MFA for On-Premise Active Directory: What You Need to Know?
With so many options available for securing your on-premise Active Directory, it’s easy to feel overwhelmed. Many organizations have a natural inclination towards hybrid solutions that provide the most secure and user-friendly experience for everyone. However, some businesses prefer on-premise solutions because they give them more control over their data.
That doesn’t mean on-premise Active Directory is redundant or outdated – far from it! As long as you don’t want to implement a cloud solution, on-premise AD is still one of the best ways to protect your network and user accounts while keeping things simple for employees. Why? Because it gives users the same password no matter where they log in, which means their security isn’t compromised if they use a different username and password combination at home or work and only an additional layer of security is added on top of it.
Is MFA for Active Directory necessary? Why do you need it?
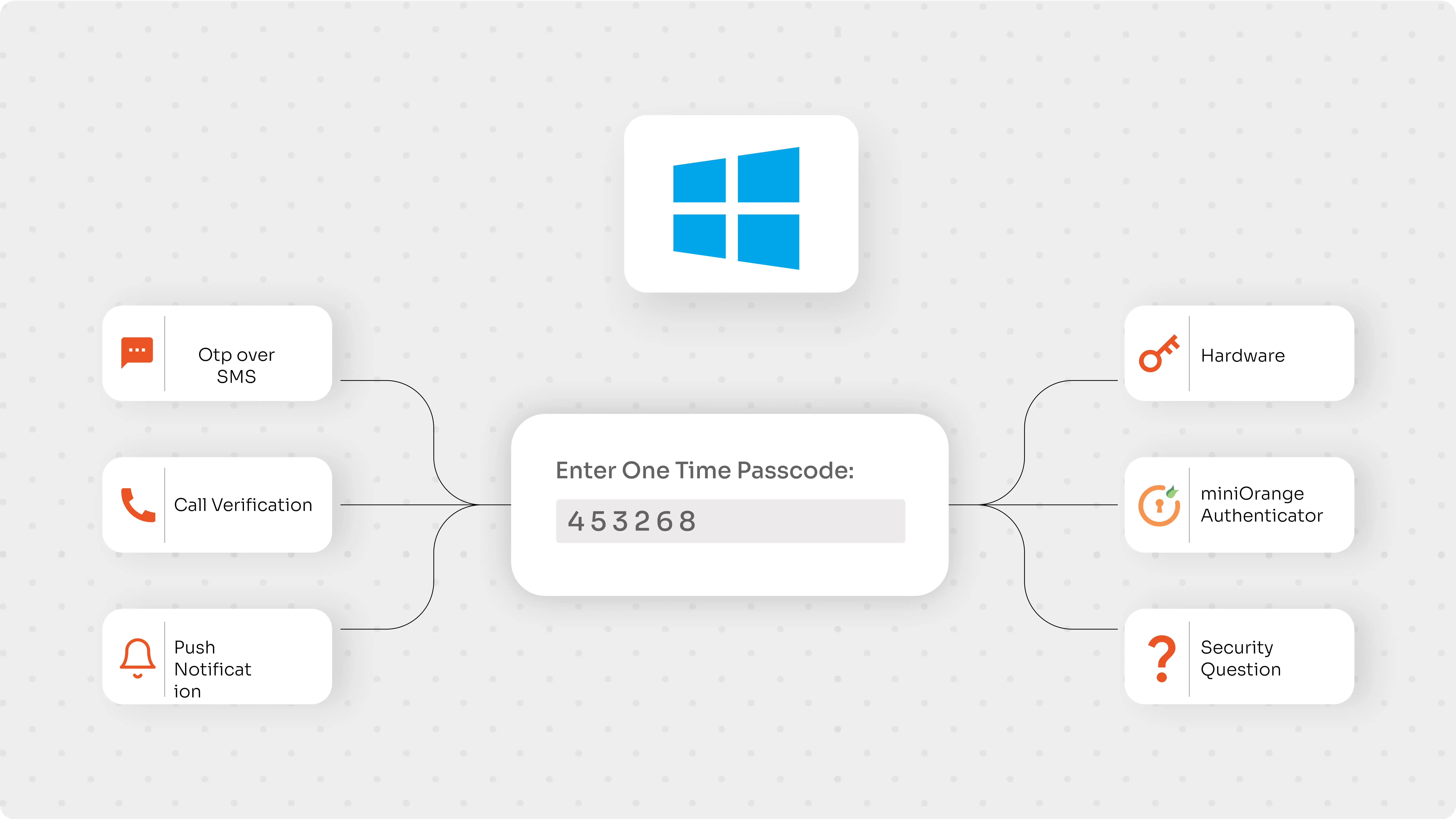
Single sign-on is one of the most important features of any identity management system. Essentially, it’s the ability to log in once and access every resource you own. This is especially important when it comes to on-premise Active Directory because you want to avoid requesting MFA codes every time you log in. On-premise AD is a closed system, and when you add MFA to your log-in, you’re essentially creating an additional layer of security for your network. However, if you don’t enable MFA for your AD, you’re taking an unnecessary security risk. That’s why it’s important to add MFA to your log-in process – especially if your employees work remotely. It’s also important to note that you can add MFA to your on-premise AD log-in using any of the following methods: SMS verification, phone call verification, hardware token, software tokens, etc. Check out the different MFA methods provided by miniOrange or else read more about what is MFA.
How and where can you enable MFA connections for Active Directory
-
MFA on Windows Machines and Linux Machines: Enable MFA for AD domain-joined machines or standalone machines working on windows or Linux operating systems. Secure your Windows logon with MFA and MFA for Linux login.
-
MFA for Windows Remote Desktop (Remote desktop services): Enable MFA for all remote desktop connections which include RDP, RD Gateway, RD Web Access, etc. for end-users remote access.
Check out MFA for RDGateway and RD Web access MFA
-
MFA over VPNs: Enable MFA for your VPN and other network devices in your organization like switches, routers, firewalls, etc. using the miniOrange Radius server. miniOrange supports all the VPNs and network devices available in the market. Learn more about VPN MFA.
-
MFA for Cloud and on-premise applications: Enable MFA for applications like Microsoft Office 365, Google Workspaces, Zoom, Jira, Salesforce, etc. using the miniOrange Identity server. miniOrange has pre-integration with 5000+ applications.
-
MFA for Legacy apps: Unique MFA solutions for legacy apps like Oracle E-business Suite (EBS), Adobe Suite of applications, SAP, etc. Cut down on the heavy costs of the traditional software and hardware requirements with miniOrange Identity server for SSO & MFA for legacy apps.
-
MFA for Mobile apps: Enable MFA for mobile apps for all the modern applications and technologies like React, Angular, Ionic, etc. using protocols like SAML, JWT, Oauth, OpenID, etc. With the exponential increase in mobile apps in the world of the internet, securing not only your web apps but also your mobile applications is one of the utmost priorities. Check more details for native mobile apps MFA.
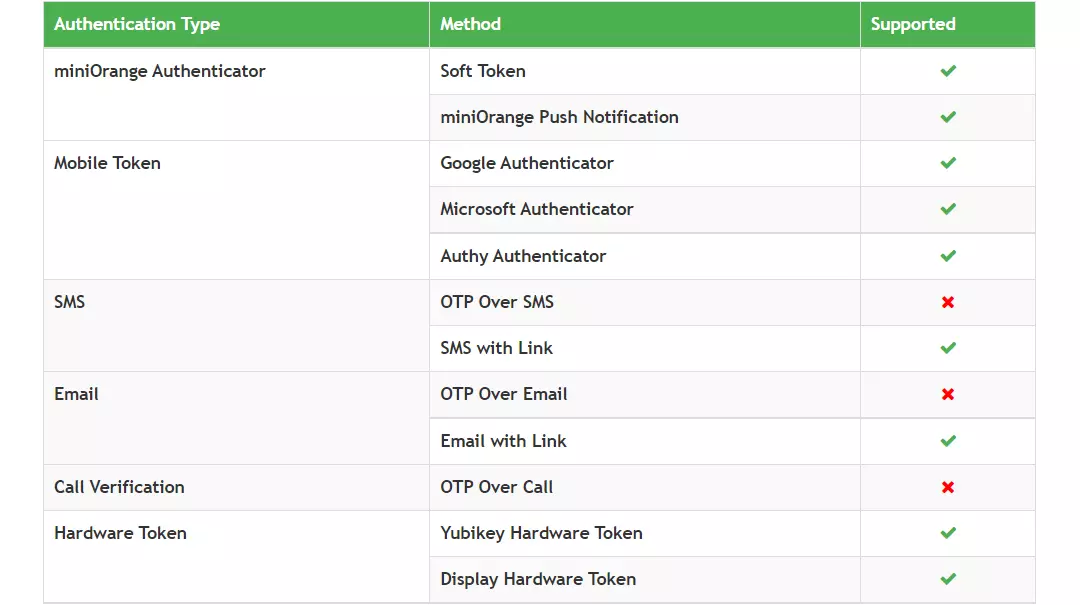
Which MFA methods over the Active Directory can you enable for your users?
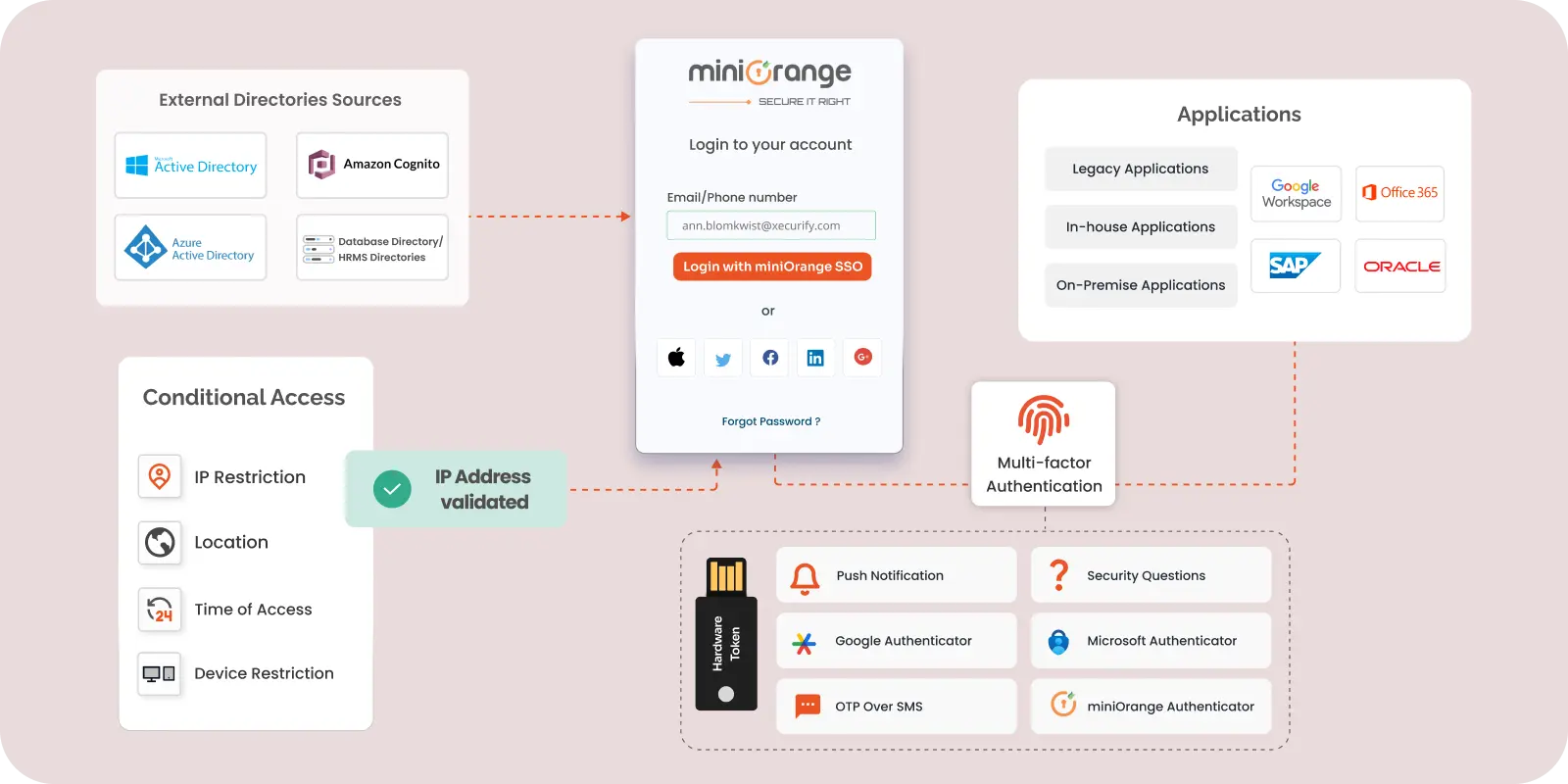
miniOrange supports the following 15+ MFA methods and the miniOrange admin has full privilege over the two-factor authentication (2FA) options for end-users and the users can select any MFA method that they have been allowed to configure:
Looking for Something more Advanced? There is Adaptive authentication for you
Adaptive authentication is an advanced MFA solution wherein you can set up custom policies for user access based on the organization’s business requirements. You can set up restrictions for users based on some additional attributes which will be risk-based. This is also called risk-based authentication. The user will be prompted for MFA based on its risk-based profile. The restriction policies can be based on the following four parameters:
1. IP Restriction: In the Adaptive MFA IP-based restriction method, the admin configures and enlists all IP addresses to allow or deny access.
2. Device Restriction: In the Device-based Adaptive Multi-Factor Authentication (MFA) method, the admin allows end-users to add a fixed number of trusted devices to their account (A device here refers to a Browser Session). Once a user’s device has been registered, that person will be able to log in without restriction.
3. Location Restriction: In Location-based Adaptive MFA restriction, the admin shortlist and configure a list of Geo-locations where they want to allow end-users to either login or deny based on the location set by the admin.
4. Time Restriction: One of the most significant components of Adaptive MFA configuration is a time restriction, which begins with the admin establishing a time zone with Start and End Time. Users are either permitted, refused, or challenged based on the timezone and policies defined.
Check more details on Adaptive Authentication MFA
Additional Features and functionalities for MFA
Here are some additional features with miniOrange MFA that makes sure that adopting MFA for any organization becomes a very smooth and seamless process. These features make sure that the solution is highly maintainable, easy to use, and fits almost every business requirement of any organization. The details are as follows:
-
Offline MFA: The MFA can be prompted even if there is no active internet connection on your devices.
-
Deploy easily with AD: miniOrange supports both cloud as well as on-premise identity server solutions. You can easily connect your on-premises Active directory to miniOrange using LDAP protocol and use it as an identity source. You can establish a connection with AD which is not publicly accessibly using the miniOrange Gateway module.
-
Easy MFA enrollment: Users can be enrolled to enable MFA during the registration process. All users including remote can self-enroll themselves by providing a registration link to them. All users get access to a self-service console through which they can change the MFA method, change or reset passwords, etc.
-
Group and policies: The Admin and create groups of users from the active directory. Based on the groups, multiple policies can be applied to have MFA rules based on groups, restriction specific application access to specific groups, enabling Adaptive authentication only for targeted groups, etc. This makes sure that your business models are matched and that you have the right set of restrictions for different types of users and groups.
Can I enable MFA for the Active directory without Azure AD and M365?
A big yes! There is absolutely no requirement to have an Azure or Microsoft 365 subscription to enable MFA for the on-premise Active directory. You can connect the On-premise AD directly to miniOrange via LDAP protocol and use it for authentication purposes. Although you get a basic MFA functionality with some higher plans of Azure, those are not much detail-oriented and flexible to meet any of the organization’s requirements. You can check out the comparison of miniOrange vs Azure AD for in-depth details regarding the same. So there is no requirement for an additional Azure Connect as well to keep a sync between your on-premise AD and AAD to enable MFA. Thus, saving you a lot of money! However, even if you have a hybrid environment already in place using on-premise Active directory and AAD, then also the process and steps to enable MFA remains the same without hampering the experience of end-users and using the same set of usernames and passwords for all the logins.
Conclusion
The on-premise AD with MFA is one of the most secure ways to protect your network. However, it’s important to note that if your network uses an on-premise AD server, Microsoft recommends that you use AD MFA instead of Azure AD MFA because it’s a more secure option. That said, on-premise AD does have limitations compared to its cloud equivalent. If you want modern features like integrated security, single sign-on, and identity governance, you should look into switching to Azure AD. Additionally, you can also choose to use a hybrid solution that offers the best of both worlds.
Author



Leave a Comment