In this blog, we’ll uncover what is CASB, how it functions, its game-changing benefits for businesses, and its comparison with other existing security solutions in the market.
Understanding CASB Cyber Security
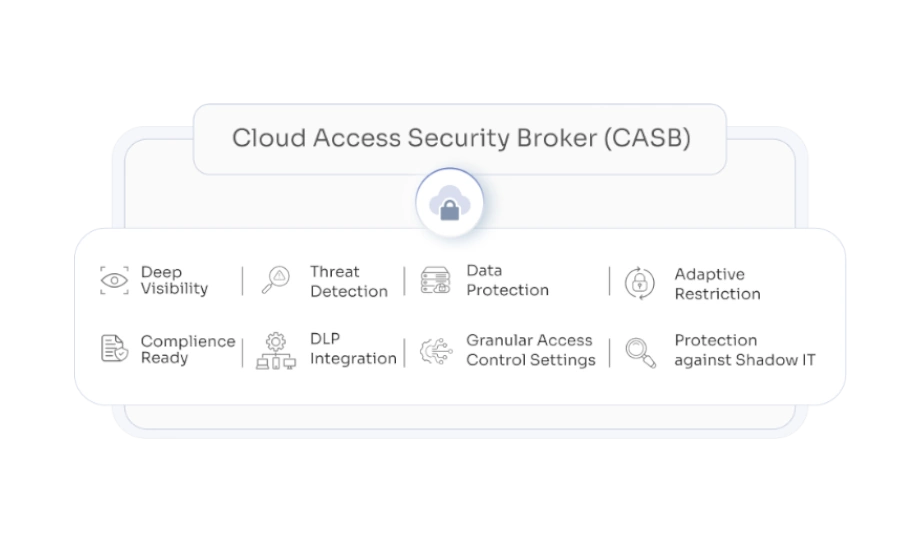
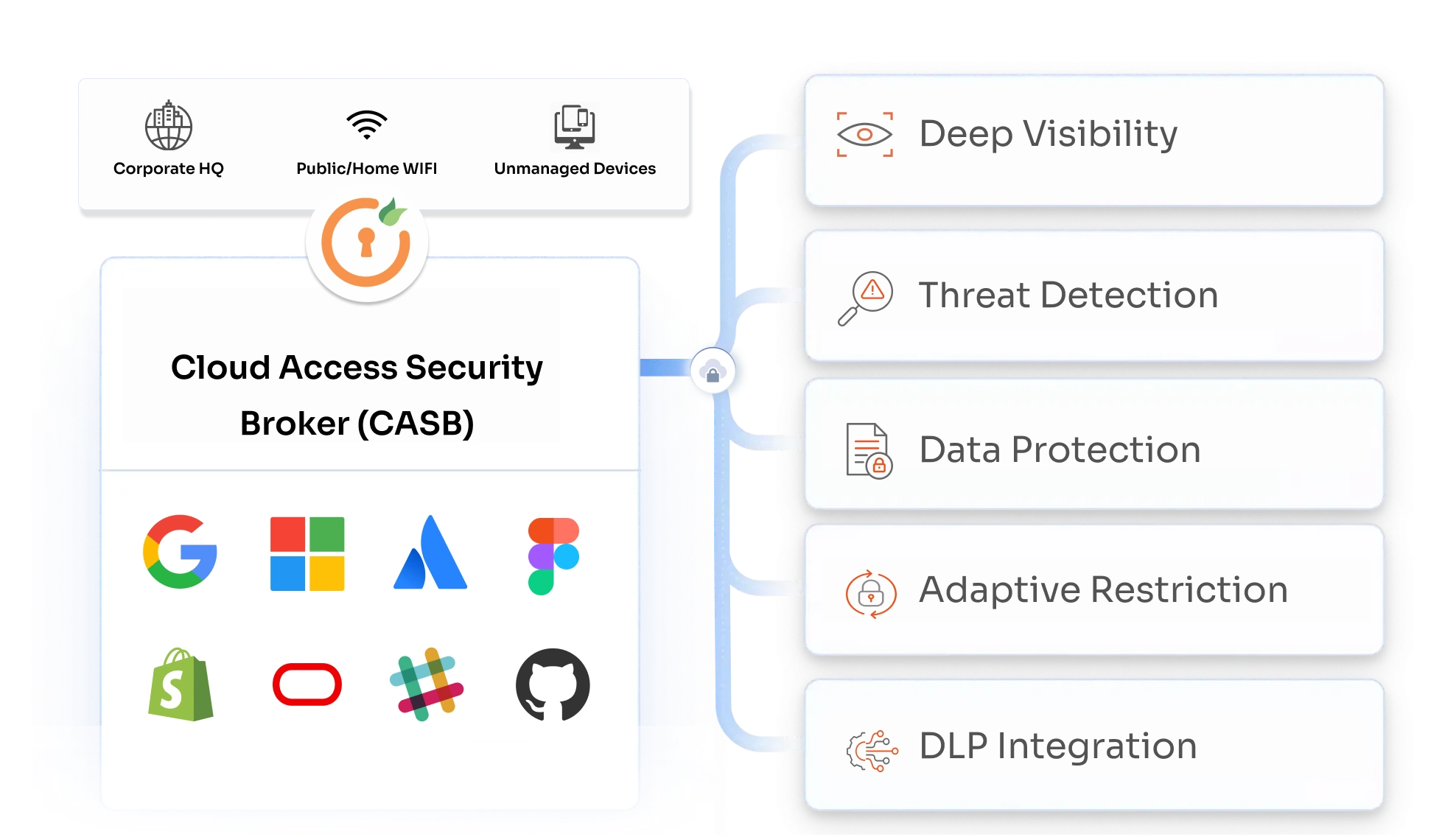
A Cloud Access Security Broker (CASB) acts as a security checkpoint between your organization and cloud-based applications. Its job is to protect your data by preventing threats, monitoring activities, and alerting administrators about potential dangers. CASB cloud also blocks malicious activities and identifies compliance issues to keep sensitive information safe.
With the rise of cloud services and the BYOD (Bring-Your-Own-Device) culture, managing data security has become much more challenging. CASB security helps solve these problems by applying your organization’s security policies to cloud environments. It monitors and filters traffic, enforces strict rules to prevent breaches, and ensures compliance.
In short, CASB solutions block unwanted traffic and protect cloud transactions, providing robust security.
Problems with Traditional Perimeter Security
1. Limited Control Over Cloud Apps:
Traditional perimeter security focuses on protecting the network's edge, often neglecting the visibility and control needed for cloud-based applications and remote devices. This gap can leave sensitive data exposed and unmonitored.
2. Inadequate Protection for Cloud Services:
Traditional security measures may not effectively cover the complexities of cloud services and applications, leading to potential security gaps and vulnerabilities.
3. Challenges with Remote and Mobile Access:
As organizations embrace remote work and mobile devices, traditional perimeter security struggles to secure data accessed from outside the corporate network, increasing the risk of breaches.
4. Difficulty in Preventing Shadow IT:
Employees often use unauthorized cloud services (shadow IT) that bypass traditional security measures, leading to unmonitored data access and potential security risks.
5. Compliance and Data Privacy Issues:
Traditional perimeter security may not address the specific compliance and data privacy requirements for cloud environments, risking regulatory violations and data breaches.
What are the 4 Pillars of CASB?
- Visibility:
Visibility is all about seeing what's going on in your cloud environment. With so many cloud services, it’s tough to keep track of where your data is and how it’s being used. That’s where a CASB solution comes in. It gives you a clear view of all your cloud services, whether you’re managing them or not. - Compliance:
Staying compliant with regulations is crucial and can be tricky. CASB cloud security simplifies this by automating compliance checks and reporting. Whether it’s HIPAA for healthcare, GDPR for data privacy, or PCI-DSS for payment security, CASB software helps you meet these standards effortlessly. - Data Security:
Data security is a top priority, and CASB solutions act as your shield. As your company moves to the cloud, protecting sensitive data from cyber threats becomes more challenging. A strong CASB security scans for vulnerabilities, encrypts data, controls access, and keeps an eye on sensitive information. - Threat Protection:
The threat landscape is always changing, and you need to stay ahead of it. CASB security offers real-time scanning to catch threats before they do damage. They monitor both internal and external networks, spotting unauthorized access and potential risks like misconfigured settings or exposed APIs.
Learn More: 4 Fundamental Pillars of CASB
How CASB Works?
Cloud Access Security Broker (CASB) works in three key steps—discovery, classification, and remediation—to keep your data safe and sound. Here’s how they get the job done:
- Discovery: Finding All Your Cloud Stuff
First up, discovery. A Cloud App Security Broker's job is to find out which cloud services your team is using and who’s using them. They automatically track down every cloud app, even the ones you might not know about. This means you get a clear picture of everything going on in your cloud world. - Classification: Checking the Risk Factor
Next, the CASB tools sort out the risk level for each cloud app. They look at things like:- What’s Inside: What type of data is stored in the app?
- How It’s Shared: How is this data being shared or accessed?
- What It Does: What functions does the app perform?
This helps you understand which apps are risky and need extra protection.
- Remediation: Setting Up the Right Security
With all the info in hand, CASB solutions set up security policies tailored to your needs. They keep an eye out for any future threats or policy breaches and handle them automatically. This way, you stay ahead of any security issues before they become a problem.
Security Capabilities of CASB Solutions
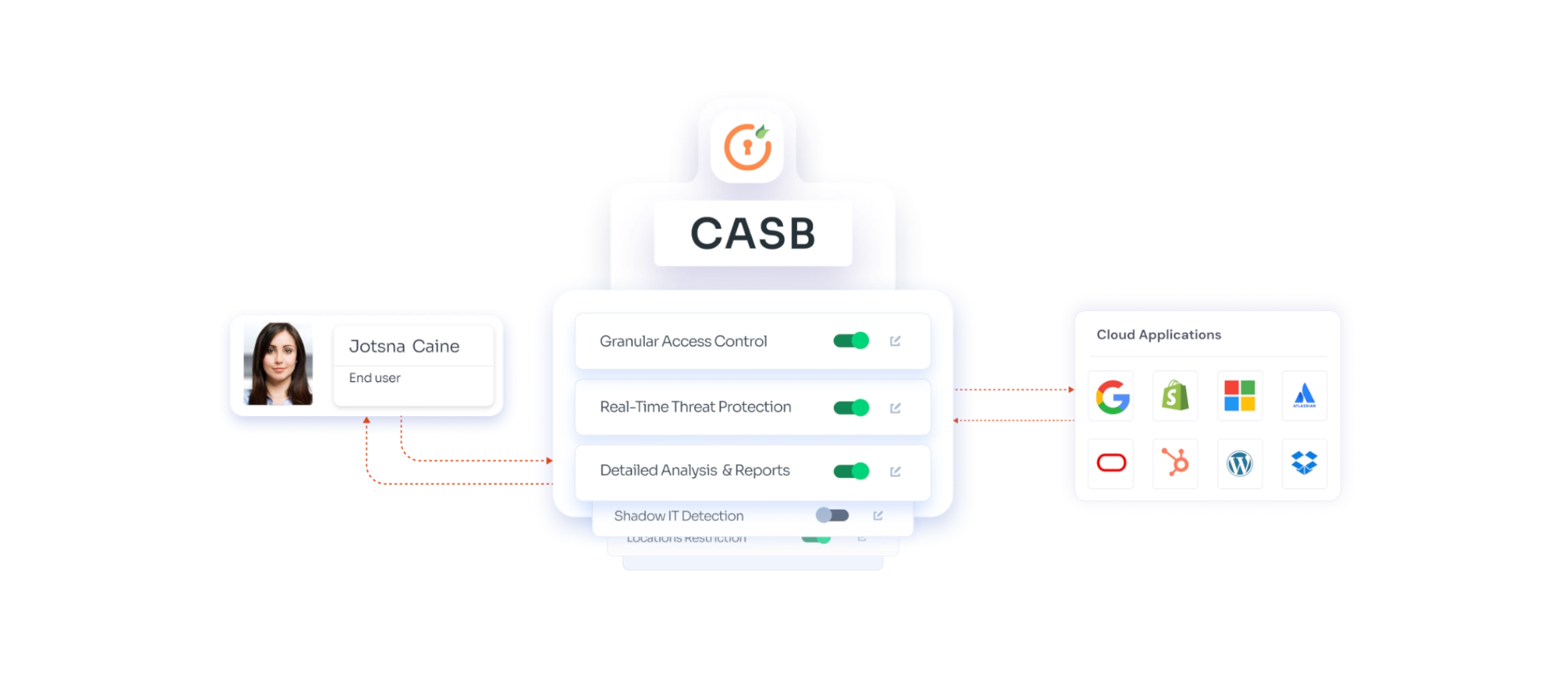
1. Controls Access with Precision
CASB cyber security offers advanced access controls to ensure that only the right people can access your data. Features like Single Sign-On (SSO) and Multi-Factor Authentication (MFA) make it tough for unauthorized users to sneak into your cloud applications.
2. Monitors and Detects Threats in Real-Time
Cloud security broker continuously monitors all activities and detects any suspicious behavior in real-time. If something seems off, like an unusual login attempt or data access request, CASB security springs into action to alert you and take preventive measures.
3. Enforces Data Policies
CASB security helps enforce your organization’s data policies across all cloud services. Whether you need to ensure that sensitive information is stored securely or that data sharing complies with regulations, Cloud App Security Broker makes it easy to set and enforce these rules.
4. Protects against Insider Threats
Not all threats come from the outside. Sometimes, the risk comes from within your organization. Cloud access broker helps mitigate these insider threats by providing detailed visibility into user activities. If an employee starts accessing data they shouldn’t, or if there’s a sudden surge in data downloads, the CASB security will alert you so you can take action before it’s too late.
5. Shields Your Data with Encryption
One of the most vital roles of CASB software is encrypting your data. Imagine encryption as a lock that keeps your data safe from prying eyes. Whether your data is at rest or in transit, CASB security ensures that it’s encrypted and secure. This means even if someone manages to intercept your data, it will be utterly unreadable without the proper decryption key.
Top Use Cases of CASB: Enhancing Your Cloud Security
A Cloud Access Security Broker (CASB) isn’t just a tool for boosting cloud security with increased visibility and threat protection. It’s also a versatile solution with a range of powerful use cases that can secure your organization’s cloud infrastructure.
Here are three key ways CASB solutions can transform your cloud security strategy:
1. Govern Your Cloud Usage
A Cloud Access Security Broker is your go-to solution for governing cloud usage with precision. It excels at monitoring potentially risky behaviors, like the use of unsanctioned cloud apps for storing and sharing files. With a CASB, you get granular visibility and control over cloud activities based on identity, service, activity, application, and data.
CASB cloud security lets you define policies tailored to specific services or risk levels. You can take action like blocking certain services, alerting users, or even providing a security policies refresher. This means your security team can address issues proactively, ensuring that cloud usage aligns with your organization’s security standards.
2. Guard Against Cybersecurity Risks
Your CASB security broker is your frontline defense against both internal and external cybersecurity threats. It provides comprehensive visibility into all cloud services, allowing you to customize your security approach with ease. By integrating out-of-the-box workflows and security features, CASB cloud access can detect and mitigate malware attacks, protect against unauthorized data uploads, and ensure that sensitive data remains secure.
With tokenization and encryption, any data moving in or out of the cloud is protected, while upload prevention blocks internal users from adding unsanctioned data. This multi-layered approach ensures strong protection against a variety of cyber threats.
3. Protect Sensitive Data
Sensitive data deserves the best CASB protection. It enforces Data Loss Prevention (DLP) policies to secure data as it travels to and from both sanctioned and unsanctioned cloud services. Whether your data is accessed from a mobile device, web browser, or sync client, Cloud App Security Broker ensures it’s protected against loss and unauthorized access.
Advanced enterprise DLP capabilities discover and shield sensitive information across your entire cloud environment. With features like encryption, tokenization, and upload prevention, a cloud security broker keeps your sensitive data safe and sound, no matter where it’s being used.
Crucial Role of CASB for Businesses and Cloud Adoption
Data Governance:
CASB cloud security provides deep visibility into who’s accessing what, when, and from where. If something goes wrong, the solution can block, alert, encrypt, or quarantine data, ensuring the IT team stays informed about any policy breaches.
Data Security:
CASB encryption, tokenization, and other techniques help protect and shield your data from theft or leakage across all cloud services. By using Data Loss Prevention (DLP) capabilities, a CASB broker ensures your data remains secure whether it’s in use, in motion, or at rest.
Threat Protection:
Cloud App Security Broker identifies and isolates threats like malware and ransomware by continuously evolving to meet new threats. It ensures your business remains protected against the latest cyber dangers. Any suspicious activity or active threats are promptly flagged to your cloud security team.
Power of CASB Solution: Key Benefits for Your Organization
- Centralized Policy and Governance:
Cloud App Security Broker is like a single, central hub where you can manage policies and governance across all your cloud services. It makes this possible by providing a consistent approach to security for users and devices, including those personal devices brought into the workplace (BYOD). This means you get a unified view and control over your entire cloud environment, streamlining management and reducing complexity. - Deep Visibility and Control:
A CASB security offers detailed visibility into user activities, applications, sensitive data, and SaaS usage. This means you can see exactly what’s happening in your cloud environment and take control where needed. Whether it’s monitoring application use or tracking sensitive data, you get the insights necessary to safeguard your organization effectively. - Secure Workforce Mobility:
Cloud App Security Brokers help ensure that workforce mobility remains secure. By monitoring and controlling access to cloud applications, like Office 365, you can enable your team to work securely from anywhere, without compromising on safety. - Protection Across All Devices:
With the shift away from traditional device management to accommodating BYOD, CASB security protects all device access to SaaS applications. This ensures that every device—whether company-issued or personal—is covered under CASB security. - Insightful Data and User Behavior Analytics:
CASB software offers powerful analytics capabilities, inspecting and analyzing data, application use, and user behavior within cloud services. This includes identifying unsanctioned cloud use and shadow IT, giving you the tools to address potential risks before they become issues. - Seamless Integration:
Integrating a CASB solution with your existing identity provider, Security Information and Event Management (SIEM) tool, and Unified Endpoint Management (UEM) product enhances your overall security framework. This integration allows for a cohesive security strategy that leverages your current systems while adding an extra layer of protection. - Malicious Activity Detection:
A Cloud Access Security Broker can detect and block unusual behavior that might indicate malicious activity. This proactive approach helps prevent potential threats before they can impact your organization.
How to Choose a CASB? 3 Points to Keep in Mind{#how-to-choose-casb}
When it comes to adopting a Cloud Access Security Broker (CASB) solution, it’s crucial to view it as just one piece of your broader cybersecurity puzzle. A CASB can be incredibly powerful, but its effectiveness depends on how well it fits with your existing security setup and meets your specific needs.
Here’s how to choose the right CASB solution for your organization:
- Match the Solution to Your Specific Needs
Every organization’s cloud security needs are unique. To make sure you’re choosing the best CASB, start by identifying your specific use cases. When evaluating potential CASB vendors, focus on those who specialize in the areas that matter most to you. Look for CASB vendors with proven expertise in your priority areas. For example, if insider risk management is a key concern, check if the CASB solution offers strong features in that category. This ensures that the CASB you choose has the right tools to handle your unique security challenges. - Assess the Vendor Landscape
To find the best fit, dive into media coverage and analyst reports. Look for CASB vendors with a solid track record of preventing breaches and effectively managing security events. Check testimonials and case studies from organizations similar to yours to see how these vendors have performed in real-world scenarios.
Be aware of potential limitations in the CASB solutions you’re considering. Some may excel in certain areas but fall short in others. If you have multiple use cases, ensure that the CASB can handle all of them without compromising on any front. - Test Before You Commit
A trial run can be a game-changer. Many CASB vendors offer the opportunity to pilot their solution before you make a full commitment. This trial period allows you to see how well the CASB cloud security integrates with your existing cloud infrastructure and whether it aligns with your company’s resources and needs.
How miniOrange CASB Helps?
miniOrange Cloud Access Security Broker (CASB) offers a one-stop solution to protect your organization’s cloud apps and data. As one of the leading CASB vendors, miniOrange provides CASB security capabilities like real-time threat detection, data encryption, and policy enforcement. The solution gives you deep visibility into user activities, precise control over data access, and strong protection against insider threats.
miniOrange CASB tools are designed to integrate seamlessly with your existing cloud services, like AWS, Google Workspace, and Office 365. Whether you need to prevent unauthorized access, manage shadow IT, or ensure compliance with data privacy regulations, miniOrange has you covered.
How to Implement miniOrange CASB Solution: A Simple Guide
Implementing miniOrange Cloud Access Security Broker (CASB) is simple and easy to configure. Here’s a straightforward CASB setup guideto help you get started:
- Integrate with Your Cloud Services:
Connect the CASB to your cloud applications and services. For Out-of-Band CASBs, this involves API integration. For Inline CASBs, configure the proxy settings to handle traffic between users and the cloud. - Configure Policies:
Set up security policies and rules to monitor and control access, data transfer, and application usage. - Monitor and Adjust:
After deployment, continuously monitor the CASB’s performance and make adjustments as needed. This will help you stay on top of new threats and changes in your cloud environment.
CASB vs DLP
| Feature | CASB (Cloud Access Security Broker) | DLP (Data Loss Prevention) |
|---|---|---|
| Definition | CASB acts like a security guard for cloud services, monitoring and controlling user activity in the cloud. | DLP prevents sensitive data from being leaked or mishandled from any given device in an organization. |
| Main Purpose | Ensures secure cloud usage by enforcing policies, monitoring activity, and providing visibility. | Protects sensitive data from being lost, stolen, or accessed improperly. |
| Focus Area | Cloud applications and data, including SaaS and IaaS platforms. | Data in transit, at rest, and during use across various environments. |
| Granular Controls | Offers detailed visibility and control over cloud-based activities and data sharing. | Focuses on safeguarding data by enforcing rules and preventing unauthorized access. |
| Use Case | Ideal for managing and securing cloud applications like Office 365, Salesforce, and AWS. | Perfect for protecting sensitive data such as personal information, financial records, and intellectual property. |
| Threat Detection | Detects suspicious activities and potential threats in cloud environments. | Identifies and responds to potential data breaches or leaks. |
Read more: CASB vs DLP
CASB vs SASE
| Feature | CASB (Cloud Access Security Broker) | SASE (Secure Access Service Edge) |
|---|---|---|
| Definition | Acts as a gatekeeper, ensuring that cloud applications are used securely. | A comprehensive framework that combines network security and WAN capabilities. |
| Primary Focus | Secures access to cloud applications and data. | Secures both cloud and on-premises access, blending security and networking. |
| Core Functions | - Visibility: Monitors cloud usage. - Control: Enforces policies. - Compliance: Ensures regulations are met. |
- Networking: Provides optimized network access. - Security: Combines multiple security functions. - Cloud Integration: Integrates with cloud services. |
| Security Capabilities | - Compliance - Threat Protection - Access Control |
- Firewall-as-a-Service (FWaaS) - Secure Web Gateway (SWG) - Zero Trust Network Access (ZTNA) |
| User Experience | Can introduce some complexity due to the need for integration with various cloud apps. | Streamlined user experience with integrated security and network services. |
| Best For | Organizations focused on securing cloud applications and data. | Companies seeking an all-in-one solution for secure access and optimized networking. |
CASB vs SIEM
| Feature | CASB (Cloud Access Security Broker) | SIEM (Security Information and Event Management) |
|---|---|---|
| Purpose | Protects cloud services by monitoring and controlling access, enforcing policies, and ensuring data security. | Collects, analyzes, and correlates security event data from various sources for real-time monitoring. |
| Focus Area | Cloud applications and data protection. | Overall IT infrastructure security, including network, systems, and applications. |
| Threat Detection | Detects threats related to cloud services, such as unauthorized access and data breaches. | Detects a wide range of threats by analyzing logs and events for suspicious patterns or anomalies. |
| Compliance | Helps ensure compliance with regulations and policies specific to cloud services. | Ensures compliance with broader IT security regulations by providing comprehensive logging and reporting. |
| Alerting | Provides alerts for cloud-specific issues such as risky user behavior or unauthorized data access. | Generates alerts based on detected security events and anomalies across the entire IT infrastructure. |
| Reporting | Delivers insights on cloud usage patterns, potential risks, and compliance status. | Produces detailed reports on security events, incident investigations, and compliance status. |
Summary
A Cloud Access Security Broker (CASB) acts as a gatekeeper between your organization and the cloud services you use. It watches over all the data going in and out, making sure everything stays secure.
miniOrange CASB comes as an ideal cloud security solution that helps protect against data breaches, cyber threats, and unauthorized access. It even ensures your organization complies with all the necessary regulations and policies.
Think of it as the all-in-one security tool that gives you peace of mind while you enjoy the flexibility of the cloud. Whether you’re working from home, the office, or anywhere in between, CASB makes sure your data is locked up tight and only accessible to those who should have access.
Reference links
Author

Leave a Comment