The Australian Cyber Security Centre (ACSC) issued the Essential Eight Maturity Model, which is a mandatory compliance for all Australian organizations. The fifth security control among the Essential 8 Security Controls, "Restrict Administrative Privileges", stands out as an important mitigation strategy. In the Essential Eight Maturity Model, reaching Level 3 Maturity necessitates placing this strategy into practice. Your organization could achieve this maturity level and enhance its overall security posture with a robust Privileged Access Management (PAM) solution. This also brings your enterprise in accordance with cutting-edge operational efficiency and compliance standards.
What are the Essential Eight Mitigation Strategies?
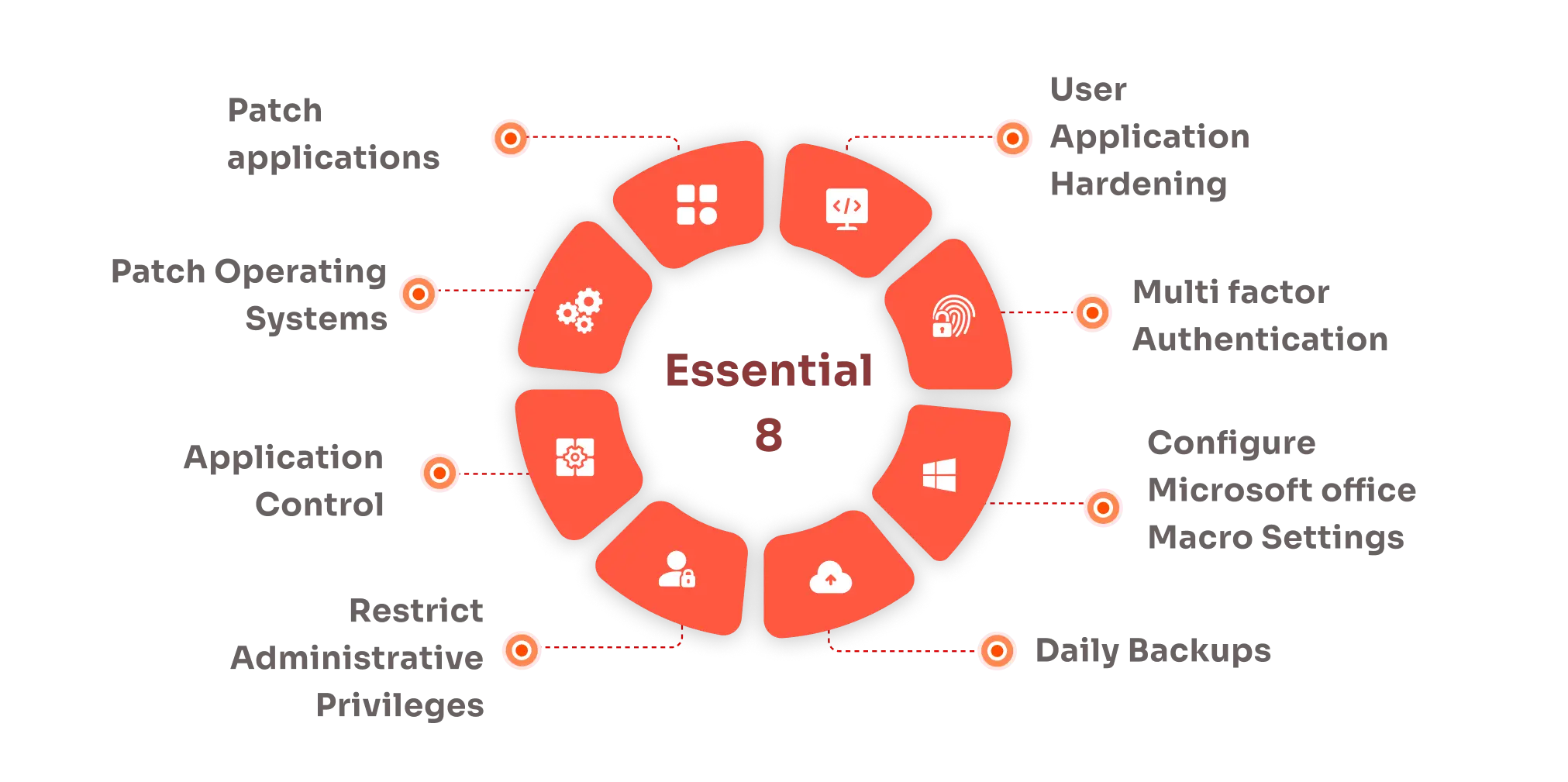
There are 8 mitigation strategies mandated by the Essential Eight compliance. Each strategy plays a significant role in preventing cyberattacks and upgrading the organizational defenses against potential attackers. Let’s take a look into each of the security controls and how they help in bolstering the security of your enterprise:
- Application Control: The purpose of the Essential 8 application control strategy is to prevent harmful or unauthorized apps from operating on the corporate network and to enable only trustworthy and whitelisted apps to function.
- Patch Applications: Ensuring efficient control and rapid mitigation of risks necessitates organizations to promptly implement software patches, run vulnerability scans, allocate workforce, analyze data, and implement appropriate measures.
- Restrict Microsoft Office Macros: Your organizations must eliminate unnecessary macros, restrict macro settings in Microsoft Office, and verify digital signatures before using them in order to avoid harmful macros harboring malicious code for cyber invasion.
- Application Hardening: This control includes measures restricting user applications from frequently interacting with unnecessary web-based content, such as blocking Flash and pop-ups in browsers and JavaScript on specific websites.
- Restrict Administrative Privileges: To stop attackers from escalating crucial operations and blocking important security settings and controls, ACSC advises defining privileged tasks, establishing separate privileged user accounts, and limiting admin access.
- Patch Operating Systems: Like patching apps, patching OS systems involves ensuring the patch is necessary and safe. Patches require regular checking for updates, analyzing vulnerabilities, and monitoring data in order to prompt swift action.
- Multi-Factor Authentication (MFA): In addition to conventional security measures, ACSC advocates the subsequent further steps of implementing MFA or Multi-Factor Authentication. It acts as an added layer of security that prevents unauthorized access to corporate networks, systems, and applications.
- Daily Backups: It is critical for your organization to safeguard its digital assets & prevent data loss with regular, secure backups, ensuring critical information remains recoverable in the event of any cyber invasion.
Restricting Administrative Privileges to Level Up the Essential Eight Maturity Model
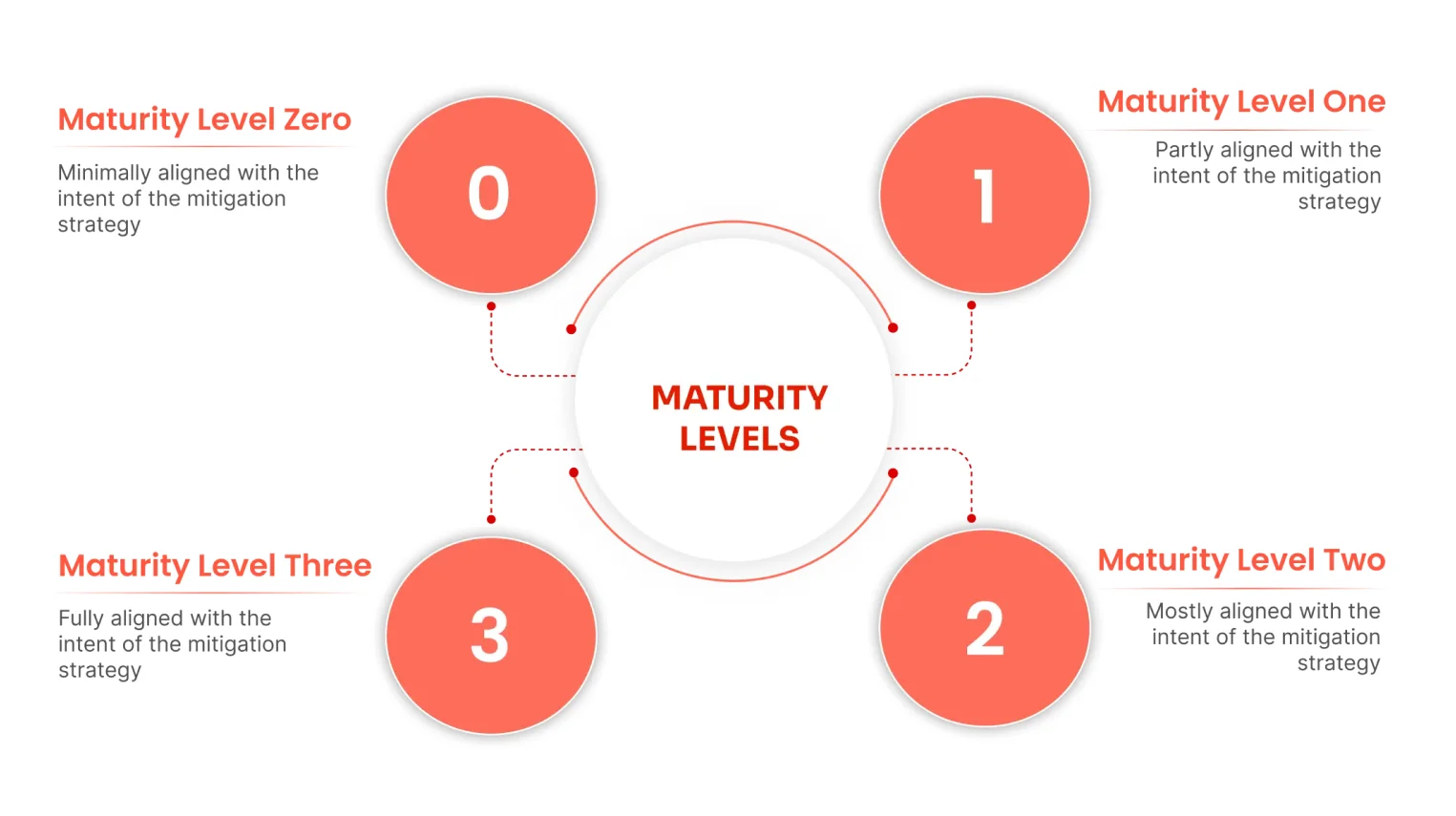
ACSC's Essential Eight Maturity Model is categorized into four maturity levels (0 to 3), each representing a higher level of security and resilience. Understanding these maturity levels can help your organization improve cybersecurity practices, enhancing overall security posture.
The Essential Eight Compliance (maturity level 2) is a mandatory requirement for all Australian non-corporate Commonwealth entities (NCCEs) subject to the Public Governance, Performance, and Accountability Act 2013 (PGPA Act). Essential Eight Maturity Levels 1, 2, and 3 should be examined first in order to ensure a holistic approach.
Your organization needs to develop a privileged access management strategy that should include restricting System Administrator Privileges, removing Local Admin Privileges, and protecting Privileged User Accounts. Let us understand how to implement privileged access management strategy in different maturity levels:
Maturity Level 0 & 1
In the Maturity Level 0, all eight of the Essential Eight Security Controls are not put into practice. Hence, the organization is vulnerable to common cyber threats and potential attacks. Whereas in the Maturity Level 1, although the Essential Eight mitigation strategies have been applied at a basic level, but there is still room for improvement as these security controls might not be fully optimized or cover all systems.
To ensure the least privilege and appropriate role groups, maturity level one organizations need to adopt a request validation policy for privilege delegation. Using an Application Control system, they can restrict admin accounts from connecting to internet services like email and web services. Admins will be provided with separate accounts in a dedicated environment while prohibiting basic user accounts. Also, admin accounts will not be able to access regular workstations.
Maturity Level 2
In addition to implementing all eight controls into practice, they are also customized according to the corporate environment in the Maturity Level 2. This entails more extensive system coverage, regular upgrades and evaluations, and more defensive layers. This is a mandatory level that all Australian organizations are required to achieve.
Maturity Level two organizations can effectively reduce privilege by revalidating issued privileges on a regular schedule, monitoring dormant accounts, and scrutinizing accounts that have been inactive for more than 45 days. A dedicated privileged environment is required to host admin operating environments, and each account is identified with unique credentials. To implement this seamlessly, an Agentless PAM solution can be helpful because it nullifies the need to deploy PAM agents at endpoints. Logging policies are set up to log privileged credentials and changes made to privileged groups and roles for Microsoft 365 and on-premises domains. Protecting credentials of privilege accounts by storing them in a secure Password Vault is advisable.
Maturity Level 3
At this final level, the cybersecurity posture is strong and sophisticated. The systems and processes incorporate all eight approaches, which are updated often, continuously monitored, and equipped with adaptable defenses against changing threats.
Organizations at this Level are required to audit administrative rights on a regular basis to ensure that the privileges are appropriate for any individual or service function and are not over-scoped. They would need to stop privileged accounts from using online services, email, and the internet. It is essential to have a Just-in-Time Privileged Access system, in which individuals must log in and out of privileges as required. It is important to monitor indications of compromise and take appropriate action when needed to log privileged user accounts and groups. A central configuration policy and SIEM system are essential as well.
5th Mitigation Strategy (Restrict Administrative Privileges) in a Nutshell
"Restrict Administrative Privileges," the fifth mitigation approach in the ACSC’s Essential Eight framework, is aimed at regulating and managing privileged admin access permissions within an organization's computer networks. This strategy is essential because compromised or misused administrator rights can result in catastrophic security breaches. Here's a quick overview of this technique:
Identity Governance
This is focused on limiting admin access and admin or privileged account controls. Limiting user access and admin access aligns with the core principles of identity governance, ensuring that access rights are closely aligned with the individual's role within the organization. Privileged account controls involve creating a clear distinction between normal user accounts and those with administrative privileges. This ensures that users have access only to the necessary resources.
Least Privilege
The principle of Least Privilege ensures that admins should receive only the required rights to carry out their responsibilities; wide or excessive privileges should not be granted. This method is crucial for maintaining a safe and regulated IT environment, where access is restricted to that which is absolutely required. Least Privilege is also essential for implementing a Zero Trust environment for organizations.
Account Restrictions
Account Restrictions focus on Privilege Escalation Control, which means, putting in place security measures that restrict or limit the ability of attackers to obtain higher-level privileges. This entails taking steps to prevent malware from acquiring admin privileges, while monitoring any behaviors that could indicate an attempt to escalate privileges.
Administrative Devices
Admin devices and accounts should be secured with robust authentication mechanisms like Multi-Factor Authentication (MFA). This security measure is essential for lowering the possibility of compromised admin accounts and crucial for effective admin device management.
Logging and Monitoring
This implies routinely reviewing and auditing the usage of administrator privileges, as well as maintaining surveillance on privileged accounts in order to detect any suspicious activity. Timely identification and response to threats depend primarily on efficient logging and monitoring.
How Can miniOrange PAM Solution Help You?
The miniOrange Privileged Access Management (PAM) solution provides holistic tools to manage, monitor, and audit every privileged session. Here is an overview of how miniOrange PAM can help you establish, secure, and manage Administrative Privileges within your organizational environment.
Allow, Restrict & Manage Applications
You can easily implement Application Control by assigning Just-in-Time privileges only to approved applications, scripts, tasks, and commands across both endpoints and servers. Enforce allow listing, block listing, greylisting, and more, implementing a pragmatic approach to application control.
Fortify User Applications
The miniOrange PAM helps you implement User Application Hardening by blocking the execution of child processes, code injection into other processes, and the creation of executable content. The solution also includes the ability to implement effective whitelisting, greylisting, and blacklisting, where unknown applications can be prohibited from executing, significantly reducing the endpoint attack vector.
Redefine Administrative Privileges
You can effectively limit privileged access to operating systems and applications based on user duties using the concept of least privilege while regularly revalidating the need for privileges. The miniOrange PAM solution enables you to remove local admin rights from day one, without impacting user productivity. In addition, get secure access control, auditing, alerting, and recording of any privileged account.
miniOrange provides a centralized solution that includes IAM (Identity & Access Management) & PAM (Privileged Access Management) functionalities and can effectively help you implement the Essential Eight Security Controls and level up the Maturity Model.
Author



Leave a Comment