What is a PAM Solution?
A PAM solution stands at the forefront of cybersecurity, offering a robust strategy for protecting organizations from credential theft and misuse of privileged access. Privileged Access Management (PAM) solutions focus on managing and overseeing elevated privileges associated with user roles, resources, accounts, and systems within an IT environment. By implementing a PAM security solution, organizations effectively shrink their attack surface, thereby reducing the likelihood of external cyber attacks and mitigating damage from insider threats, whether intentional or accidental. Recognized by analysts and tech experts, PAM solutions are key to diminishing cyber risk and maximizing the return on security investments.
A PAM security solution employs a variety of cybersecurity strategies and technologies to exert control over privileged access. One such strategy is the concept of least privileges in a PAM solution. It ensures that users are granted the minimum levels of access necessary to carry out their job functions. With this organizations can significantly reduce their attack surface, limiting potential avenues for malicious insiders or external cyber threats. This reduction in exposure helps to mitigate the risk of costly data breaches and other security incidents that could have severe consequences for the organization.
Understanding what a PAM solution is and how it operates is crucial for modern cybersecurity practices. By incorporating a privileged access management (PAM) solution into their security framework, organizations can ensure that they are utilizing one of the best PAM solutions available to protect their critical assets and maintain robust security postures.
The Importance of PAM Solutions
The absence of an effective PAM solution can lead to substantial financial and operational losses for businesses. In an era of increasing cyber threats and expanding endpoints, vulnerabilities are more pronounced. Issues like repeated use of passwords, inadequate access management, and lack of monitoring and auditing leave systems open to unauthorized access. Furthermore, insufficient visibility into privileged users, accounts, and shared credentials exacerbate these security challenges.
PAM solutions address these issues by ensuring complete control and accountability over all privileged accounts. They automate privilege management and secure endpoint access, identifying machines, accounts, and applications with administrative rights across workstations and cloud servers. Features like Privileged Account Password Management and automated password rotation comply with stringent password policies, updating credentials automatically.
A privileged access management PAM solution provides granular access control, allowing organizations to tailor their security infrastructure by granting, modifying, and revoking access as needed. This level of control is vital for maintaining security and minimizing the risk of unauthorized access or misuse of privileged accounts. By enforcing the least privilege principle, PAM solutions guarantee that users have only the permissions necessary for their tasks, significantly reducing the potential attack surface.
Implementing the best PAM solution helps organizations maintain robust security postures by automating key security processes and enhancing visibility and control over privileged access. This comprehensive PAM security solution approach is essential for modern cybersecurity practices.
What Features Should You Look For In A PAM Solution?
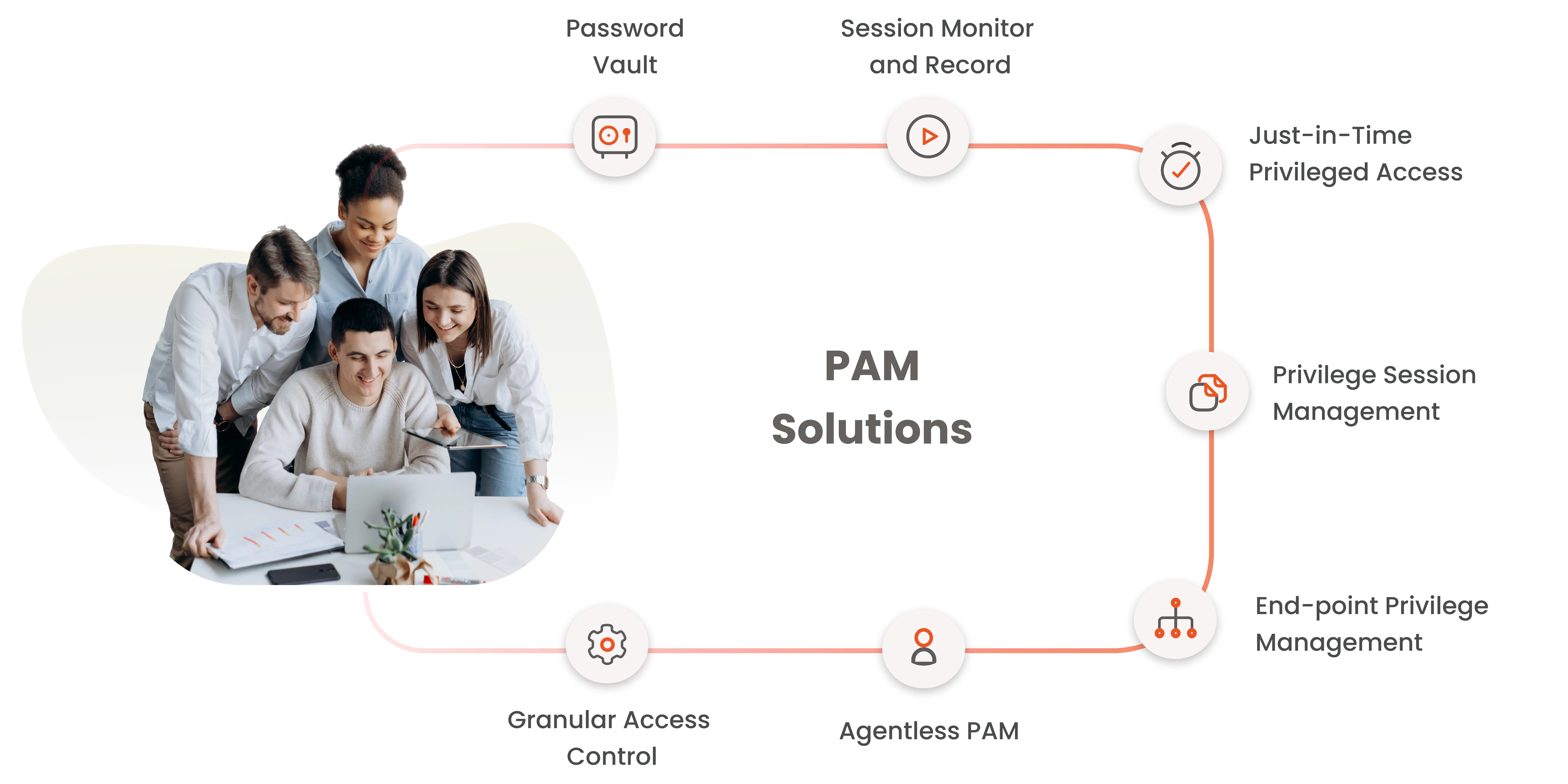
1. Password Vault and rotation : The Password Vault simplifies password management by providing easy handling of passwords, including updates, password rotations, disposal, and tracking. It seamlessly integrates with existing systems, making password management a seamless process. One of its key features is the secure storage of privileged passwords within an encrypted vault, ensuring that sensitive credentials are protected from unauthorized access or theft. By using the Password Vault, organizations can significantly reduce the risk of credential theft, enhance endpoint security, and enhance the overall cybersecurity posture of their organization.
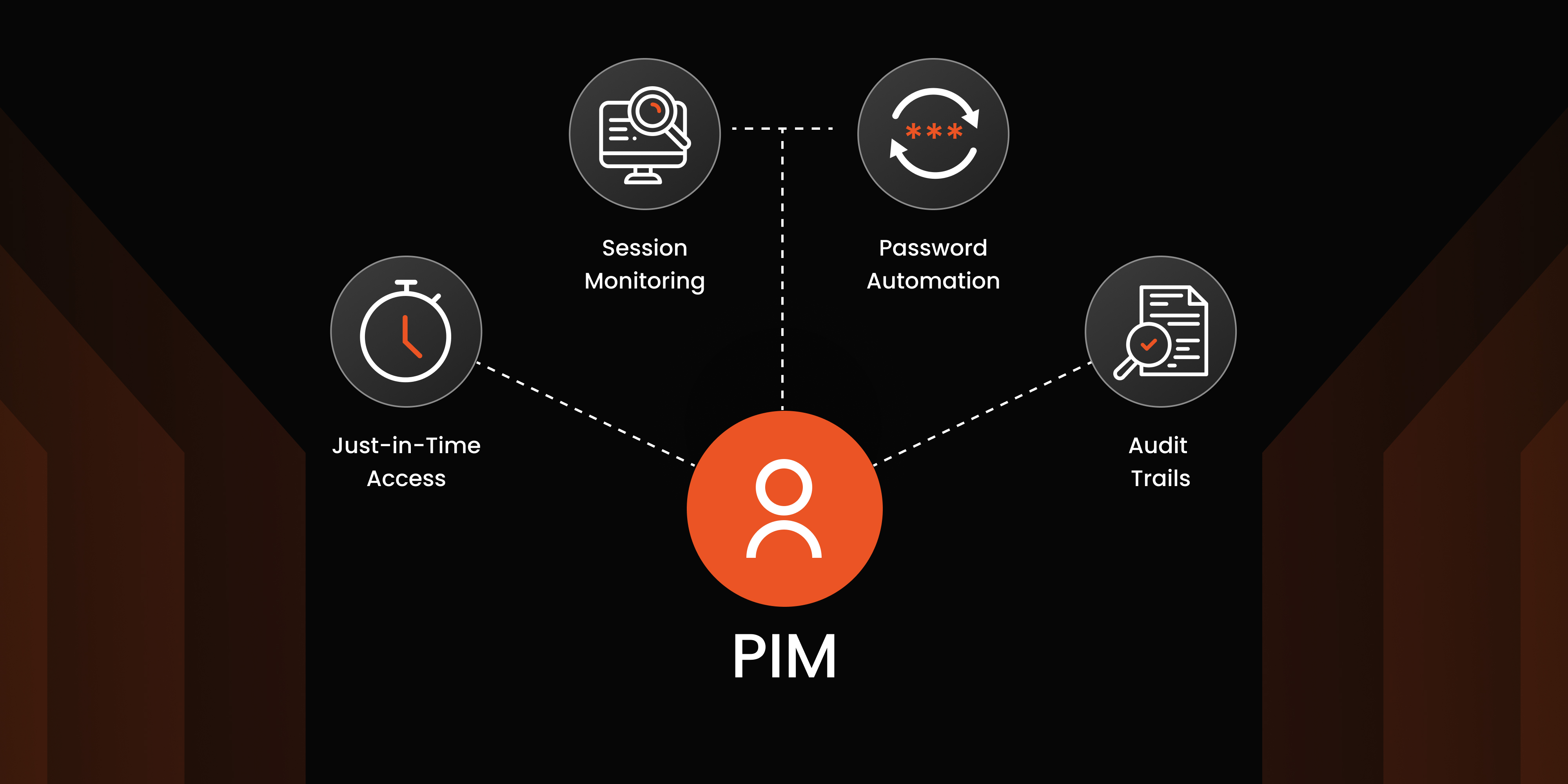
2. Audit trails: Session and audit trails closely monitor user and session activities, Admins have access to an audit log that tracks all actions performed by privileged users during their sessions, providing detailed event information and timestamps for each event.
These audit trails enable administrators to promptly detect suspicious behavior, system issues, operational problems, and related errors. Audit trails play an essential role in keeping track of privileged user activities and mitigating the risks associated with unmonitored access and misuse within systems.
3. Session Monitoring and Recording: Through Session monitoring and recording, the PAM solution offers advanced oversight and accountability for users accessing privileged accounts. This functionality offers granular control over critical assets like databases, servers, and network devices, ensuring that privileged access is closely monitored and recorded. Real-time monitoring of sessions and user activities allows for thorough organizational audits, enabling administrators to track and review actions taken during privileged sessions. Additionally, there is also an option to terminate a session while session monitoring.
4. Just-in-Time (JIT) Privileged Access: The Just-in-Time Access grants users access to accounts and resources for a specific, limited timeframe. This approach aims to minimize risk by providing access only when necessary, preventing users from having more privileges than required. Rather than granting permanent, unlimited access, temporary access is provided on demand. Access is restricted based on predefined roles, adhering to the Principle of Least Privilege (POLP). This ensures that users have access only to what is essential for their designated tasks and responsibilities.
5. Endpoint privilege management: With EPM, users are granted only the necessary privileges and access to applications, ensuring robust security. Unauthorized applications are easily restricted or blocked, creating a fortified environment. Privileges are granted on a needs basis, allowing trusted applications to run with the lowest possible privilege levels. EPM protects desktops, laptops, and servers from attacks, reducing the risk of data theft or ransomware encryption.
6. Privilege Elevation and Delegation: enables users to temporarily elevate their privileges on a granular level when needed to complete a task, without granting them permanent administrative privileges. It reduces the risk of accidental exposure, limiting access to privileged accounts and resources only when needed. The principle of least privilege is applied through digital password vaults, granting temporary admin accounts on a need basis, ensuring secure access to critical resources.
7. Granular Access Control: Refers to implementing precise and detailed access controls that are based on the principle of least privileges. This approach restricts access to privileged accounts by assigning permissions at a highly specific level, Granular Access Control gives users only the minimum access required to perform their authorized tasks. Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) are two common methods used for implementing granular access controls. By adopting granular access control, organizations can enhance security, minimize the risk of unauthorized access, and maintain a more controlled and efficient privileged access management system.
8. Privileged Account Discovery: This identifies and catalogs all privileged accounts within an organization's IT infrastructure, it consists of accounts with elevated privileges or administrative access on various systems such as servers, databases, network devices, and applications. There is a comprehensive inventory of all privileged accounts, making it easier for organizations to manage and secure these critical accounts effectively. By knowing where these privileged accounts exist, organizations can implement stronger security measures, and conduct regular audits.
9. Integration with Identity and Access Management (IAM): Merging Privileged Access Management (PAM) solutions with existing IAM systems creates a unified approach to access control, user provisioning, and user lifecycle management. This integration enables seamless and efficient management of both standard user accounts and privileged accounts from a single centralized platform. It allows administrators to apply consistent security policies, access rules, and authentication mechanisms to all users, regardless of their privileges, thereby simplifying the overall management and ensuring a more robust security posture for the organization.
miniOrange PAM Solution: Unveiling the Realm of Privilege with an Array of Account Types!
We have categorized the Privileged accounts into several types, each serving distinct roles within an organization's IT infrastructure:
- Local administrative accounts: These accounts provide elevated privileges on individual endpoints or devices within a network. They are used to manage the local system settings, and their misuse can lead to unauthorized access and potential security breaches.
- Domain administrator accounts: Have the highest level of access rights within an IT environment. These accounts have control over all the other user accounts, workstations, and all network resources across the entire domain. Securing these accounts is vital as compromising them can cause severe network damage.
- Service accounts : These are created to enable specific services or applications to interact securely with the operating system or resources on the network. Such accounts are often used for automation, and it's essential to properly manage and secure them to prevent potential abuse by attackers.
- Application accounts : Application accounts are used by software applications to get full access to specific applications and data stored in those apps, databases, and related resources. E.g. Service accounts require precise management to ensure minimal permissions for any task.
- Privileged accounts : These accounts are the elevated access to privileges over standard users, they have significant access rights across various systems and applications, making them highly attractive targets for cybercriminals.
- Emergency accounts: They are intended for crisis situations or troubleshooting scenarios where regular privileged accounts might be unavailable. In times of disaster or disruption, emergency accounts grant non-privileged users temporary admin access to critical systems for securing operations.
Properly handling and overseeing various privileged accounts is essential for a strong privileged access management (PAM) strategy. It is crucial to protect these accounts effectively to reduce the risk of unauthorized access and potential security issues in an organization's IT infrastructure.
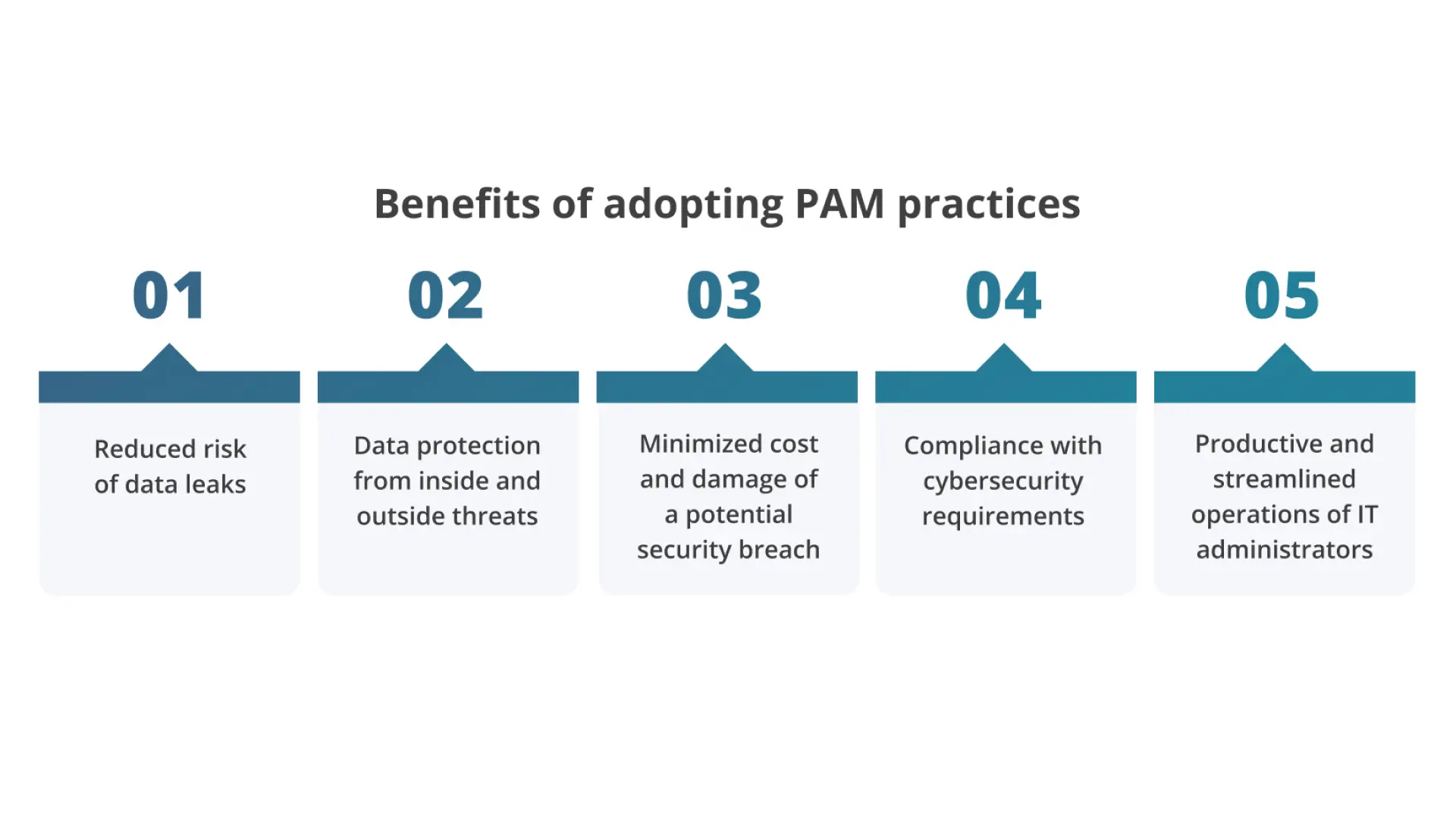
What Are The Benefits Of Privileged Access Management?
Privileged Access Management (PAM) plays a crucial role in enhancing the security of an organization's IT infrastructure, let us look at some of the benefits of Privileged Access Management.
- Enhanced security : PAM solution helps to fortify an organization's IT infrastructure by minimizing the risks posed by human errors and misuse of privileged accounts.
- Reduced attack surface : Limiting privileges for users, processes, and applications decreases potential pathways for both internal and external threats.
- Mitigated malware risk : Removing excessive privileges and enforcing the least privilege curtails the ability of malware to infiltrate and spread within the system.
- Improved operational performance : By restricting privileges to authorized activities, PAM solutions reduce compatibility issues between applications and lower the risk of downtime.
- Simplified compliance : PAM solution creates an audit-friendly environment, streamlining compliance efforts and facilitating assessments and reporting.
- Cyber insurance support : Cyber insurance often requires PAM solutions for reducing cyber risk. These controls are essential to get or renew cyber liability coverage and protect against financial losses from any cyber incidents.
How Does Privileged Access Management (PAM) Software Work?
Implementing Privileged Access Management (PAM): To enhance security with PAM, follow these key steps:
- Gain Visibility: Select a PAM solution that provides comprehensive visibility into all privileged accounts used by human users and workloads. This allows you to identify and eliminate default admin accounts and enforce the least privilege principle, granting users only the access they need.
- Govern and control access : Maintain continuous oversight of privileged access and manage privilege elevation to prevent unauthorized access, thereby protecting your organization's cybersecurity.
- Monitor and audit activities : Establish policies that define acceptable behavior for privileged users and identify policy violations. Regular monitoring and auditing ensure compliance and enable swift action against suspicious activities.
- Automate PAM solutions : Implement automation for discovering, managing, and monitoring privileged accounts, users, and resources. Automation facilitates scaling across numerous accounts, reduces administrative burden, and simplifies complexity.
- Gradual implementation and expansion : Begin with the PAM solution tailored to your IT department's immediate needs and gradually integrate additional modules for enhanced functionality. Follow security control recommendations to ensure compliance with regulations effectively.
Unlocking the Key to Security: miniOrange's PAM Best Practices
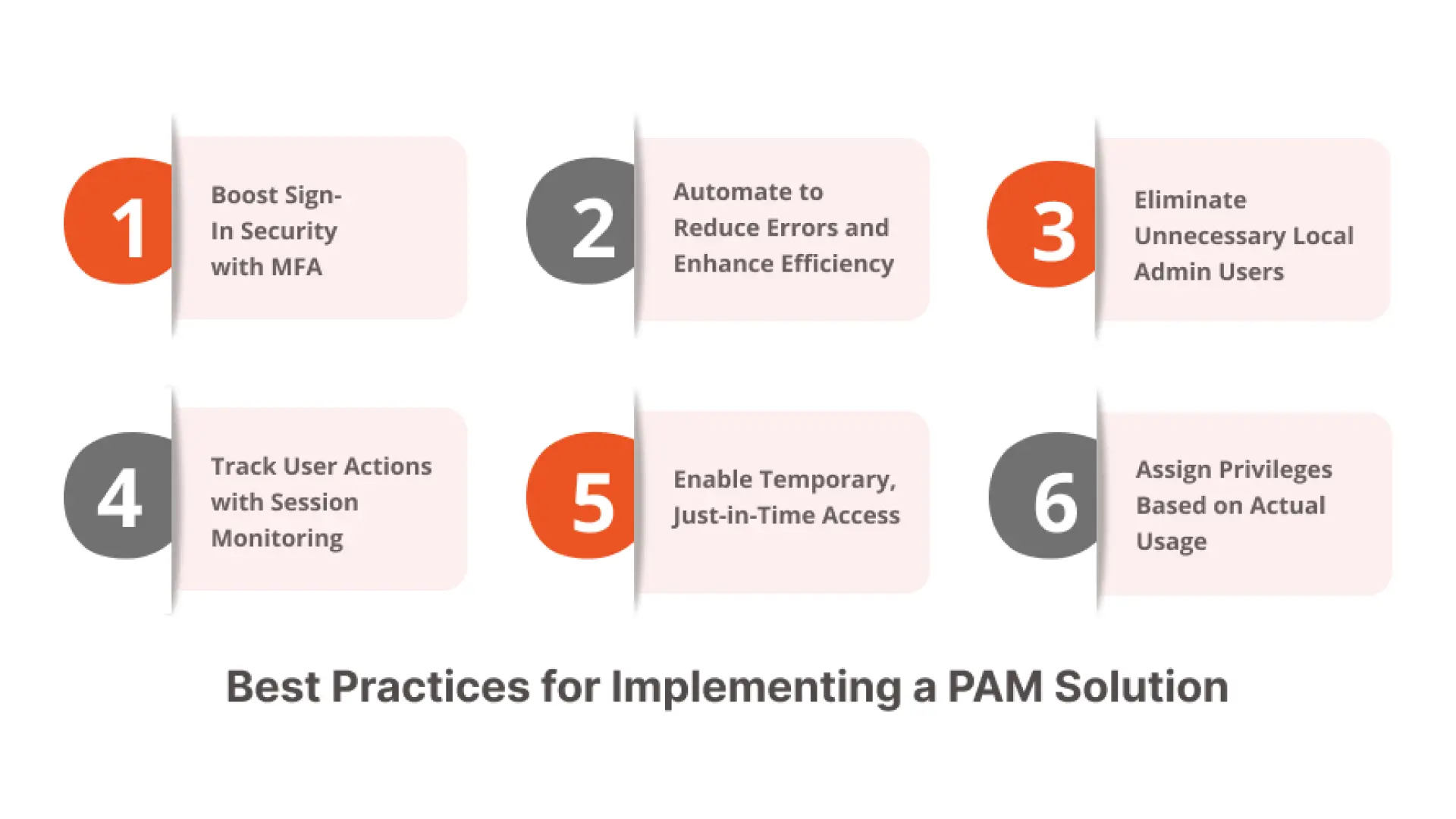
Implementing a Privileged Access Management (PAM) solution requires adherence to best practices that bolster security and mitigate risks within an organization's IT infrastructure. Let us have a look at these essential guidelines that we implement in our PAM solutions:
- Implementing MFA : Strengthens the sign-in process by incorporating Multifactor Authentication(MFA). This additional layer of security demands users to verify their identity through a trusted device when accessing accounts or applications.
- Automation of Security : Automating security processes minimizes human errors and enhances efficiency. Automation is utilized to swiftly restrict privileges and prevent unauthorized actions in situations of potential threats.
- Restrict End-Point Users : Identifies and eliminates unnecessary end-point users from the local admin group on IT Windows workstations. By doing so, the risk of threat actors is reduced using admin accounts to move through the network, steal credentials, and elevate their privileges.
- Monitor Privileged User Sessions: Audit and monitor privileged access activities track user actions and privileged password usage. Setting baseline standards for acceptable behavior helps detect any suspicious deviations that could threaten system security.
- Granting Limit Privileged Access: Consider granting temporary just-in-time access and just-enough access instead of providing perpetual privileged access. This ensures that users have a valid reason for elevated access and only for the required timeframe.
- Employ Activity-Based Access Control: Provide privileges based on a user's actual resource usage and historical activity. Closing the gap between granted and used privileges enhances security and minimizes unnecessary access.
By following these best practices, organizations can implement an effective PAM solution, fortify their security measures, and significantly reduce the risk of unauthorized access and potential security incidents within their IT infrastructure.
FAQs
1. Why Do You Need A PAM Solution?
PAM is important for organizations as it helps to protect against security risks posed by credential theft and privilege misuse, it also helps in reducing the risk of data breaches and cyber-attacks.
2. What is the importance of privileged access management? The importance of privileged access management lies in its ability to control, monitor, and secure privileged identities and activities, limiting potential security breaches and unauthorized access to critical systems, data, and resources.
Author

Leave a Comment