What is Adaptive Authentication?
Standard authentication methods, including Multi-Factor Authentication (MFA), ask users for specific credentials whenever they try to log in or access corporate resources. While MFA provides better security by requiring additional credentials, such as a code from a smartphone app, it can still be vulnerable to cyberattacks if users always log in with the same credentials. Cybercriminals can potentially acquire or hack these credentials and use them to gain access.
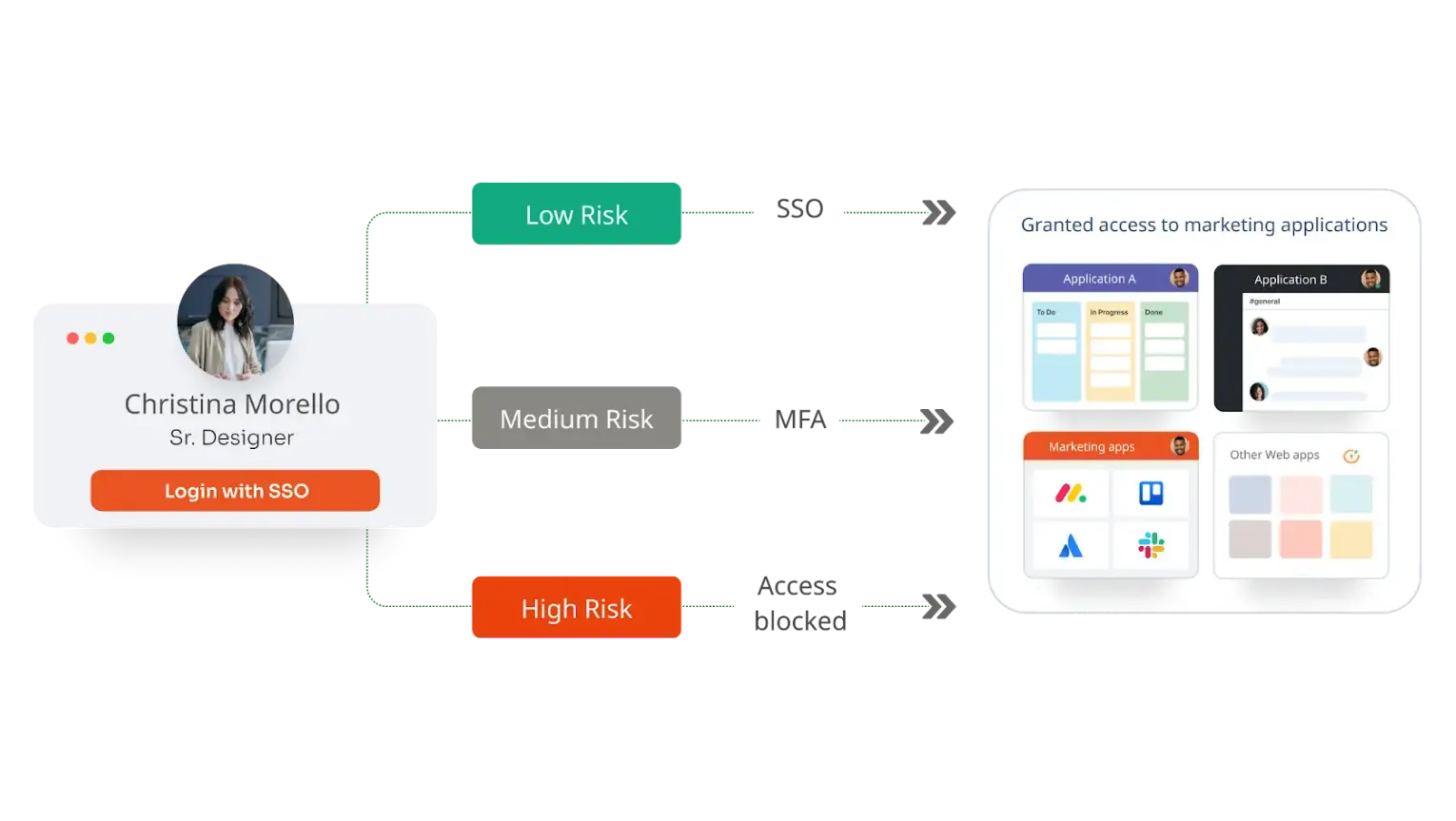
Adaptive Authentication changes this approach by dynamically adjusting the authentication process based on contextual risk factors, such as the user’s IP address, location, device, behaviour, and time of access. This ensures higher security while maintaining a smooth user experience. In low-risk scenarios, users can access resources seamlessly using their username and password. However, in higher-risk situations, the system requires additional verification steps or denies access altogether.
How Does Adaptive Authentication Work?
Adaptive Authentication or Risk-Based Authentication creates a unique profile for each user, consisting of attributes such as geographical location, registered devices, job role, and IP address. When a user attempts to authenticate, their profile is assessed, and the system assigns a risk score based on factors like the device used, location, and time of access. Authentication requirements are then adjusted according to this risk score.
For instance, if a user tries to access applications from an unregistered device, they may be prompted to register it. If logging in from an unusual location, they might need to answer a security question. In high-risk scenarios, such as logging in from a different country, the user may need to complete an additional MFA process to validate their identity.
Adaptive Authentication and Machine Learning
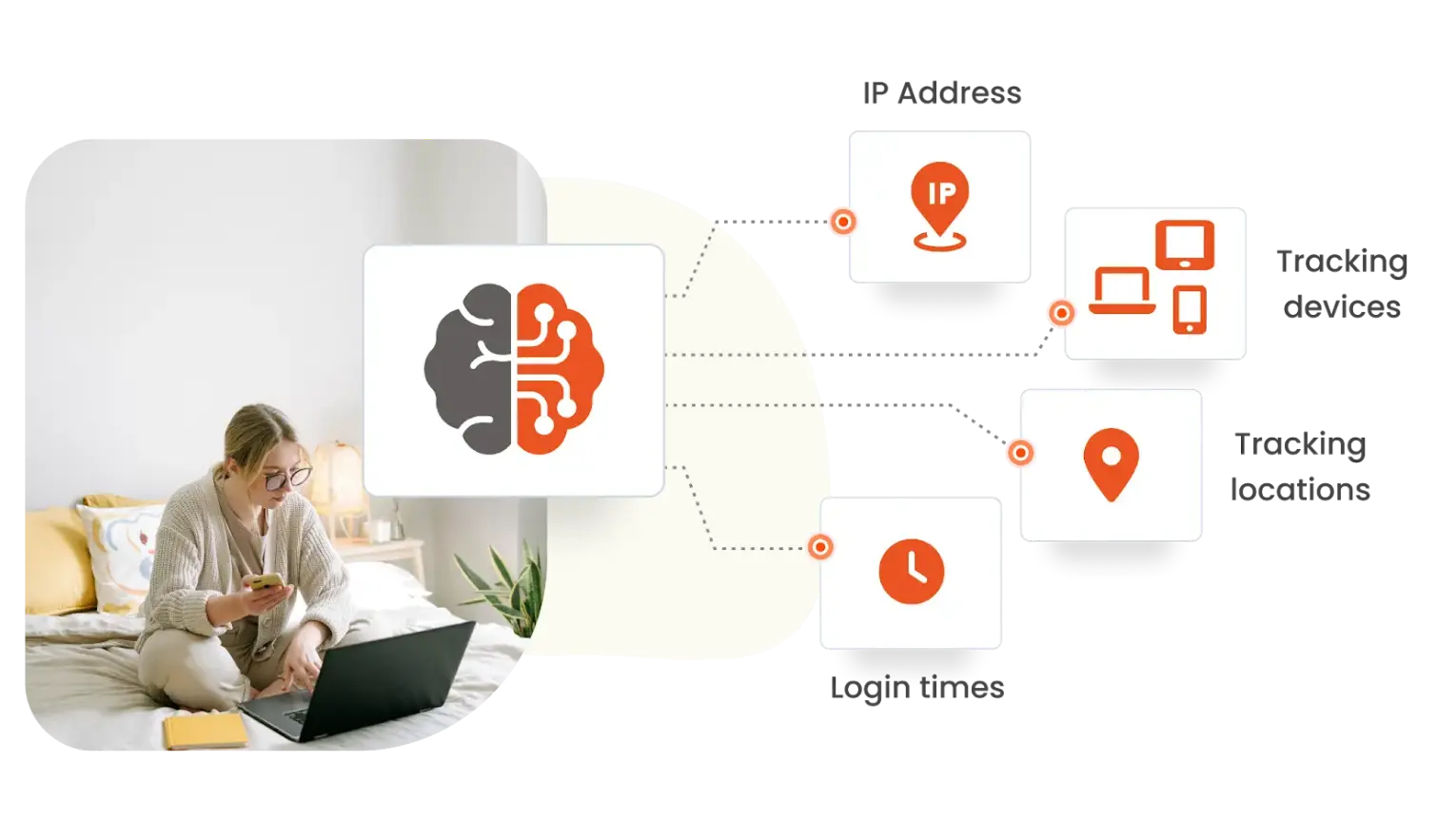
Adaptive Authentication solutions leverage machine learning to improve security and user experience. These systems learn user behavior over time, tracking devices, login times, and locations. They also monitor IP addresses and network reputations to spot unusual activity that might indicate a security risk.
Machine learning helps assign a risk score based on behavior and context. The response to this risk is determined by rules set by IT, which can vary depending on the user’s role, location, and other factors. Advanced solutions use AI to monitor login attempts in real time, identifying any unusual patterns or threats.
Adaptive Authentication Methods
Here are some popular Adaptive Authentication methods:
- IP-Based Restriction: Admins set a list of IP addresses to allow or deny access. User login attempts are compared against this list to determine if access is granted, denied, or challenged.
- Location-Based: Admins configure a list of geo-locations where users can log in. If a user tries to log in from an unlisted location, they may be challenged or denied access.
- Device-Based: Users can link trusted devices to their accounts. Only these devices are permitted access, enhancing security by restricting access to known devices. Time-Based Restriction: Access is granted or denied based on predefined time zones and policies. If a user logs in outside these parameters, they may face additional authentication steps or be denied access.
Benefits of Adaptive Authentication
- Enhanced Data Protection: Fortifies protection against unauthorized access, safeguarding corporate networks and privileged information.
- User-Friendly & Efficient Integration: Smooth integration with existing infrastructure, allowing dynamic policy configuration.
- Immediate User Access Control: Adjusts access based on real-time risk assessment, ensuring secure login processes.
- API-Enhanced Security: Effortlessly integrates enhanced security across all cloud-based applications.
- Universal Compatibility: Works across various platforms and devices with web browsers.
- Uninterrupted User Interaction: Maintains user productivity by embedding security protocols invisibly.
Conclusion
Adaptive Authentication is a powerful approach that offers enhanced security by adapting to real-time risks. By tailoring authentication processes to match your organization's risk tolerance, you can achieve a balance between user experience and robust security. With solutions like those from miniOrange, organizations can effectively manage their authentication needs and protect against cyber threats.
Author





Leave a Comment