Need Help? We are right here!
Search Results:
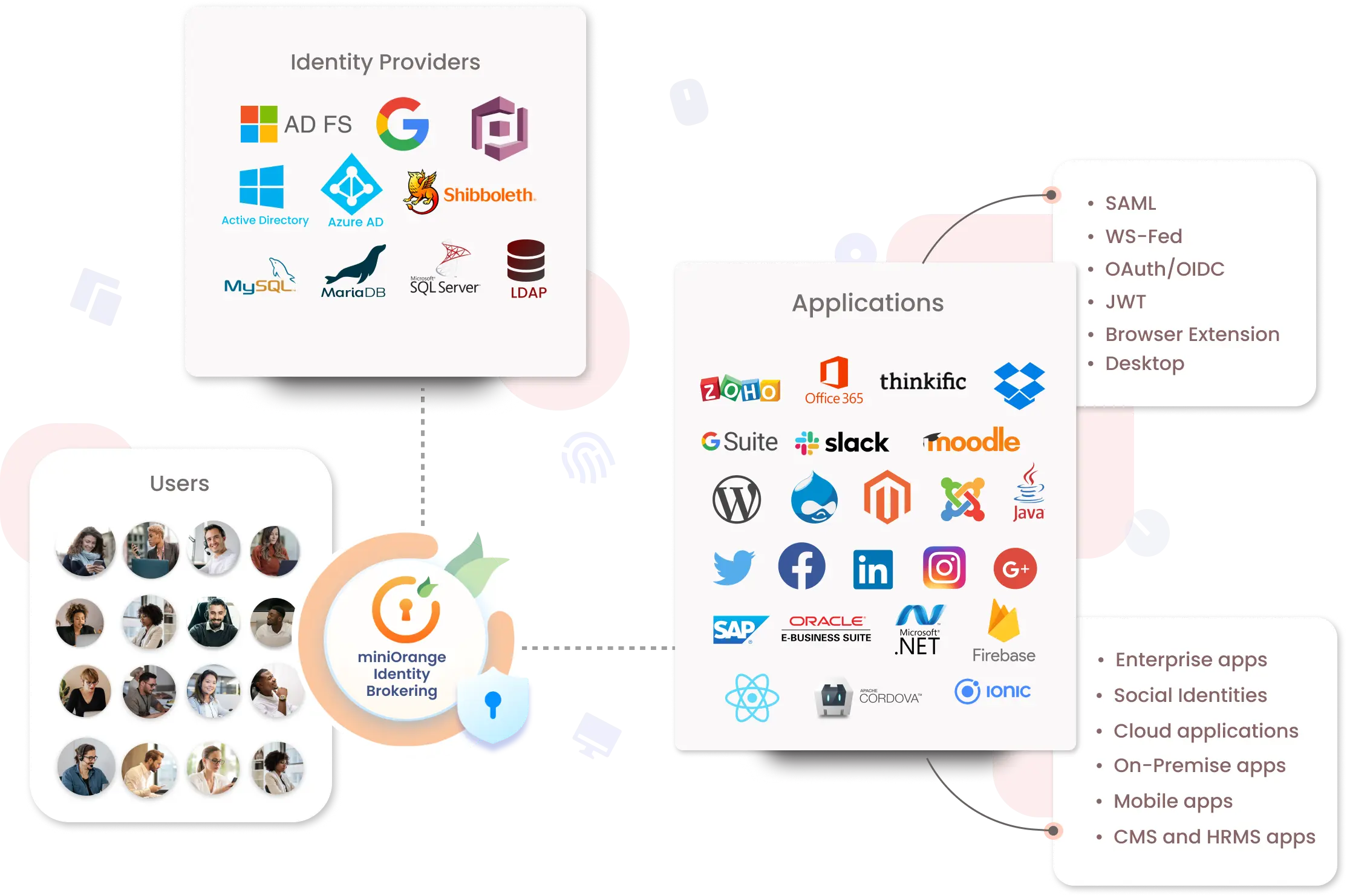
×Identity Brokering is a way to establish trust between parties that want to use online identities of one another. Identity Broker is a service that connects multiple Service Providers(SPs) with different Identity Providers(IdPs). No need to understand or implement complex Single Sign-On (SSO) protocols like SAML, OAuth, OpenID, CAS, etc. The important reason why we should use Identity Broker is that it supports Cross Protocol i.e. configuring a Service Provider following a particular protocol with an Identity Provider following some different protocol. miniOrange Identity Broker service provides secure and easy access to all your services.
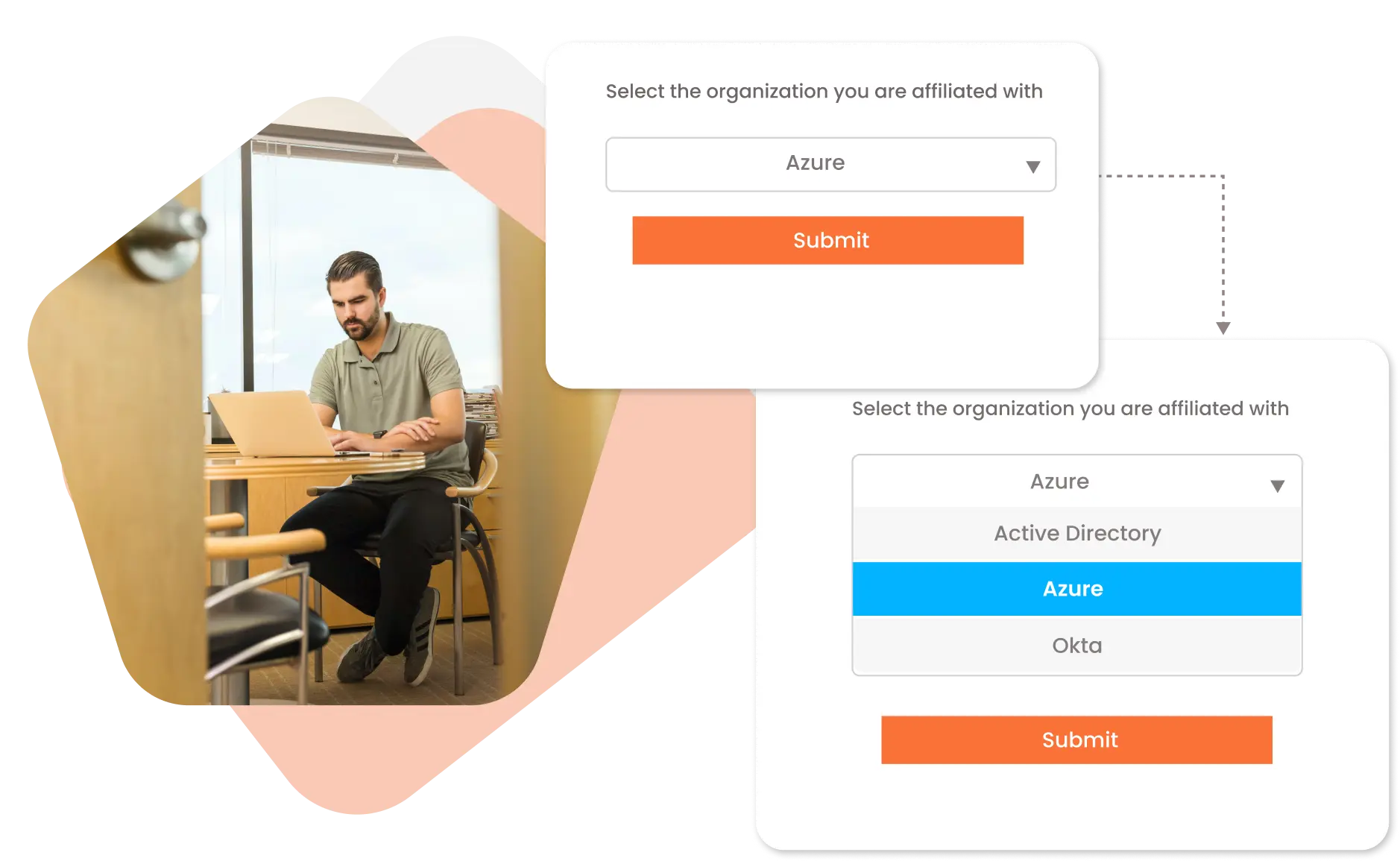
miniOrange provides Login using the IDP selection page feature, where you can configure multiple IDPs (identity providers) and give users the option to select the IDP of their choice to authenticate with for brokering. For Example - It could be multiple AD domains belonging to different departments or multiple Okta organizations. You can also change the look and feel of this page by customizing the title, logo, favicon, background, button color, and many more of the login page.
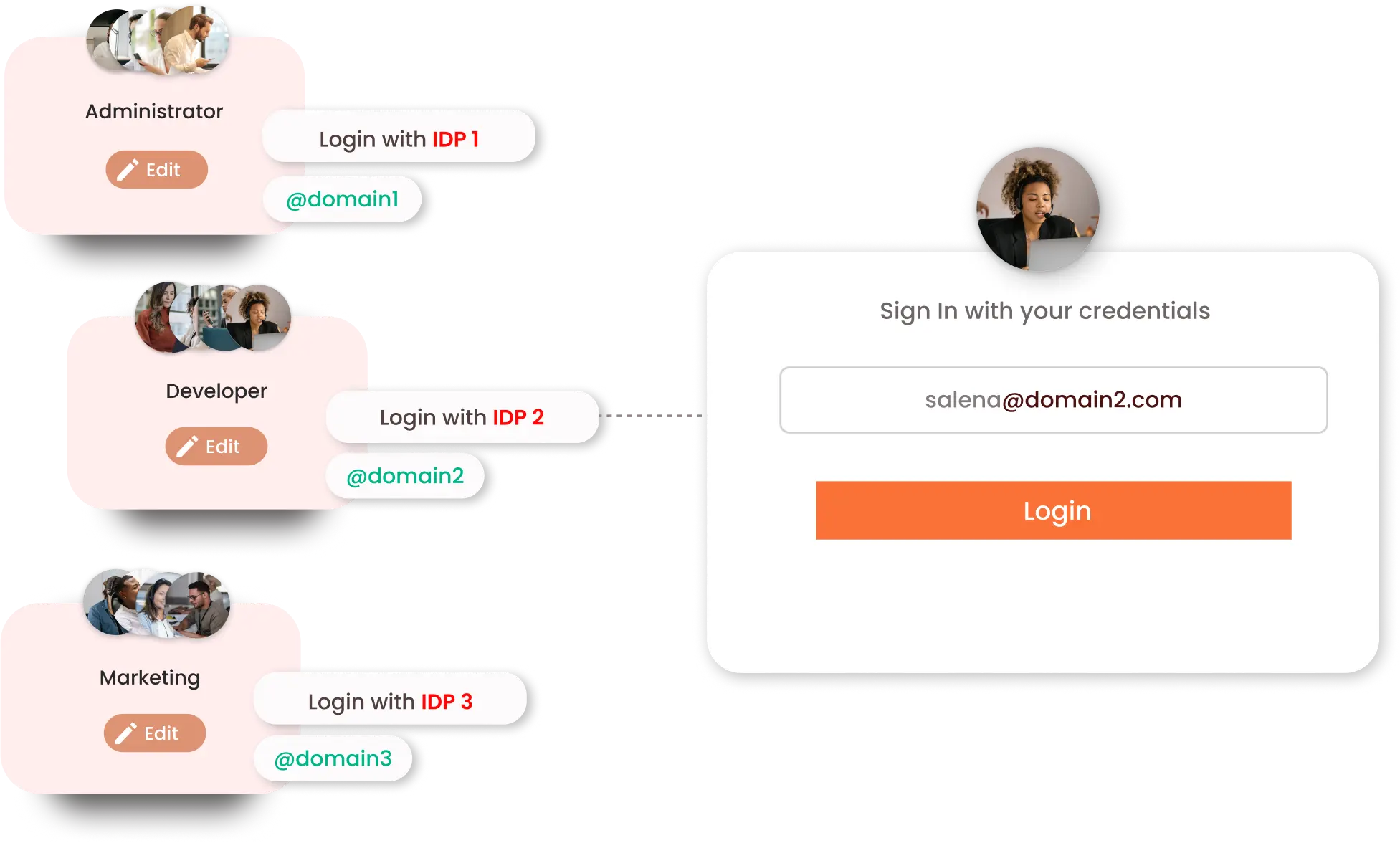
miniOrange Identity Broker Service provides Login via Domain Mapping feature when you have multiple IDPs and you want a certain set of users to authenticate from one IdP whereas another set of users to authenticate from another IdP based on their email domains. In that case, you can achieve this with our Domain Mapping feature. We have provided a Domain Mapping field under each IdP where admins can enter the domain eg. demo.com, example.com as shown in the screenshot. So users logging in with any domain will be redirected to the specific organization for authentication.
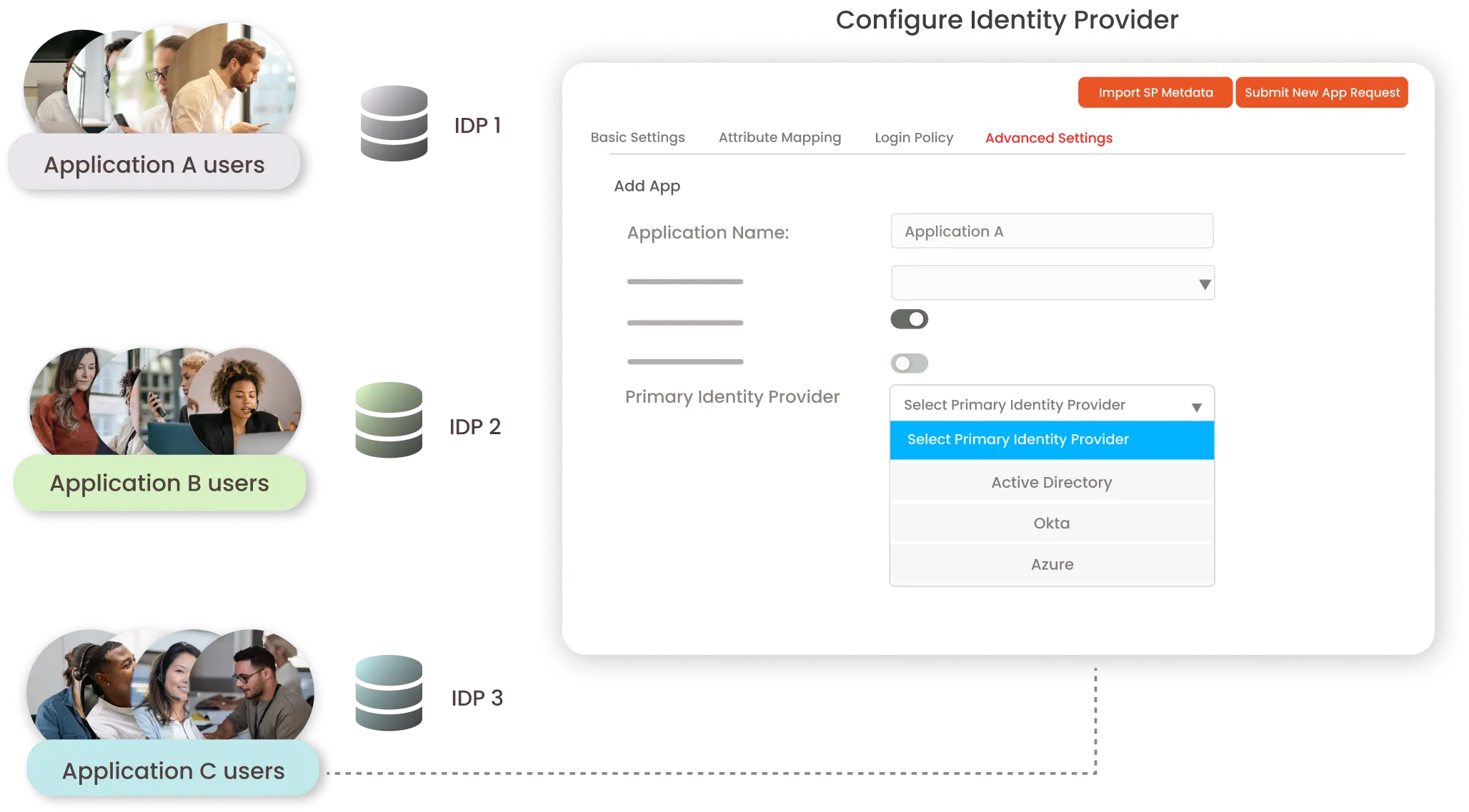
miniOrange provides Login via App Identity Provider Mapping feature when you have multiple IDPs (identity provider) and you want a certain application user to authenticate with one IDP and other application users with another IDP. In that case, you can achieve this by our Identity Source feature. With this feature, you can configure a particular identity source for your selected application. And the users of your selected application would be able to authenticate only by the IDP (Identity Provider) selected from the Identity Source dropdown list.
Identity solutions from miniOrange can be easily deployed in your organization's existing environment.
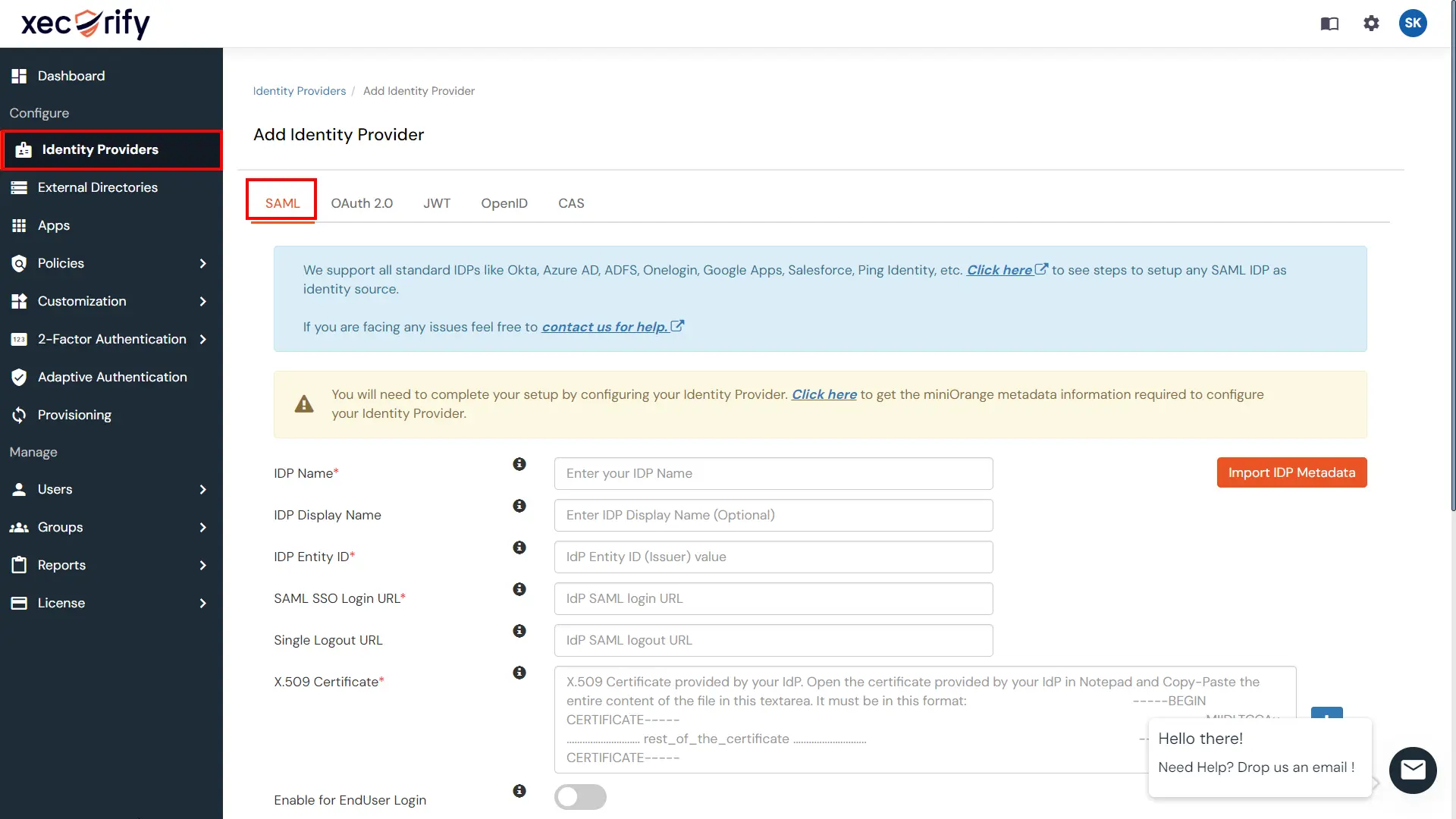
Our SAML Identity Broker Service acts as Service Provider to any Identity Providers of your choice following the same protocol. You can configure any Enterprise SAML IDP like ADFS, Microsoft Entra ID, Shibboleth, Google Apps, Okta, Salesforce, OneLogin, or any other SAML identity provider (IDP).





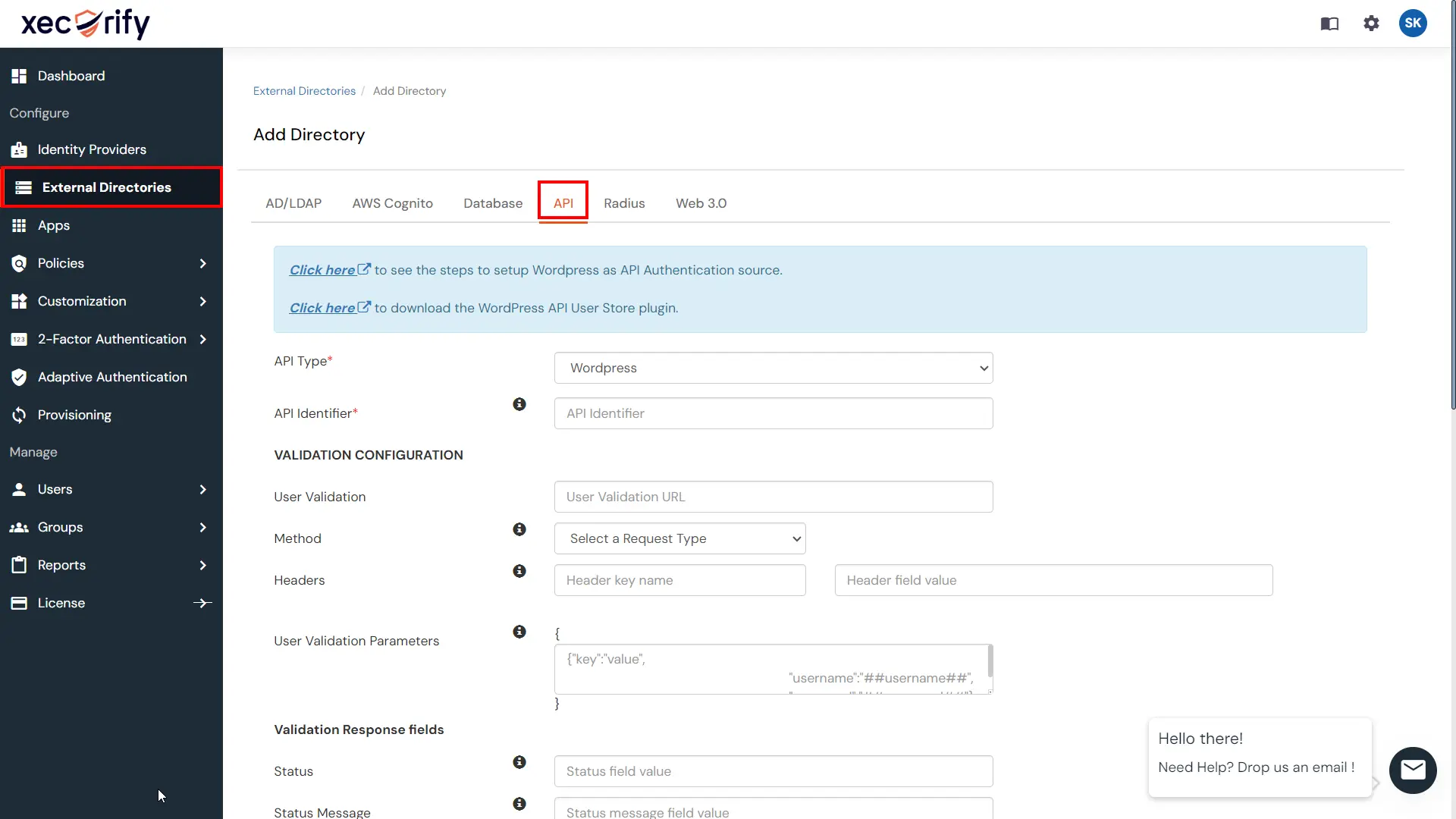
By using our Identity Broker Services you can configure any OAuth Provider like Slack, Discord, AWS Cognito, Microsoft Entra ID, Keycloak, Okta, Salesforce, etc. and provide Authentication to your users.







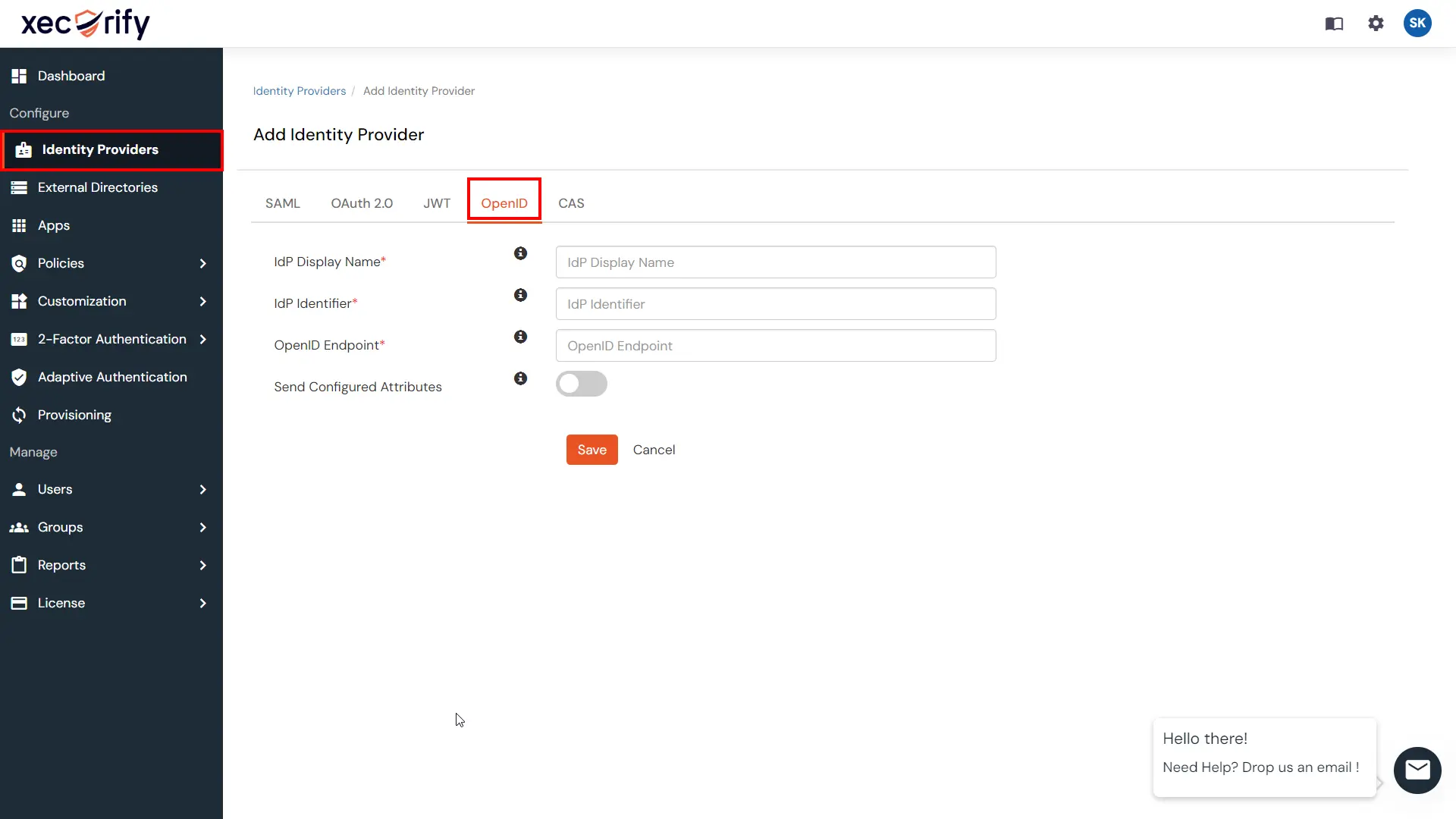
OpenID Connect (OIDC) is simple an authentication layer on top of the OAuth protocol. This OIDC allows clients to verify the identity of an end-user and to obtain their basic profile information. We provide multiple OAuth Provider like Atlassian Crowd, Microsoft Entra ID, AWS Cognito, WHMCS, Ping Federate, Slack, Discord, Keycloak, Okta etc.






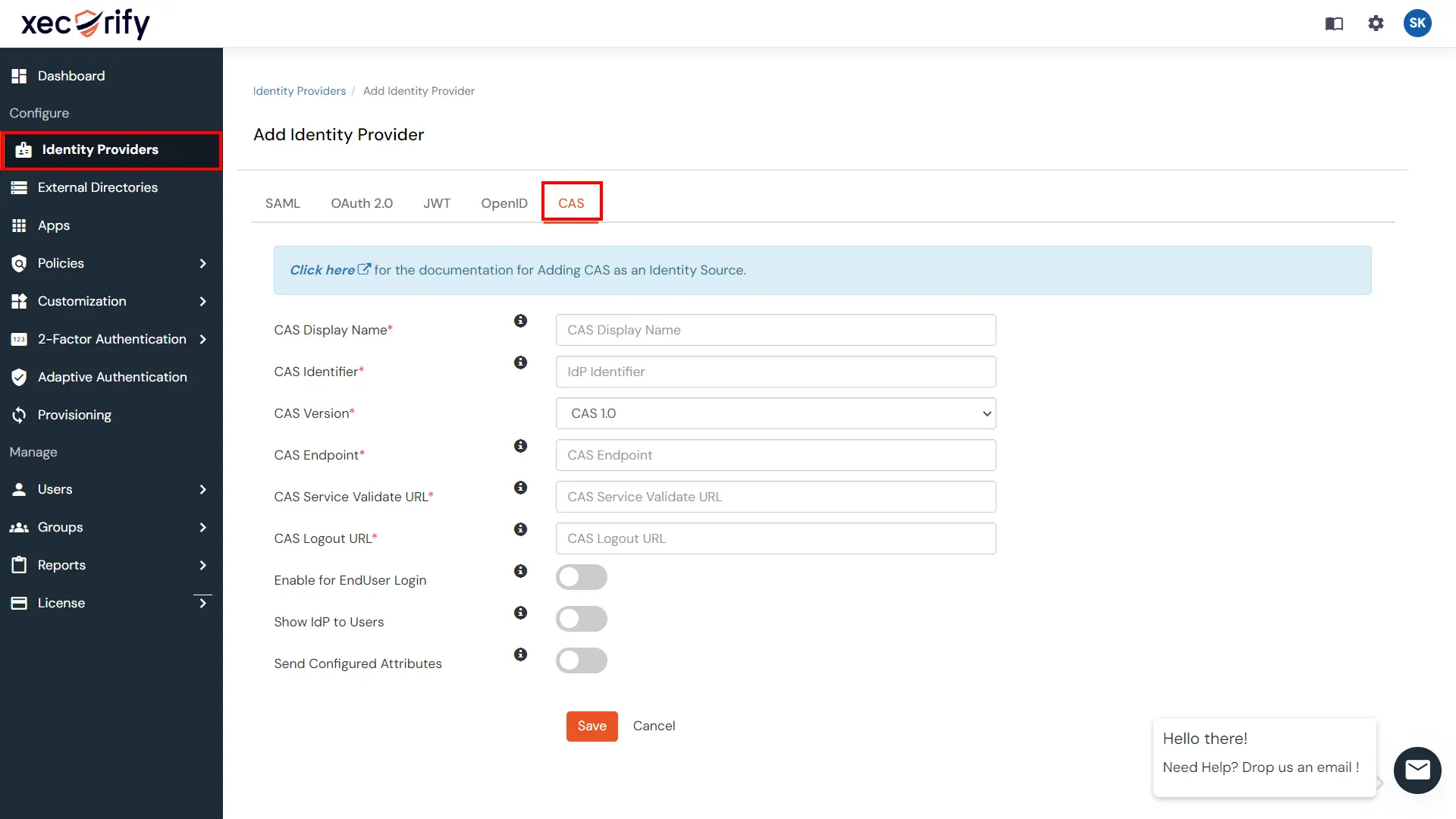
CAS is a ticket-based Single Sign-On (SSO) protocol that provides users access to web applications after authentication against a central CAS Server. By configuring CAS protocol, you permit a user to access multiple applications while providing their credentials (such as user id and password) only once. It also allows web applications to authenticate users without gaining access to a user’s security credentials, such as a password.
By configuring our Identity Broker Service, it will be allow users to authenticate against various LDAP implementations like Microsoft Active Directory, OpenLDAP, and other directory systems and provide a login to any of your applications using credentials stored in your LDAP Server.



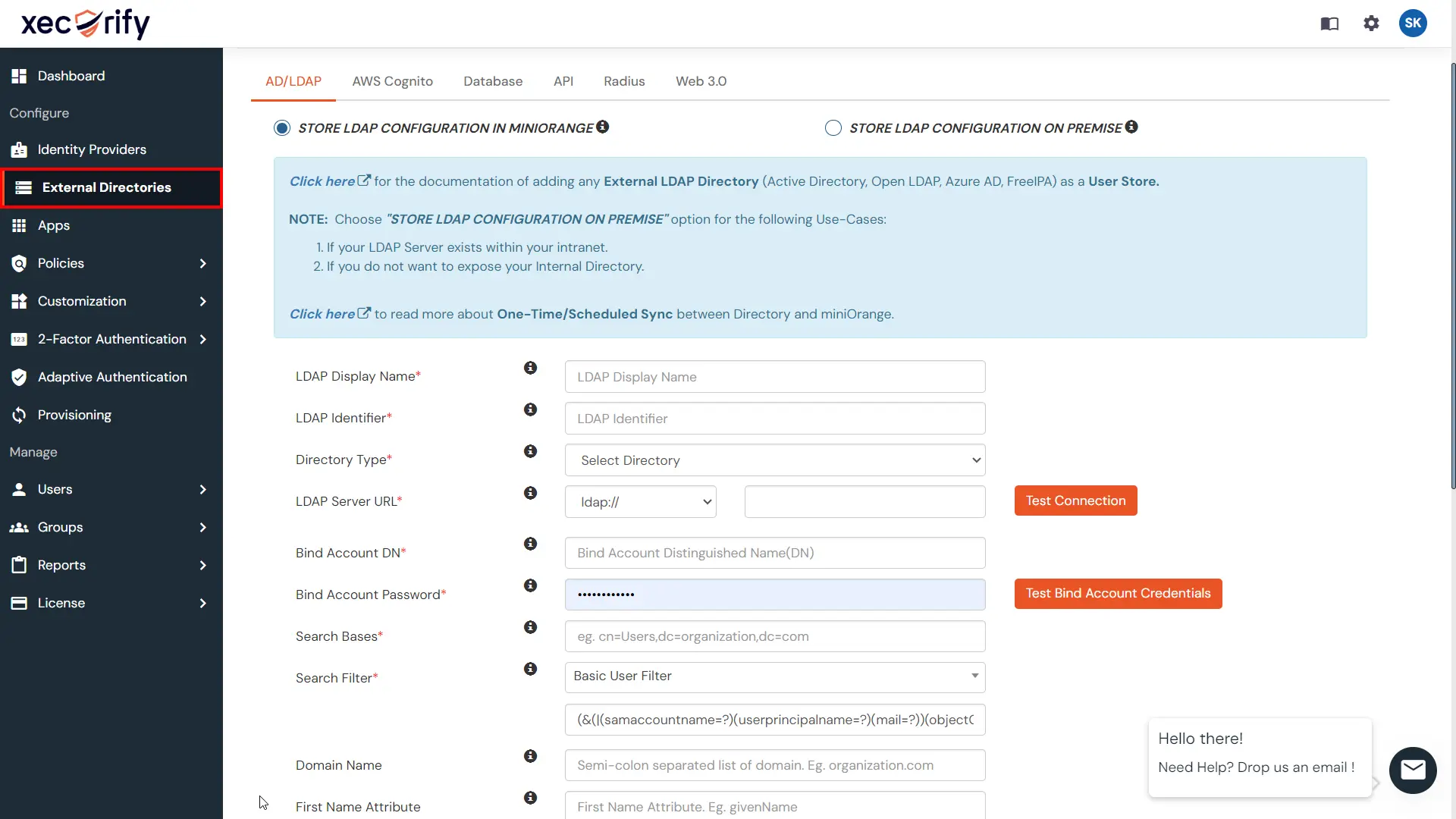
Connect your existing My SQL, Microsoft SQL, Postgres SQL and other databases with miniOrange and allow your users authentication and Single Sign-On (SSO) without moving into miniOrange.




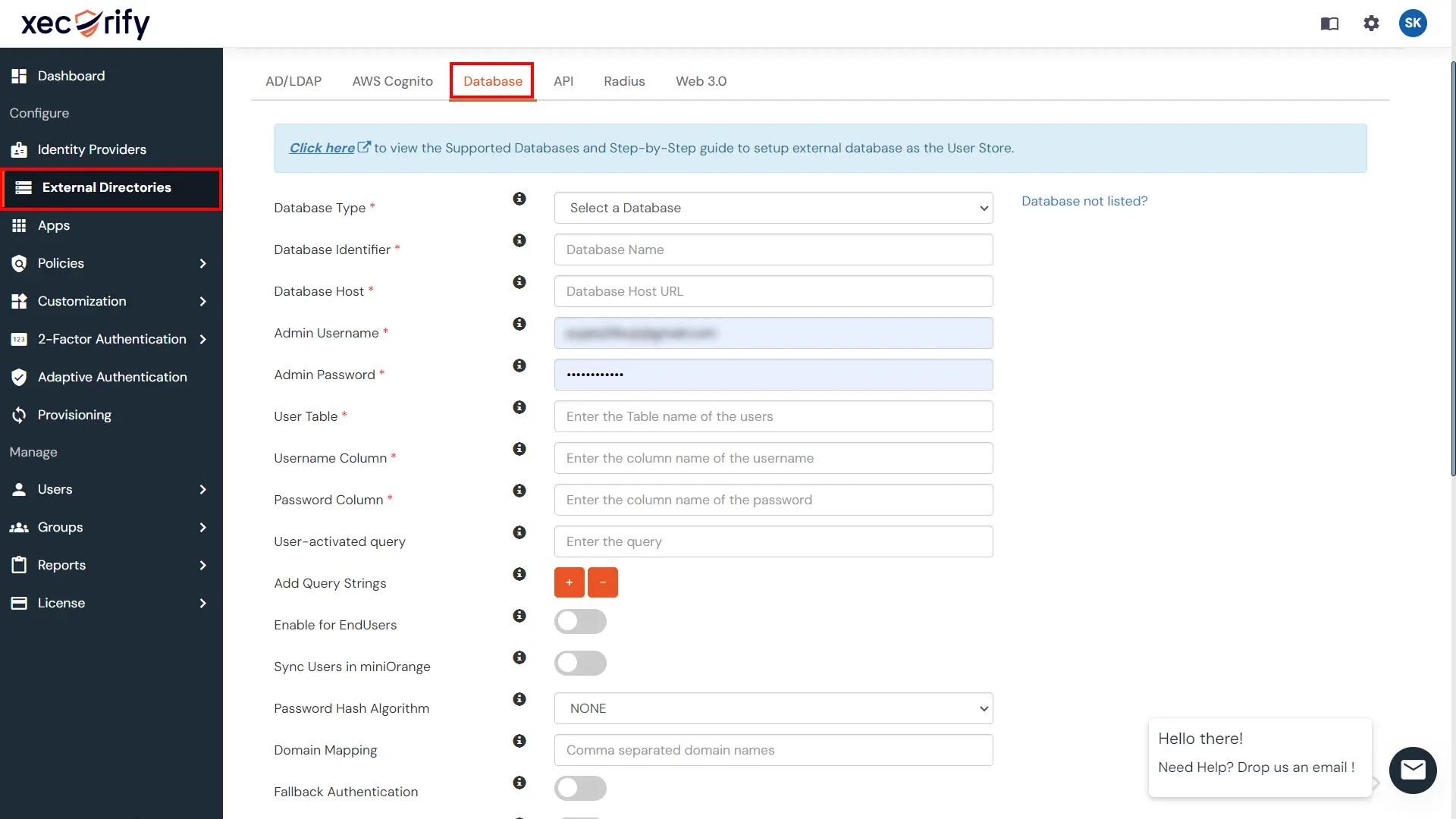
miniOrange provides secure login to any application via any CMS like WordPress, Moodle, Magento, Oracle Siebel CRM and many more and it allows your users to login to multiple applications via using their CMS credentials.




miniOrange provides secure login to any application via any Human Resource Management System like BambooHR, Workday, SuccessFactors, etc and it allows your users to login to multiple applications via using their HRM System credentials.




With IdP Brokering, admins can configure multiple SAML Identity Providers and configure which users/apps authenticate against which Identity Source.
Admins can configure which Identity Source should the users be authenticated from if the authentication request originates from a particular app.
Admins can configure the domains of the users who would authenticate against any SAML, OAuth, etc Identity Provider through Identity Broker Service.
Users can be redirected to a particular Identity Source automatically without prompting the user to choose his/her Identity Source on each login attempt.
Users can get attributes from their IdP and map them to SP user attributes like firstname, lastname with support for custom attributes through miniOrange Broker.
With IdP Brokering, users can start SSO from Service Provider (SP) and are then redirected to the Identity Provider (IDP) for authentication and vice-versa.
per month
upto 500 Users
per user per month
*Please contact us to get volume discounts for higher user tiers.
No need to understand any complex protocols like SAML, OAuth, OpenID as miniOrange seamlessly connects any SP with IDP and provides a simple HTTPS endpoint with IdP Broker.
Saves time by accessing all resources with just one click. Easily integrate with your application which supports SAML, OAuth 2.0, etc.
Pay As You Go subscription model helps you to spend less with a special user tier structure with free 24/7 support.
We provide customization on our products which are platform-independent and they can be easily accessed by an end user.

Identity, Access, and Beyond