What is IAM?
Identity and Access Management (IAM) is a framework of policies, processes, and technologies designed to ensure that the right people have the right level of access to the right resources at the right time, and for the right reasons. Essentially, IAM is about securing digital identities and regulating access to sensitive information and systems within an organization. It plays a critical role in maintaining security, especially as organizations manage increasing amounts of data and access points. Effective IAM is essential for adopting a Zero Trust security framework, which operates on the principle of "never trust, always verify." By ensuring that only authorized users have access to specific resources, IAM helps organizations comply with regulatory requirements and significantly reduces the risk of cyber threats like ransomware and privilege escalation. Overall, we can say that IAM not only protects against unauthorized access but also strengthens overall cybersecurity posture, making it an important aspect of any organization's security strategy.
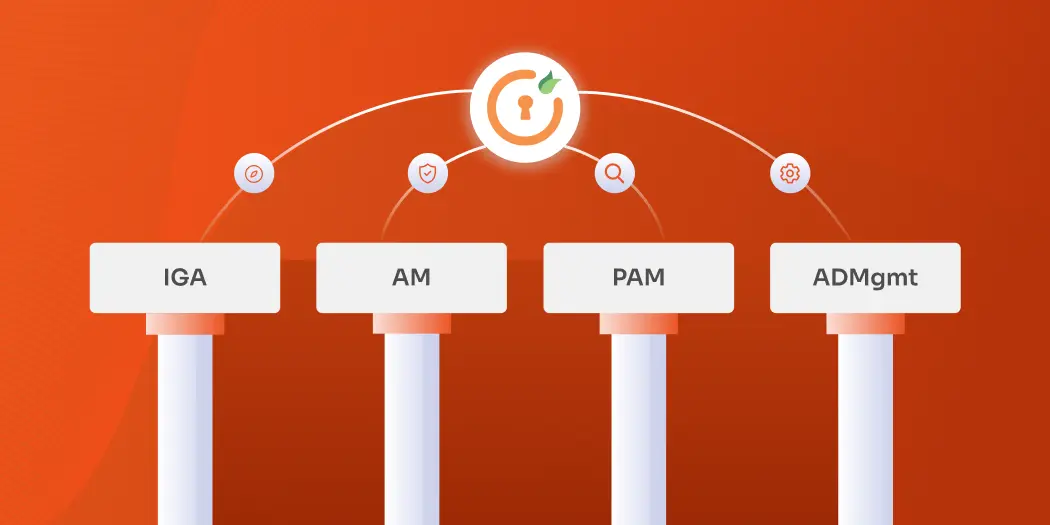
The Four Pillars of IAM
IAM is a comprehensive framework anchored by four key components: IGA, AM, PAM, and ADmgmt
1. Access Management (AM)
Access Management (AM) is a core component of IAM that focuses on controlling and managing how users access resources within an organization. It ensures that users have the appropriate permissions to perform their roles while safeguarding sensitive data and systems from unauthorized access.
Key features of access management include centralized role and permission management, which allows administrators to define and manage user roles and access rights from a single, unified platform. This centralization simplifies the process of assigning and adjusting permissions as users' roles within the organization evolve. AM systems also support multiple authentication protocols, enabling secure access across diverse environments and applications.
Additionally, Access Management implements Role-Based Access Control (RBAC), which restricts access based on the user’s role within the organization, ensuring that they only have access to the resources necessary for their job functions. To further enhance security, AM often incorporates Multi-Factor Authentication (MFA), requiring users to provide multiple forms of verification before gaining access. Another valuable feature is temporary privilege assignment, which grants users elevated access for a limited time, ensuring that higher-level permissions are not misused or left unchecked.
2. Privileged Access Management (PAM)
Privileged Access Management (PAM) is a critical aspect of IAM that focuses on securing and managing privileged accounts, as accounts/ users with elevated access rights can potentially cause significant harm if compromised. PAM plays an important role in protecting these high-risk accounts from unauthorized access, misuse, and cyber threats.
Key features of PAM include centralized management of privileged accounts and credentials, ensuring that all privileged access is controlled and monitored from a single platform. This centralization helps prevent the misuse of privileged accounts by tightly regulating who can access critical systems and data. PAM also provides fine-grained permissions, allowing organizations to assign the minimum level of access necessary for users to perform their roles, thereby reducing the attack surface.
In addition, PAM supports customized approval workflows that require specific authorization before privileged actions can be taken, adding an extra layer of security. Automated password rotation is another essential feature, regularly changing passwords for privileged accounts to minimize the risk of exposure. PAM also includes session monitoring and auditing, which track and record all activities performed during privileged sessions, enabling real-time oversight and providing a detailed audit trail for compliance and forensic purposes.
3. Active Directory Management (AD management)
Active Directory Management (ADMgmt) focuses on managing identities and access within an organization through Microsoft Active Directory (AD). It plays a crucial role in controlling and securing user access to network resources, applications, and services, making it an essential part of any IAM strategy.
Key features of ADMgmt include seamless integration with cloud identity providers and other IAM components, allowing organizations to manage identities across both on-premises and cloud environments efficiently. ADMgmt also automates the provisioning of AD users and groups, ensuring that user accounts are created, updated, and deactivated as needed. This automation is complemented by robust monitoring, auditing, and reporting tools, which provide visibility into user activities and help maintain security and compliance.
ADMgmt also enforces role-based access control (RBAC) within Active Directory, ensuring that users have access only to the resources they need based on their roles. Additionally, it provides protection against common Active Directory shortcomings, such as misconfigurations and unauthorized access, by implementing best practices and security measures to strengthen AD’s overall security posture.
4. Identity Governance and Administration (IGA)
Identity Governance and Administration (IGA) is an important aspect of IAM, focusing on the centralized management and oversight of user identities and their access rights within an organization. IGA ensures that only authorized individuals have the appropriate access to systems and data, helping to maintain security and compliance across the enterprise.
Key features of IGA include automated workflows that streamline the process of access request management, provisioning, and de-provisioning of user accounts. This automation reduces the manual workload and minimizes errors, ensuring that users receive the right level of access promptly. IGA systems integrate seamlessly with directories and other enterprise systems, allowing for efficient synchronization of identity data across the organization.
IGA also provides robust tools for entitlement management, which defines and controls what resources users can access based on their roles. It also enforces Segregation of Duties (SoD) policies to prevent conflicts of interest and unauthorized access. Access review workflows, role-based access management, and powerful analytics and reporting tools are also integral to IGA, providing visibility into who has access to what, ensuring compliance with regulations, and enabling informed decision-making regarding access rights.
Key Aspects of IAM Solutions
When evaluating IAM (Identity and Access Management) solutions, several key aspects should be kept in mind for efficient identity management. User Management: This involves tracking and managing every user within the organization, including their roles, permissions, and access rights. Effective user management ensures that each user has the correct level of access to perform their duties while minimizing the risk of unauthorized access. Authentication & Authorization: This component governs how users gain access to resources and systems. It includes mechanisms for verifying user identities (authentication) and determining what resources they can access (authorization). User Reviews: Regularly auditing user access is essential to maintaining security. Periodic reviews help ensure that users have the appropriate access for their current roles and that any unnecessary or outdated permissions are revoked. This process reduces the risk of privilege escalation and unauthorized access. Onboarding and Offboarding: Streamlining the process of adding and removing users is crucial for maintaining security and operational efficiency. Onboarding ensures that new users are quickly granted the access they need, while offboarding ensures that access is revoked when a user leaves the organization, reducing the risk of lingering access.
Conclusion
For organizations looking to further strengthen their IAM approach, considering a cloud-based Identity Management Platform is a wise investment. Such a platform offers seamless integration of all IAM components, providing centralized control and improved efficiency. miniOrange offers a robust Unified Identity Platform that can help your organization implement a comprehensive IAM strategy, ensuring that your digital environment remains secure and well-managed.
Author


Leave a Comment