforms, and social media sites are also integrating FIDO2 to improve security and streamline user experiences.
Challenges in FIDO2 Adoption and Future Trends Forecast
Challenges in Adoption of FIDO2
1. One of the key challenges in FIDO2 adoption is the need for widespread user education, as many individuals may be unfamiliar with the concepts of passwordless authentication and the benefits it offers.
2. Integrating FIDO2 authentication across diverse hardware and software platforms can be complex, requiring coordination between various vendors and service providers to ensure seamless implementation.
3. Robust backup and account recovery mechanisms are essential for FIDO2 adoption, as users may lose their security keys or face other device-related issues, necessitating a reliable and user-friendly process to regain access to their accounts.
4. Regulatory and compliance requirements may vary across different industries and regions, making it necessary for organizations to carefully navigate the landscape and ensure their FIDO2 implementation aligns with relevant standards and guidelines.
5. As FIDO2 gains momentum, future trends may include the integration of biometric authentication, such as fingerprint or facial recognition, to provide an even more convenient and secure user experience, while also addressing potential concerns around the storage and privacy of biometric data.
Innovative Trends in FIDO2
FIDO2 adoption is expected to grow rapidly as more organizations prioritize passwordless authentication. New FIDO2 use cases will emerge in IoT, with secure device onboarding and management. FIDO2 will integrate with blockchain technologies to enable decentralized identity and access control. Mobile devices will increasingly leverage FIDO2 biometrics for seamless authentication across apps and services. Enterprise cloud services will widely adopt FIDO2 to enhance security and user experience. FIDO2 will enable secure, standards-based passwordless login for web applications.
Governments will leverage FIDO2 to modernize digital identity programs and e-services. The integration of FIDO2 with smart home and building automation systems will improve IoT security. Cryptocurrency exchanges and DeFi platforms will utilize FIDO2 to protect digital assets. Widespread FIDO2 deployment will drive the decline of legacy password-based authentication.
FIDO2 Implementation and Adoption
FIDO2 Implementation Steps
Implementing FIDO2 is essential to elevate security and achieve passwordless security. These are the steps to implement it for enterprise applications.
1. Assess Compatibility: Ensure your website or application is compatible with the FIDO2 standard by checking the technical requirements and supported features.
2. Enable FIDO2 on Popular Websites: Implement FIDO2 authentication on popular websites and platforms that offer this functionality, such as Microsoft, Google, and social media platforms.
3. Choose Authenticators: Select the appropriate FIDO2 authenticators, such as security keys, biometric readers, or mobile devices, based on your users' preferences and security needs.
4. Integrate FIDO2: Integrate the FIDO2 authentication flow into your application's user registration and login processes, following the recommended implementation guidelines.
5. Educate Users: Provide clear instructions and guidance to your users on how to set up and use FIDO2 authentication for a seamless experience.
6. Monitor and Maintain: Regularly monitor the FIDO2 implementation, address any issues, and keep up with the latest updates and best practices.
How Can FIDO2 Improve Online Life?
FIDO2 eliminates the need for passwords, improving security and convenience by using biometrics or security keys for authentication. It protects against phishing and other credential theft attacks, as it uses cryptographic keys that cannot be replicated. Also, it increases privacy by keeping personal biometric data local on the user's device without sharing it with websites.
FIDO2 dispels the misconception that strong security is difficult, as it offers a simple, user-friendly authentication experience. Additionally, it addresses fears about losing access to accounts, as users can easily recover access by registering new security keys. It encourages adoption by being an open standard, with support from major tech companies and widespread integration across online services. FIDO2 enhances online life by providing a seamless, secure authentication experience that reduces the burden of managing numerous passwords.
Begin your journey in creating passwordless login experiences with miniOrange. Explore miniOrange passwordless authentication solutions today.
Author



Leave a Comment