Need Help? We are right here!
Search Results:
×miniOrange Authentication Service verifies that you are who you say you are before letting you move forward. We ensure that however varied your user base may be, we have the right authentication method for each one of them.
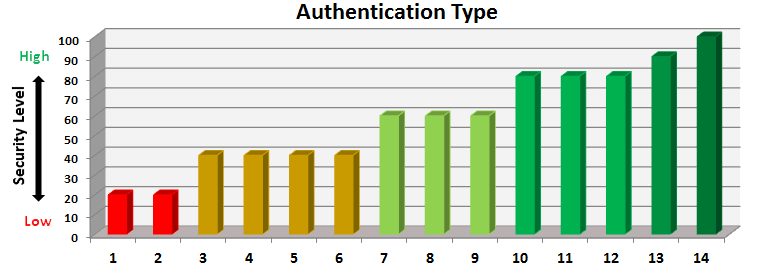
| X-Axis | Authentication Type | Description of Security Level |
|---|---|---|
| 1 | Password | Can be guessed by fraudsters. Susceptible to brute force attacks. |
| 2 | Security questions | |
| 3 | OTP over SMS | Verifies that you have your mobile device but susceptible to Man-In-The-Middle attacks. |
| 4 | Soft Token | |
| 5 | Hardware Token | Verifies that you have your Hardware Token but susceptible to Man-In-The-Middle attacks. |
| 6 | Biometric | Verifies who you are but susceptible to Man-In-The-Middle attacks. |
| 7 | Out-of-Band(Mobile) | NO Man-In-The-Middle attacks are possible because verification happens through a separate channel but spoofing is easy by creating a duplicate SIM or acquiring the credentials related to Push Notifications. |
| 8 | Push Notifications(Mobile) | |
| 9 | Device Authenticaion(Mobile) | NO Man-In-The-Middle attacks are possible and Spoofing is much more difficult. |
| 10 | Biometric+Mobile | Verifies who you are and what you have. |
| 11 | Password+Mobile | Verifies what you know and what you have. |
| 12 | Password+Biometric | Verifies what you know and who you are. |
| 13 | Password+Biometric+Mobile | Verifies what you know, who you are and what you have. |
| 14 | Risk Based Access | Verifies what you have, where you are, what time you are accessing the resources that you need and is your behavior different from what you have done in the past. |
We have expertise over a large number of authentication methods including the following :

The most commonly used form of authentication today is password based wherein a user is prompted to enter his userid and password and based on that he is granted access to resources. Although the most commonly used one, it has a number of issues - they are difficult to remember so a user generally has the same password for multiple accounts, they can easily be stolen and if your account is compromised you may not get to know until its too late.
OTP over SMS - A six to eight digit one time passcode is sent to your registered phone number through SMS and you are required to enter it when prompted. This number is valid for one minute only. This is supported for all types of phones.
OTP over EMAIL - A six to eight digit one time passcode is sent to your registered email id and you are required to enter it when prompted. This number is valid for one minute only.
Out of Band Authentication using SMS - This is supported for all types of phones. When this option is configured for you, at the time of authentication, you will be sent an SMS with an Accept Link and a Deny Link. If you click on the Accept link then your transaction will proceed otherwise not.
Out of Band Authentication using Email - When this option is configured for you, at the time of authentication, you will be sent an Email with an Accept Link and a Deny Link. If you click on the Accept link then your transaction will proceed otherwise not.
Soft Token is supported only for smart phone users. To use this you need to download and configure miniOrange Authenticator app from the Google Play store or Apple App store. Once you have this app configured on your smart phone, you can go to the soft token screen and see a six digit code that is visible and changes every minute. When prompted, you should enter this number to allow your transaction to proceed.
To enable this authentication method, you need to purchase and carry an additional token. When prompted on the screen, you need to plugin the token to the USB of your computer and press the only button thats on the token. While doing this, the cursor should be in the text box that is meant to enter the one time passcode. You will see that by pressing the button on the token (while its connected in the USB), the text box will automatically get filled with a large number. This is your one time passcode and you will be able to use this to make your transaction successful.
This is supported only for smart phone users. To use this you need to download and configure miniOrange Authenticator app from the Google Play store or Apple App store. Once you have this app configured on your smart phone, every time you do a transction, you will receive an 'Allow' or 'Deny' message on your phone and your transaction goes forward only if you 'Allow' it.
In this authentication method, you pre-configure a set of life questions with answers that no one else knows but you. When prompted on the screen, you enter the answers exactly how you entered them while configuring.
This is supported only for smart phone users. To use this you need to download and configure miniOrange Authenticator app from the Google Play store or Apple App store. Once you have this app configured on your smart phone, when prompted you should open the app and click on the 'Authenticate' button. It opens a scanning screen. Scan the encrypted QR code on the screen to make your transaction proceed further.
This is supported only for smart phone users. To use this you need to download and configure miniOrange Authenticator app from the Google Play store or Apple App store. Once you have this app configured on your smart phone, when performing your transaction on your laptop, you will be notified on your smart phone that this transaction needs additional authentication to move forward and you need to authenticate your voice. Press any part of your smart phone screen to indicate you understand this, and you will be prompted to enter either a series of digits or phrases, depending on how you have configured it earlier. You may be prompted for this more than once because of background noise etc while the program tries to determine your voice print. If your voice print matches the one on record, your transaction goes through.
The certificate-based authentication is based on the premise that you and only you have access to the secret information that is associated with your certificate. The web site never sees your secret information so your identity is secure (unlike password authentication). Unlike passwords, certificates are too big to remember and the mathematical operations to prove that you are in possession of the associated secret information is too involved to perform manually. Therefore, certificate-base authentication must be performed by a computer. Fortunately all popular browsers handle certificates and the associated math. The certificate and secret information are usually held on the computer's hard drive, but can also be stored on a smart card (a portable device the size of a credit card) or on a USB token (a portable device that plugs into a USB port). When a web site asks for user authentication, the browser accesses the certificate and secret information and performs the authentication on behalf of the user. The browser can be configured to automatically authenticate the user, so the user is not aware that the authentication took place.
miniOrange provides 24/7 support for all the Secure Identity Solutions. We ensure high quality support to meet your satisfaction.
Try Nowminiorange provides most affordable Secure Identity Solutions for all type of use cases and offers different packages based on customer's requirement.
Request A QuoteWe offer Secure Identity Solutions for Single Sign-On, Two Factor Authentication, Adaptive MFA, Provisioning, and much more. Please contact us at -
+1 978 658 9387 (US) , +91 97178 45846 (India) | info@xecurify.com