In the current digital landscape, Multi-factor authentication (MFA) is crucial as it safeguards sensitive information and data, because of its capability to strengthen security, prevent breaches, and counter phishing. MFA ensures compliance, safeguards remote access, and prevents unauthorized entry. This proactive approach not only protects sensitive information but also offers long-term cost savings.
With ever-increasing cyber threats, relying only on passwords for protection is no longer sufficient. This is where Multi-Factor Authentication (MFA) comes into play. MFA adds an additional layer of security by requiring users to provide multiple forms of verification before granting access. To help you implement MFA effectively, we've compiled a comprehensive MFA checklist that covers critical considerations and best practices.
Elaboration on Key Points for Effective MFA Requirements
1. User-friendly and comprehensive support:
Choose an MFA solution that offers both a user-friendly setup and comprehensive support. This combination of an easy setup process and robust user assistance reduces any issues encountered during implementation and empowers users to embrace the new security measure, integrating Multi-Factor Authentication (MFA) seamlessly into daily operations.
2. Application Integration:
The MFA solution should seamlessly integrate with the applications and systems you use, it should seamlessly integrate with your existing infrastructure. That would ensure security enhancements without disrupting operations, minimizing disruptions to workflows. The integration streamlines the user experience and helps to maintain their familiar workflows while benefiting from enhanced security measures.
3. Offline MFA Methods:
Explore MFA methods that work offline, ensuring access even when connectivity is limited. Offline-capable methods, like hardware tokens or biometrics stored on a device, ensure users can authenticate even in situations where an internet connection is not available.
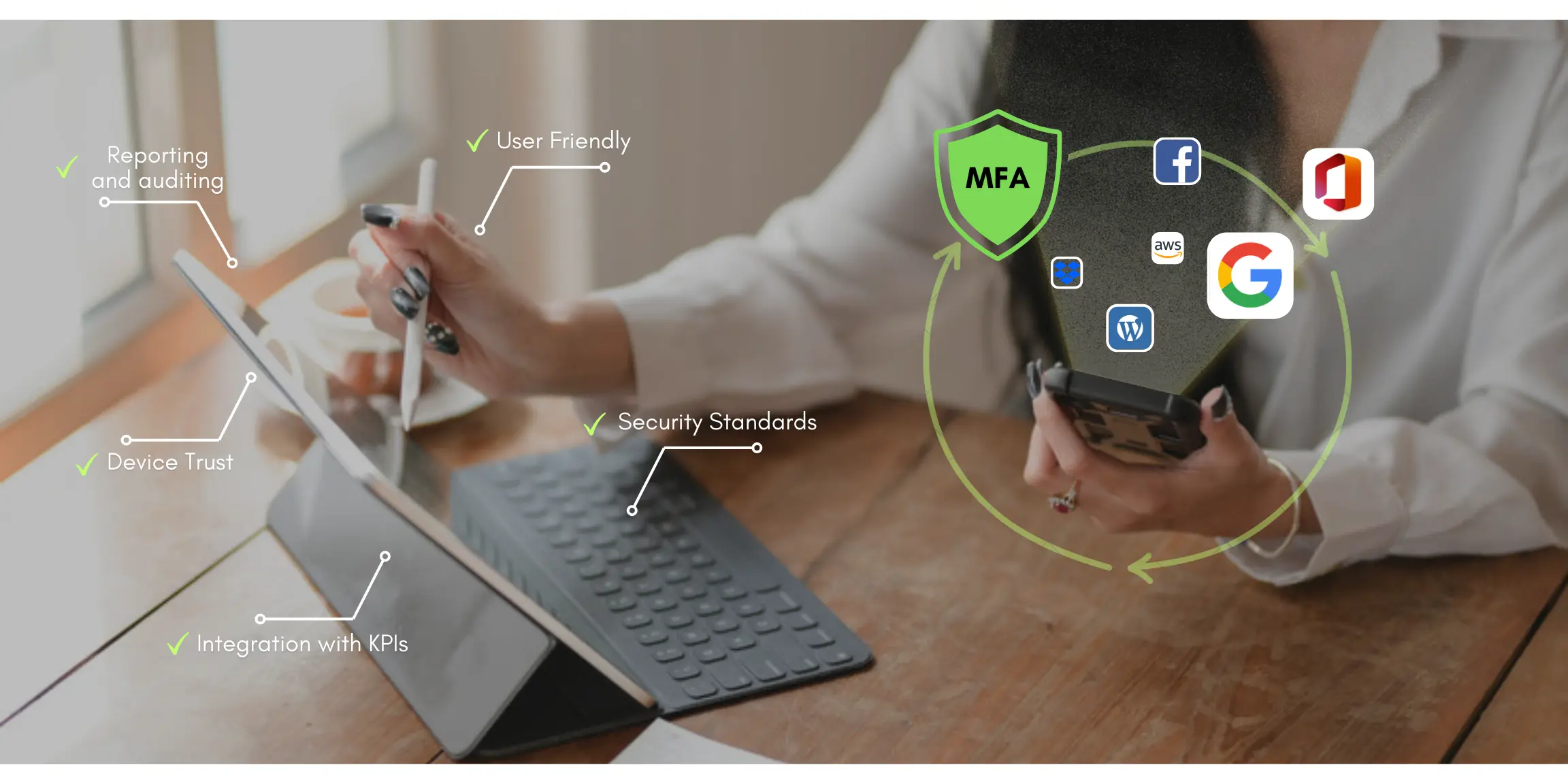
4. Integration with KPIs:
Integrate MFA effectiveness with key performance indicators (KPIs) to measure its impact on security and user experience. By aligning MFA deployment with quantifiable metrics, you can evaluate its success in enhancing protection while maintaining a positive user journey.
5. Authentication Methods:
Explore the diverse set of authentication methods, such as - SMS, push notifications, biometrics, hardware tokens, and authenticator apps. Choose the method that aligns with user preferences and security requirements. This array of options enables users to select the most suitable authentication and accommodates a wide range of preferences while maintaining security standards.
6. Flexible Authentication Policies:
Tailored authentication policies to suit varying levels of sensitivity and risk. This is done by implementing different levels of MFA complexity, such as - requiring stronger methods for high-risk actions. Security measures are aligned with the value and potential impact of the access.
7. Reporting and Auditing:
Select an MFA solution with a robust reporting system, offering insights into user behavior, failed login attempts, and potential threats for proactive responses. These reports provide a comprehensive overview of security events, enabling prompt actions to mitigate risks and address security vulnerabilities.
8. Device Trust:
When MFA solutions support device-based trust, it enables certain devices to bypass specific MFA methods based on the security structure of the organization. This approach strikes a balance between security and convenience. It enables trusted devices to undergo streamlined authentication while still upholding overall security standards.
9. Application Integration and Standards:
When developing an in-house application, ensure your chosen MFA solution provides strong APIs and developer support, allowing smooth integration. Additionally, prioritize MFA solutions that follow open standards like OAuth, ensuring compatibility and enhancing overall security.
MFA solutions that incorporate behavioral analytics to detect anomalies in user behavior, in turn, enhance security by identifying potentially compromised accounts. This proactive approach helps to prevent unauthorized access by recognizing patterns that deviate from established user behavior norms.
Conclusion
Overall, Following the above checklist will enable you to implement MFA effectively, significantly enhancing your organization's digital security posture. Hence, the miniOrange Multi-Factor Authentication (MFA) solution is an essential tool in your cybersecurity toolkit.
Protecting sensitive information and maintaining user trust has never been more crucial, and MFA is a step in the right direction. Stay ahead of cyber threats by embracing MFA and securing your digital assets, to experience the benefits firsthand, we invite you to schedule a demo or take advantage of our 30-day Free Trial Link.
Our round-the-clock 24x7 global assistance ensures you're never alone in your journey toward enhanced security. What's more, all of this comes at a competitive price point, making miniOrange the ultimate destination to achieve the utmost comfort and security in the market.
Author




Leave a Comment