In a world where cyber threats are growing and compliance demands are becoming stricter, companies worldwide must put together robust Identity and Access Management (IAM) strategies in place. IAM solutions offer a holistic toolkit to safeguard sensitive data, streamline user access, and boost security without disrupting workflows. This blog explores the essential IAM features, their real-world benefits, and how they empower businesses to stay secure and efficient in today’s digital landscape.
Key IAM Features Every Business Needs
Discover the essential IAM features that play an important role in safeguarding your organization’s digital assets and ensuring seamless, secure access for users:
Single Sign-On (SSO)
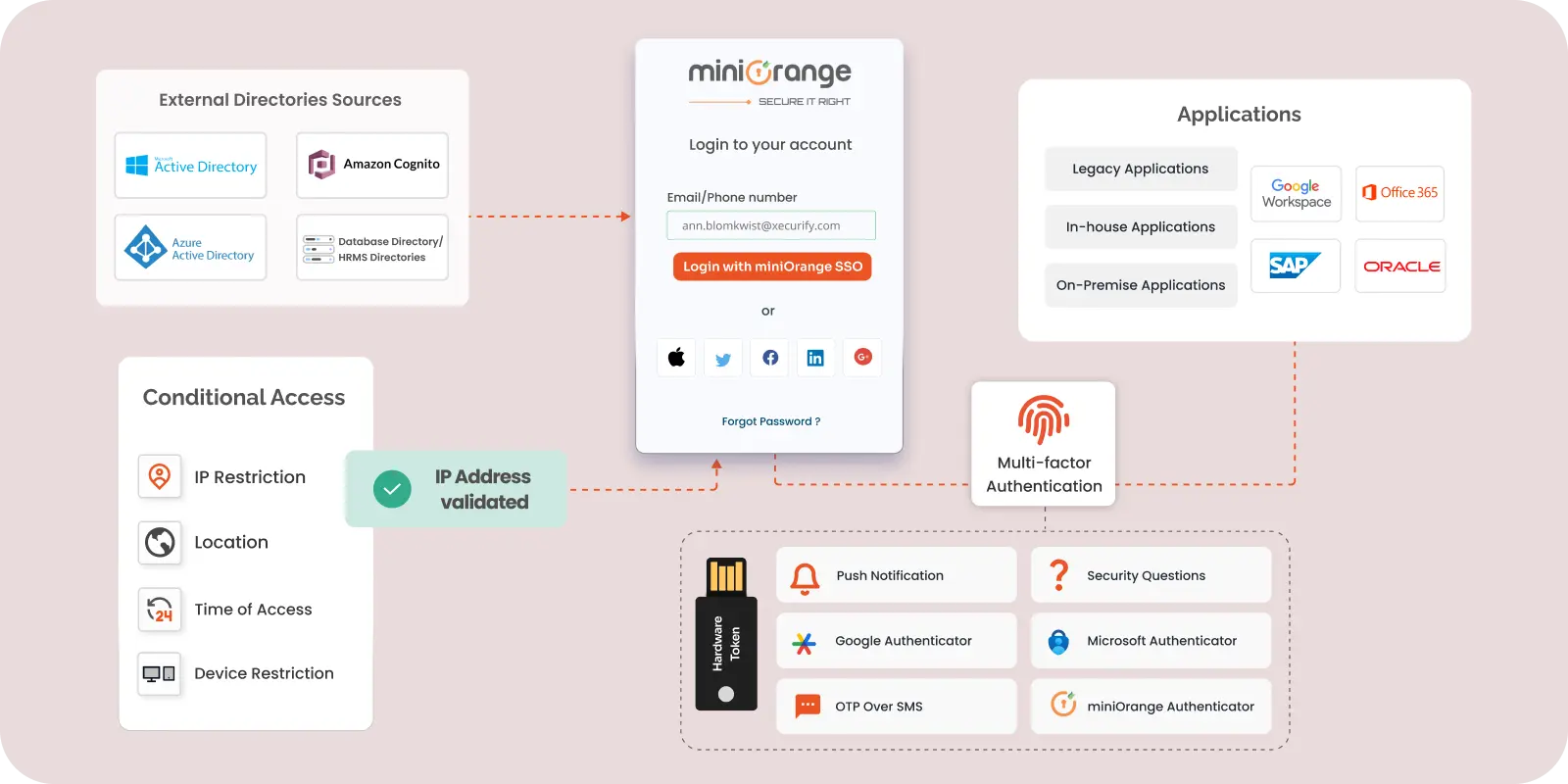
Single Sign-On (SSO) works like a master key for your digital tools. With just one login, users can unlock access to multiple applications without needing to log in repeatedly. This not only saves time but also makes work more seamless and productive.
A user logs in once and gains access to multiple interconnected applications without needing to log in again.
- Supports protocols like SAML (Security Assertion Markup Language), OAuth OpenID, and JWT.
- Reduces credential theft risks and enforces centralized authentication policies.
Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) adds an extra layer of security to ensure that only authorized users can access sensitive systems. Think of it as double-checking your identity as only relying on a password isn’t enough. MFA combines at least two factors(or more). MFA drastically reduces the risk of unauthorized access, even if passwords are compromised.
- Something you know: Like a password or PIN.
- Something you have: Such as a one-time passcode sent to your phone or an authenticator app.
- Something you are: Biometric data like a fingerprint or face scan.
All the above makes it much harder for attackers to gain access, even if they steal your password.
- Adaptive MFA adjusts security requirements based on risk factors like location or behavior.
- Complies with industry standards through compliances like GDPR, PCI-DSS, and HIPAA.
- Protects against threats like phishing, credential theft, and brute-force attacks.
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a security mechanism that assigns access permissions based on a user’s role within an organization. Think of it as tailoring access to fit responsibilities—managers and interns don’t need the same level of access. By aligning permissions with roles, RBAC ensures users have just the right tools and information needed for their tasks, reducing risks and simplifying management.
- Uses predefined roles and permissions to enforce access control.
- Enforces the principle of least privilege, ensuring users only access what’s necessary.
- Minimizes the risk of unauthorized access and insider threats.
- Simplifies access management for large teams and complex hierarchies.
- Scales easily accommodate growing or changing organizational structures.
User Provisioning and Deprovisioning
User Provisioning and Deprovisioning is an essential IAM feature that automates the process of granting and revoking access for employees. Example: Think of provisioning as giving a new hire the keys to access the tools they need, and deprovisioning as taking those keys back when they leave. This ensures employees have the right access during their tenure and prevents unauthorized access once they depart.
- Automates identity lifecycle management using directory services like Active Directory (AD).
- Integrates with HR systems to synchronize employee records for accurate account creation and deletion.
- Streamlines onboarding and offboarding processes, reducing delays.
- Prevents unauthorized access by ensuring timely deprovisioning.
- Reduces human errors and improves overall IT efficiency.
Password Management
Password Management acts as a secure vault for your digital keys, helping users create, store, and manage passwords safely. It ensures strong password standards are met while offering an easy and secure way to reset or recover passwords, much like having a reliable locksmith on call.
- Enforces password complexity and expiration policies to strengthen security.
- Provides self-service password reset tools through secure channels, reducing IT workload.
- Prevents weak or reused passwords with strength checkers and password history enforcement.
Identity Federation
Identity Federation establishes trust between different identity providers, enabling seamless authentication for users. It allows individuals to use a single identity to securely access various systems without the hassle of managing multiple credentials.
- Establishes trust between multiple identity providers (e.g., Google, EntraID).
- Uses standards like SAML, OAuth, and OpenID Connect for secure token-based authentication.
- Simplifies authentication for hybrid or multi-cloud environments.
Adaptive Authentication
Adaptive Authentication, also known as Risk-Based Authentication (RBA), dynamically adjusts security measures based on factors such as location, device, IP address, user behavior, and time of access. By analyzing these elements, it assigns a risk score to each login attempt and triggers additional authentication steps, like Multi-Factor Authentication (MFA), for high-risk scenarios. This approach ensures a balance between robust security and user convenience by minimizing friction for actual users while blocking suspicious activity.
- Leverages contextual data (e.g., location, device, IP address, and time) to assess risk.
- Real-time risk engines can apply extra verification only for high-risk scenarios.
- Reduces friction for known behaviors while enhancing security.
Audit Logs and Reporting
Audit Logs and Reporting are essential IAM features that create a digital trail of user activities, offering complete visibility into who accessed what and when. These tools are especially critical for organizations in regulated industries like finance, healthcare, and education, where compliance with strict standards is mandatory. By tracking access and detecting anomalies, audit logs and reporting ensure accountability, support proactive risk management, and help businesses meet regulatory requirements seamlessly.
- Maintains logs for every access attempt, modification, or system event.
- Integrates with SIEM tools (Security Information and Event Management) for deeper analysis.
- Generates compliance-ready reports for standards like GDPR, ISO 27001, and SOC 2.
Integration with Third-Party Applications
Integration with Third-Party Applications is a key feature of modern IAM solutions, enabling seamless connectivity with cloud platforms, on-premise systems, and third-party apps. This ensures streamlined operations, enhanced security, and the flexibility to adapt to diverse business environments.
- Works with on-premise, cloud, and SaaS environments.
- Ensures seamless workflows with connectors for popular platforms (e.g., Salesforce, AWS).
- Allows API integrations to customize IAM capabilities as needed.
How to choose the best IAM solution features for your business
Choosing the right IAM solution is pivotal for addressing your organization’s security, compliance, and operational requirements. Here are key factors to guide your decision-making process:
- Understand Your Use Cases
Identify your organization’s unique challenges, such as securing remote access, safeguarding sensitive data, or managing hybrid and multi-cloud environments. This clarity ensures the chosen solution addresses your specific needs effectively. - Scalability
Go for an IAM solution that can grow with your organization, accommodating an increasing number of users, applications, and evolving infrastructure without compromising performance. - Integration Capabilities
Prioritize solutions that seamlessly integrate with your existing IT landscape, including connecting with your existing directories and database, cloud platforms, and on-premise systems, to ensure smooth operations and enhance productivity. - Vendor Reliability
Choose a provider with a strong track record in delivering secure, innovative IAM features. Look for proven expertise in managing complex environments and supporting industry compliance standards.
Conclusion
IAM features are the cornerstone of a secure, scalable, and efficient identity management framework. From foundational tools like Single Sign-On (SSO) and Multi-Factor Authentication (MFA) to advanced capabilities like adaptive authentication and audit logs, each feature plays a crucial role in safeguarding your business, enhancing productivity, and meeting regulatory requirements.
In today’s digital-first world, selecting the right IAM solution is not just a choice but a necessity. With miniOrange, you gain access to a comprehensive suite of IAM features tailored to meet your organization’s unique needs. Whether it's protecting against cyber threats, streamlining user access, or achieving compliance, our solutions are designed to empower businesses to thrive securely.
Take the next step in fortifying your digital environment. Explore how miniOrange can transform your security and operational efficiency—because securing your business starts with the right IAM partner. Contact us today!
Author




Leave a Comment