Identity Lifecycle Management (ILM) offers a comprehensive solution for managing digital identities, encompassing not only user management but also controlling access levels for employees. This system effectively tracks an employee's journey from their first day at an organization until their departure. But before diving deeper into the intricacies of ILM, often synonymous with User Lifecycle Management, it's important to first grasp the fundamental concept of digital identity.
What is digital identity?
Digital identity refers to a collection of information that uniquely represents an individual, organization, application, or device in the digital ecosystem. For this discussion, our focus will be on the digital identity of an individual user, exploring how this unique set of data defines and distinguishes a person in cyberspace
What is Identity Lifecycle Management?
Identity Lifecycle Management (ILM) becomes essential when an organization hires a new employee, enters into a contract, or engages the services of a third party. It involves providing access to crucial information for efficient task execution. However, it's important to recognize that identity management extends beyond just human identities. It encompasses a variety of non-human elements such as systems, roles, responsibilities, keys (API and SSH), and devices.
As organizational infrastructures grow more complex, particularly with the expansion of remote workforces accessing cloud services, the need for a comprehensive ILM strategy becomes paramount. This approach should encompass all accounts linked to the organization, including their respective access privileges, ensuring seamless and secure operations across the board.
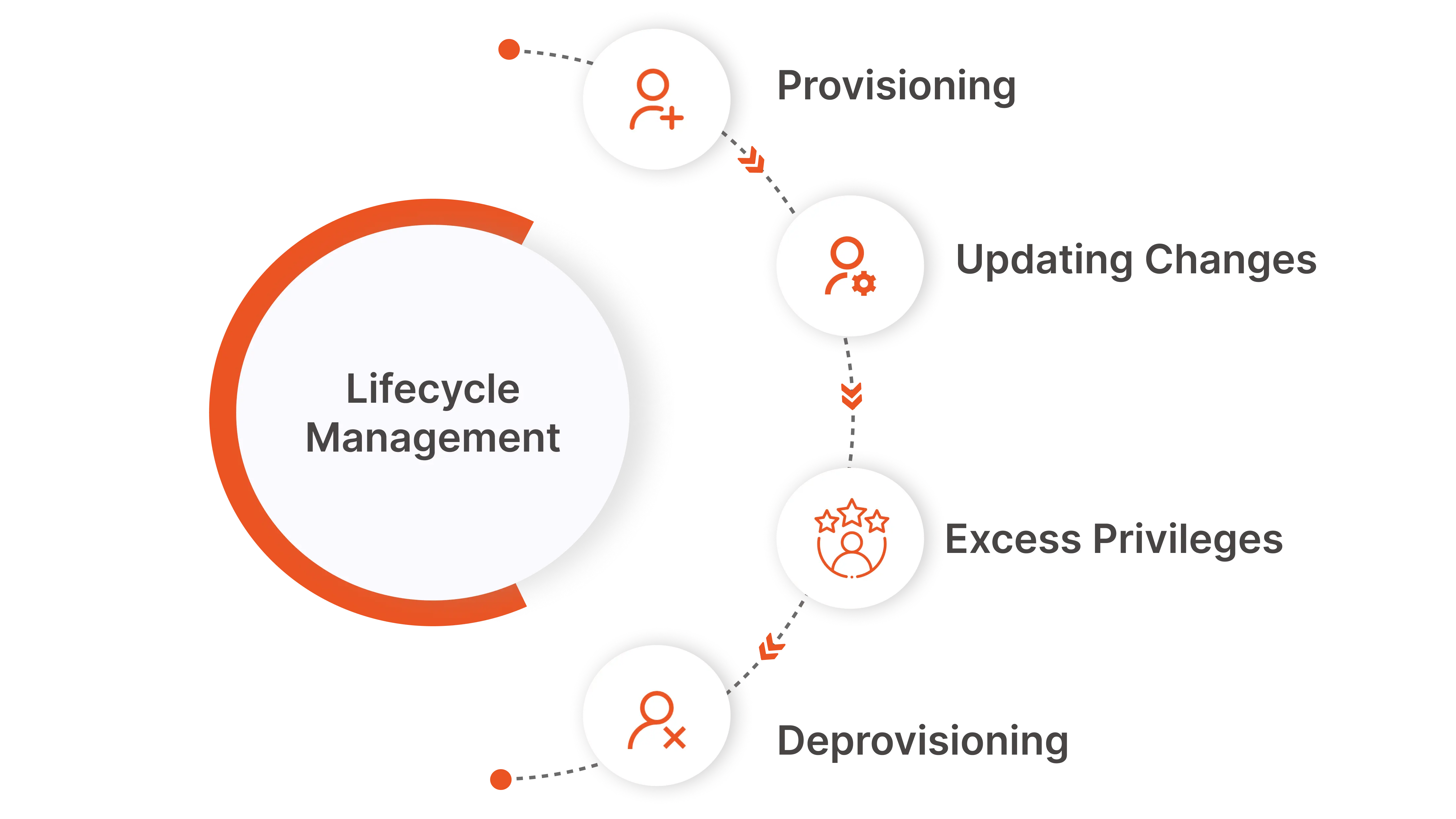
Key Stages and Best Practices in Identity Lifecycle Management
Let us now have a look at some of the best practices and various stages of Identity lifecycle management.
- Provisioning – The integration of new employees, contractors, or third parties involves establishing their digital identities, a process that should adhere to the principle of least privilege. This approach ensures that individuals are granted only the minimum level of access necessary to fulfill their roles. Verification of a user's identity is typically achieved through Single Sign-On (SSO) and Multi-Factor Authentication (MFA) methods. These verification steps are crucial as they restrict access to what is essential for users to perform their tasks effectively and securely.
- Updating/ changes - As the roles and privileges of users evolve, it's crucial to adjust their access to sensitive data accordingly. This can be ensured by implementing Role-Based Access Controls (RBAC). It ensures appropriate user access throughout the identity lifecycle. Equally important is revoking access when it's no longer necessary, as a fundamental aspect of the lifecycle management process
- Excess Privileges: Over time, accounts, especially admin ones, can accumulate excessive privileges, particularly as employees shift roles. Such over-privileged accounts become prime targets for attackers. Regularly reviewing access rights is vital, not just for security, but also to ensure employees have permissions appropriate for their current tasks. Inadequate identity lifecycle management can result in employees retaining access beyond their needs or lacking necessary permissions, thereby affecting both productivity and security
- Deprovisioning – Studies indicate that almost 50% of ex-employees still access their work accounts after leaving their position, whether through resignation or termination. Timely deprovisioning of these accounts is crucial to reduce the risks of unauthorized access or potential harmful actions, especially in cases of termination for cause. This principle is equally important for machine identities, such as those linked to service accounts, to ensure security and prevent misuse
Benefits of identity lifecycle management solution
Let us now take a look at few of the benefits of identity lifecycle management (ILM) solution
- System Overview: Provides a comprehensive view of all digital identities and their permissions within the system.
- Real-time Identity Governance: Facilitates instant role updates, permission adjustments, and rights revocation.
- Enhanced Security: Ensures precise role definition and prevents excessive privileges, eliminating inactive 'zombie' accounts.
- Efficient Password Management: Enables password synchronization across platforms and simplifies password reset/change processes.
- Seamless Integration Across Platforms: Simplifies IT management by integrating critical applications, bridging gaps between IT and HR.
- Breaking Down Operational Barriers: Alleviates the complexity of managing disparate identity silos across applications.
- Automation of Manual Tasks: Reduces IT workload by automating repetitive identity management tasks, minimizing human error and security risks.
- Regulatory Compliance Assurance: Supports compliance with standards like HIPAA, PCI-DSS, through proper access management and rapid deprovisioning.
PAM Integration with ILM
Pairing Privileged Access Management (PAM) with ILM adds another layer of security and efficiency. PAM specifically handles the access rights of privileged users, like administrators or those with high-level access to systems. Integrating PAM with ILM creates a more holistic approach to identity management.
This combination ensures that privileged accounts are governed with the same standards as regular accounts, providing a unified view of all access privileges across the organization. The integration helps in continuously monitoring and managing the lifecycle of privileged identities, reducing the risk of security breaches and enhancing compliance with regulatory standards. By incorporating PAM into ILM, organizations can achieve a more controlled and secure environment, while maintaining the flexibility and efficiency needed in dynamic business landscapes.
miniOrange's Identity Lifecycle Management (ILM)
The miniOrange's Identity Lifecycle Management (ILM) provides a complete solution tailored to the digital identity management requirements of modern organizations. This platform streamlines the identity management process, automated workflows, provisioning, de-provisioning, and access control, and ensures comprehensive management of digital identities. Not just that, the ILM solution emphasizes reducing human error and increasing productivity through the automation of manual tasks. Additionally, the platform features real-time identity governance, efficient password management, and a complete system overview. This approach not only enhances security measures but also significantly boosts operational efficiency.
Overall, the miniOrange's ILM solutions are designed to adapt to the evolving digital landscape, with its ability to break down operational silos and ensure seamless integration across different platforms. It provides organizations with the tools to manage identities securely and efficiently. By implementing these solutions, organizations can protect their assets, comply with regulatory requirements, and streamline their identity management processes, thereby achieving a balance between security and operational efficiency.
Author




Leave a Comment