Sensitive data in a company's infrastructure, if left vulnerable by securing with just traditional usernames and passwords, is prone to cyber attacks. This calls for the need for a more secure method of authentication. What if you have many methods to choose from in order to make it more challenging for a user to login to their accounts? This is where multiple authentication methods from multi-factor authentication (MFA) come into play.
In this article, we will learn about MFA, its working, authentication methods, use cases, benefits, miniOrange MFA, and future trends.
What is Multi-Factor Authentication (MFA) in Cybersecurity?
Multi-Factor Authentication (MFA) is a security method requiring multiple credentials to verify a user's identity. It enhances security, protects against cyber threats, aids regulatory compliance, and can be user-friendly.
MFA adds an extra authentication layer to access resources, requiring users to authenticate with two or more factors beyond usernames and passwords. These factors can include OTP over SMS/email, push notifications, or Google/Microsoft authenticator.
Why Use Multi-Factor Authentication (MFA)?
Users often make it easier for hackers by choosing weak passwords, reusing passwords across multiple applications, storing them insecurely, and not updating them regularly. These practices may help users remember their credentials but also make it easier for hackers to gain access.
The 2019 Data Breach Investigations Report found that 81% of account breaches were due to leaked or weak passwords (e.g., "password," "admin").
- 92% of organizations have credentials for sale on the Dark Web.
- 81% of data breaches are the result of weak or stolen passwords.
- 90% of passwords can be cracked in less than six hours.
These factors underscore the importance of using Multi-Factor Authentication (MFA). By combining your username and password with MFA, your access becomes more secure.
In our work with various organizations, we've seen the devastating impact of security breaches caused by weak authentication methods. For example, a major healthcare provider we consulted suffered a significant data breach due to compromised passwords, resulting in millions of dollars in damages and loss of patient trust. Implementing MFA could have prevented this incident.
How Does MFA Work?
Drawing from our experience in implementing MFA systems for Fortune 500 companies, we can attest to the effectiveness of this layered approach. For example, when a user attempts to access a protected resource:
- They enter their username and password (first factor).
- The system then prompts for a second factor, such as a fingerprint scan or a one-time code sent to their smartphone.
- Only after successfully providing both factors is access granted.
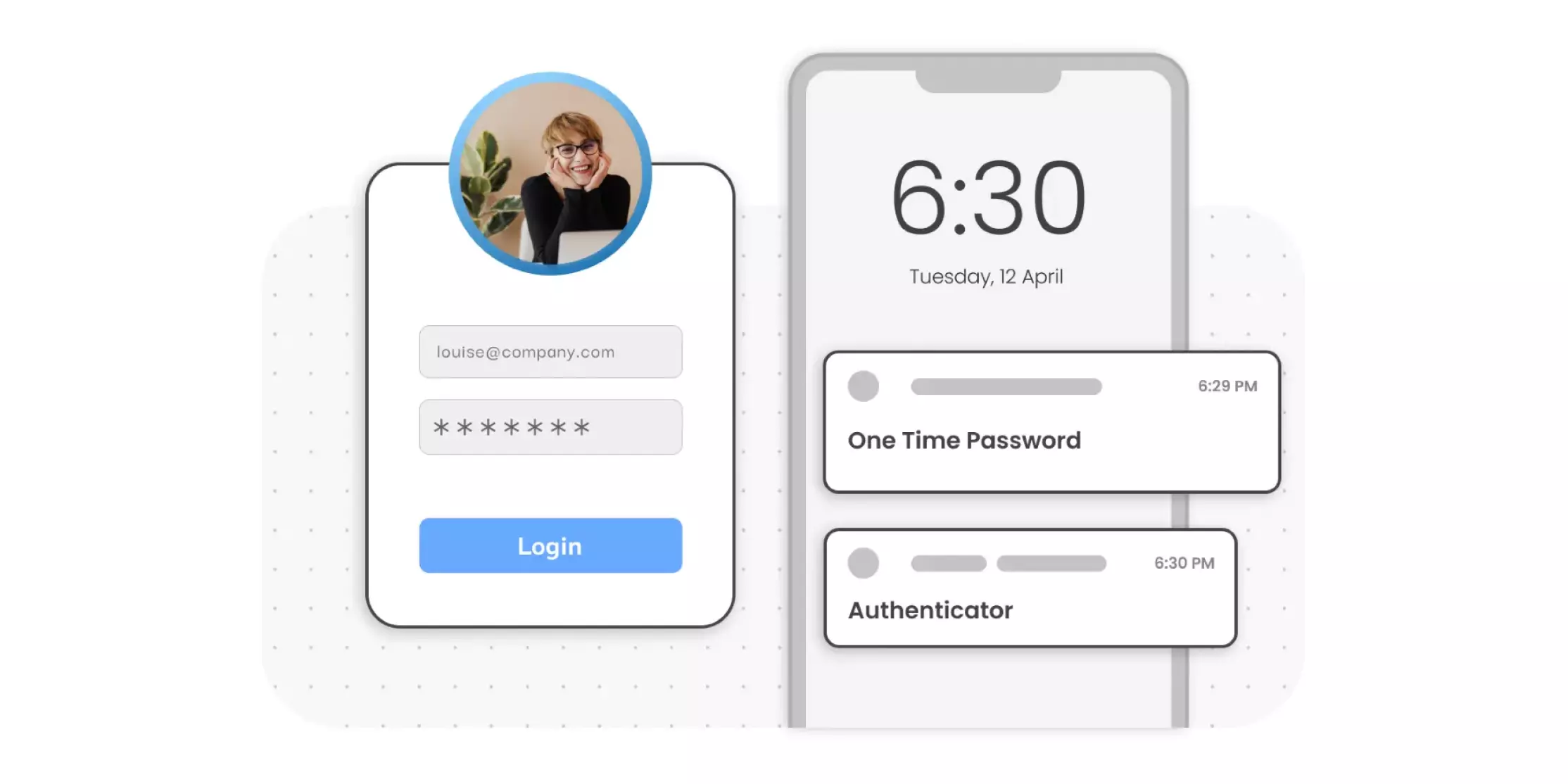
As the user attempts to gain access to a specific resource, they are prompted with multiple authentication factors instead of only one. The user credentials are then verified by a core identity provider (IdP) or directory services platform, and the user gains access to the requested resource. Most MFA systems use a one-time passcode (OTP) for each login attempt. miniOrange offers 15+ MFA methods, which we will cover later in this blog.
Multi-Factor Authentication Methods
Multi-Factor Authentication takes the help of these factors to authenticate a particular individual.
- Knowledge factor is something that a user remembers, like "first password," "first school name," "a pin," etc.
- Possession factor is something the user has, such as a mobile device, smartphone app, or security token to approve authentication requests.
- Inherence factor, mainly referred to as a biometric factor, is something different in the user's physical self. These could also be personal attributes like fingerprint, retina, or voice.
- Location factor usually denotes the location from which an authentication attempt is being made. Location-based MFA methods can limit user access when a user breaks out from the given location.
- The time factor restricts user authentication to a specific time panel in which logging on is granted and restricts access to the system outside of that window. In simpler terms, we called it time-based OTP (TOTP). Mobile apps like Microsoft Authenticator, Google Authenticator, and miniOrange Authenticator provide a key code that's time-dependent up to limited seconds.
In our work with financial institutions, we've found that a combination of possession and inherence factors provides the highest level of security.
Multi-Factor Authentication vs. Two-Factor Authentication
| Aspect | MFA | 2FA |
|---|---|---|
| Definition | An authentication method that requires two or more factors of authentication. | An authentication method that requires exactly two factors of authentication. |
| Subset | MFA is a broader term that includes 2FA as a subset. | 2FA is a specific type of MFA that uses exactly two factors. |
| Security | MFA is considered to be more secure because it uses multiple layers of authentication. | 2FA can still be vulnerable if one of the factors is compromised. However, it’s still a highly secure protocol. |
| Ease of Use | MFA might be more complex to implement and use due to the involvement of more than two factors. | 2FA is often easier to implement and use as it involves only two factors. |
| Examples | Entering a password (something you know), verifying a code sent to your smartphone (something you have), and scanning your fingerprint (something you are). | Entering a password and then confirming your identity through a code sent to your mobile phone. |
Authentication Challenges for the User in Multi-factor Authentication
Users who have to remember multiple passwords will find it difficult to use MFA if they add security features. MFA aims to simplify MFA for users. These are some main approaches to simplifying MFA.
This applies business rules and policies to user-based elements such as location or device. A corporate VPN may know that a user can sign in from their home, seeing their location and assessing the risk of misuse or compromise. An employee accessing the VPN through a coffee shop can trigger the system, and you will be required to enter MFA credentials.
Push Notification
This method allows the security system to issue a third, single-use ID code to the user's smartphone. To access a secure system, users can enter their user ID or password. A security system will then issue a third single-use code to their mobile devices. To gain access, users must enter the code into the system. Push authentication makes MFA easier by giving users the third code. This eliminates the need for them to remember it.
Multi-Factor Authentication Use Cases
MFA over VPN
A global organization with a distributed workforce implements multi-factor Authentication (MFA) over its VPN to enhance security.This implementation not only strengthens security but also improves operational efficiency and regulatory compliance. It's a robust solution for securing remote network access, making it a worthwhile investment for companies looking to enhance their VPN security.
miniOrange MFA over VPN is a robust solution for securing remote network access. It supports a range of VPNs, including Cisco, Palo Alto, Fortinet, SonicWall, and OpenVPN, making it a worthwhile investment for companies looking to enhance their VPN security.
MFA for Windows
Implementing Multi-Factor Authentication (MFA) for Windows enhances security for logon and [Remote Desktop Protocol (RDP)]sessions. The process involves configuring the RADIUS client/server in miniOrange, setting up the Windows VPN client, and enabling 2FA for end users, with options like Google Authenticator.
The Windows MFA solution integrates with Active Directory/LDAP for identity management and offers customizable MFA policies based on roles, groups, or applications. It supports device-based and cross-domain MFA, allowing logins for accounts on any trusted domain or local Windows accounts. Offline MFA ensures security even when disconnected from the internet using soft tokens, authenticator apps, and backup codes.
MFA for Web Apps
Our MFA can be enabled for any of your web apps anywhere on the internet to ensure a secure and efficient way of accessing your critical resources. miniOrange offers MFA for a wide range of web applications running on cloud, on-premise servers, or in hybrid environments.
Enhances MFA security across cloud (SAAS), on-premises, and in-house apps, supporting protocols like SAML, Radius, OpenID, and JWT. Integrate MFA seamlessly with in-house web apps.
MFA for Network Devices
Implement MFA security for firewalls, switches, routers, and other network deviceswith the miniOrange MFA solution that extends beyond VPNs and fortifies your entire corporate network.
Leverage Radius & TACACS protocols with miniOrange to encrypt switches and routers based on your network's hardware capabilities and add Multi-Factor Authentication to enhance the security posture. Bonus point is that miniOrange MFA is deployed without requiring any external proxy.
MFA for Office 365
Microsoft provides MFA only via their default application with limited MFA methods, and you cannot configure any additional MFA authentication method. In some cases, you need to spend an enormous amount for licensing and user differentiation, and if you need to activate or deactivate for the particular user you have. However, with miniOrange MFA for Office 365 it is possible to add more MFA methods.
miniOrange MFA integration for Microsoft Applications allows you to use Yubikey (or the other method from 15+ available MFA methods) as the multi-factor to login into your Office 365 or any of your Microsoft Applications.
Benefits of MFA
Implementing MFA isn't just about security—it's a strategic move that safeguards your company's most valuable digital assets. Beyond thwarting cyber threats, MFA demonstrates a commitment to data integrity that can bolster client trust and give you a competitive edge as we enter a security-conscious market.
- Compliance: Multi-Factor Authentication (MFA) helps organizations meet regulatory requirements and industry standards. By implementing MFA, companies can ensure they are compliant with data protection laws and regulations, reducing the risk of legal penalties, meeting the requirements for cybersecurity insurance, and enhancing their reputation.
- Enhanced Security: Multi-Factor Authentication (MFA) decreases the probability that an attacker can mimic a user and may gain access to the system. miniOrange MFA solution allows users to log in using username and OTP, thus preventing the necessity to enter the password.
- More Productivity and Flexibility: Organizations are accepting mobility because it helps in increasing productivity. Employees can securely login and access corporate applications and resources from virtually any device and from any location, without putting the corporate network at risk.
- Reduced Operating Costs: Implementing MFA reduces the probability of data breaches, resulting in reduced investment.
In a recent case study involving a mid-sized technology firm, our implementation of MFA resulted in:
- 99.9% reduction in account compromise incidents
- 30% decrease in IT support calls related to account lockouts
- $500,000 annual savings in potential breach-related costs
These results underscore the tangible benefits of MFA in real-world scenarios.
miniOrange MFA Solutions
Key Features of miniOrange MFA Solutions:
Zero Trust Authentication
The Zero Trust approach within 2FA helps to create an effective environment, policies, and infrastructure to minimize data breaches.
Support for Cloud and On-premise
Flexible deployment options, like on-premise and cloud. Seamlessly integrates into your organization's existing environment.
Offline Authentication
Allow users to log in even if there is no internet available by using offline 2FA methods such as soft tokens and security questions.
Passwordless Authentication
2FA login for users using just username and OTP/TOTP, thus preventing the need to enter password.
Role-based 2FA
Admin can enable or disable 2FA for a specific user role and for any particular application.
User Self Enrollment
It offers inline registration of users, so you'll simply activate and setup 2FA, and you're ready.
Custom SMS/EMAIL Gateway & Templates
Templates for SMS and email that are sent to users containing OTPs for authentication are also completely customizable.
Reporting and Auditing
Stay informed on all user logins. Get complete reports on all user activities in a single dashboard: session management, user monitoring, user login audit, user & admin activity reports, etc.
Future Ready: MFA Trends to Mitigate Automated Cyberattacks
The more the data, the more is the need to protect it. This implies that cybersecurity is a journey, not a destination. And at the heart of this journey is Multi-Factor Authentication (MFA). It's evolving, becoming smarter and more intuitive. Imagine logging in with just your fingerprint, facial recognition, or even your typing speed!
But it's not just about convenience. MFA is a powerful shield against cyber threats. In fact, it blocks 99.9% of automated attacks. That's why, whether you're a start-up or a big corporation, MFA is a must-have for your security toolkit.
And when it comes to MFA, miniOrange is your trusted companion. We're here to guide you through the increasing threats in cybersecurity, ensuring your digital identity is always protected. With miniOrange, you're not just safe; you're future-ready. Connect with us for your MFA-related queries and use cases today.
Further Reading
Author


Leave a Comment
1 Comments
Saniya
abcabcabc