Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×
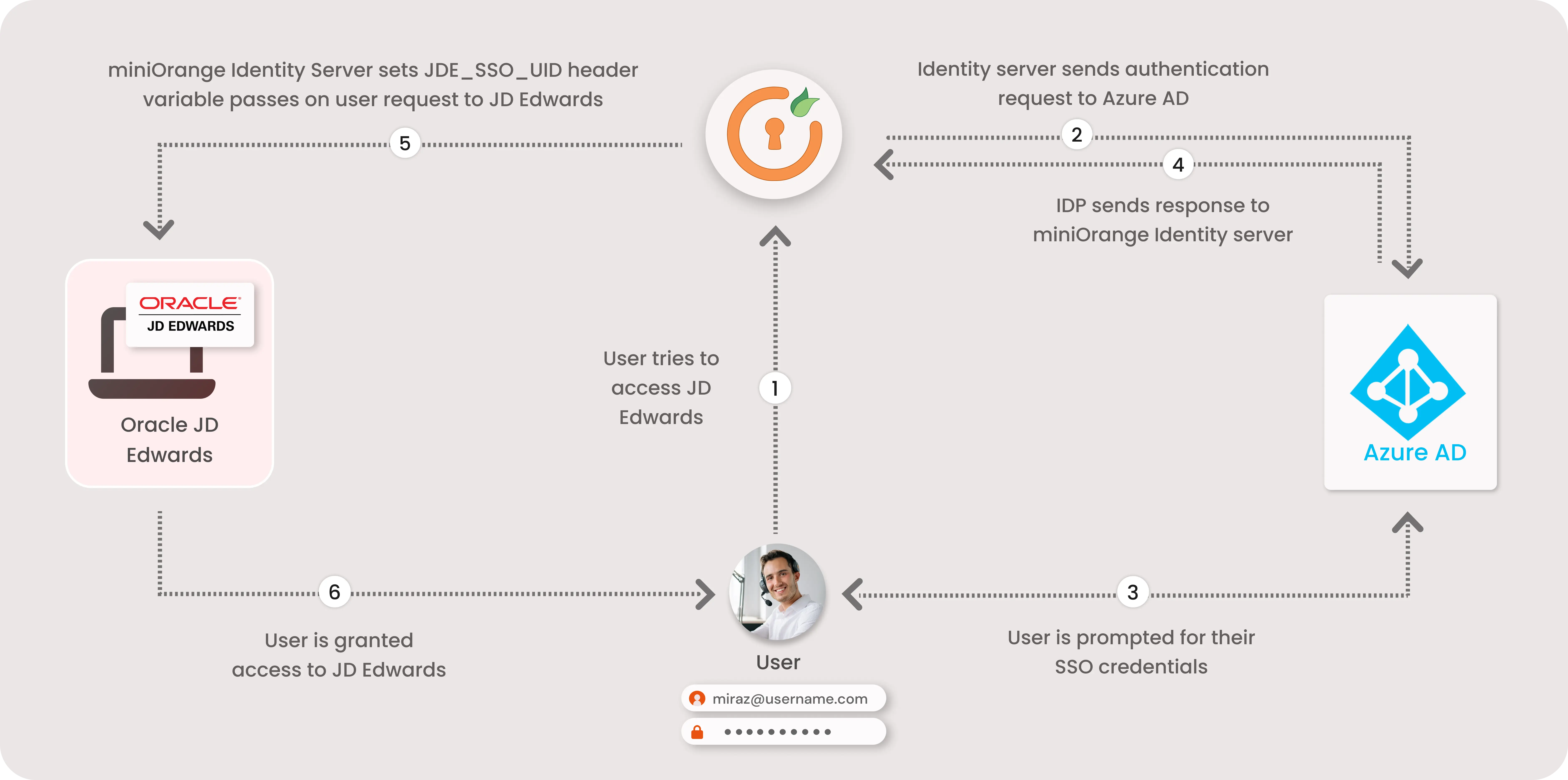
JD Edwards SSO is a feature that enables easy and seamless Single Sign-On into your Oracle JD Edwards application instance authenticating against any of your existing identity source (Azure AD, LDAP, or any IDP).
As we have officially been recognized as a Global Modernized Oracle Partner Network (OPN) Partner, you can rest assured that all of our integrations on the Oracle Stack fulfill the highest competencies set by Oracle for their trusted advisors like miniOrange.
"miniOrange Oracle JD Edwards SSO connector enables Single Sign-On (SSO) between Oracle JD Edwards and any IDPs without the need to purchase and install Oracle Access Manager (OAM) and Oracle Internet Directory (OID) license."
JD Edwards SSO connector enables the Single Sign-On (SSO) integration between any Oracle application and IDPs (Identity Providers) like miniOrange, ADFS, Active Directory, Azure AD, Google, Okta, Onelogin, Ping Idenity, Centrify and many more. It also provide SSO support for web applications which do not provide support for federated Single Sign-On (SSO) protocol such as SAML or OAuth 2.0. SSO connector gives you the flexibility of extending your existing SSO integration to Oracle JD Edwards as well. This is possible due to its capability to act as a broker between multiple IdP's & your configured applications. This states that you can perform seamless SSO integration for Oracle JD Edwards with your existing authentication platform.
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, OpenLDAP, AWS etc), Identity Providers (like Microsoft Entra ID, Okta, AWS), and many more. You can configure your existing directory/user store or add users in miniOrange.
miniOrange offers 1 hour free help through a consultation call with our System Engineers to Install or Setup JD Edwards SSO SAML solution in your environment with 30 days free trial. For this, you need to just send us an email at idpsupport@xecurify.com to book a slot and we'll help you setting it up in no time.
1. Applications involved in the deployment
2. Port Configuration

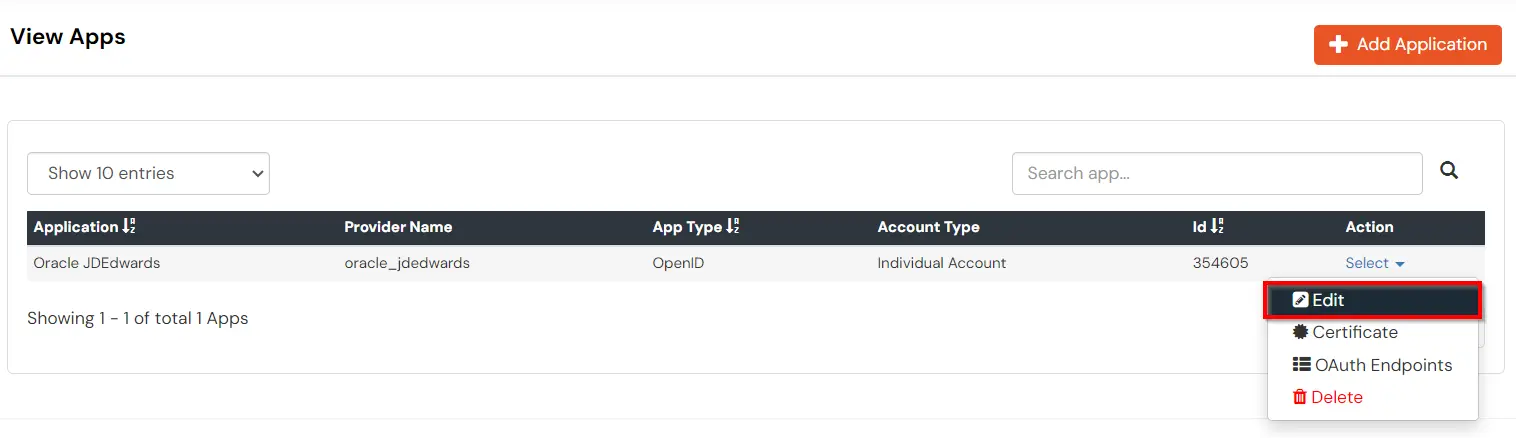
You can edit Application by using the following steps:
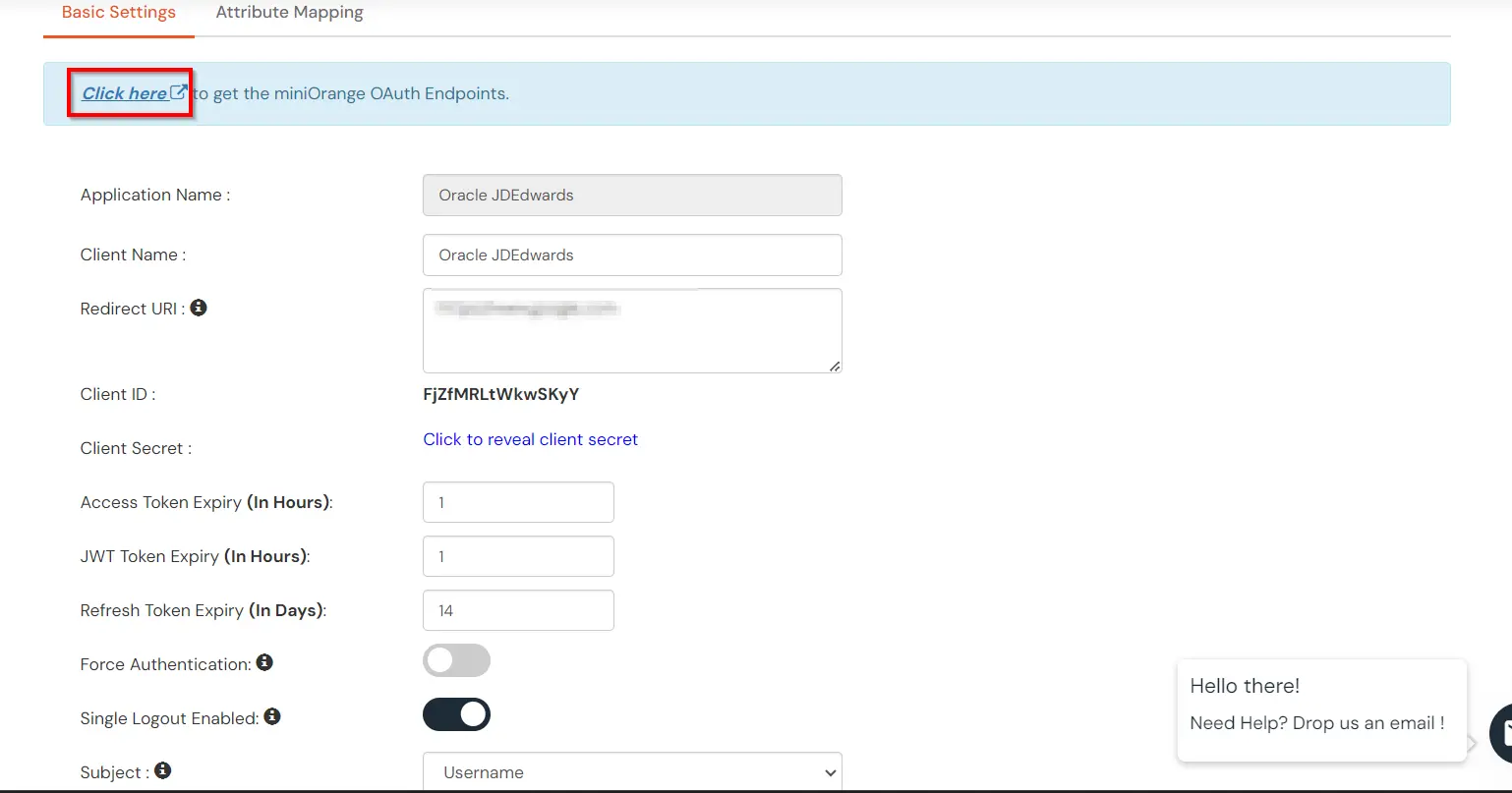
| Authorization Endpoint: | https://login.xecurify.com/moas/idp/openidsso (Note: Use this endpoint only if you want to use miniorange as oauth identity server.) https://login.xecurify.com/moas/broker/login/oauth/260174 (Note: Use this enpoint only if you are configuring any Identity Provider in Identity Providers Menu and not using miniorange as IDP.) |
| Token Endpoint: | https://login.xecurify.com/moas/rest/oauth/token |
| User Info Endpoint: | https://login.xecurify.com/moas/rest/oauth/getuserinfo |
| Introspection Endpoint: | https://login.xecurify.com/moas/rest/oauth/introspect |
| Revoke Endpoint: | https://login.xecurify.com/moas/rest/oauth/revoke |
| OpenID Single Logout Endpoint: | https://login.xecurify.com/moas/idp/oidc/logout?post_logout_redirect_uri=<YOUR-APP-LOGOUT-URL> |
| email: | View email address of the user |
| profile: | View profile attributes of the user account |
| openid: | Retrieve JWT token for OpenID Connect |
# HTTPS server
#
server {
listen 8100 ssl;
server_name localhost;
ssl_certificate "<path-to-ssl-certificate-pem>";
ssl_certificate_key "<path-to-ssl-rsa-key>";
error_page 401 = @error401;
location @error401 {
return 302 https://sso.example.com:8443/auth/sso;
}
# location specifies the context path of jdEdwards relative to the server FQDN
location /<context-path-of-jdEdwards> {
auth_request /auth;
proxy_set_header Host $host;
proxy_pass https://jde.example.com:443/<context-path-of-JdEdwards-app>;
proxy_set_header MO_REMOTE_USER $cookie_MO_REMOTE_USER;
add_header MO_REMOTE_USER $cookie_MO_REMOTE_USER;
}
location / {
proxy_set_header Host $host;
proxy_set_header MO-REMOTE-USER $host;
proxy_pass https://jde.example.com:443/;
}
location /auth {
proxy_pass https://sso.example.com:8443/auth/check;
}
}

Our Other Identity & Access Management Products