Need Help? We are right here!
Search Results:
×IP restriction is a security feature that allows company admins to give selective access to websites and web applications, depending on the user's IP address, and whether it is whitelisted or blacklisted from accessing that domain. This setting adds an extra layer of security by allowing an administrator to limit the IP addresses by specifying which systems should be allowed or restricted from accessing and making requests to the origin server and hence minimizing unwanted traffic. There are numerous requests submitted to web servers on a regular basis, and there are numerous reasons to maintain web services secure. We can handle these requests that come to the server with IP address restrictions. IP restriction monitors network traffic and, if it suspects a request coming from a specific IP address is suspicious, it will either limit the IP address from accessing your backend server or notify you to limit IP address access to a domain.
IP restriction protects access to your web domain from unauthorized or blacklisted IPs from ever accessing your site to improve security.
You can control and utilize the number of IPs or ranges of IPs you want to restrict from accessing your domain to provide a flexible security solution.
IP restriction helps you manage the network traffic by allowing only the whitelisted IP addresses from sending requests to your backend server. This is highly useful for eCommerce sites enabling IP restriction.
All IP restriction addresses are synchronized so that the authorization is highly accurate and Security is enhanced for your business security.
IP restriction solution is easier to implement and install for your domain to whitelist IPs or blacklist IPs easily.
IP restriction will help to quickly transmit access to people who are allowed to access the site to only allow whitelisted IPs to reach your domain.
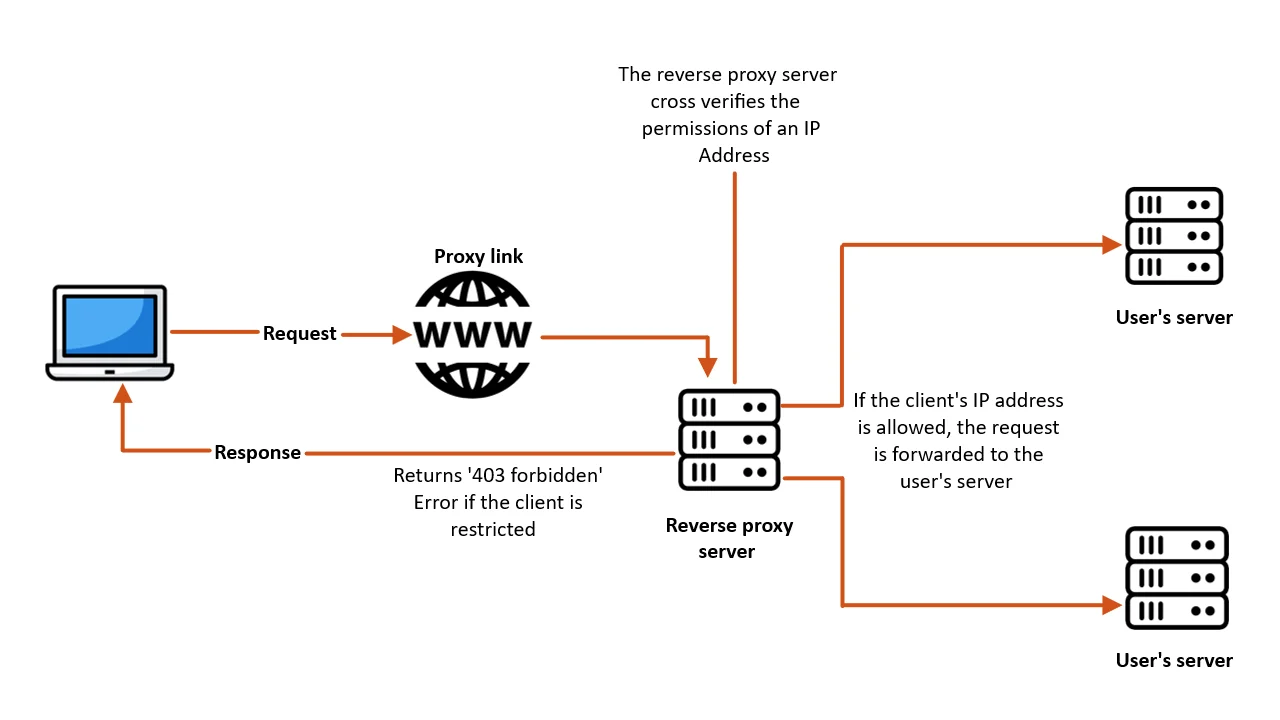
IP restriction only allows the whitelisted IPs to access and log in to a site by preventing access from unauthorized users. If a user attempts to access the site from a blacklisted IP or an unknown IP address, that user won’t be granted access and will be shown a 403 Forbidden response, to safeguard the integrity of the target site.
Let’s see, how this IP restriction would work in a scenario where a client of the user, who has enabled the IP restrictions with a reverse proxy feature wants to access the user’s server:
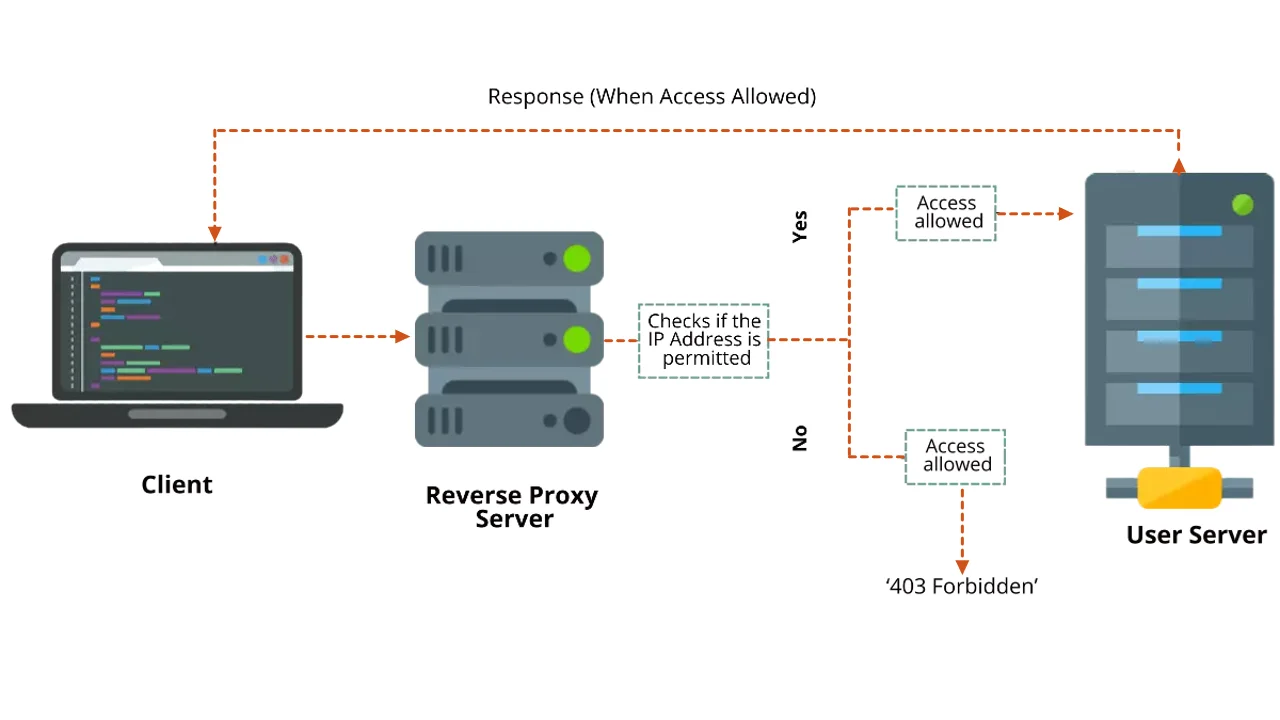
Let's take an example to understand the IP restriction feature better. Suppose an admin wants to restrict users from accessing his company's internal web applications from foreign requests. The admin can restrict access to these apps by enabling IP restriction. This way the admin can limit access to the web app by only allowing users on the authorized network with a whitelisted IP address. As the company admin only wanted to allow authorized personnel to be whitelisted, their IP addresses were the only ones allowed to access the web application via the proxy link.
Suppose a user on a foreign network tries to access the same application via the proxy link. The IP address from where the request originated will be verified against the list of IP addresses whitelisted by the admin utilizing the services of the reverse proxy product. Since this IP is not whitelisted, the user will receive a 403 Forbidden error.