Out Of Band Authentication (OOBA) is a type of two-factor authentication (2FA) that demands a secondary verification method delivered over a different communication channel (call or text) in addition to the typical user ID and password. The possibility of compromising the transaction/account decreases by splitting the process into two channels, employing both the user’s internet and mobile wireless connection. An attacker is unlikely to be able to compromise both channels in the short amount of time required for an online transaction to take place.
Financial firms and other companies with high-security requirements employ out-of-band (OOB) authentication to prevent unwanted access. OOBA improves cybersecurity by making it more difficult to hack an account because it requires two different and unrelated authentication channels to be compromised at the same time for an attacker to get access.
How Does Out-of-Band Authentication (OOBA) Work?
The channel used to authenticate a customer in an out-of-band authentication (OOBA) system is completely independent of the channel used by the customer to log in or make a transaction. Out-of-band authentication, as opposed to multi-factor authentication, is a sort of 2FA (something you know, like a password, and something you have, like your mobile device).
Let’s imagine a customer wishes to do a banking transaction on their computer. They use their username and password to access the online banking system. The system then sends a one-time password (OTP) to their mobile device by text message or push notification. The user’s internet and wireless network are both involved in this scenario.
Malicious actors may have access to compromised credentials and use a laptop to make a transaction, but they rarely have access to the user’s smartphone to obtain the one-time password required for authorization unless additional means like call forwarding, cloning, phone theft, or other ways are used. The transaction cannot be completed without the OTP. Other Out-of-Band Authentication techniques, such as a fingerprint scan or QR code, could be used instead of an OTP by the company.

How is OOBA more beneficial than other authentication methods?
Using Two-factor authentication (2FA) for Out-of-Band Authentication may appear to be a hassle to you; as you have to go through an extra step to log on to your accounts and access resources. Traditional authentication does not work in this fast-paced digital environment when cyber criminals are seeking critical consumer data. You might be leaving yourself open to thieves who want to steal your data and personal information if you don’t use 2FA Security.
Out-of-band authentication is critical in identity and access management because it significantly minimizes the risk of a “man-in-the-middle” attack. Hackers can intercept data transferring channels by taking over the communication channel between the sender and the recipient in an MITM attack.
In access management, using two different channels to authenticate lowers the risk of MITM attacks and keeps the transmitted information safe.
Key benefits of using Out Of Band Authentication (OOBA)
Fraud Prevention
Before allowing you to proceed, Multi-Factor Authentication confirms that you are who you say you are. It adds another degree of protection to your website, preventing unwanted access.
Improved Customer Trust
Multi-factor authentication (MFA) adds an extra layer of security to your business and your customers’ accounts. It safeguards customer information against identity theft.
Enhanced Security
MFA reduces the likelihood that an attacker will be able to impersonate a user and obtain access to the system. The miniOrange MFA solution allows users to log in using only their Username and OTP, eliminating the need for a password.
Adaptability for different use cases
When dealing with sensitive data, more caution is necessary. The adaptive MFA evaluates risk based on factors including geo location, IP address, and time since the previous login.
As a result, out-of-band authentication (OOBA) is utilized to secure your devices, accounts, and data from security breaches, phishing, and brute-force password attempts. Knowing the password alone isn’t enough for cyber attackers to pass the security check if you’ve set 2FA protection.
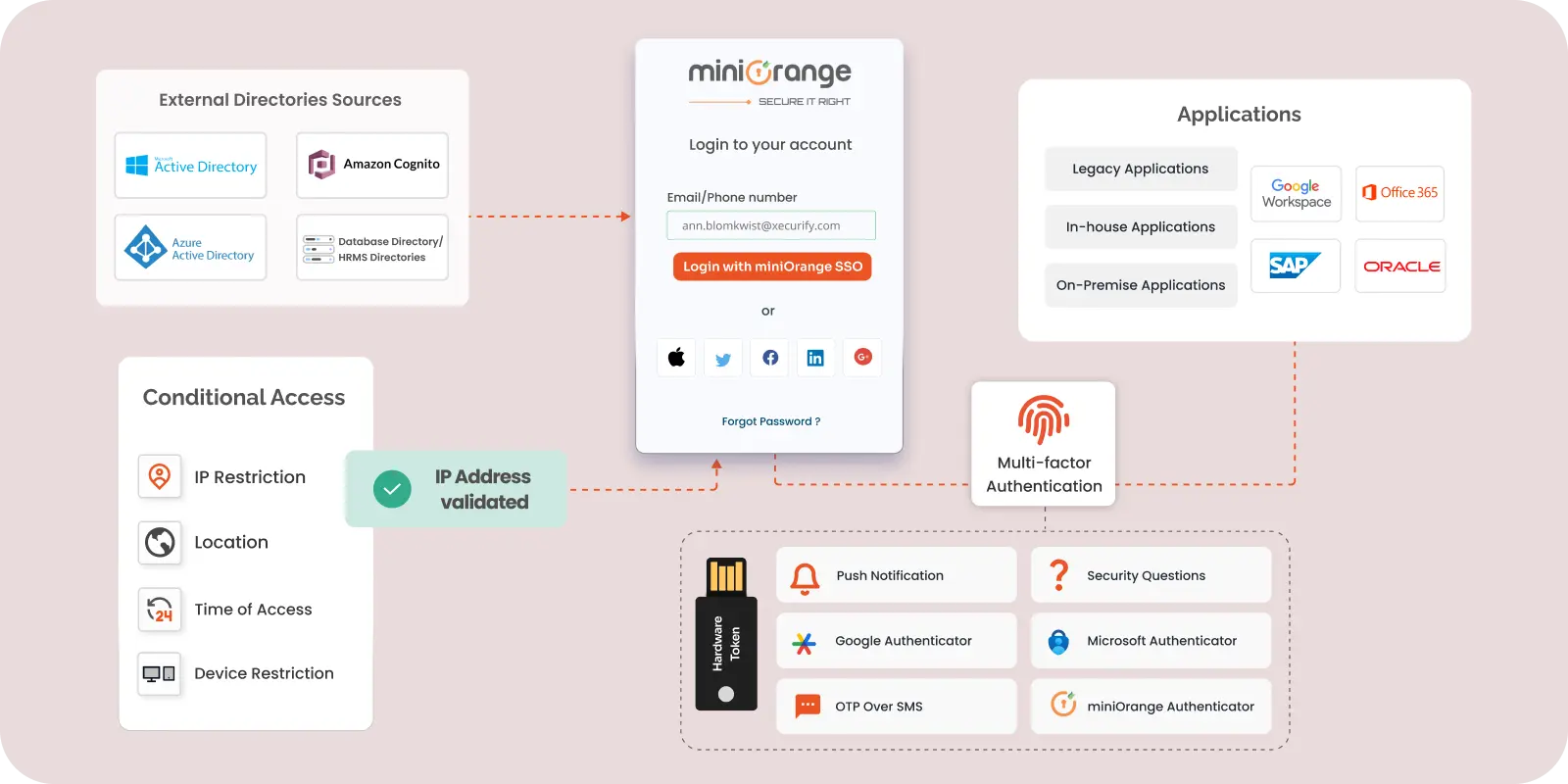
How can miniOrange help you?
miniOrange Authentication Service verifies that you are who you claim to be before letting you move forward. We ensure that however varied your user base may be, we have the right authentication method for each one of them.
OOBA: OTP/Link over SMS/EmailOTP over text/call using SMS/Email: miniOrange offers OTP via SMS/Email via the default gateway, which users can access. The templates for sending OTP to your users by SMS and email are entirely customizable as well.
Link over SMS/Email: When this option is enabled, you will receive an SMS/email containing an Accept Link and a Deny Link at the moment of verification. If you click the Accept button, your transaction will be completed; otherwise, it will not.
OOBA Push NotificationPush notifications: When the push notification mechanism is enabled, you will receive a push notification from miniOrange on your Authenticator App, which you either accept or deny. You can successfully finish the second-factor challenge after clicking Accept.
Authenticator apps: Receive a time-based OTP token (TOTP) by an external authenticator app such as Google/Microsoft authenticator for secure login.
Hardware Token: Use of a physical USB token in your computer, which generates the required information to gain access.
For any firm or organization trying to increase security, using multiple authentication methods is a clear choice. It secures client information and protects against security breaches. It benefits everyone: customers are less likely to have their data stolen, and organizations are less likely to suffer a significant data breach.
Further Reading:
Author




Leave a Comment