miniOrange Identity & Access Management (IDAM) helps every financial & banking services firm whether it is large or small, needs to know and adhere to the financial & banking services industry’s regulatory compliance standards. These standards govern everything from how your company prices products, collects premiums or handles customer disputes. They are also the foundation for anti-fraud measures that protect the identity theft of credit card holders and identity fraud worldwide. Financial regulators are always increasing the cost of committing wrongdoings in these two areas. Becoming compliant with these regulations will help you survive any potential changes.
Financial & Banking enterprises need to have data protection & Access control with Identity & Access management for internal & external applications. This is helping finance & banking enterprises to build trust & create safe experiences for the workplace & customers.
miniOrange IDAM solution for Banking or Non-Banking & Finance Sector, whether it is on-premise or cloud (identity as-a-service – IdaaS, for example), ensures that the authorized users can access only the data they are permitted to access.
Is IDAM Necessary for the Banking & Finance Sector?
Identity and Access Management (IDAM) is a critical aspect of cybersecurity in the banking industry. It refers to the processes and technologies used to manage and secure access to a company’s systems and data.
In the banking industry, IDAM is particularly important due to the sensitive nature of the data being handled. This includes customer financial information, as well as internal banking operations data. Ensuring that only authorized individuals have access to this data is essential for maintaining the security and integrity of the bank’s operations.
Banking & Finance sectors have compliance programs designed to make sure that banks adhere to a certain set of guidelines and regulations that affect the operations of financial institutions. Compliance in banking has become more important than ever before due to the number of regulations adopted by both government and financial regulators. Compliance regulations such as:
PCI-DSS mandates the implementation of IT security measures to protect the integrity, confidentiality, and availability of financial data.
SOX compliance refers to compliance with the Sarbanes-Oxley Act, a US federal law passed in 2002. SOX requires companies to maintain internal controls and procedures for financial reporting, and to have an independent auditor attest to the effectiveness of those controls. It is mandatory for any company that is publicly traded in the United States to comply with SOX
GLBA compliance refers to compliance with the Gramm-Leach-Bliley Act, a US federal law passed in 1999. GLBA requires financial institutions to have a written information security plan (WISP) in place, which includes administrative, technical, and physical safeguards to protect nonpublic personal information from unauthorized access or use. The GLBA applies to banks, credit unions, securities firms, and other financial institutions that offer consumers financial products or services.
FISMA compliance refers to compliance with the Federal Information Security Modernization Act, a US federal law passed in 2002. FISMA requires federal agencies to implement information security policies and procedures, including risk management, incident response, and continuous monitoring of their information systems.
SAMA compliance refers to compliance with the regulations set by the Saudi Arabian Monetary Authority (SAMA), which is the central bank of the Kingdom of Saudi Arabia. SAMA sets rules and regulations for financial institutions operating in the country to ensure stability and safety of the financial system.
RBI Guidelines - In India, banks are required to comply with various IT-related regulations and guidelines set forth by the Reserve Bank of India (RBI) to ensure the security and integrity of banking systems and data.
miniOrange IDAM solution supports more banking & finance compliance like above mentioned according to the different countries & regions.
IDAM System
There are several key components of an effective IDAM system in the banking industry:
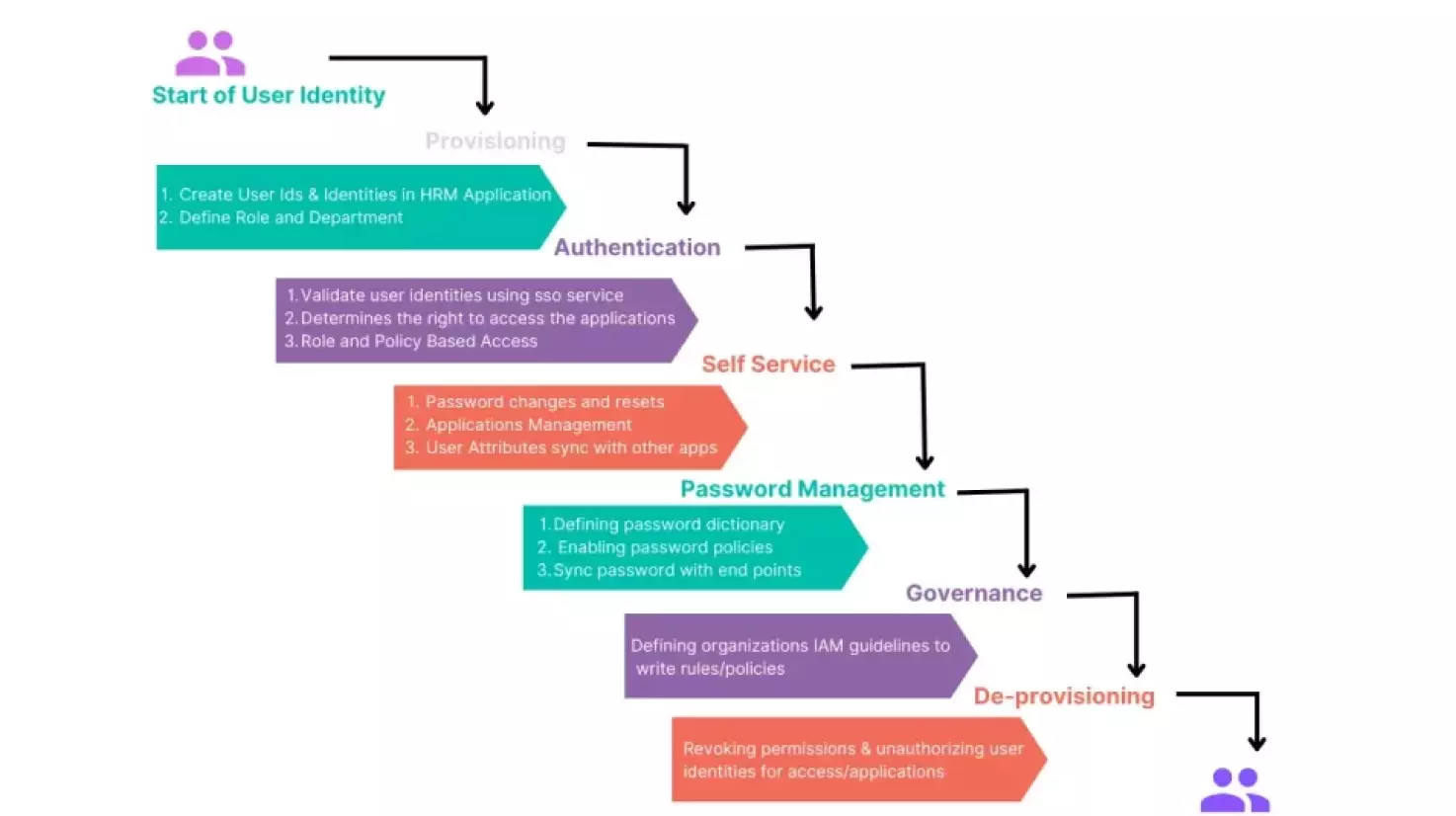
- User registration: Customers register for online banking by providing personal and identification information, such as name, address, date of birth, and government-issued ID.
- Authentication: The bank verifies the user’s identity by using one or more authentication methods, such as a password, security questions, or biometrics.
- Authorization: Once the user is authenticated, the bank grants access to the appropriate resources, such as account information or online transactions, based on the user’s role and permissions.
- Access management: The bank monitors and controls the user’s access to resources by implementing policies and procedures, such as password expiration, multi-factor authentication, and access logs.
- Audit and compliance: The bank maintains records of all user activity for compliance and auditing purposes, such as to detect and prevent fraud.
- De-provisioning: When a user’s access is no longer needed, the bank revokes the user’s access to resources and performs any necessary clean-up tasks, such as deleting the user’s account or archiving the user’s data.
Overall, IDAM is a crucial aspect of cybersecurity in the banking industry. By implementing strong identity verification, access control, and auditing and reporting processes, banks can ensure that their systems and data are protected against potential threats.
IDAM combines SSO with multi-factor authentication (MFA) to secure user access to cloud and on-premises applications and protects confidential financial data by applying different authentication factors for different users based on risk factors such as IP address, time of access, device, and geo-location with risk-based automated access control.
Author


Leave a Comment