To make WFH possible, businesses must ensure their remote employees can access internal apps and business data from anywhere, anytime. This may seem logical but it does raise some concerns related to trust, such as the mishandling or sharing of confidential data like customer information by remote employees. Such unfortunate incidents could be detrimental to a company's bottom line and reputation. To tackle this, businesses are considering the use of solutions like Zero Trust Network Access (ZTNA) and Virtual Private Network (VPN), but many of them are still unsure as to which one best suits their use case and requirements.
Let’s clear up this confusion!
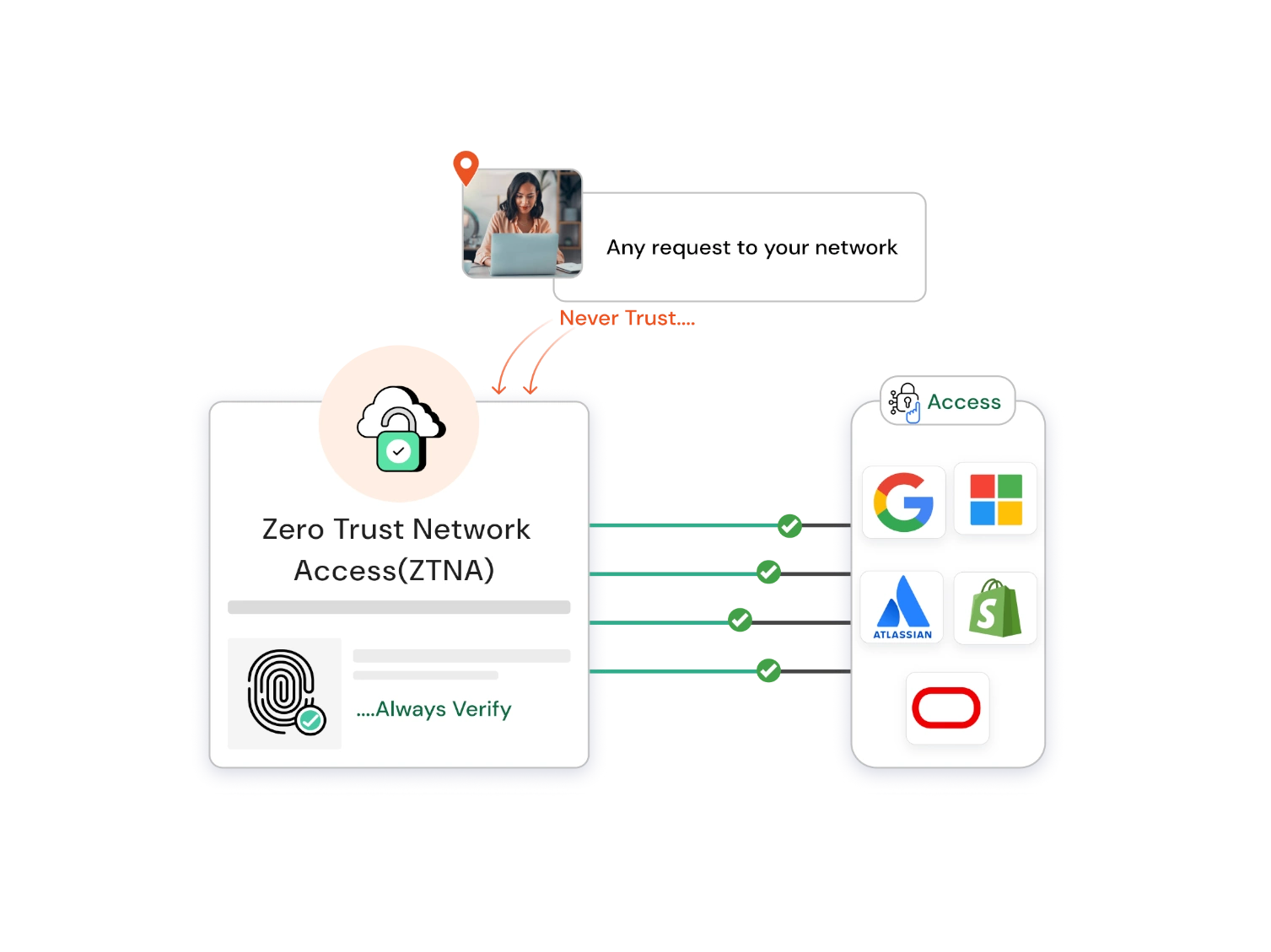
What is ZTNA?
Zero Trust Network Access (ZTNA) is a security solution that helps businesses set policies that require users, whether working remotely or from the office, to verify their identity before accessing any application or business data. It follows the principle of "never trust, always verify," meaning access is only given after evaluating factors like:
- User identity
- Device security
- Group or user role in the organization
- Geolocation, etc.
ZTNA dynamically grants access to specific apps or data that employees need at a given time. This access is immediately revoked once the session ends.
In short, Zero Trust Network Access allows organizations to selectively and securely provide access to their applications and resources without exposing their entire network. This is where zero trust providers play a crucial role in delivering ZTNA as a service.
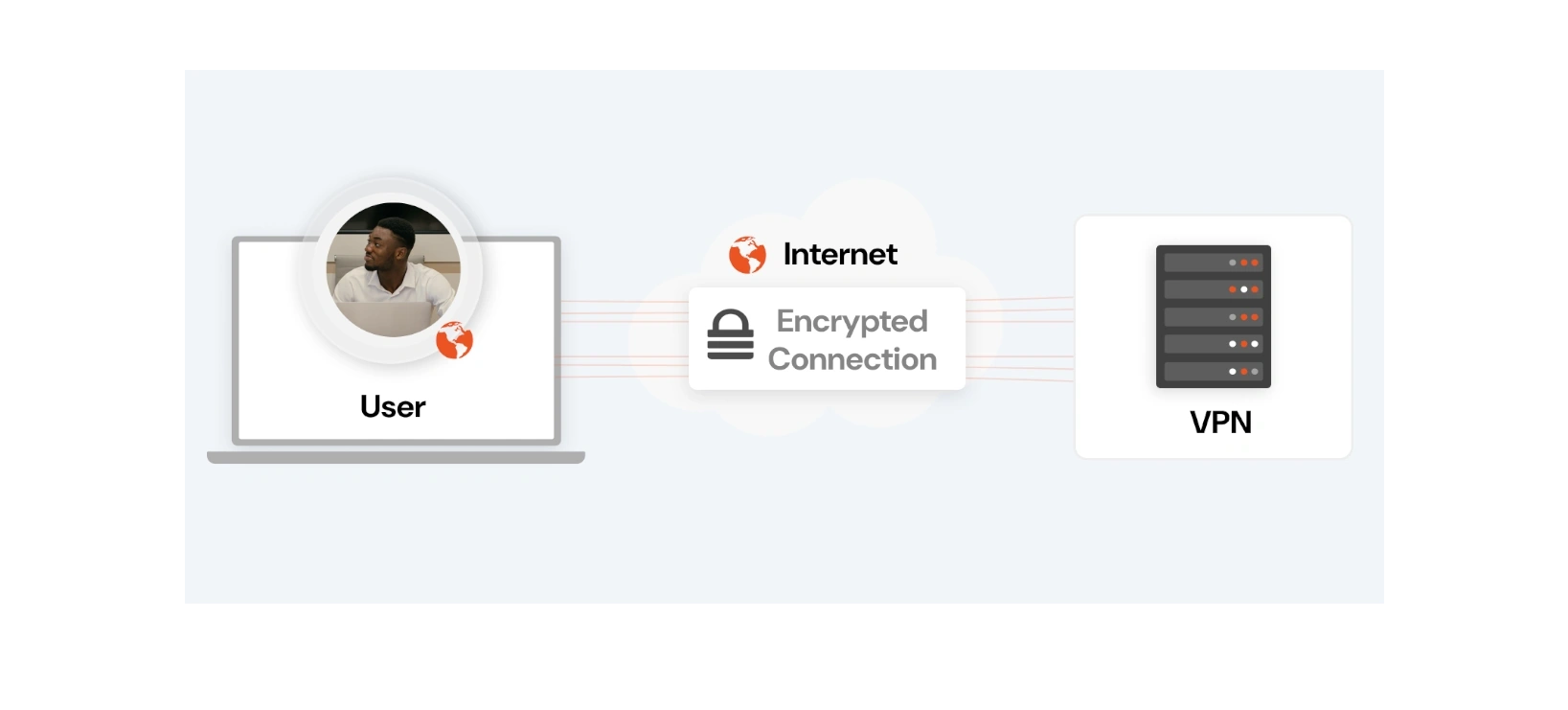
What is VPN?
A VPN (Virtual Private Network) is a technology that creates a secure and encrypted connection between two networks or devices over the internet, providing remote access for distributed workforces. When a user connects to a VPN, internet traffic is encrypted and sent through a secure tunnel to a VPN server. This changes your IP address to match the VPN server's IP, hiding your identity and location. As a result, your data is protected from eavesdropping, and all business traffic can be inspected by security solutions, no matter its source. However, as remote work becomes more common and businesses rely more on cloud-based apps, VPNs are struggling to keep up compared to modern Zero Trust Network Access solutions.
ZTNA vs VPN - Key Differences
| Feature | ZTNA (Zero Trust Network Access) | VPN (Virtual Private Network) |
|---|---|---|
| Security Posture | Continuously verifies users, devices, and access levels, limiting exposure to sensitive resources. | Provides access to the entire network once a user is authenticated. |
| User Access Control | Allows users to only access specific apps or data they are authorized to use. | Grants wide-range access to all network resources once connected. |
| Deployment Model | Primarily cloud-based, allowing for easier deployment, management, and updates. | Usually requires on-premises hardware or appliances, which can be cumbersome to deploy and maintain. |
| Remote Work Compatibility | Built specifically for secure remote access, making it ideal for remote or hybrid work environments. | Designed for remote access but may not be optimized for large-scale remote or hybrid work setups. |
| Scalability | Designed for dynamic environments and growing remote workforces. | Limited scalability. Its performance can degrade with an increase in users. |
| User Experience | Simple and fast access to cloud apps. | Slower speeds due to encryption and tunneling processes. |
| Cloud Integration | Integrates with cloud-based apps and services. | Integrates with on-premises network access; less optimized for cloud environments. |
| Performance Impact | Less performance impact due to app-specific access. | Impacts performance due to encrypted tunnels and high bandwidth usage. |
Limitations of VPN over ZTNA
Virtual Private Networks (VPNs) are often used by businesses for secure remote access, particularly in perimeter-based security models. However, VPNs have several limitations that make them less suitable for the security needs of modern businesses. Here are the main drawbacks:
- No Cloud Support: VPNs are designed for secure remote access to corporate networks. However, they often struggle to support cloud-based apps like Google Workspace, Office365, and other resources outside the traditional network perimeter.
- Network-Level Access Controls: VPNs provide access controls at the network level but lack visibility and control over individual applications. This means users may gain broad access to sensitive resources within various apps. If a cybercriminal breaches your VPN, they could easily access your confidential data.
- Poor Support for BYOD Devices: Allowing employees to use their own devices (BYOD) to access the corporate VPN exposes the network to potential threats from unmanaged endpoints. Malware or other cyber threats can gain direct access to corporate resources.
The ZTNA Advantage
Zero Trust Network Access (ZTNA) offers a different approach. It doesn't require users to connect to the corporate network. Instead, it verifies identity first and grants access afterward, allowing secure use of cloud apps over the public internet. This approach is ideal for remote-first companies, enabling employees to work securely from public spaces like cafes, airports, or anywhere else.
Top Use Cases for ZTNA Solutions
Remote Work Security
Zero Trust Network Access improves remote work security by allowing employees to securely access the company’s network and resources from anywhere. It protects sensitive data while keeping productivity high. For example, a remote team member can connect to the company's internal systems without worrying about data leaks or unauthorized access.
Cloud Apps Security
ZTNA locks down cloud-based applications, ensuring only the right people get in. Using CASB Cloud Apps Security, ZTNA reduces the risk of data breaches and keeps vital information secure. Picture an organization using multiple cloud tools; with Zero Trust Network Access, only verified users can access these tools, minimizing threats.
Bring Your Own Device (BYOD)
ZTNA improves Bring Your Own Device security, allowing employees to work from their personal devices while keeping the network safe. Each device and user is verified, ensuring only approved devices gain access. For instance, an employee could use their smartphone for work, but ZTNA will ensure it's authorized before any data is shared.
Network Visibility
ZTNA boosts visibility for IT teams in Corporate Office Networks, letting them see who is accessing the network and what they’re doing. This helps quickly detect and respond to threats. For example, if an unauthorized user tries to log in, the IT team gets an alert instantly.
Compliance Management
Zero Trust Network Access simplifies meeting regulatory compliances by ensuring only authorized users access sensitive data. This makes audits smoother and strengthens overall security. Imagine preparing for an audit; ZTNA provides clear records showing who accessed what, helping you pass with ease.
Choosing the Right Enterprise ZTNA Solution
Most businesses start using the ZTNA strategy by applying it to a specific use case. At an early stage, it’s crucial to check if the chosen ZTNA solution can go beyond this initial use case and meet other current needs.
Before selecting a use case to pilot a Zero Trust Network Access solution, ask yourself these points:
- Types of Apps Supported: Does your ZTNA solution support all app types—legacy, Web3, cloud, etc.?
- Server-Initiated Communication: Do your apps require the server to initiate communication with the client?
- Compatibility with IoT Applications: Can the ZTNA solution handle IoT devices and provide unattended access?
- Internet Policy Enforcement: Should your ZTNA solution control internet access?
- Secure Communication Across Data Centers: Can it secure communications between data centers?
How miniOrange Can Help?
miniOrange offers cutting-edge Zero Trust Network Access solutions that are designed to meet the needs of today’s businesses. Our solutions work in line with your current business setup, providing strong security and easy management of remote access.
No matter where your users are or what devices they’re using, miniOrange ensures they can access applications safely. Our ZTNA solutions come with features like multi-factor authentication and CASB that help adjust access based on factors like user location or device status and monitor for suspicious activity to prevent threats.
Features of miniOrange ZTNA Solution
- Zero Trust for All Apps: Extend Zero Trust principles to all your applications, restricting user access to only what’s necessary.
- Remote Access to On-Premises Tools: Get identity-based access control and quick performance for cloud applications, ensuring secure remote access.
- Fine-Tuned Security: Protect your data consistently across all cloud apps with a single, customizable data loss prevention (DLP) policy.
- Frictionless Access from Any Device: Easily expand security with agentless deployment, supporting both managed and unmanaged devices for BYOD (Bring Your Own Device) and contractor access.
- Extend DLP to Private Apps: Secure data in private web apps continuously with predefined policies and malware scanning. Reduce the attack surface by masking private apps from the internet, making them visible only to authorized users.
Final Word
Zero Trust Network Access solutions are revolutionizing the secure work-from-home model, offering businesses a modern, scalable way to manage remote work securely. By using a zero-trust approach, ZTNA enhances security, boosts scalability, improves productivity, and provides a smoother user experience. As remote work continues to rise, Zero Trust Network Access is quickly becoming the go-to choice for companies wanting to secure their networks and applications.
With the growth of the remote workforce, security threats are also on the rise. Companies need a robust remote access solution to safeguard their sensitive cloud data. While both VPNs and ZTNA provide remote access to corporate networks, they do so differently. VPNs can be effective for smaller setups, but ZTNA is considered the more modern, secure, and scalable option for today’s business needs.
Reference links
Author

Leave a Comment