So, what is Zero Trust Architecture (ZTA)?
In this article, we’ll explain ZTA and why it’s becoming essential for businesses today. We'll also provide a simple roadmap to help you implement it successfully.
What is Zero Trust Architecture (ZTA)?
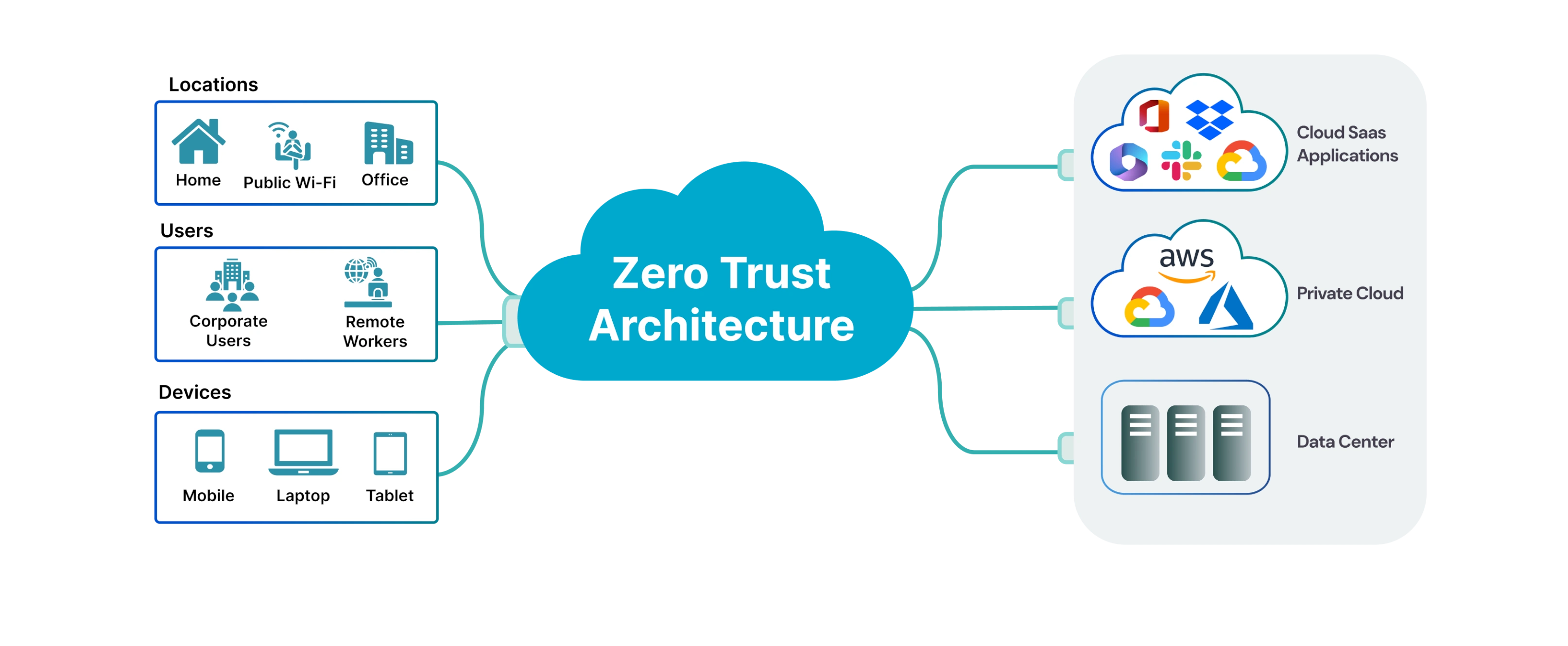
Zero Trust Architecture (ZTA) is a security strategy that is based on a straightforward idea — trust no one automatically, whether they’re inside or outside your network. Everyone, including employees and devices, has to prove who they are before getting access to any resources every time.
Why does this matter?
Well, modern businesses now use cloud apps, allow employees to bring their own devices, and support remote working options. These changes make it easier for hackers or suspicious users to sneak in by pretending to be someone trustworthy. Traditional security, which mostly includes username and password authentication, isn’t enough anymore. ZTA assumes threats can come from anywhere and makes sure every access request is verified to keep data safe.
As part of a comprehensive zero trust security architecture, organizations can implement zero trust network architecture principles to enhance their defenses. By ensuring that every access request is scrutinized, businesses can create a robust zero-trust architecture model that effectively mitigates risks associated with modern cyber threats.
ZTA vs ZTNA Difference
There is a common confusion between Zero Trust Architecture (ZTA) and Zero Trust Network Access (ZTNA). While they both come from the same zero trust security architecture idea, they serve different purposes.
To put it in simple terms, ZTA's job is to ensure that no device or user is trusted by default, no matter where they’re connecting from. It keeps checking users and devices across your entire network and cloud systems to maintain tight access control at all times.
Zero Trust Network Access, on the other hand, focuses on secure remote access. It gives users access only to the apps or systems they need—nothing more, nothing less. ZTNA is like applying ZTA’s principles specifically to remote access scenarios, ensuring control over “who gets what” access. This aligns with the zero trust network architecture security framework, which emphasizes continuous verification of users and devices.
Here’s a simplified comparison between ZTA and ZTNA:
| Aspect | Zero Trust Architecture (ZTA) | Zero Trust Network Access (ZTNA) |
|---|---|---|
| Goal | ZTA covers the entire security infrastructure (users, devices, applications, and data). | ZTNA secures access to all applications and services on the network. |
| Features | Identity-based verification, micro-segmentation, continuous monitoring, and least privilege access. | Secure remote access, single sign-on (SSO), application-level access, and encryption. |
| Use Case | Protects everything: apps, users, data, and devices inside and outside the network. | Provides remote access to specific apps for employees, vendors, or contractors. |
| Best For | Organizations looking for a complete security overhaul should adopt Zero Trust principles. | Companies with remote workers need access to cloud-based or internal apps securely. |
Core Principles of Zero Trust Architecture
The core principle of Zero Trust Architecture (ZTA) is simple: "Never trust, always verify." This means that no user or device should be automatically trusted, regardless of whether they are inside or outside the network perimeter.
Let’s break down the key principles of ZTA:
1. Least Privilege Access Controls
Zero trust security architecture ensures people only get access to what they need—nothing more. Using [role-based access control (RBAC), access is granted based on someone’s role.
For example, if you’re only allowed to view reports, you won’t get access to edit them. All traffic is blocked by default unless explicitly authorized, and every connection requires strict authentication, even from familiar users.
2. Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) adds an extra layer of security. Instead of just a password, users need to provide multiple pieces of evidence—like a PIN, text message, or fingerprint. This ensures that even if one factor is compromised, the system stays secure.
3. Micro-segmentation
Think of micro-segmentation as creating small “rooms” inside a network, each with its own set of rules. Even if an attacker enters one room, they can’t roam freely. This strategy helps security teams control data sharing and limits movement between different sections of the system.
4. Device Access Control
It’s not just about who logs in but also what device they’re using. Every device must meet security standards before accessing company resources. Even if the user is verified, the device must pass the test to maintain security.
The 5 Pillars of ZTA
The 5 Pillars of Zero Trust Architecture (ZTA) are fundamental principles that ensure no user or device is inherently trusted, regardless of their location or network. Here’s an overview of each pillar:
- Identity: Verifies who or what is accessing your system using strong authentication and behavior tracking tools to catch suspicious activity in real time.
- Device: Ensures that every device connecting to the network is known and compliant, preventing access from insecure or unauthorized devices.
- Network: Divides the network into smaller segments to restrict access only to necessary areas, reducing the risk of compromised credentials granting access to sensitive sections.
- Application and Workload: Limits application permissions to only what is necessary and ensures regular security updates to prevent vulnerabilities. Continuous monitoring helps detect and block unauthorized access.
- Data: Classifies data based on value and sensitivity, granting access only to those with a valid need. Encryption ensures that even intercepted data remains unreadable.
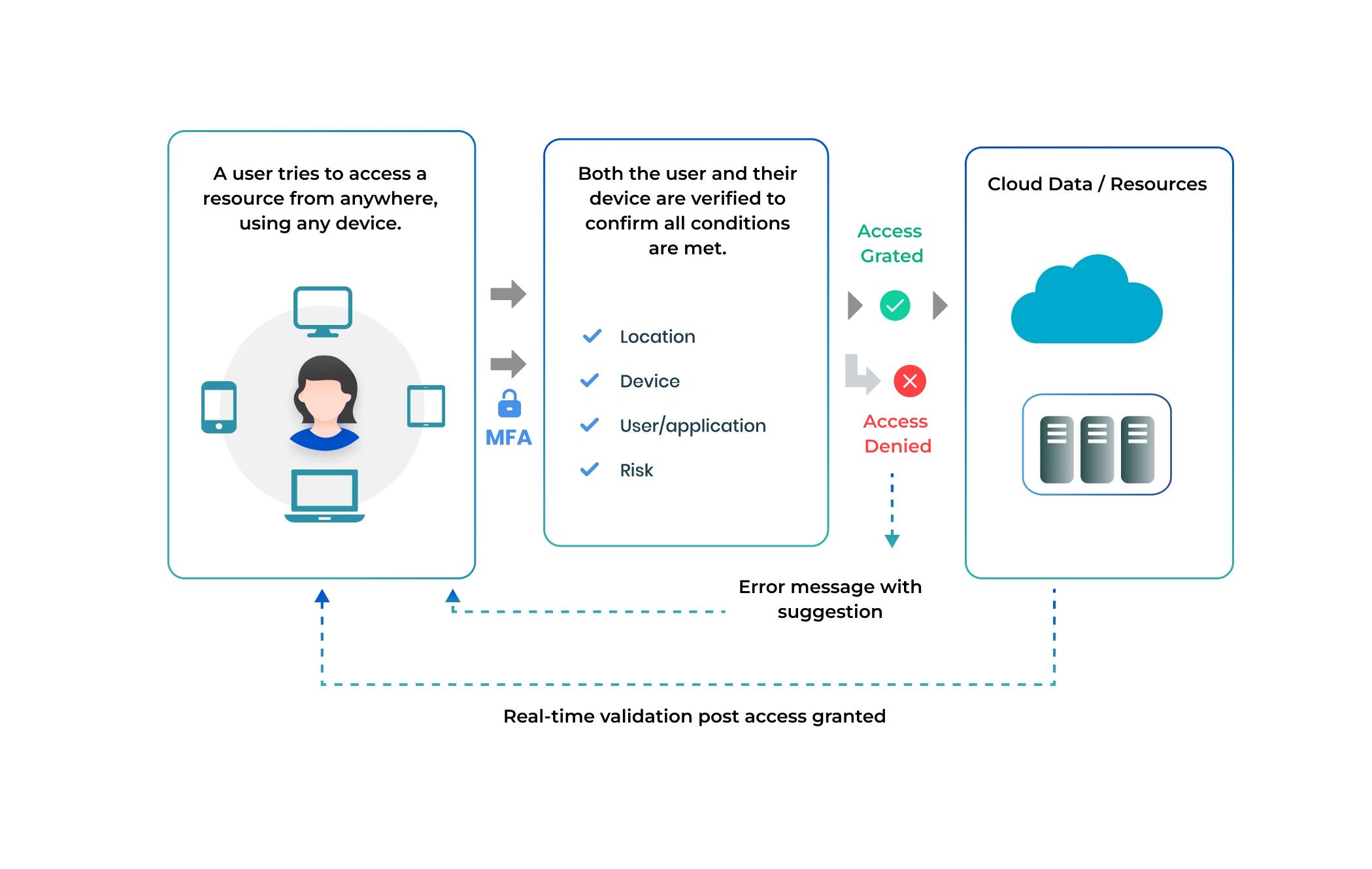
How ZTA Works?
ZTA works by verifying every access attempt, assuming no one is trustworthy by default—even within the network. It requires users and devices to verify their identity every time they access an application or data.
Here’s a quick look at how ZTA works, broken into three easy-to-follow steps:
Step 1: Verify Identity and Context
When someone or some device requests access, the connection is paused to confirm who is requesting, what they need, and from where they are accessing it. This step is crucial in implementing both the zero trust network architecture and zero trust security architecture.
Step 2: Control Risk
After verifying identity and applying segmentation rules, the system checks for potential risks — like suspicious behavior or sensitive data in traffic—and evaluates whether the request is safe.
Step 3: Enforce Policy
The system assigns a risk score to the user, device, or workload. If everything checks out, a secure connection is established to the requested app, whether on the internet, a SaaS platform, or a cloud environment (like IaaS/PaaS). If the risk is too high, access is denied.
Benefits of ZTA Security Model
Zero-trust architecture (ZTA) ensures secure, hassle-free access to the tools and data your team needs while keeping your business safe from cyber threats.
Here are the key benefits of ZTA for modern businesses:
1. Fast and Secure Remote Access
Employees and partners can easily access business data and apps from anywhere without delays, improving their user experience. ZTA simplifies remote access management and strengthens security, outperforming older tools like VPNs.
(Read our blog on ZTNA vs. VPN)
2. Strong Protection for Sensitive Data
ZTA secures your data and apps—whether on local servers or in the cloud—during transmission or storage. Encryption, on-premise multi-factor authentication (MFA), and regular security audits help maintain high protection levels.
3. Stops Insider Threats
By not granting automatic trust to any user or device (even those inside the network), ZTA minimizes the risk of insider attacks.
4. Prevents Lateral Movement
ZTA uses detailed, resource-level policies to restrict access, making it harder for attackers to move within the network.
5. Quick Breach Response
ZTA quickly detects and responds to security threats, helping to minimize damage and speed up recovery times.
6. Detailed Monitoring for Better Control
Every session and action is tracked, providing full visibility into user and device activities.
7. Real-Time Risk Assessment
ZTA continuously monitors device health, user behavior, and resource usage to detect risks early and prevent potential breaches—demonstrating the effectiveness of zero trust architecture.
To Sum Up
Zero Trust Architecture (ZTA) ensures that no one—whether a user or a device—is automatically trusted, even if they’re already inside your network. This approach enhances security for modern businesses, allowing remote workers to access data and applications quickly and safely. Tools like encryption and multi-factor authentication (MFA) help safeguard sensitive information and reduce the likelihood of insider threats.
ZTA also regulates movement within the network through detailed access policies and offers close monitoring to detect and respond to potential security issues promptly.
Want to Try Zero Trust Architecture?
If you’re considering adopting Zero Trust Architecture, check out miniOrange's Zero Trust Security Solution. It guarantees secure access for everyone—employees, partners, and applications—whether they’re on-site or in the cloud.
Get Started with miniOrange Today!
Protect your organization’s future with the power of Zero Trust Architecture. Reach out to us at info@xecurify.com to learn how miniOrange can assist you in implementing ZTA and maintaining security at every level of your business.
Reference links
Author

Leave a Comment