PAM for Linux and Unix Systems manages sensitive elements like credentials, SSH keys, and service accounts. While most PAM solutions are great in the Windows environments, effective PAM for Linux, and Unix, is essential to safeguard root privileges and other critical components.
What is privileged access in Linux?
Privileged access in Linux refers to the special permissions granted to certain users, allowing them to perform critical tasks that affect the system's operation and security. These permissions are often associated with the "root" user or other accounts that can modify system files, manage user accounts, and control system settings. Proper Linux privileged access management is crucial to prevent unauthorized actions, maintain security, and ensure compliance.
Without careful oversight through effective privileged access management tools, these elevated permissions can lead to security vulnerabilities and make it difficult to track and control user activities. Managing privilege access management for the Linux framework effectively is essential for maintaining a secure and compliant system environment.
What are root privileges in Linux?
Root privileges in Linux refer to the highest level of access a user can have, allowing unrestricted control over the system, including administrative actions and access to all files and configurations.
Importance and Risks of Root Access
Root access is crucial for system administration but poses significant security risks if misused, potentially leading to unauthorized data access and system disruptions. Effective privileged access management (PAM) Linux frameworks mitigate these risks.
Typical Use Cases for Root Privileges
Root privileges are used for installing software, configuring system settings, managing user accounts, and accessing critical system files. Implementing Linux PAM, Linux access management, and Linux endpoint management ensures secure and efficient handling of root privileges, essential for robust privileged access management Linux and privileged access management Unix systems.
Sharing Root Privileges in Linux Environments
Methods of Sharing Root Access
In Linux environments, root access can be shared using the 'su' (switch user) and 'sudo' (switch user and do) commands. The 'su' command allows users to switch to the root user if they possess the root credentials. Conversely, the 'sudo' command lets users run commands with root privileges without needing the root password, elevating the user's permissions temporarily.
Risks Associated with Shared Root Access
Sharing root access poses significant security risks. Unauthorized users with root privileges can make critical changes, access sensitive data, and potentially compromise the entire system. Without proper privileged access management of Linux, these activities can go unmonitored, leading to severe security breaches.
Best Practices for Securely Sharing Root Privileges
To securely share root privileges, implement PAM (Privileged Access Management) for Linux. This involves regulating, customizing, and auditing root access. Using endpoint management and access management solutions ensures that only authorized users have elevated permissions, and their actions are continuously monitored. This structured approach enhances security and minimizes the risks associated with shared root access.
Why should Organizations Protect Their Linux Environments?
Privilege Escalation Attacks Organizations must protect their Linux environments to prevent privilege escalation attacks. When a user account is used to perform root operations, it can lead to unauthorized access to sensitive endpoints and resources. Implementing strict access control policies and workflows ensures that admins can grant secure, time-limited access to critical systems, reducing the risk of such attacks.
Rogue Insider Threats
Rogue insider threats are a growing concern, with insiders weaponizing standing privileges to control IT ecosystems. To mitigate this risk, organizations need to establish clear boundaries for privileges shared across the Linux network. Eliminating standing privileges helps reduce the potential for rogue insiders to exploit their access.
Third-party Vendor Privilege Abuse
Collaborating with third-party vendors often involves granting additional privileges. If these privileges are unnecessary or forgotten, they can lead to privilege abuse attacks. Protecting Linux environments involves carefully managing and monitoring third-party access to ensure that only necessary permissions are granted, thereby preventing potential abuse.
How to Manage Linux Security in 3 Steps
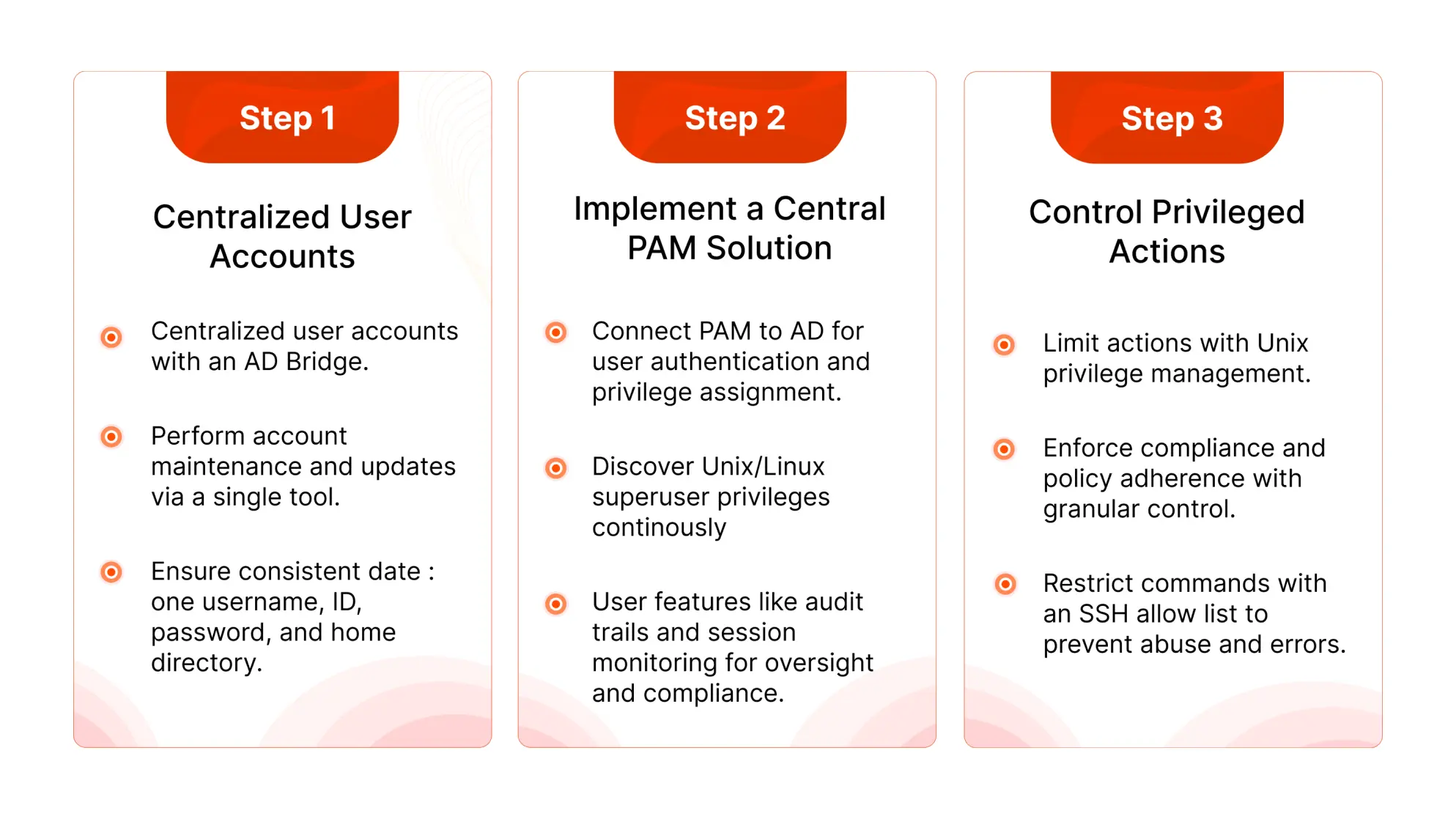
Step 1: Centralize User Accounts
The first step in managing Linux security is to centralize user accounts. In a Windows environment, Active Directory (AD) allows for this unification. However, Unix and Linux devices often struggle to integrate with AD due to different authentication protocols. Using an AD bridge can extend Group Policy to non-Windows platforms, allowing you to perform account maintenance and password updates through a single tool.
This ensures consistent data across all systems, with each user having one username, one ID, one password, and one home directory.
Step 2: Implement a Central PAM Solution
With identity unification in place, the next step is to implement a central Privileged Access Management (PAM) solution. This solution connects to your AD and allows you to authenticate users and assign privileges easily. PAM solutions enable the ongoing discovery of Unix/Linux superuser privileges, increasing accountability and enforcing consistent management.
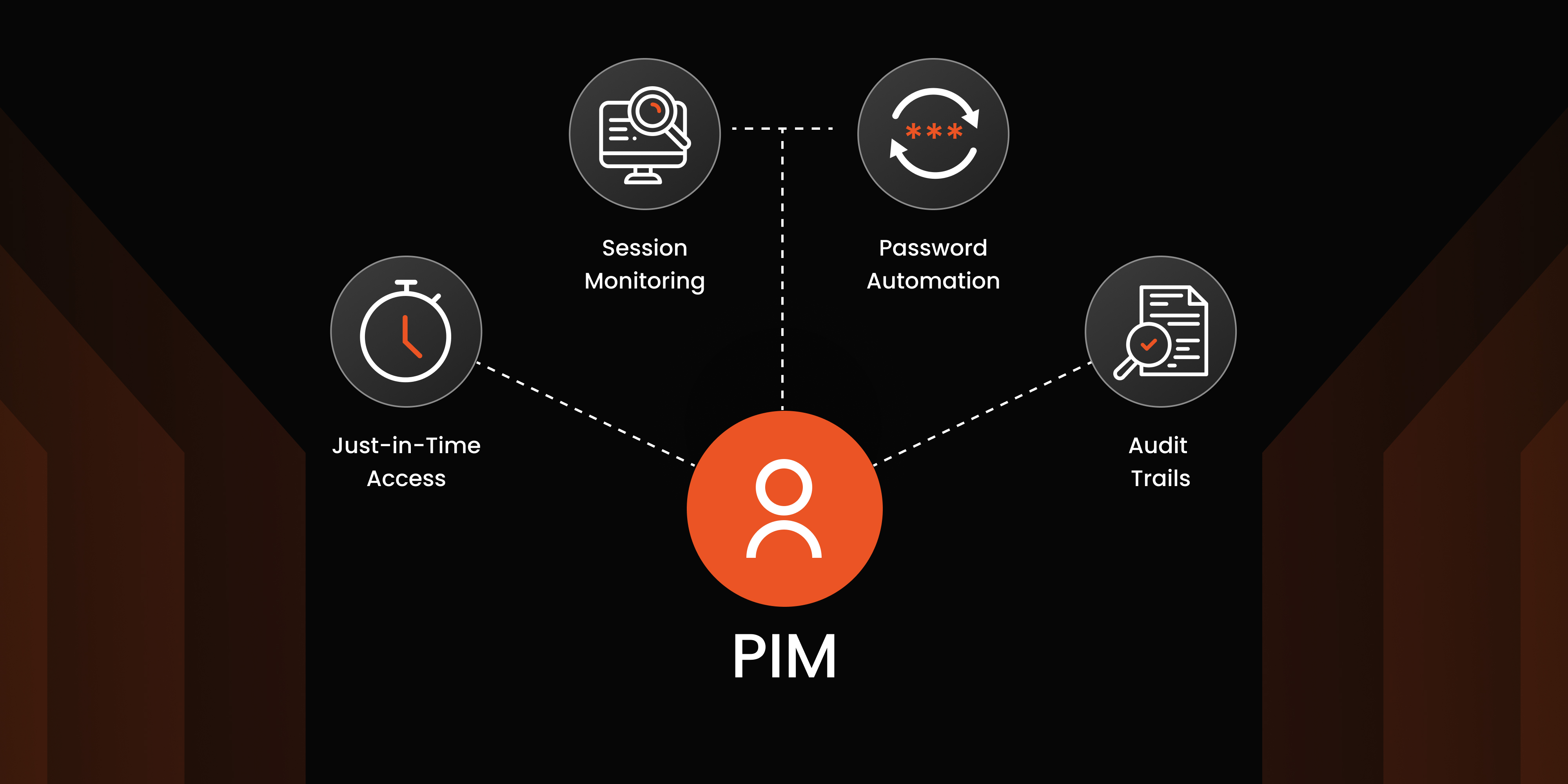
Features such as immutable audit trails and enhanced controls, like session monitoring and recording, provide oversight and simplify reporting and compliance. This is crucial for effective privileged access management Linux.
Step 3: Control Privileged Actions
Once users are authenticated and logged in, Unix privilege management controls what actions they can take. Granular control of root credentials limits privileges while meeting compliance regulations and policies for Unix Superuser Privilege Management (SUPM).
By restricting commands based on defined policies and limiting superuser permissions, you reduce the risk of privileged account abuse or accidental errors. For instance, an SSH command allowlist lets admins log in as root but restricts them to a set of predefined commands, ensuring they can perform necessary tasks without overreaching their permissions.
How Can Enterprises Ensure Privileged Access Security in Their Linux and Unix Environments?
To secure privileged access in Linux and Unix environments, enterprises can implement a Privileged Access Management (PAM) solution that provides comprehensive governance over user permissions and system access. Here's how this can be achieved:
1. Secure Account Onboarding
The first step is to periodically discover and onboard all Linux endpoints within the enterprise network. By centralizing these machines on a single platform, PAM solutions enhance visibility across what might otherwise be siloed Linux networks. These endpoints can then be grouped based on organizational hierarchy, ensuring that access is managed according to specific roles and responsibilities.
2. Automated Remote Password Management
Once endpoints and associated accounts are onboarded, enforcing robust password policies is essential. PAM solutions allow administrators to automate password resets, using native password generators to rotate passwords on a scheduled or on-demand basis. This automation not only strengthens security but also provides real-time auditing of password-related activities, such as resets, sharing, and check-outs, ensuring that all actions are tracked and compliant with internal security policies.
3. Seamless Privilege Escalation and Command Control
For managing privileged access, PAM tools offer features like Just-in-Time (JIT) access, allowing temporary access to privileged accounts for a limited period. After this period, access is automatically revoked, and passwords are reset, preventing unauthorized access. Additionally, command control enables IT administrators to restrict or allow specific SSH commands, ensuring that users only execute approved actions. This approach allows non-root users to perform necessary tasks with elevated privileges without directly accessing root credentials.
By integrating these strategies—secure onboarding, automated password management, and controlled privilege escalation—enterprises can effectively implement Linux-privileged access management. This not only enhances security but also ensures compliance and operational efficiency across their Linux and Unix environments.
Best Practices for Linux Privileged Access Management
Implementing robust practices for Linux-privileged access management is crucial for maintaining the security and integrity of your IT environment. Here are some best practices to ensure effective management:
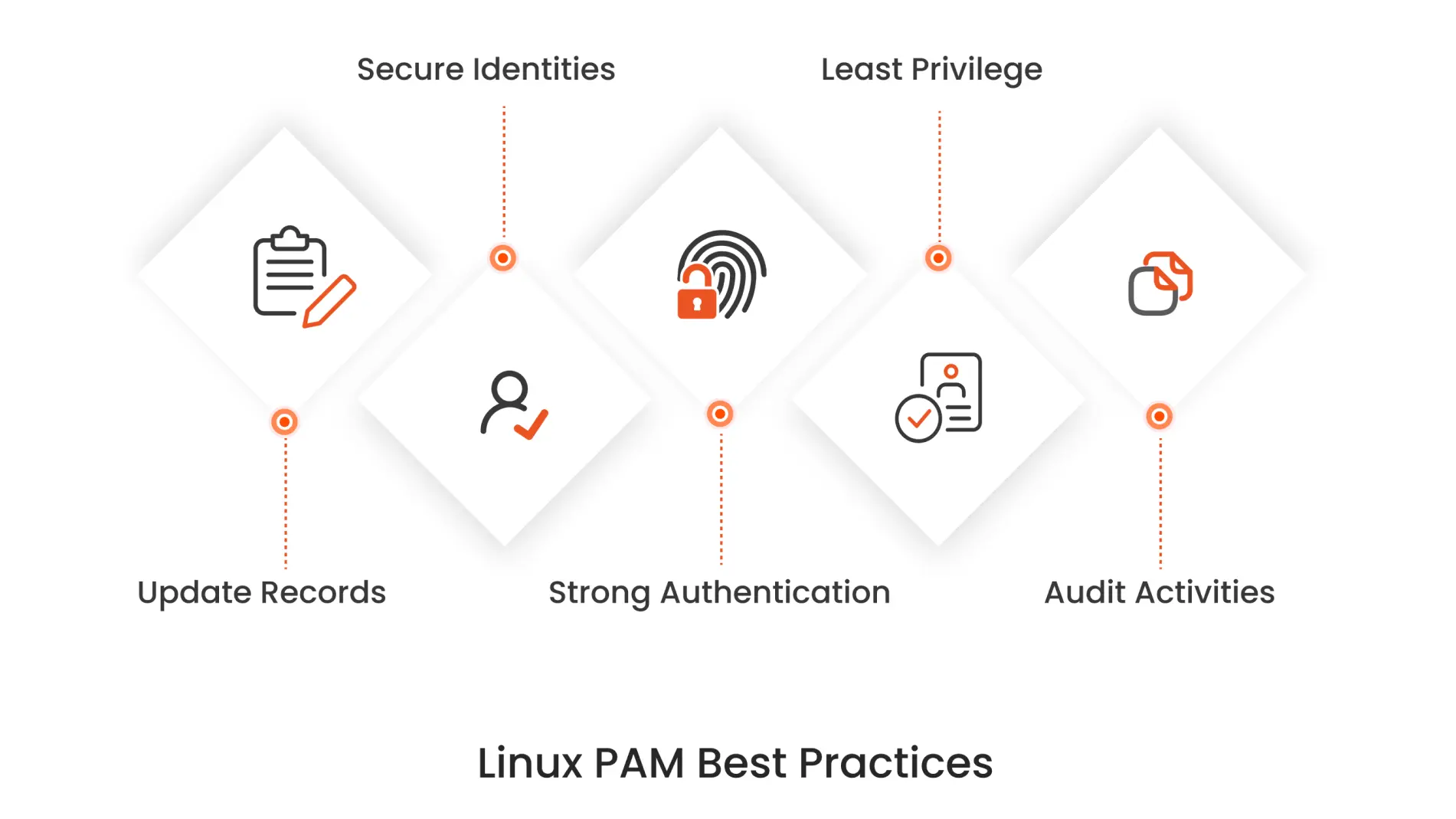
1. Maintain an Updated Record of Privileged Accounts
Regularly track and update a comprehensive record of all active privileged accounts within your Linux environment. This practice ensures that you have visibility over who has elevated access, allowing you to quickly identify and manage any unauthorized or outdated accounts.
2. Secure Privileged Identities in an Encrypted Vault
Store sensitive credentials, such as passwords and SSH keys, in a secure vault that uses standardized encryption algorithms. This ensures that your privileged Linux identities are protected from unauthorized access and potential breaches.
3. Implement Strong Authentication and Password Policies
Secure your Linux endpoints by enforcing strict password policies. This includes regular password resets, generating strong SSH key pairs, and automatically resetting these credentials after a single use. These measures help minimize the risk of credential compromise and unauthorized access.
4. Apply the Principle of Least Privilege
When sharing access to Linux endpoints, applications, and resources with third-party collaborators, always follow the principle of least privilege. Grant the minimum necessary permissions required for them to perform their tasks, and promptly revoke any standing privileges once they are no longer needed to prevent unnecessary exposure.
5. Audit and Record All Privileged Activities
Conduct regular audits and maintain detailed logs of all actions performed within your Linux environment, such as user SSH sessions, password resets, and privilege sharing. This not only aids in monitoring and preventing unauthorized activities but also provides crucial data for executing immediate corrective measures when needed.
By adhering to these best practices, organizations can strengthen their Linux-privileged access management framework, ensuring that sensitive information is protected, and access is controlled and monitored effectively.
Secure Your Linux Endpoints with miniOrange – Start Today!
Implementing effective Linux-privileged access management is essential for safeguarding critical systems and ensuring compliance. With miniOrange's PAM solutions, organizations can achieve seamless integration and comprehensive security. By centralizing user accounts, automating password management, and controlling privileged actions, miniOrange helps enterprises maintain robust security and operational efficiency.
This comprehensive approach to Linux privileged access management enhances visibility, enforces strict access controls, and mitigates risks associated with privileged access, making it an indispensable solution for modern IT environments.
Author




Leave a Comment