What is Privileged Identity Management (PIM)?
Privileged Identity Management (PIM) is a security solution that helps organizations manage and protect accounts with elevated permissions, such as those belonging to system administrators, database managers, service accounts, and superusers. These privileged accounts grant access to sensitive data and critical systems, making them valuable targets for cyberattacks.
A robust Privileged Identity Management system helps organizations securely create, control, and monitor these accounts through a centralized platform. These tools reduce the likelihood of data breaches, enhance compliance with regulatory standards, and ensure that only authorized individuals have time-bound, controlled access to critical assets.
Privileged Identity Management (PIM) Solutions: Key Features
Privileged Identity Management (PIM) solutions provide advanced tools to secure and manage privileged accounts with high-level permissions. Here are some essential features that make Privileged Identity Management tools integral to a robust cybersecurity framework:
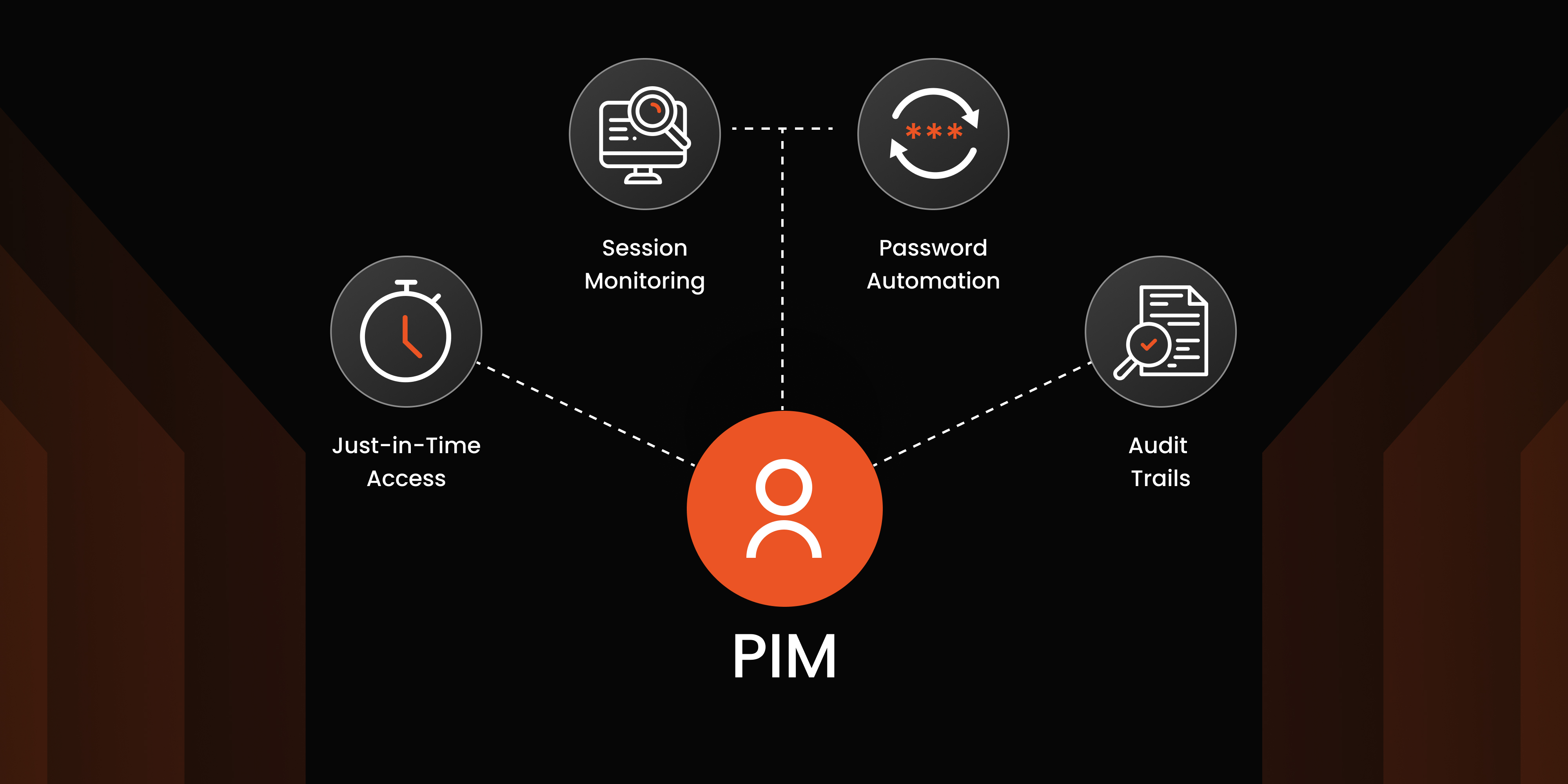
- Just-in-Time Access: PIM solutions offer Just-in-Time privilege assignment, granting temporary access to privileged accounts only when needed for specific tasks. This reduces the risk of prolonged access and ensures that elevated permissions are revoked automatically once tasks are completed, minimizing exposure to potential threats.
- Role-Based Access Control: By implementing Role-Based Access Control (RBAC), PIM solutions enforce the Principle of Least Privilege POLP, providing each user with only the permissions necessary to perform their job. This granular control enhances security by preventing unnecessary access to critical systems, a key benefit of privileged identity management systems.
- Monitoring and Audit Trails: Effective Privileged Identity Management includes tracking and logging of all activities related to privileged accounts. Monitoring and audit trails enable organizations to see who accessed accounts, when, and what actions were taken. This feature helps detect suspicious behavior and provides crucial information for any post-incident analysis.
- Reporting and Compliance Support: Privileged Identity Management tools come with robust reporting capabilities to document security-critical events such as login attempts, access requests, and configuration changes. These reports not only aid in internal monitoring but also support compliance with industry standards, ensuring that organizations meet regulatory requirements with ease.
Why Does Your Business Need a Privileged Identity Management Solution?
A Privileged Identity Management (PIM) solution safeguards sensitive information and critical systems by controlling and managing access to privileged credentials. Here’s why implementing a privileged identity management system is crucial for your business:
- Protecting Against Cyberattacks and Data Breaches Without privileged identity management, businesses are vulnerable to cyberattacks where hackers exploit weak points in the system to steal credentials. If attackers gain access to privileged accounts, they can cause substantial damage—stealing data, disrupting operations, or compromising critical infrastructure. A privileged identity manager minimizes this risk by enforcing strict access controls and protecting sensitive credentials.
- Managing Multiple Access Points With many employees accessing various applications and systems, managing who has privileged access can be complex and risky. In situations like VPN usage or network routing, multiple users may access the same resources at once, increasing the risk of unauthorized access. A privileged identity management solution allows you to centralize and monitor these access points, ensuring only authorized personnel access critical systems.
- Preventing Insider Threats Unmanaged privileged identities create a loophole for insider threats, whether intentional or accidental. Employees with unchecked access can misuse their privileges to steal or leak confidential information. Privileged identity management tools provide the controls needed to monitor and restrict access, reducing the risk of insider threats and safeguarding sensitive data.
- Knowing Who Has Access Without a privileged identity management system, organizations lack visibility over who has access to critical systems and why. This lack of oversight can lead to confusion, making it difficult to track or revoke access when necessary. PIM solutions give businesses full visibility, enabling them to monitor access permissions and quickly identify any unusual or unauthorized access.
- Enforcing Strong Password Policies Weak passwords remain a common vulnerability for organizations. PIM tools can enforce strong password policies, requiring regular updates and ensuring that privileged credentials are difficult to compromise. This strengthens the overall security of privileged accounts and minimizes the risk of unauthorized access due to weak or easily guessed passwords.
How Privileged Identity Management Works?
Privileged Identity Management (PIM) operates by providing controlled, temporary access to sensitive accounts under predefined rules, here’s a look at how a typical PIM solution functions:
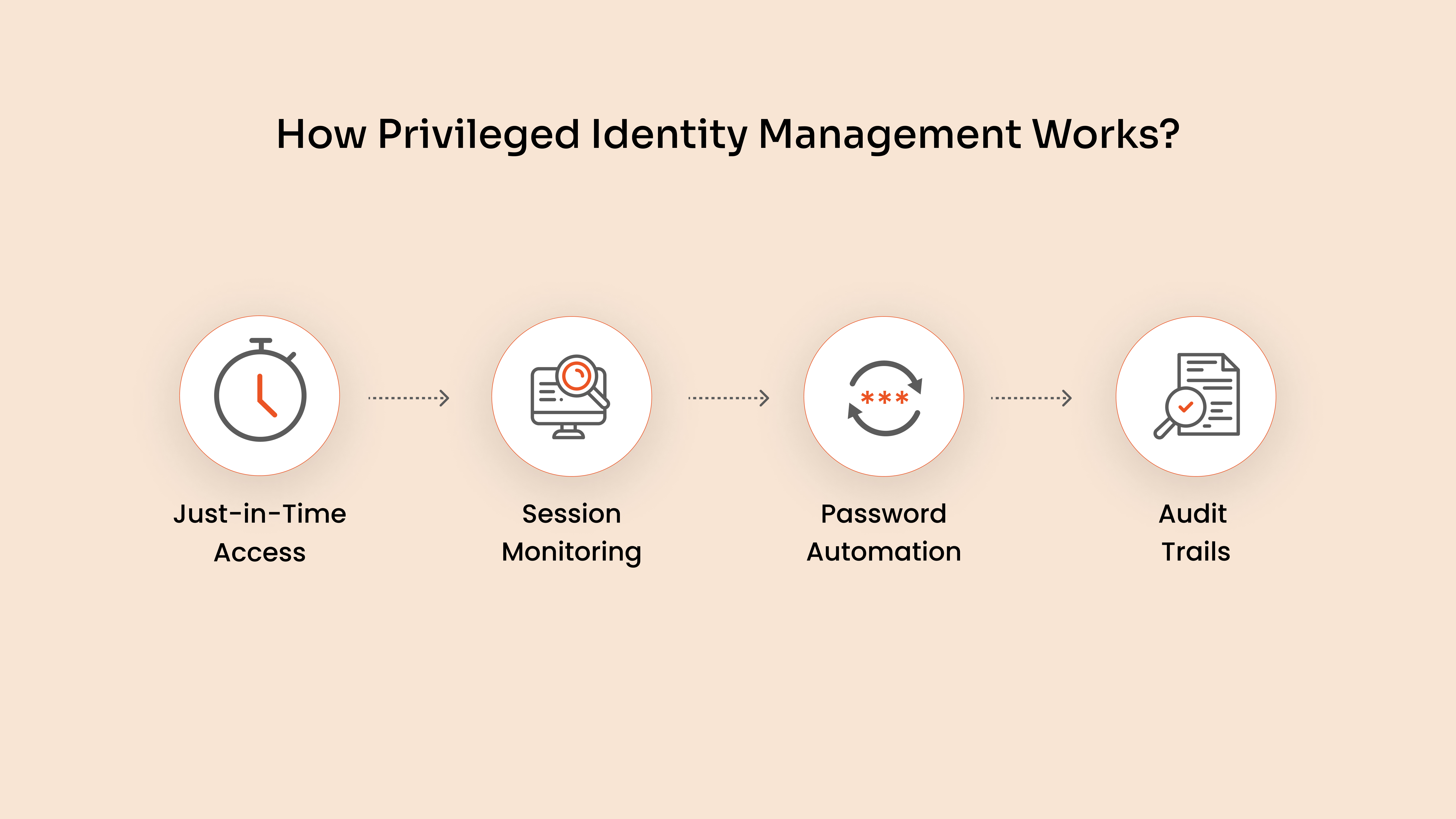
- Defining Privileged Roles and Permissions The first step in privileged identity management involves creating roles that come with specific permissions, tailored to the organization's needs. For example, a role like “Database_Admin” might have elevated access to manage database resources. Once these roles are established, only authorized individuals—such as senior administrators—are assigned to them, limiting the exposure of sensitive data to trusted users.
- Requesting Access with Justification Once roles are in place, users can request temporary activation of these privileged roles through the privileged identity management system. Each request requires the user to specify the time and reason for access, ensuring that permissions are granted only when necessary. Requests often go through an approval process, which can be automated or managed manually by a designated approver.
- Approval and Credential Injection After submission, requests are either approved or denied based on the user’s permissions and access needs. If approved, the privileged identity manager issues the necessary credentials directly into the user session. If denied, the system logs this as an incident, providing a record for future audits.
- Timely Revocation of Privileges Once the user completes their task, or the set duration expires, the privileged identity management solution automatically revokes the user’s access. This time-bound control prevents prolonged access and minimizes security risks. If more time is required, users can request an extension, ensuring that access remains tightly controlled.
- Continuous Monitoring and Auditing Privileged identity management tools provide extensive session monitoring capabilities, including session tracking and audit trails. These features enable administrators to review activity logs, identify unusual behavior, and conduct session replays for deeper analysis when needed. Regular audits are crucial for ensuring safe usage and compliance with organizational and regulatory standards.
PIM vs PAM vs IAM: Key Differences in Privileged Identity and Access Management
Understanding the differences between Privileged Identity Management (PIM), Privileged Access Management (PAM), and Identity & Access Management (IAM) is crucial for building a secure and efficient cybersecurity framework. If you're looking for an in-depth comparison of PIM vs PAM vs IAM , check out our blog on PIM vs PAM and IAM vs PAM. Each of these solutions serves distinct purposes but often works together to provide layered security for managing user access and protecting critical resources. Here’s a breakdown of their unique roles and how they complement each other
Identity & Access Management (IAM)
IAM is the foundation of identity and access security, encompassing policies, technologies, and processes for managing user identities and their access rights within an organization. It ensures that only authenticated and authorized users can access specific resources. While IAM covers all types of users, including employees, customers, and partners, it also includes management of privileged users.
Key Role of IAM:
- Manages digital identities across the organization.
- Controls access to various systems and applications.
- Enforces policies to authenticate users and determine their access rights.
IAM is the broadest of the three and serves as the base upon which Privileged Identity Management and Privileged Access Management build additional, specialized security layers.
Privileged Identity Management (PIM)
PIM focuses specifically on the identities of privileged accounts—those with elevated access, such as system administrators and database managers. PIM solutions are designed to manage the entire lifecycle of privileged identities, including their creation, maintenance, and removal. With privileged identity management tools, organizations can gain visibility over privileged accounts and apply strict access controls to limit their usage to only authorized individuals.
Key Role of PIM:
- Discovers manages, and secures privileged identities.
- Enforces policies for the lifecycle management of privileged accounts.
- Limits privileged identity access to prevent unauthorized use.
PIM ensures that privileged accounts are well-governed, thereby reducing the risk of misuse or unauthorized access that could lead to data breaches or insider threats
Privileged Access Management (PAM)
PAM goes a step beyond privileged identity management by focusing on controlling access to sensitive resources. PAM provides a more comprehensive solution that includes just-in-time access, secure remote access, and session recording. While PIM secures the identities of privileged users, PAM secures their access to critical systems and data, offering real-time monitoring and validation of privileged sessions.
Key Role of PAM:
- Manages access to critical resources for privileged users.
- Provides features like just-in-time access and session monitoring.
- Enhances security with detailed tracking and response to suspicious activities.
PAM offers advanced control over privileged access, allowing organizations to closely monitor how privileged accounts interact with sensitive systems. This makes PAM ideal for detecting and responding to potential security threats in real time.
How They Work Together
IAM, PIM, and PAM work hand-in-hand to provide comprehensive security. IAM establishes a secure foundation by managing general user identities and access, while PIM and PAM add layers to manage and monitor privileged accounts and access. Together, these solutions ensure that only authorized individuals can access sensitive resources, reducing the risk of both internal and external security threats.
By integrating Privileged Identity Management and Privileged Access Management within an IAM framework, organizations can achieve a robust security posture, minimizing vulnerabilities and safeguarding valuable assets.
Compliance Benefits of PIM
Implementing Privileged Identity Management (PIM) supports regulatory compliance by restricting superuser access to authorized individuals only. Many regulations, like the General Data Protection Regulation (GDPR), mandate controlled access to sensitive data and critical assets. With PIM tools and policies, organizations can enforce these standards, ensuring that only qualified personnel access sensitive information, thereby meeting compliance requirements and strengthening security practices.
What are the Best Practices for Privileged Identity Management(PIM)?
To implement Privileged Identity Management(PIM), it can be helpful to follow these proven strategies:
- Create a policy that specifies how superuser accounts are managed and what the account holders should and should not be able to do.
- Develop a management model that identifies a responsible party to ensure that the above policies are followed.
- Inventory privileged accounts to determine how extensive the population is and to identify the holders.
- Establish tools and processes for management, such as provisioning tools or specialized PIM products.
It's also important to identify the attack surface, i.e., all the enterprise assets that are at risk of compromise if a privileged account is misused. Creating an IT asset inventory can show which assets are most in need of protection, which can then provide guidance for the creation of an effective privileged account policy and program.
Deploying two-factor authentication or multifactor authentication, implementing a password policy, and monitoring the behaviors and activities of privileged account holders are some other ways to implement PIM and protect privileged accounts and the enterprise from malicious users.
How to Choose the Right Privileged Identity Management (PIM) Solution for Your Enterprise in 2024
Selecting the right Privileged Identity Management (PIM) solution for your enterprise is essential to ensure comprehensive protection over high-level accounts. Here are some critical factors to consider as you evaluate PIM solutions:
- Identify Your Organization’s Privileged Account Needs Begin by understanding the scope and requirements of your organization’s privileged accounts. Assess how many privileged accounts are in use, the level of access each requires, and the specific areas where privileged access is most critical. This assessment will guide you in choosing a PIM solution that best aligns with your organization’s security needs.
- Look for Robust Access Control Features A strong PIM solution should offer advanced access control features, such as Role-Based Access Control (RBAC) and Just-in-Time (JIT) access. These features help limit access to critical systems by ensuring each user only has access when they genuinely need it. Look for tools that support granular control, helping you enforce the principle of least privilege effectively.
- Prioritize Monitoring and Auditing Capabilities Effective monitoring and auditing are essential components of privileged identity management systems. Choose a solution that provides real-time tracking, session recording, and detailed audit trails to detect any suspicious activities. Comprehensive monitoring enables quick responses to security incidents and provides the insights needed for compliance reporting.
- Ensure Compliance Support A Privileged Identity Management system that includes compliance support will help you meet regulatory standards such as GDPR, HIPAA, and more. Look for a PIM solution with automated reporting features and easy access to audit logs, ensuring that you can quickly provide compliance documentation when needed.
- Consider Scalability and Integration As your organization grows, your PIM needs may change. Choose a solution that can scale alongside your enterprise and integrate smoothly with existing identity and access management (IAM) systems. A scalable and compatible PIM solution will offer flexibility as your security landscape evolves.
- Evaluate User Experience and Usability PIM solutions that are intuitive and user-friendly encourage widespread adoption among your IT teams. Select a tool with a clear interface and streamlined workflows, ensuring that your administrators can manage privileged accounts efficiently without complex processes.
Next Step
In 2024, as cybersecurity threats continue to evolve, having a reliable and comprehensive PIM solution is more critical than ever. miniOrange offers powerful PIM solutions tailored to meet enterprise needs, helping you secure privileged identities and protect sensitive data with confidence.
Author





Leave a Comment