Need Help? We are right here!
Search Results:
×Auditing Privileged Access Management (PAM) ensures that all privileged users comply with your organization's security policies. It involves tracking and monitoring privileged accounts, assessing access levels, and analyzing user activity. By auditing PAM, you can identify potential security gaps, prevent unauthorized access, and enhance your organization’s cybersecurity posture.
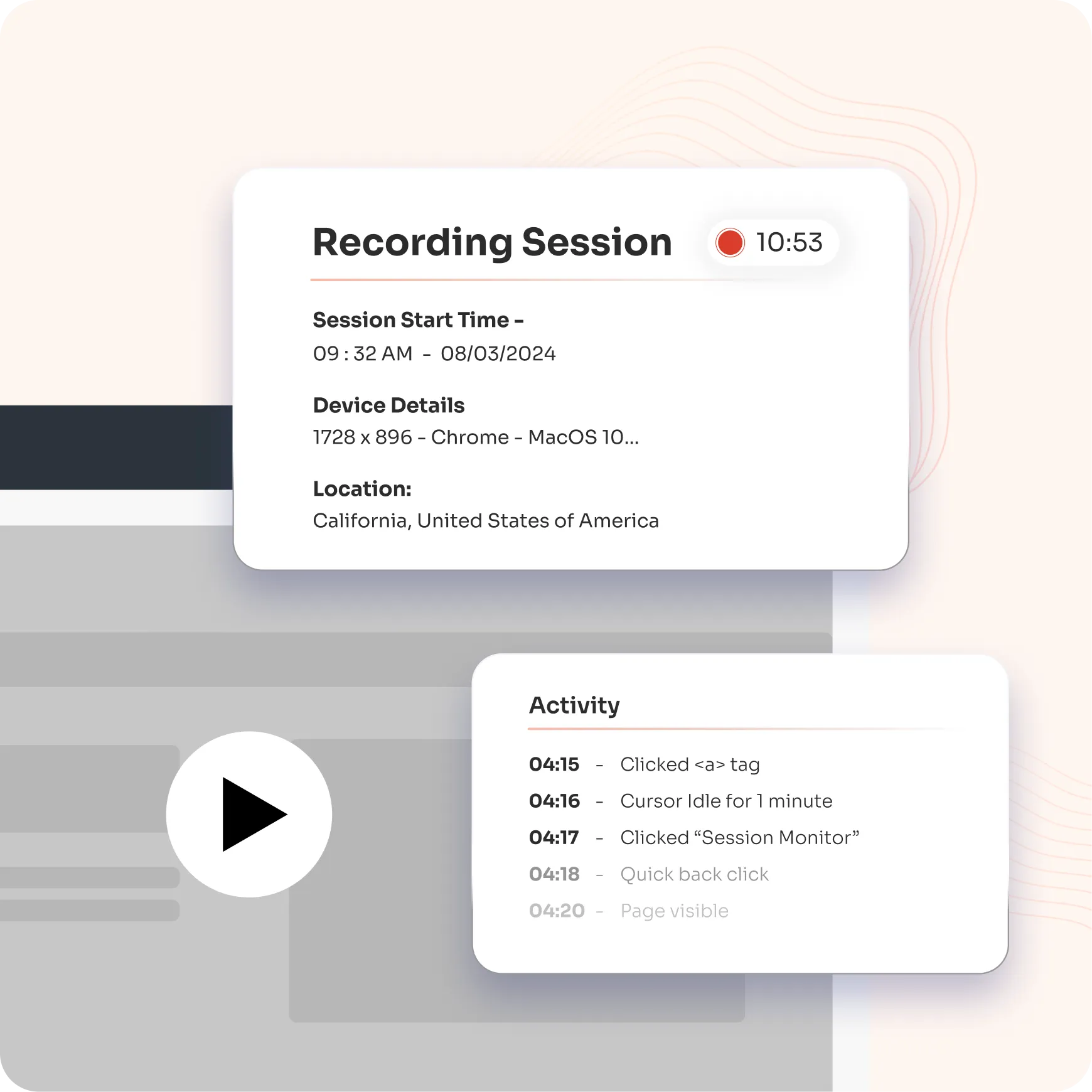
Audit Trails, a vital component of Privileged Access Management (PAM), provide detailed logs of privileged user and session activities, ensuring adherence to security policies. By capturing session details such as event specifics, IP addresses, user actions, and timestamps, they help identify suspicious behavior and operational issues. Real-time monitoring and automated logs empower administrators to detect and address potential threats promptly, reinforcing a secure and compliant environment







Regularly reviews user access rights to ensure that privileges are aligned with current job roles and responsibilities through Role-Based Access Control (RBAC). This policy helps maintain security by assigning appropriate permissions based on user roles.
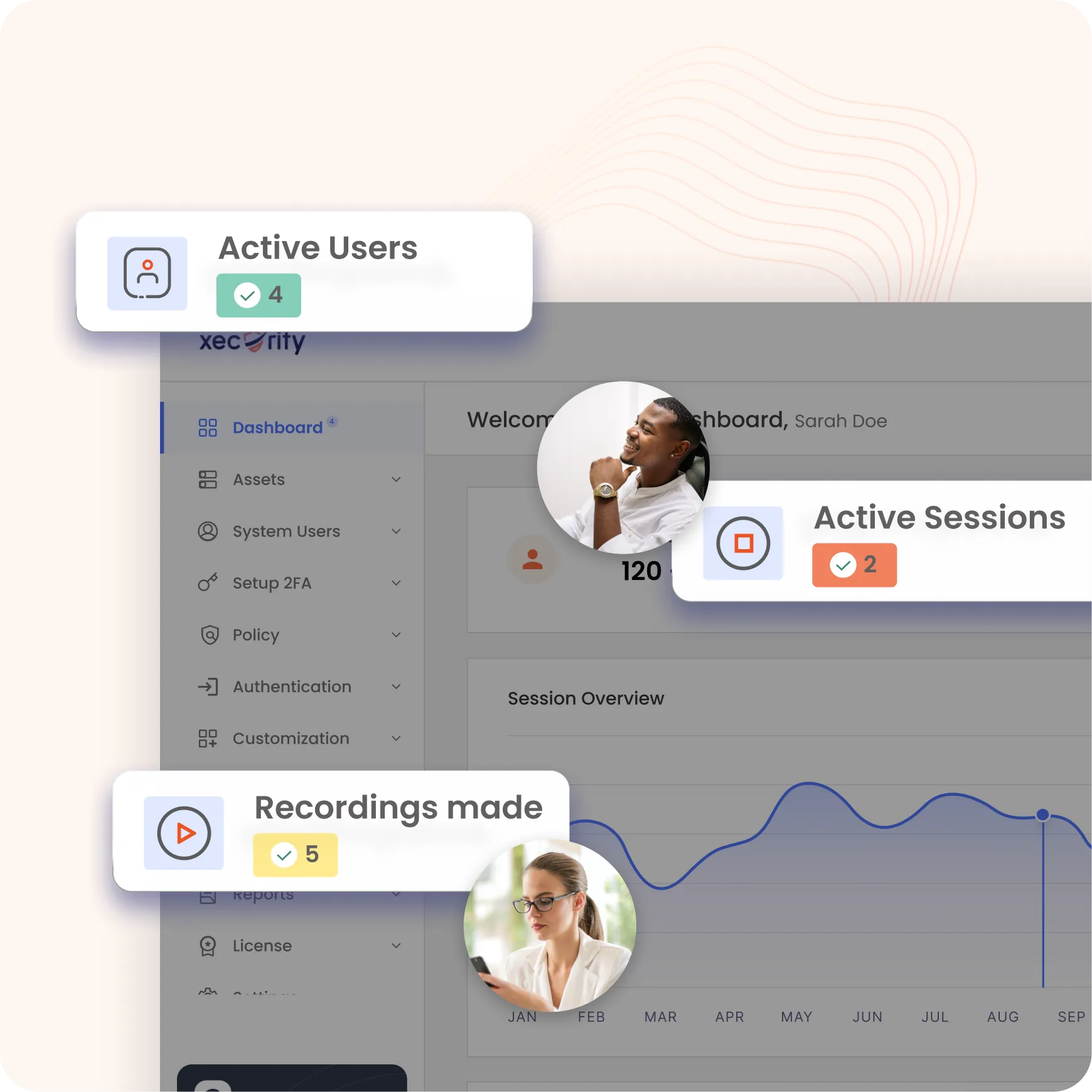
Monitor and record privileged sessions to detect unauthorized activities and ensure adherence to security policies.
Establish and maintain strong password management policies to ensure they are consistently followed across the organization.
It simplifies the process of requesting and approving privileged access to improve security and accountability.
Ensure that Privileged Access Management (PAM) practices are in line with relevant compliance standards and regulations.
Gain constant visibility into all privileged operations with a real-time dashboard that offers a comprehensive view of administrator activities. This feature ensures enhanced oversight and security, helping administrators monitor and manage privileged access effectively.
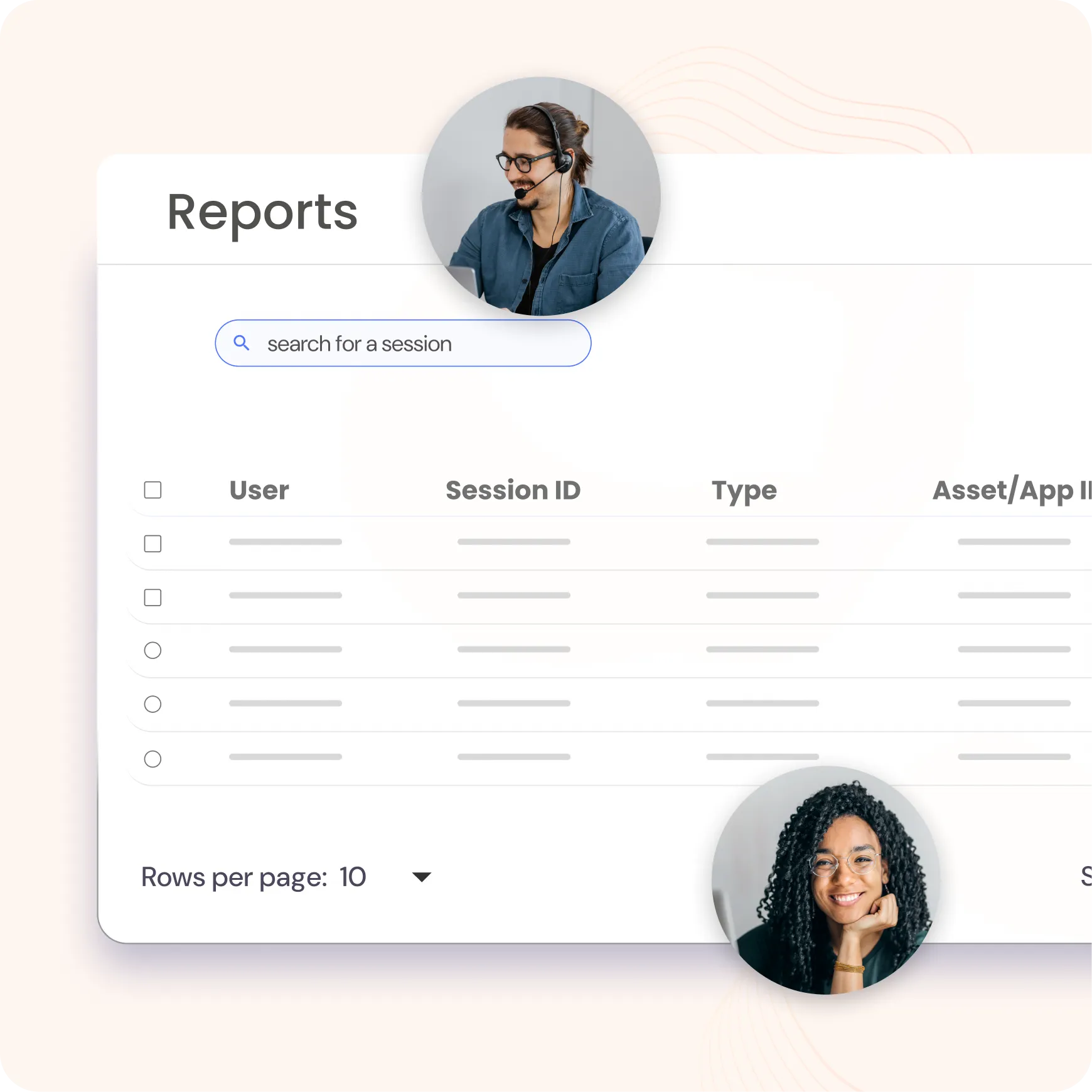
Customize your reporting process with flexible options to generate reports on user-defined schedules, on-demand, or at regular intervals. Access detailed and scheduled reports across key categories, including:
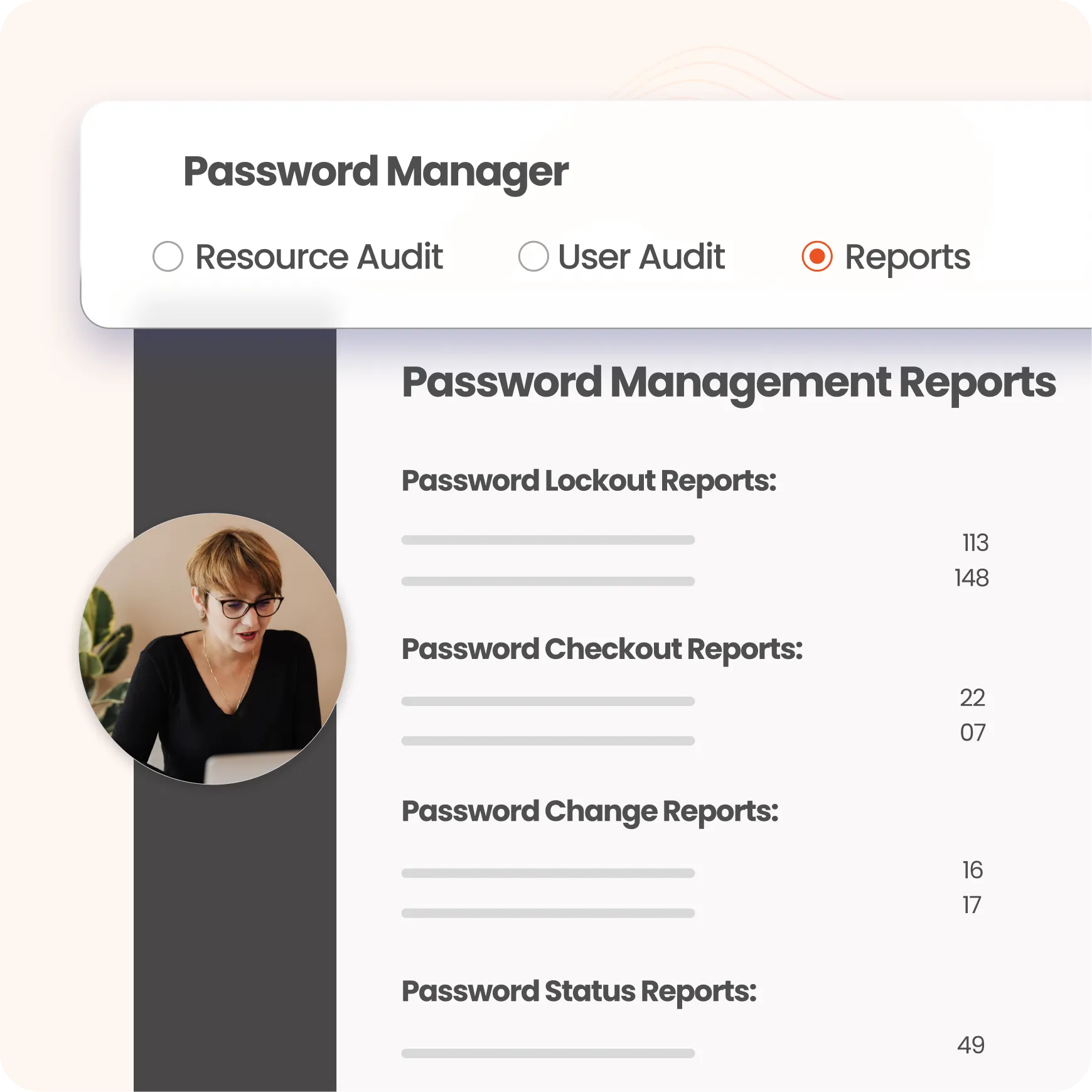
Enhance security with comprehensive password management reports, including:
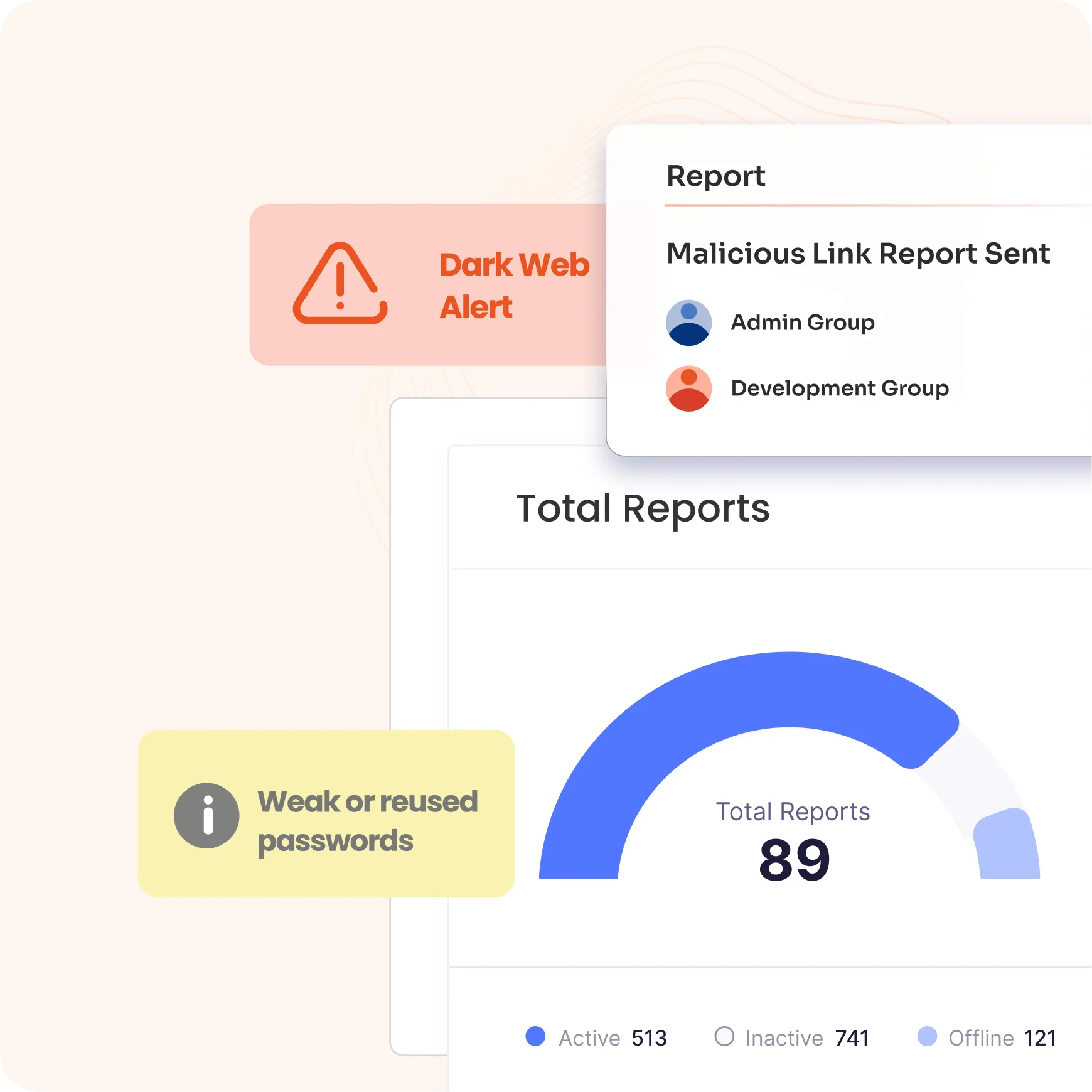
Leverage advanced analytics to monitor session activities and assign a risk score to each session and user task. Integrated with SIEM, this feature helps prioritize auditing efforts by identifying potentially risky behavior in real-time, enabling faster response to threats and enhanced security management.
Enable forensic investigations with session recording and replay capabilities while generating tailored reports. Built-in threat analytics enhance the detection of suspicious activities within privileged sessions, ensuring comprehensive security oversight and response.
Ensure only authorized users access critical assets, reducing data breach risks.
Identify potential vulnerabilities and weak practices to mitigate insider threats.
Align PAM practices with industry regulations to meet compliance requirements and avoid penalties.
Auditing access management involves a systematic process to ensure that access rights are properly assigned and managed. Here’s an overview of the steps typically involved:

Our Other Identity & Access Management Products