Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×miniOrange LDAP Gateway allows login to miniOrange and several other applications using credentials stored in Active Directory, OpenLDAP and other LDAP servers where the LDAP Server is not publicly accessible. The LDAP Gateway is installed in the intranet's DMZ zone. This module also functions as a sync agent, keeping your identity provider in sync with the LDAP Server objects. Furthermore, the Gateway module allows you to configure numerous LDAP Servers, allowing you to specify each unique LDAP Server required for authentication.

| Specifications | miniOrange Gateway Server (minimum requirements) |
|---|---|
| CPU Core | 2 core |
| RAM | 4 GB |
| HDD | 30 GB |
| OS | Windows Server 2008+ or Linux Server |
| Java Environment | Java SE Development Kit v8 (Download Link) |
| Apache Tomcat | Apache Tomcat v8 Windows Service Installer (Download Link) |
You can check the below table to download miniOrange Gateway on your operating system:
| Operating System | Download Link | Checksum(SHA256) |
|---|---|---|
| Zip | Download |
|
| Windows Offline 32 bit | Download |
|
| Windows Offline 64 bit | Download |
|
| Windows Online Installer (32 or 64 bit) | Download |
|

Access the gateway from your browser using the url "<hostname:port>/miniorangegateway". Replace "<hostname>" with your hostname or server IP .
NOTE: This step is mandatory for Chrome Browser. Chrome will not run the Web-Application on HTTP. For all the other browsers this is optional.








Access the gateway from your browser using the url "<hostname:port>/miniorangegateway". Replace "<hostname>" with your hostname or server IP .
Eg:localhost:8080/miniorangegateway.
NOTE: If you have configured another port in Step-2, you can use that custom port instead of 8080. Eg. If you configured Tomcat to run on 8081 then the url will be Eg:localhost:8081/miniorangegateway.

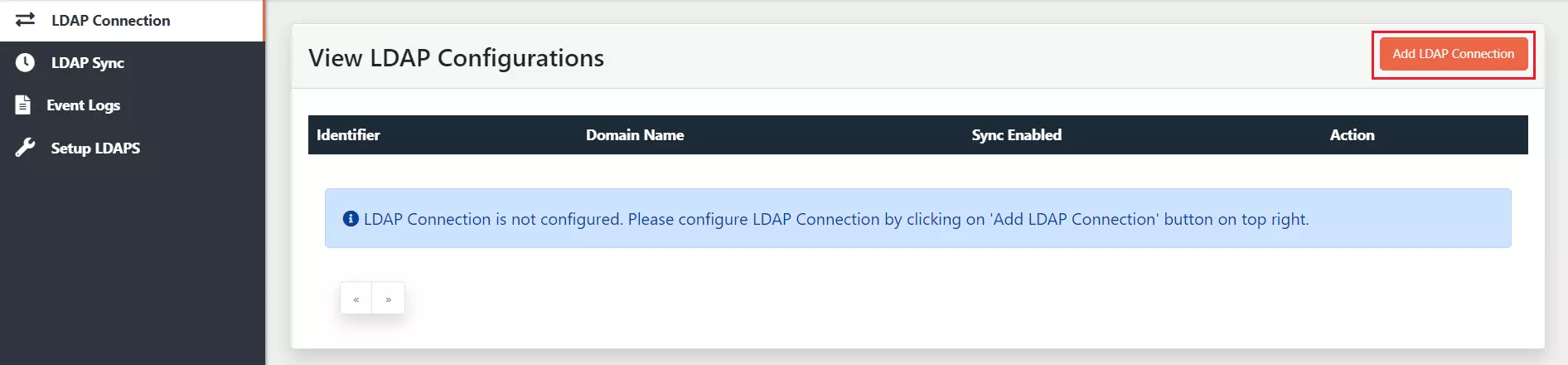

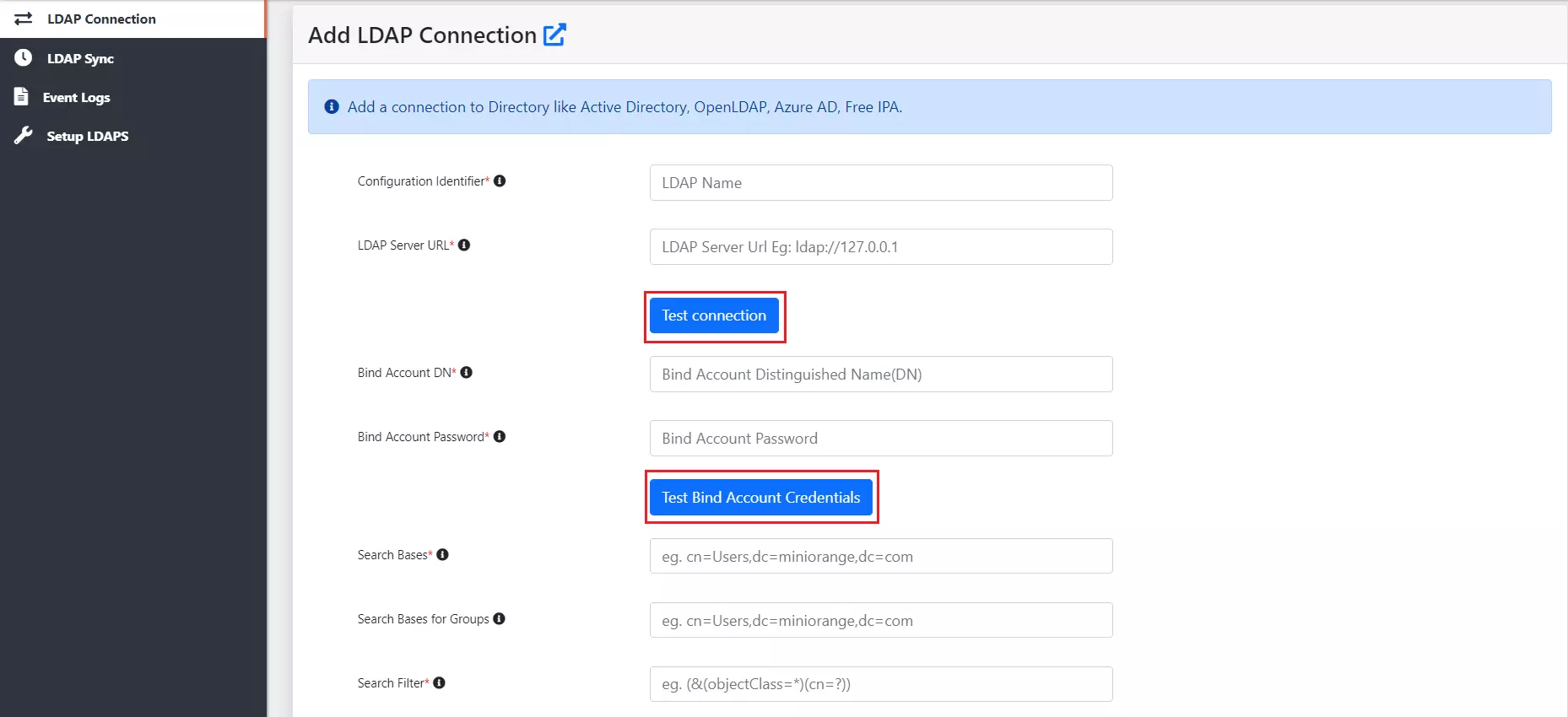
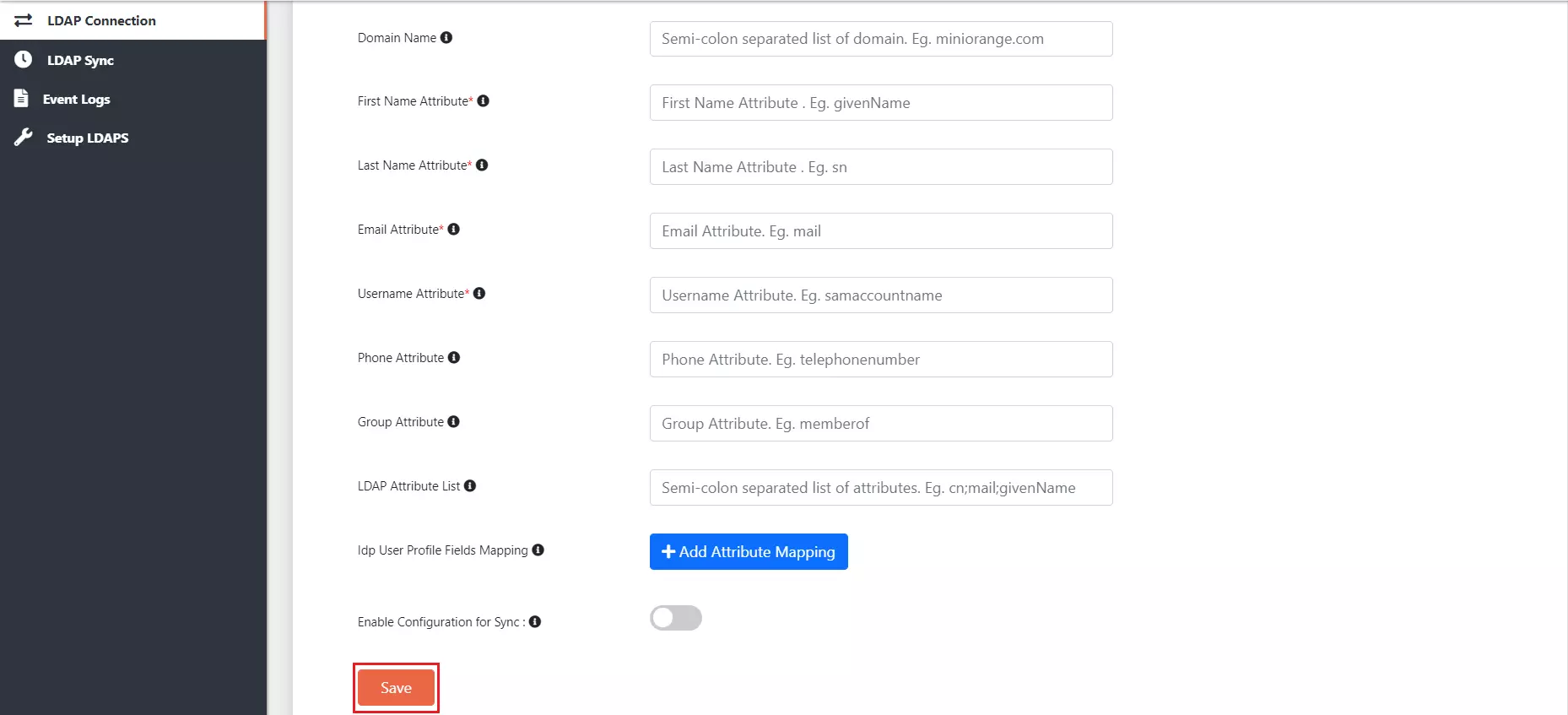
| Field | Description. |
|---|---|
| Configuration Identifier | Any name that will specify this set of configuration. |
| LDAP Server URL | Specify the host name for the LDAP server Eg: ldap://myldapserver.domain:389 |
| Bind Account DN | This will be used to establish the connection with LDAP Server. Specify it in the following ways: Username@domainname or Distinguished Name(DN) format |
| Bind Account Password: | Password for the Bind Account in the LDAP Server |
| Search Bases: | Provide distinguished name of the Search Base object Eg:cn=User,dc=domain,dc=com |
| Search Bases for Groups: | Provide distinguished name of the Search bases objects for your groups Eg:cn=User,dc=domain,dc=com |
| Search Filter: | Search filters enable you to define search criteria and provide more efficient and effective searches. Eg: "(&(objectClass=*)(cn=?))" If you use User in Single Group Filter or User in Multiple Group Filter, replace the <group-dn> in the search filter with the distinguished name of the group in which your users are present. |
| Domain Name: | Semi-colon separated list of domain. Eg: miniorange.com |
| First Name Attribute: | LDAP attribute for the First Name. Eg: givenName |
| Last Name Attribute | LDAP attribute for the Last Name. Eg: sn |
| Email Attribute | LDAP attribute for the First Name. Eg: mail |
| Username Attribute: | LDAP attribute for the First Name. Eg: sAMAccountName |
| Phone Attribute | LDAP attribute for the First Name. Eg: telephoneNumber |
| Group Attribute | LDAP attribute for the Group Name. Eg: memberof |
| LDAP Attribute List | Semi-colon separated list of attributes. Eg: cn;mail;givenName |
| IdP User Profile Fields Mapping | Idp User Profile Fields which will be used during sync |
| Enable Configuration for Sync | This option Enables/Disables the enrollment of the current connection is Scheduler |







NOTE: This step is optional. Follow the below steps if you want to setup user sync between your Directory and the miniOrange Cloud service via LDAP Gateway. We support both, scheduled sync as well as One Time Sync.
Eg. If the server time is 13:00 then anytime before 13:00 should initiate immediate sync.
| Field | Description. |
|---|---|
| Enable Group Sync | Enable/Disable group sync. |
| Enable User Sync | Enable/Disable user sync |
| Enable User Group Membership Sync | Enable/Disable user group membership sync |
| Enable Delete User Sync | Enable/Disable to delete user sync. |
| Configure Exclusion List | Click on Select Users to select Users who are excluded from being deleted. |
| Mark User as Registered in miniOrange | Enable/Disable marking user as registered in miniOrange. |
| Start Time(hh:mm) | Start time for the schedule sync Eg: 01 in hours and 01 in minutes. |
| Sync Interval (in hrs) | Time Interval between periodic sync. |




NOTE: Make sure that the Tomcat is running with the Admin Privileges.
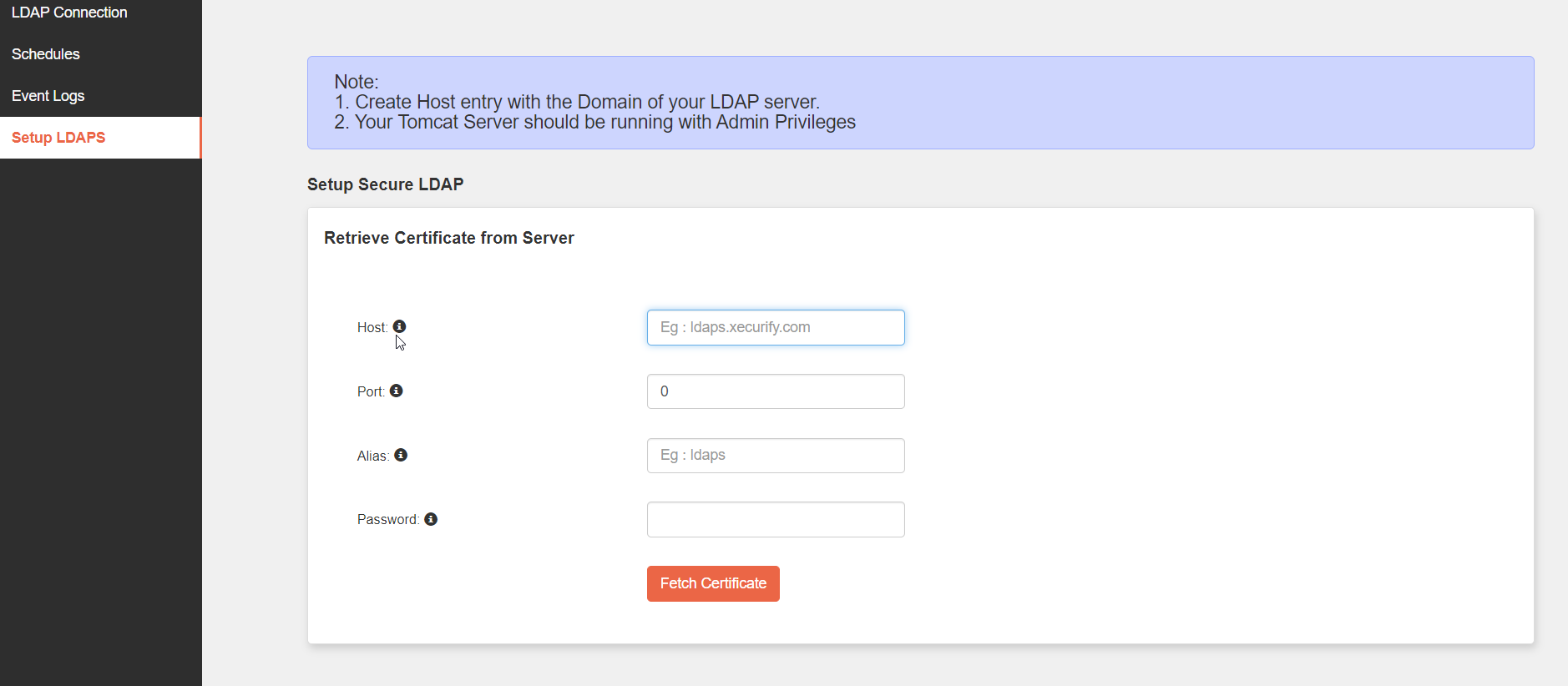

sudo vi /etc/systemd/system/tomcat.service
# Systemd unit file for tomcat
[Unit]
Description=Apache Tomcat Web Application Container
After=syslog.target network.target
[Service]
Type=forking
Environment=JAVA_HOME= <Location of your JRE> Eg: /usr/lib/jvm/jre
Environment=CATALINA_PID=<Location of your PID file> Eg:/opt/miniorangegateway-1.x.x/temp/tomcat.pid
Environment=CATALINA_HOME=<Location of your miniOrange Tomcat Directory> Eg: /opt/miniorangegateway-1.x.x
Environment=CATALINA_BASE=<Location of your miniOrange Tomcat Directory> Eg: /opt/miniorangegateway-1.x.x
Environment='CATALINA_OPTS=-Xms512M -Xmx1024M -server -XX:+UseParallelGC'
Environment='JAVA_OPTS=-Djava.awt.headless=true -Djava.security.egd=file:/dev/./urandom'
ExecStart=/opt/tomcat/bin/startup.sh
ExecStop=/bin/kill -15 $MAINPID
User=tomcat
Group=tomcat
UMask=0007
RestartSec=10
Restart=always
[Install]
WantedBy=multi-user.target
sudo systemctl daemon-reloadsudo systemctl start tomcatsudo systemctl status tomcatsudo systemctl enable tomcat

Our Other Identity & Access Management Products