How to use Single Sign-On for your ASP.NET MVC application?
There may come a time when you need to implement Single Sign-On onto your ASP.NET MVC application. It allows you to integrate your app with other systems and helps them work together as if they are one unified application.
Some of the benefits of doing this are an improved user experience, increased security, and reduction in costs. Users will be able to seamlessly access pages on any of these applications or systems after signing in only once.
Or, if you want to migrate your application, rather than having to rewrite it entirely, you can migrate it one service at a time. Implementing SSO between the two applications helps you effectively link them together as if they were one, after which you can migrate your app with ease. There are even more advantages discussed later in this article.
To understand how you can implement ASP.NET MVC Single Sign On, let us first understand what its components mean.
What is ASP.NET MVC?
ASP.NET MVC is composed of two parts: ASP.NET and MVC. The first is an open-source web application framework that can be used to produce dynamic web pages, applications, and services. The second is MVC, which stands for Model View Controller. It is an architectural pattern that is meant to achieve separation of concerns.
Together, they form a web application framework that eliminates the drawbacks of web forms like slow response times, issues in unit testing, and HTML customization.
Designing your application using the ASP.NET MVC framework allows you to benefit from both its components’ advantages. However, you still need to make it easier for users to sign in to your application and avail of its services in a hassle-free manner. Let’s see how we can do that.
What is SSO?
When a user wants to access secured services on your application, they have to enter their username and password once to authenticate themselves. In a situation where they want to access similar services over multiple applications connected or related to each other, they would be required to enter either the same or different usernames and passwords multiple times.
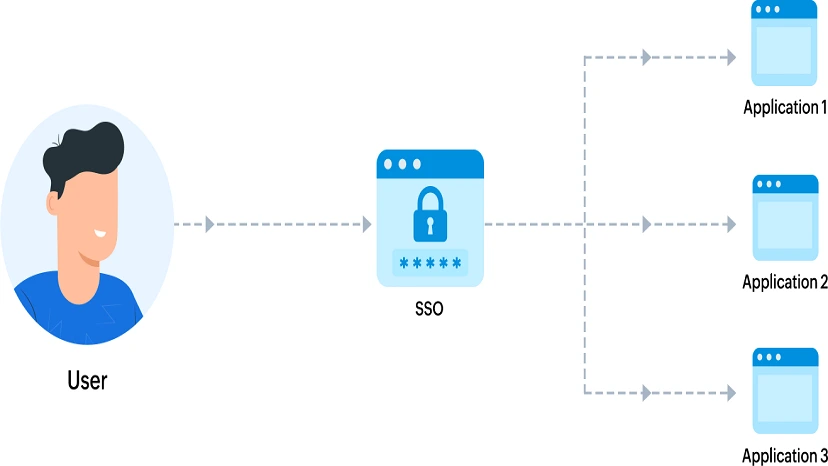
Single Sign-On (SSO) makes this process easier by using the same authentication ID and authorizing the user across multiple services. Because of SSO, as the name suggests, the user is required to sign in only once in a certain time window before the authentication token expires.
What are the types of SSO protocols?
For SSO to work, Service Providers (SP) and Identity Providers (IDP) must decide on an open standard protocol for how they will choose to exchange identity and authentication information with one another over the relevant applications.
Here are a few examples of these protocols:
OAuth: This is an open standard for token-based authentication and authorization, which is used to provide Single Sign-On (SSO). It allows an end user’s account information to be used by third-party services without exposing the user’s password. It serves as an intermediary on behalf of the end-user, providing the service with an access token that authorizes specific account information to be shared.
OpenID: This is one of the most popular authentication protocols, used by the likes of Google and Facebook. It is open standard and decentralized. Third-party Identity Providers (IdP) are used to authenticate users to Relying Parties (RP). It serves as an identity layer on top of OAuth, thereby functioning as an extension to it.
SAML: SAML uses session cookies in a browser that allows a user to access certain pages. It gives more control to enterprises to keep their SSO logins more secure. You can find a detailed explanation of SAML below.
Let’s take an in-depth look at SAML
SAML stands for Security Assertion Markup Language. Its main purpose in online security is to enable you to access multiple web applications using one set of credentials. It works by passing authenticated credentials between two parties: an Identity Provider (IDP) and a Service Provider (SP). Doing so makes the user experience simpler while also providing better security.
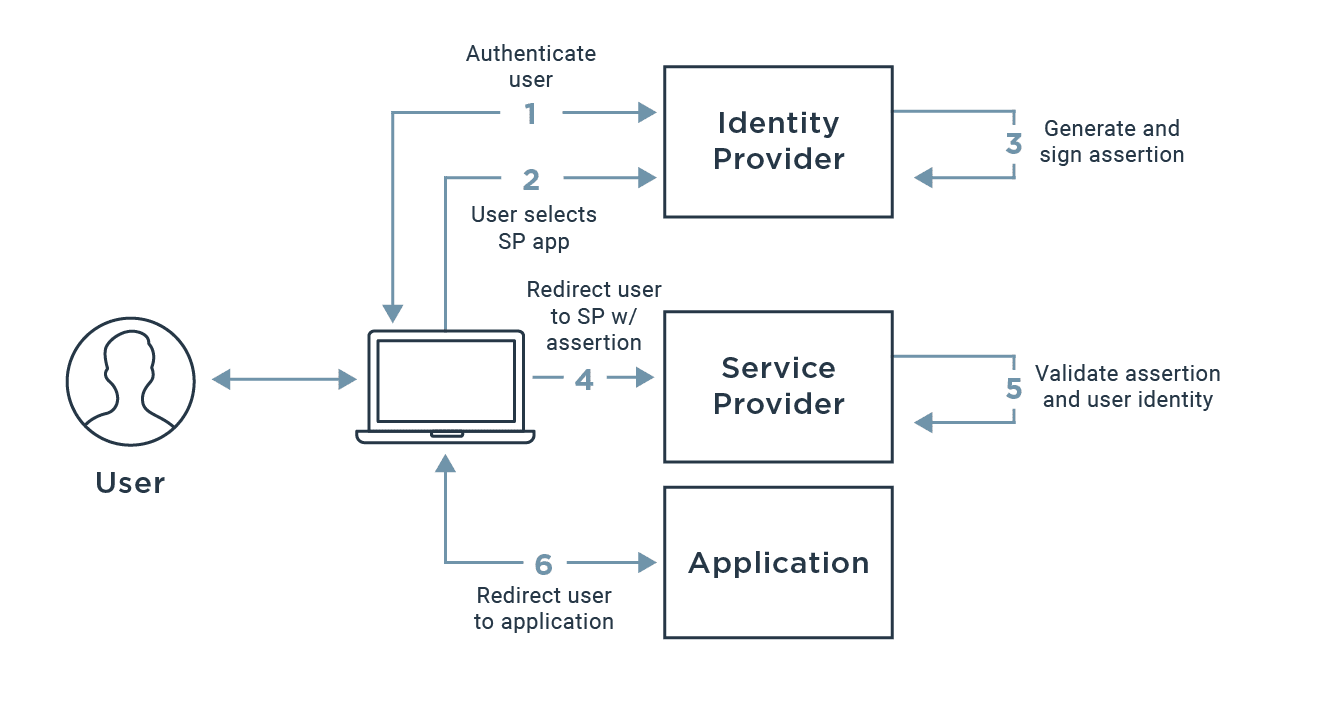
Where can we use SAML SSO?
The primary attribute of SAML is that it is used for authentication, not authorization. This means that a variety of applications, websites, and services that could be used to access and edit data from the service provider need to form a trusted relationship with the SSO website.
Now, when a user tries to access data from the service provider’s app, they’ll need to be authenticated at least once by entering a username and password before they can read or write onto this data. If, however, they have already done this once, then they will be granted access more directly. A SAML request will be generated by the application, asking to authenticate the user, to which the identity provider will respond with a SAML response.
This is particularly useful in situations where the service provider is offering their services across a wide range of applications. It inadvertently also increases the scope of the product by allowing a variety of third-party applications to offer their unique services using the same data.
For example:
- Data-driven statistics websites and applications for online multiplayer games.
- Social media applications and bulletin boards designed around the same topic.
- Online video streaming services with features for viewer engagement.
- Online software marketplaces like Steam that offer user analytics and metadata.
What are the benefits of using ASP.NET MVC Single Sign On?
Shorter development time: Using ASP.NET MVC Single Sign-On reduces development time by providing developers with a common authentication framework. It takes even more load off of them if the mechanism is independent.
Reduction in costs: Besides the fact that development time is reduced, support requests for forgotten passwords and IT help desk calls also go down, thereby lowering the overall costs.
Increased security: An important benefit of SSO is that it reduces the chance of users falling prey to phishing attacks. This is because the user is not trained to mindlessly enter their username and password everywhere. Furthermore, SSO systems usually force users to use secure communication channels. This means that only one place of authentication receives their credentials. The applications, however, don’t receive any specific information besides whether they should let the user in or not. This happens only once, resulting in a minimum transfer of sensitive information, which is naturally favorable.
Streamlined administration: The burden on the administrative system to manage user accounts is massively reduced with the implementation of SSO. Keep note, however, that SSO only takes care of authentication. The authorization of users based on their access privileges still needs to be set up separately.
Improved user experience: With ASP.NET MVC Single Sign On enabled, users don’t have to enter their usernames and passwords multiple times to access the same service across multiple applications and browsers.
Additional Sources:
Author


Leave a Comment