Adaptive Authentication
Why should I need to configure Adaptive Authentication (MFA) for Super Admin?
If you want to reduce the burden of 2fa on your users and also want to add the extra layer of security, you can do that by configuring adaptive authentication methods. With miniOrange you can set adaptive methods differently for super admin and users.
1. Adaptive Authentication Configuration
How to Add a new Adaptive Authentication Policy:
- Login to Self Service Console and navigate to Adaptive Authentication section from the left side menu.
- In Configure Adaptive Risk Authentication select Add Policy tab and add name for your policy.
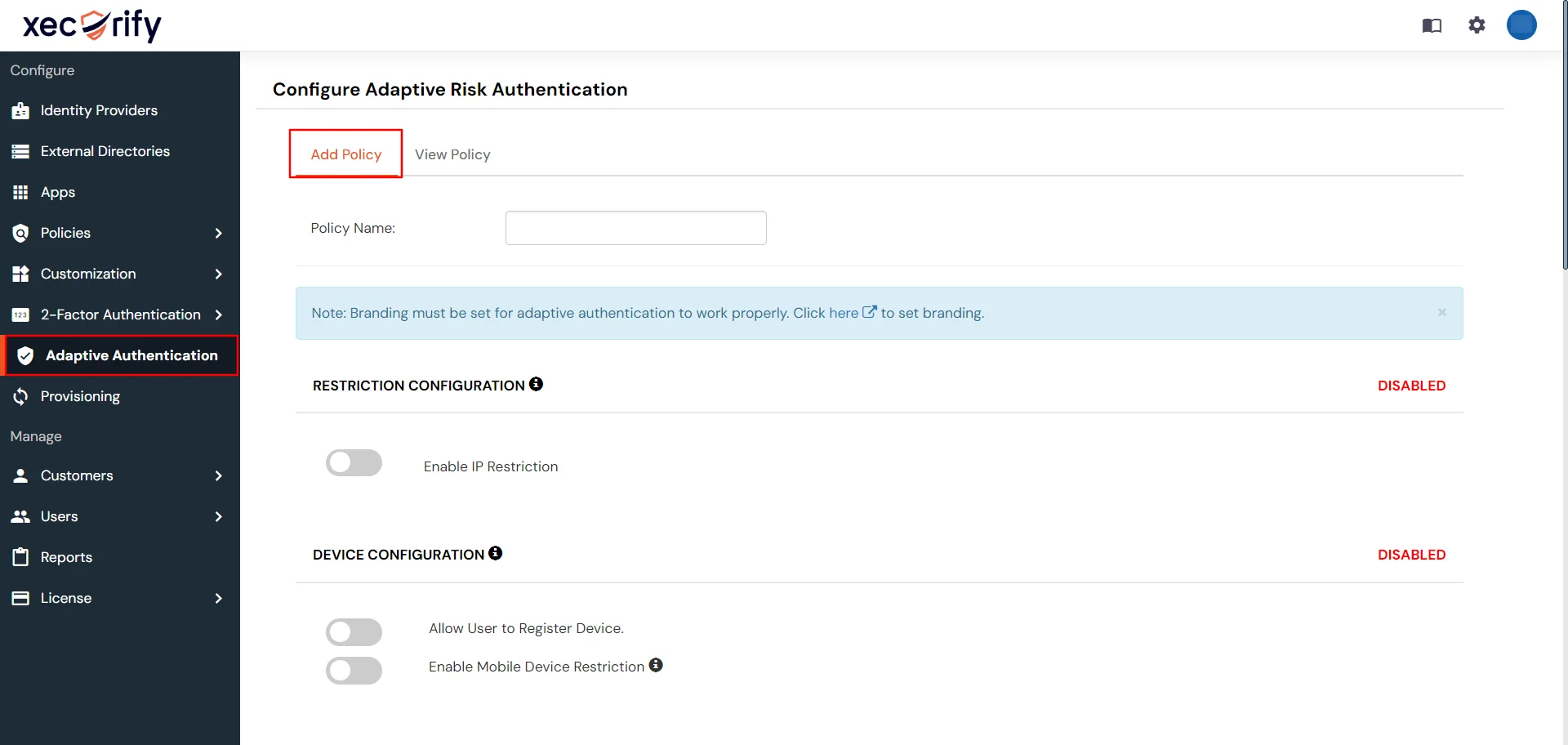
- There are six different sections you can configure in a Adaptive Authentication Policy :
- IP Restriction Configuration
- Device Restriction Configuration
- Location Restriction Configuration
- Time Restriction Configuration
- Action for behavior Change Configuration
- Notification and Alert Message Configuration
A. IP Restriction Configuration :
In this restriction method super admin configures a list of IP addresses to allow or deny access on and when a user tries to login into any of the applications configured with adaptive authentication, his IP address is checked against the configured IP list and based on that the action is decided as per the configuration (.i.e. Allow, Deny or Challenge).
How to configure IP Restriction :
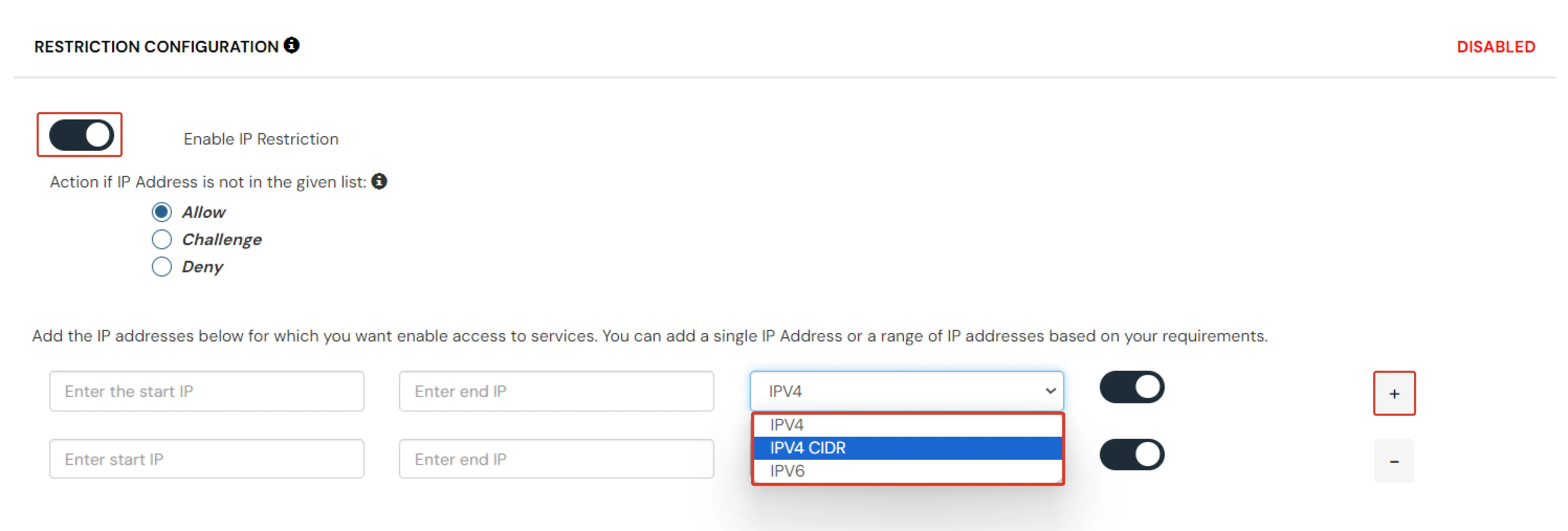
- On the Add Policy tab, navigate to the RESTRICTION CONFIGURATION section and enable the Enable IP Restriction option.
- Select Action for behavior Change if the Users IP Address is not in the configured list.
- Specify the IP Address which you want to whitelist. For the IP Range other that the whitelisted one, you can select the above setting to reflect.
- Choose either allow or deny by selecting the radio button next to it.
- If a user tries to login with the whitelisted IP address, they will always be allowed access.
- We support IP addresses range in three formats i.e. IPv4, IPv4 CIDR and IPv6 CIDR. You can choose whichever is suitable for you from the dropdown menu.
- You can add multiple IP's and IP ranges by clicking on the + button.
- Scroll down to the bottom of the page and click on save.
Note : If you select Challenge as the action then select the same option in the Action for behavior Change Configuration section.
B. Device Restriction Configuration :
In this restriction method super admin allow end-users to add a fixed number of devices as Trusted devices for their account(A device here refers to a Browser Session). Once a device is registered for a user, then that user will be allowed to login without any Restriction (This works with all other Restriction methods also). If the users registered Device exceeds the total registered device limit specified by the super admin, In that case the user will be either Challenged or Denied as specified in the policy by the super admin.
How to configure Device Based Restriction
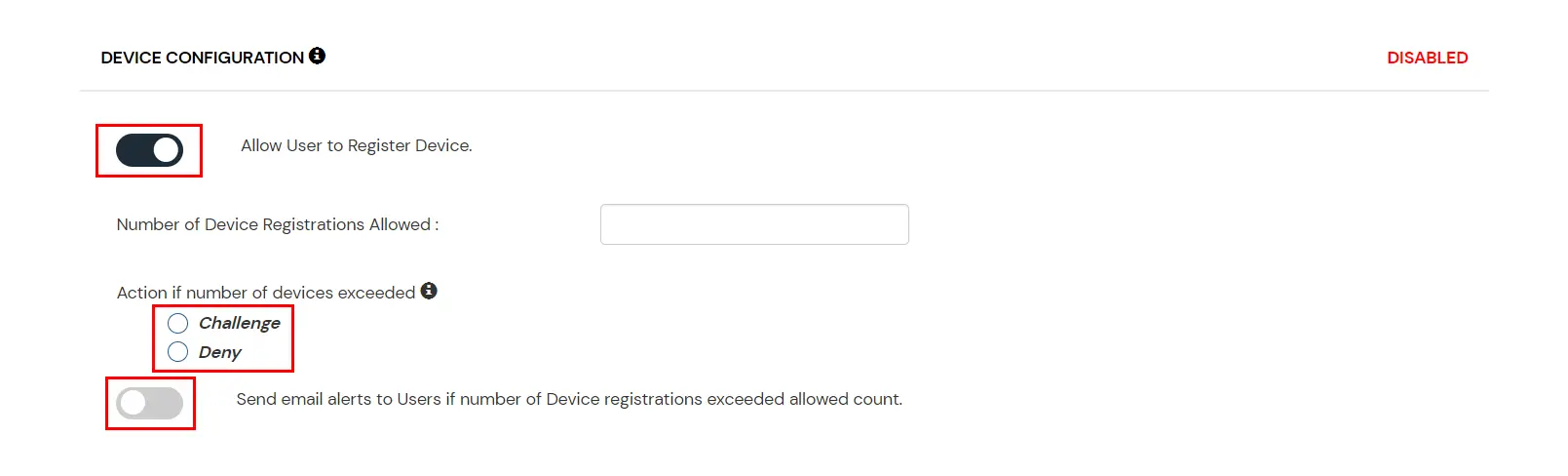
- On the Add Policy tab navigate to DEVICE CONFIGURATION section and enable the Allow Users to Register Device option.
- In the input field next to Number of Device Registrations Allowed enter the no. of devices you want your end-users to register.(2-3 devices are recommended.)
- Select your action if the number of devices registered by users exceeds the allowed limit. (.i.e Challenge or Deny)
- Enable the option Send email alerts to Users if number of Device registrations exceeded allowed count if you want to alert the user about no of devices exceeding the limit.
- Scroll down to the bottom of the page and click on save.
- Notes :
- Users are only allowed to register devices when Challenge is selected as the Action.
- Once a Device is registered, users will be allowed to login seamlessly without any restriction.
- If you select Challenge as the action then select the same option in the Action for behavior Change Configuration section.
C. Location Restriction Configuration :
In this restriction method super admin configures a list of locations where we want to allow end-users to either login or deny based on the condition set by the super admin. When a user tries to login with adaptive authentication enabled, his Location Attributes such as (Latitude, Longitude and Country Code) are verified against the Location list configured by the super admin. And based on this user will be either allowed, challenged or denied.
How to configure Location Based Restriction
- On the Add Policy tab navigate to LOCATION CONFIGURATION section and enable the Enable Location Based Restriction option.
- In the enter location input field enter the Location Name and then select the correct location from the search results using the UP & DOWN navigation keys.
- Add the In and Around Distance for your location in the next input field. This will be the total area in and around the location we have configured using the Latitude and Longitude points.
- In the next select list, select your distance parameter as either KMS(KiloMeters) or Miles. For each Location you add, you can choose to either allow or deny it by enabling or disabling the switch button next to it.
- You can click on the + button to add more than one location and then follow steps 2-4 as mentioned above.
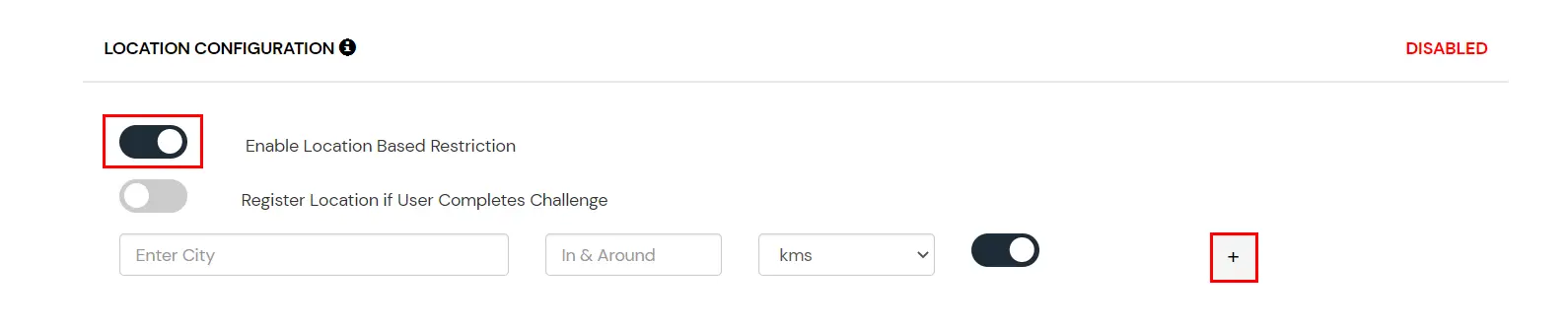
- Scroll down to the bottom of the page and click on save.
D. Time Restriction Configuration :
In this restriction method super admin configures a time zone with Start and End Time’s for that time zone and users are either allowed, denied or challenged based on the condition in the policy. When an end-user tries to login with the adaptive authentication enabled, his time zone related attributes such as Time-Zone and Current System Time are verified against the list configured by the super admin and based on the configuration the user is either allowed, denied or challenged.
How to configure Time Based Restriction
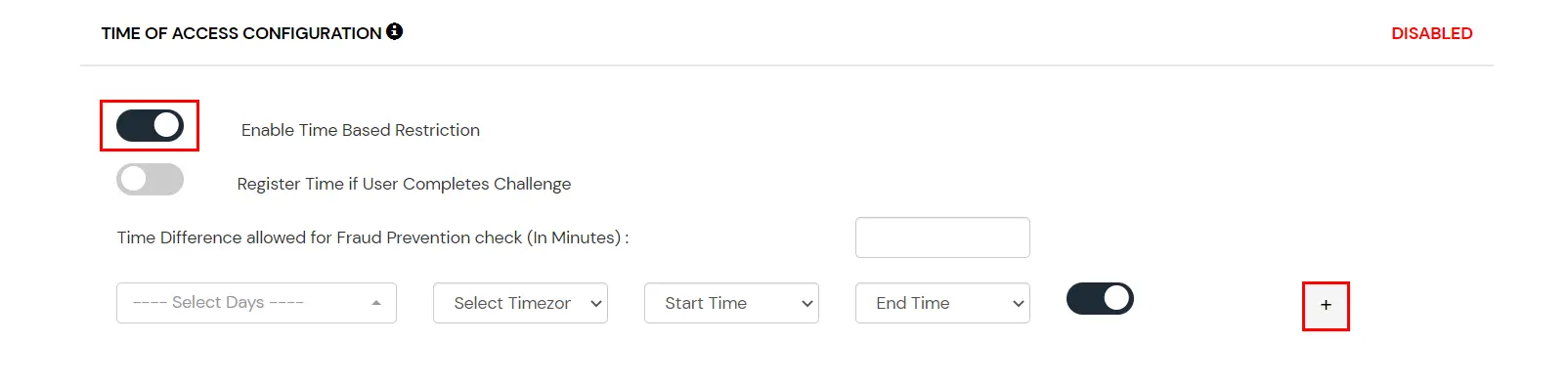
- On the Add Policy tab navigate to TIME OF ACCESS CONFIGURATION section and enable the Enable Time Based Restriction option.
- From the select Timezone list, select the timezone. From the Start Time and End Time lists select the appropriate values. For each Time configuration you add, you can choose to either allow or deny it by enabling or disabling the switch button next to it.
- Enter the a value in minutes in the input field next to Time Difference allowed for Fraud Prevention check. This value allows you to specify some relaxation before your start time and after your end time. (so if the start time is 6 AM and the end time is 6PM with a time difference value set to 30 minutes, then the policy will consider time from 5:30AM to 6:30 PM). If no value is entered in this field, the default value is set which is 15 minutes.
- You can click on the + button to add more than one Time Configurations and then follow step 2 as mentioned above.
2. Action for behavior Change Configuration
You can configure one the three possible actions for your Adaptive Authentication Policy as explained below :
A. Action for behavior Change Options :
| Attribute |
Description |
| Allow |
Allow user to authenticate and use services if Adaptive authentication condition is true. |
| Challenge |
Challenge users with one of the three methods mentioned below for verifying user authenticity. |
| Deny |
Deny user authentications and access to services if Adaptive authentication condition is true. |
B. Challenge Type Options :
| Attribute |
Description |
| User second Factor |
The User needs to authenticate using the second factor he has opted or assigned for such as
- OTP over SMS
- PUSH Notification
- OTP over Email
- And 12 more methods.
|
| Security Questions |
The System will ask the user for 2 of 3 questions he has configured in his Self Service Console. Only after the right answer to both questions is the user is allowed to proceed further. |
| OTP over Alternate Email |
User will receive a OTP on the alternate email he has configured threw Self Service Console. Once user provides the correct OTP he is allowed to proceed further. |
- Action for behavior Change and Challenge Type can be configured from the Action For behavior Change section of the Adaptive Authentication page.

3. Notification and Alert Message Configuration
This section handles the notifications and alerts related to Adaptive Authentication. It provides the following options :
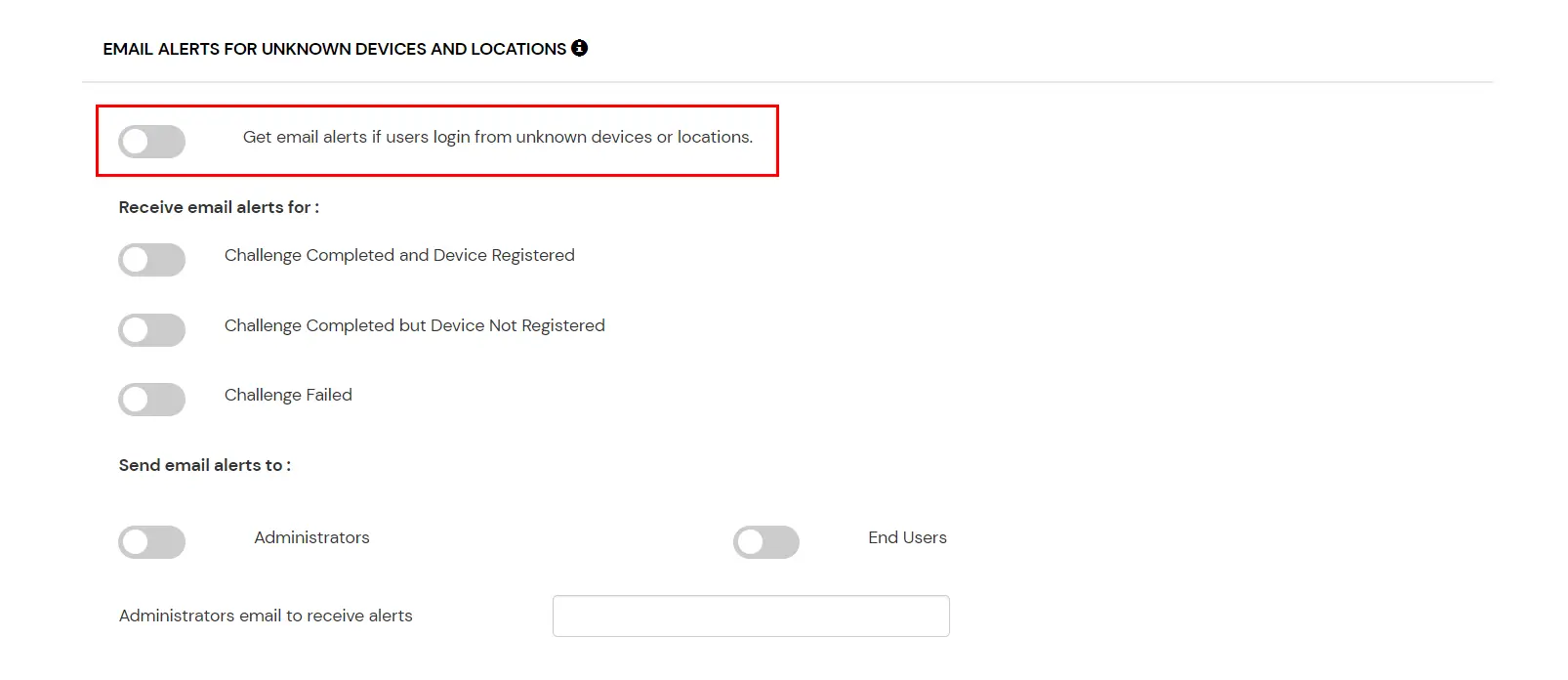
- Get email alerts if users login from unknown devices or locations : Super Admin need to enable this option to enable receiving alerts for different alert options.
| Option |
Description |
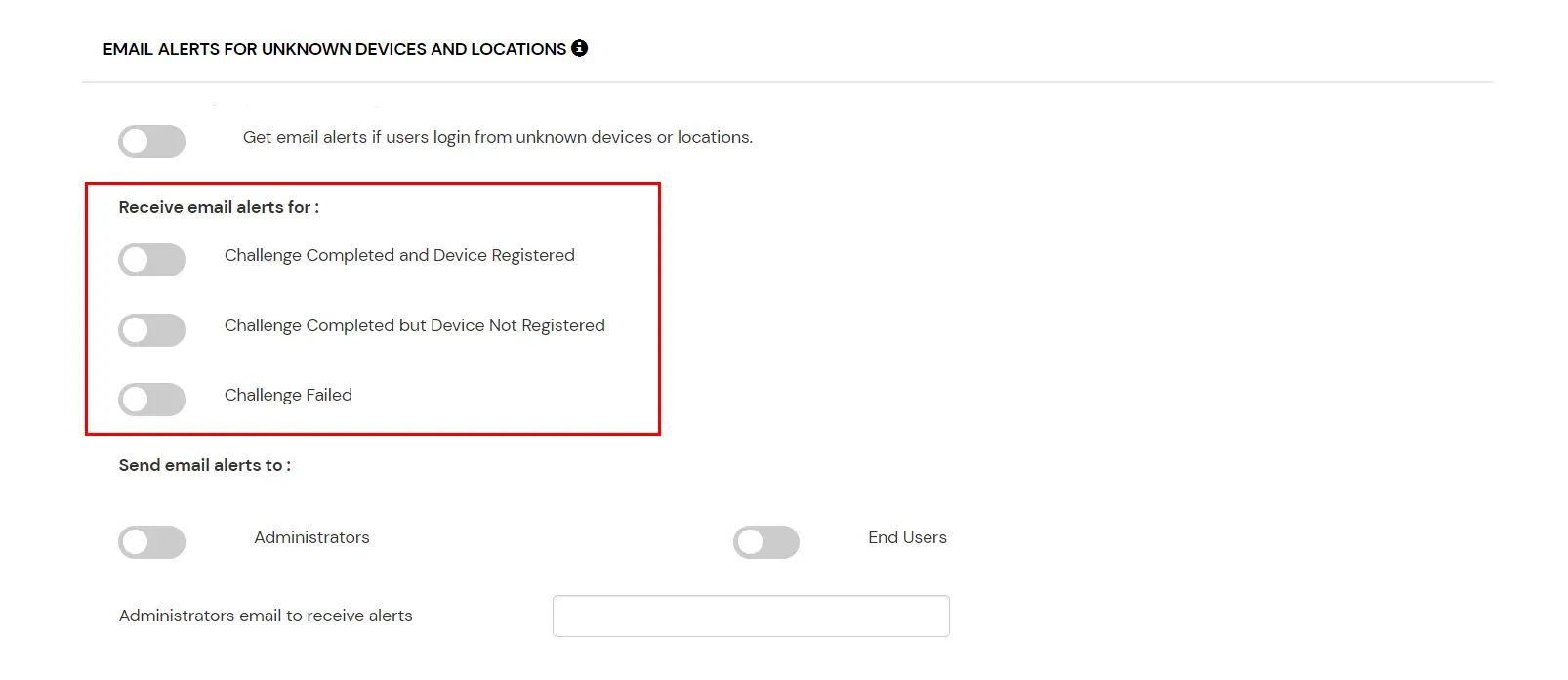
| Challenge Completed and Device Registered |
Enabling this option allows you to send an email alert when an end-user completes a challenge and registers a device. |
| Challenge Completed but Device Not Registered |
Enabling this option allows you to send an email alert when an end-user completes a challenge but do not registers the device. |
| Challenge Failed |
Enabling this option allows you to send an email alert when an end-user fails to complete the challenge. |
- Next subsection is Send email alerts which allows us to enable or disable alerts for super admin and end-users. To enable alerts for super admins, you can enable the “Administrators” switch button.
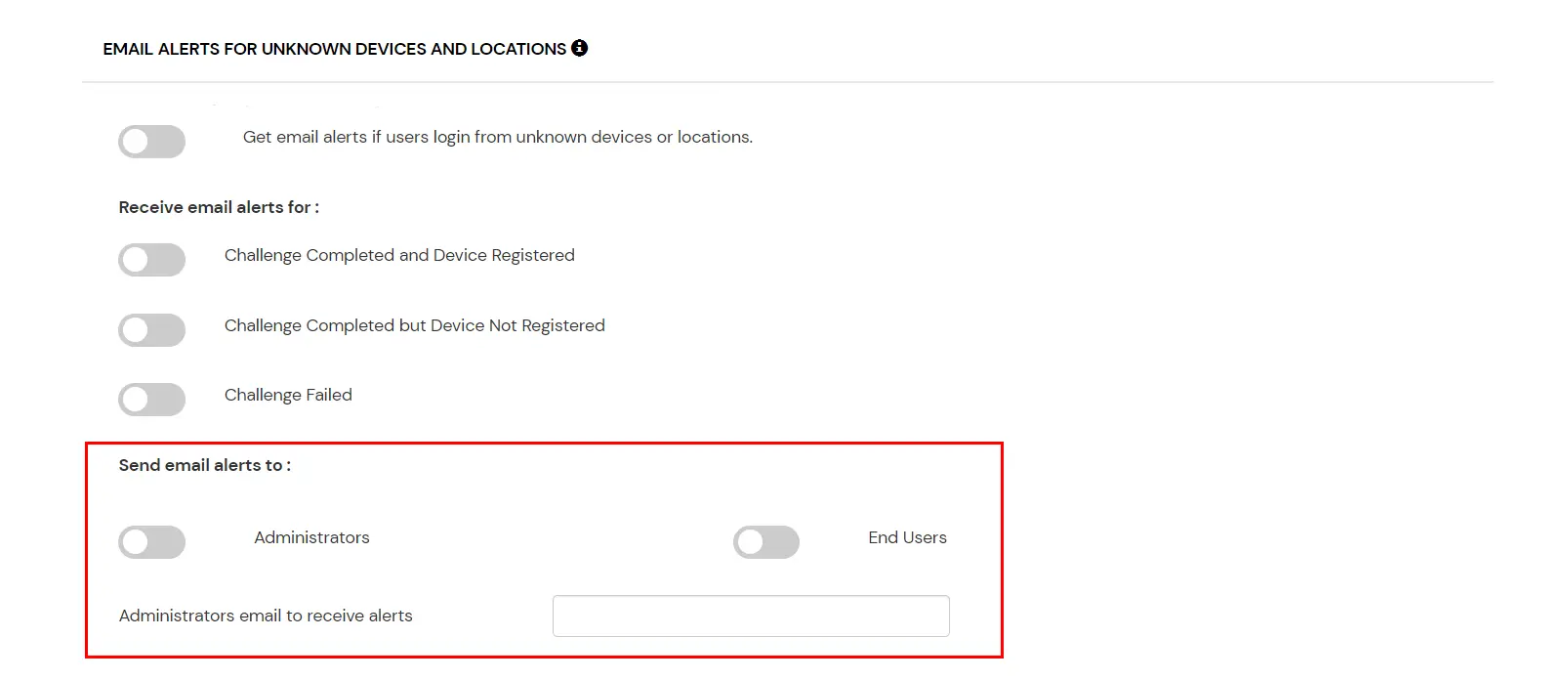
- In case you want multiple super admins accounts to receive alerts then you can enable the option for super admin and then enter the super admin emails separated by a ‘,’ in the input field next to Administrators email to receive alerts label. To enable alerts for the end-users, you can enable the “End Users” switch button.
- In case you want to customize the deny message that end user receive in case his authentication denied due to adaptive policy, you can do this by entering the message inside “Deny message” text box.