In today's rapidly evolving digital landscape, privileged accounts hold the keys to an organization’s most sensitive data and critical systems. These accounts, if not managed properly, pose a significant security risk, as they can become prime targets for cyberattacks. The misuse of privileged access has led to real-world breaches, exposing organizations to data theft, operational disruptions, and financial loss.
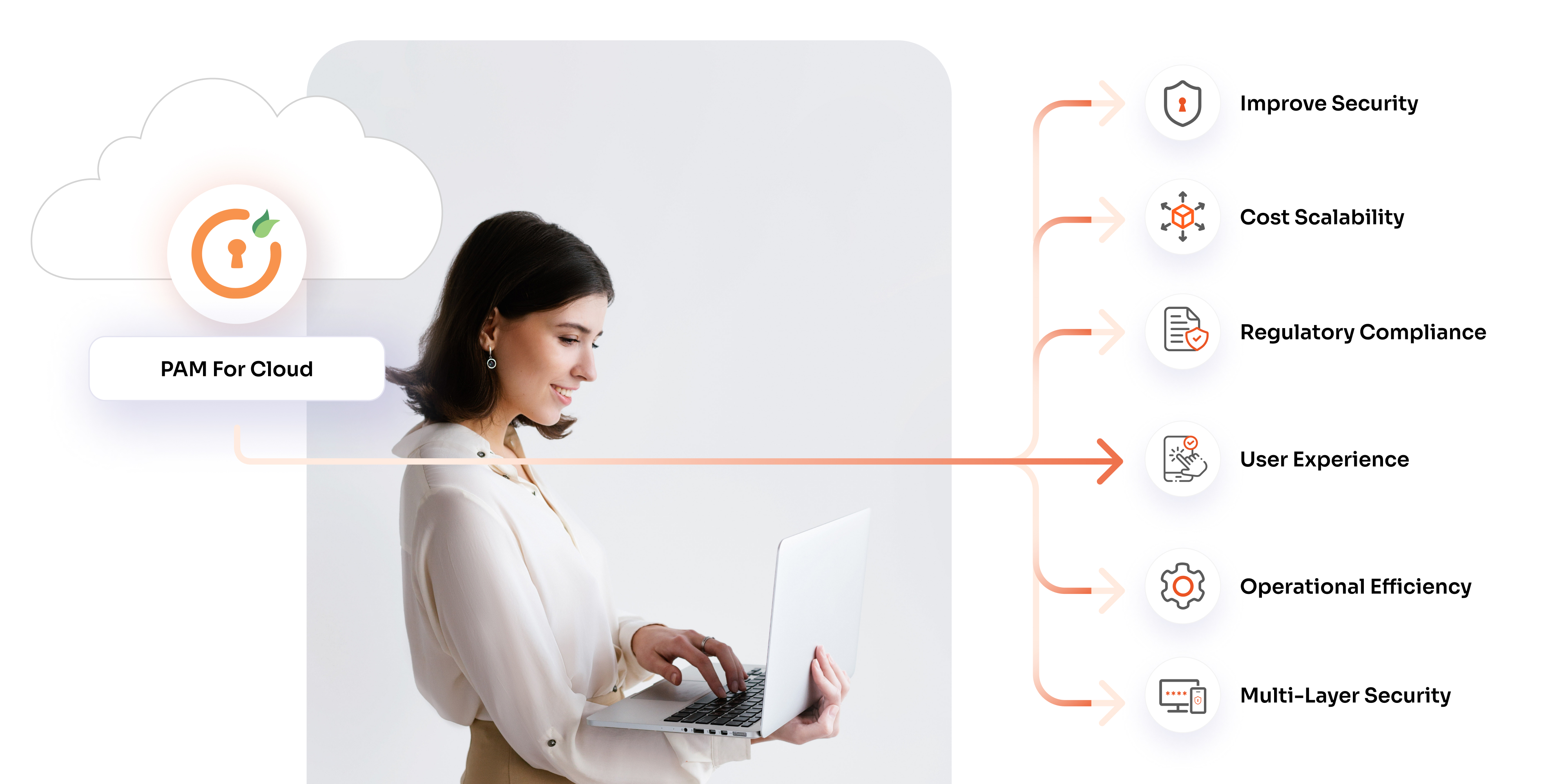
This is where the benefits of privileged access management (PAM) come into play. By implementing robust PAM solutions, businesses can safeguard their critical infrastructure, mitigate insider threats, and reduce vulnerabilities. In this blog, we’ll uncover the top privileged access management benefits for 2024 and why they are essential for a secure digital future.
Top 10 Most Benefits of Privileged Access Management (PAM)
Privileged Access Management (PAM) has become an essential security measure for organizations that aim to protect their sensitive systems and data. The benefits of privileged access management solutions are extensive, providing critical defenses against cyber threats while improving operational efficiency. Let’s explore the top 10 privileged access management benefits for 2024.
1. Enhanced Visibility Across the Network
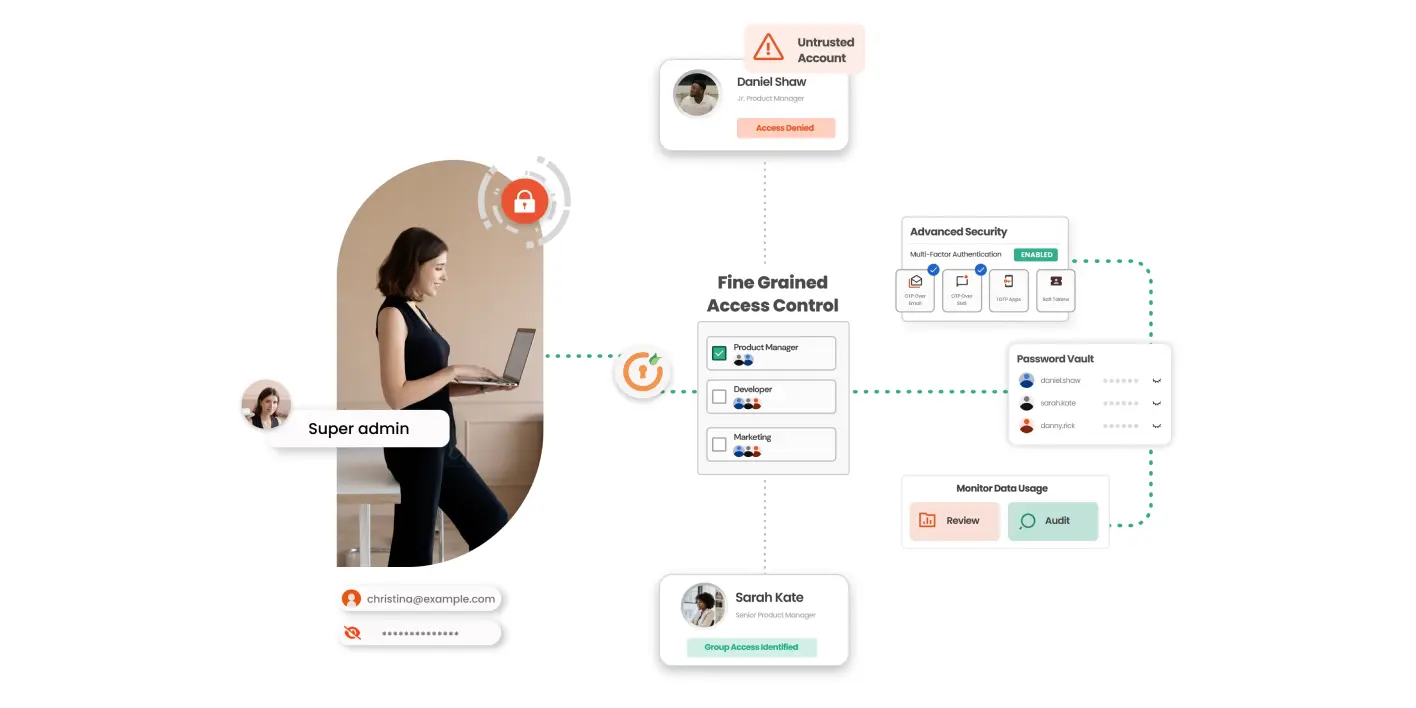
One of the top benefits of privileged access management is its ability to provide complete visibility into your network, allowing IT admins to monitor and record activities within privileged accounts and sessions. By recording privileged sessions, PAM helps prevent unauthorized access, making it easier to enforce a Zero Trust security model. This heightened oversight helps pinpoint and mitigate potential security breaches swiftly.
2. Prevents Privilege Abuse and Misuse
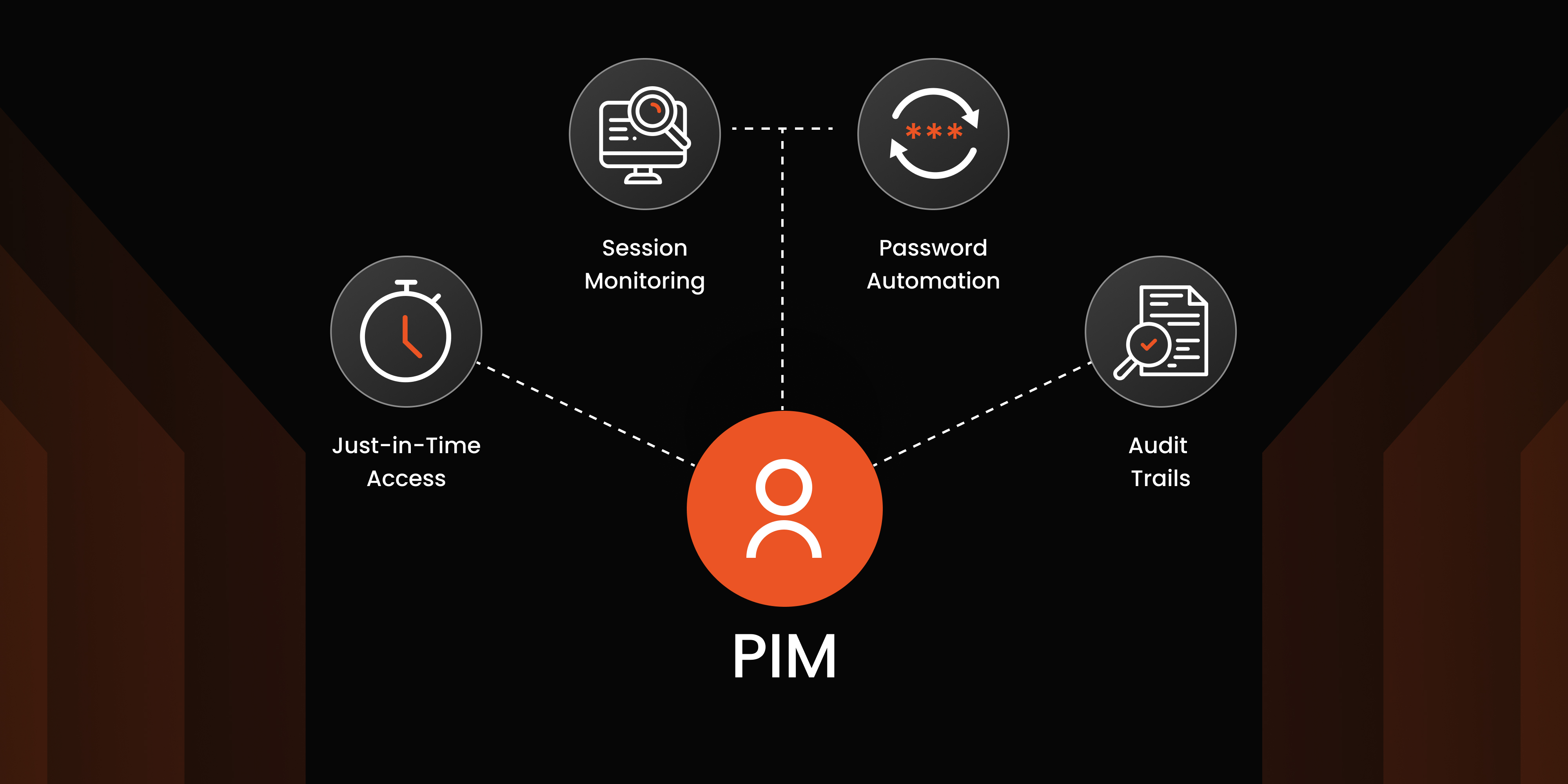
Privileged accounts are prime targets for abuse when not properly managed. Privileged access management solutions prevent privilege misuse by enforcing policies like the Principle of Least Privilege (PoLP) and Zero Standing Privilege. Key PAM features such as Privileged Session Management (PSM) and Just-In-Time (JIT) access help monitor, record, and control privileged sessions, reducing the risk of internal misuse.
3. Simplifies Regulatory Compliance
Regulatory frameworks such as HIPAA, PCI DSS, and SOX mandate that organizations manage and monitor access to privileged accounts. By enforcing least privilege access and providing robust auditing capabilities, PAM solutions ease the compliance burden for organizations. PAM solutions make it easier to comply with these regulations by enforcing the Principle of Least Privilege and enabling auditing capabilities. Organizations can meet compliance requirements efficiently, minimizing the risk of non-compliance penalties.
4. Improve Employee Productivity
With a PAM solution, IT teams can streamline the delegation of access through centralized management tools, saving time and increasing efficiency. Features like password vaulting, secure remote access, and session management make it easier for employees to perform their duties securely, enhancing overall productivity without compromising security.
5. Minimizes Configuration Errors
Misconfigurations of privileged accounts can lead to excessive access and security risks. Privileged access management solutions help minimize these errors by automating access management, ensuring that users have only the necessary privileges. This automation upholds the Principle of Least Privilege, reducing the chance of human error and security gaps.
6. Reduces the Attack Surface
By limiting user privileges and enforcing Zero Trust principles, PAM solutions significantly reduce an organization’s attack surface. Cybercriminals find it more difficult to exploit systems when access is strictly controlled. Features like password vaulting also contribute to a stronger security posture by enforcing better password management and reducing credential-based attacks.
7. Eases Breach Containment
If a breach occurs, PAM helps contain it quickly by limiting lateral movement within the network. Because users only have access to the systems they need, a compromised privileged account won’t grant attackers unlimited access to your network. Privileged access management ensures tighter control over privileged sessions, making it easier to contain and remediate breaches.
8. Helps fulfill Cyber Insurance Requirements
Cyber insurance providers often require organizations to demonstrate strong security controls. Privileged access management solutions help satisfy these requirements by offering enhanced visibility, security, and control over privileged accounts. This can help organizations qualify for better coverage or lower premiums.
9. Reduces Long-Term Costs
While implementing a PAM solution may have upfront costs, the long-term savings are significant. Effective privileged access management reduces the likelihood of costly data breaches, minimizes downtime, and lowers the risk of regulatory fines. Additionally, it can lead to reduced cyber insurance premiums, ultimately saving your organization money.
10. Supports Future Security Initiatives
As organizations adopt more advanced security frameworks like Zero Trust, PAM plays a pivotal role. With features like JIT access, session monitoring, and password management, privileged access management solutions provide the foundation for secure digital transformation, ensuring that only the right users have access to the right resources at the right time.
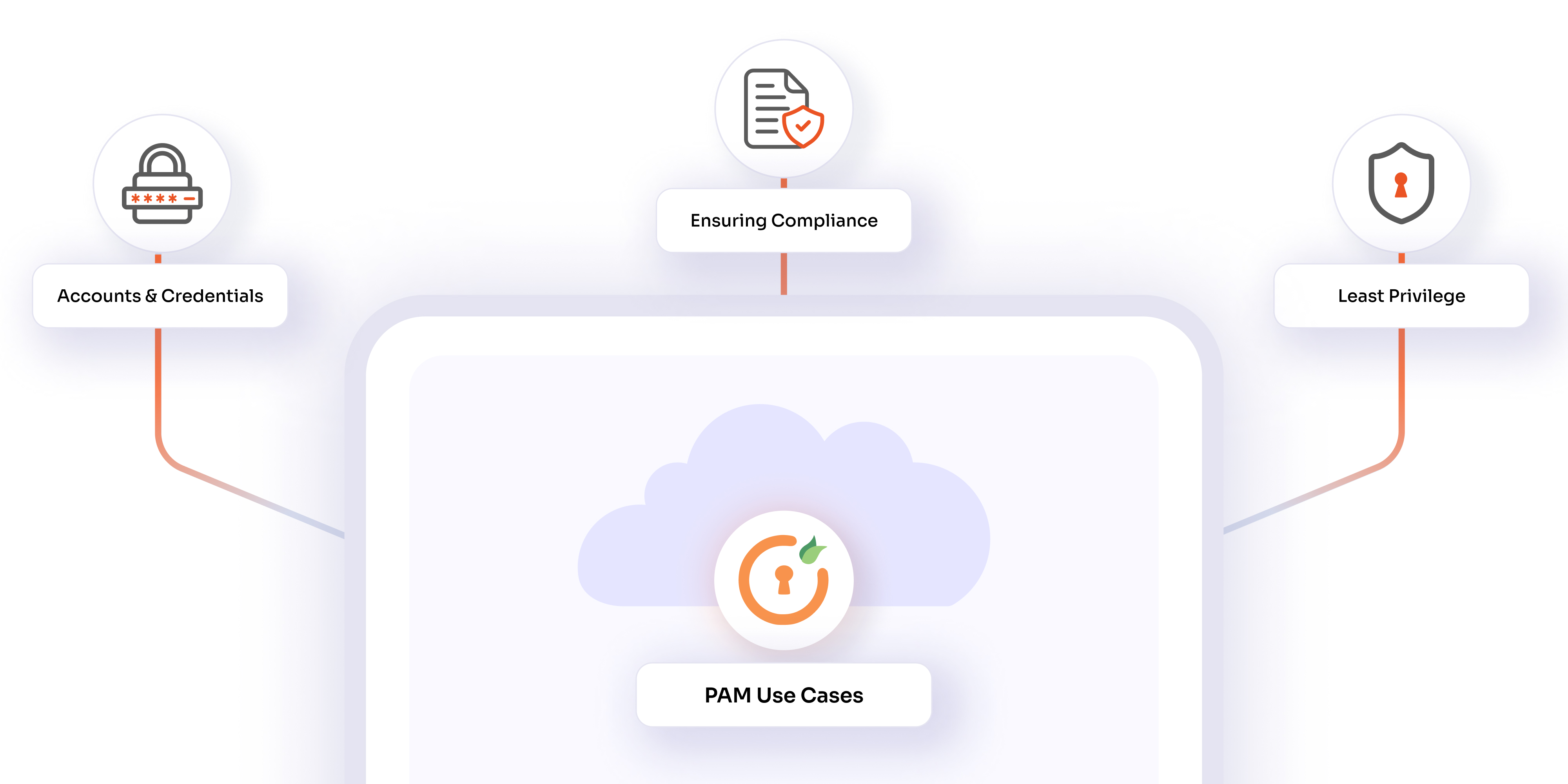
Use Cases of Privileged Access Management
- PAM in Financial Institutions: In banks, where security and privacy are critical, PAM systems ensure that only approved staff can access sensitive financial data. This reduces the chances of fraud and helps banks meet strict regulatory standards.
- PAM in Healthcare: Hospitals use PAM to control who can view and edit patient records, protecting personal health information. This not only keeps patient data secure but also ensures hospitals comply with privacy laws like HIPAA.
- PAM in Government: Government agencies use PAM to manage access to vital systems and confidential data, preventing unauthorized access and ensuring that national security isn't compromised. This is crucial for protecting the integrity of everything from electoral processes to national defense systems.
How to Choose the Right PAM Solution for Your Business?
When selecting the right Privileged Access Management (PAM) solution, it's essential to focus on features that match your specific security needs. Look for capabilities like privileged session management, password vaults, endpoint management, and granular access controls to ensure comprehensive protection for your sensitive data. Evaluate the scalability of the solution to ensure it can grow with your business and its ability to integrate easily with your existing IT infrastructure. Additionally, the quality of vendor support and regular software updates are crucial for staying ahead of evolving security threats. A well-rounded PAM solution should not only meet your immediate requirements but also provide long-term security and support as your business evolves.
Author



Leave a Comment