Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×Microsoft Entra is Microsoft’s cloud-based Identity and Access Management (IAM) service, which helps your employees sign in and access resources. miniOrange provides a solution where existing identities in Microsoft Entra Services can be leveraged for Single Sign-On (SSO) into different cloud and on-premise applications. Microsoft Entra supports standard authentication and authorization protocols such as LDAPS, SAML 2.0 and OAUTH 2.0.
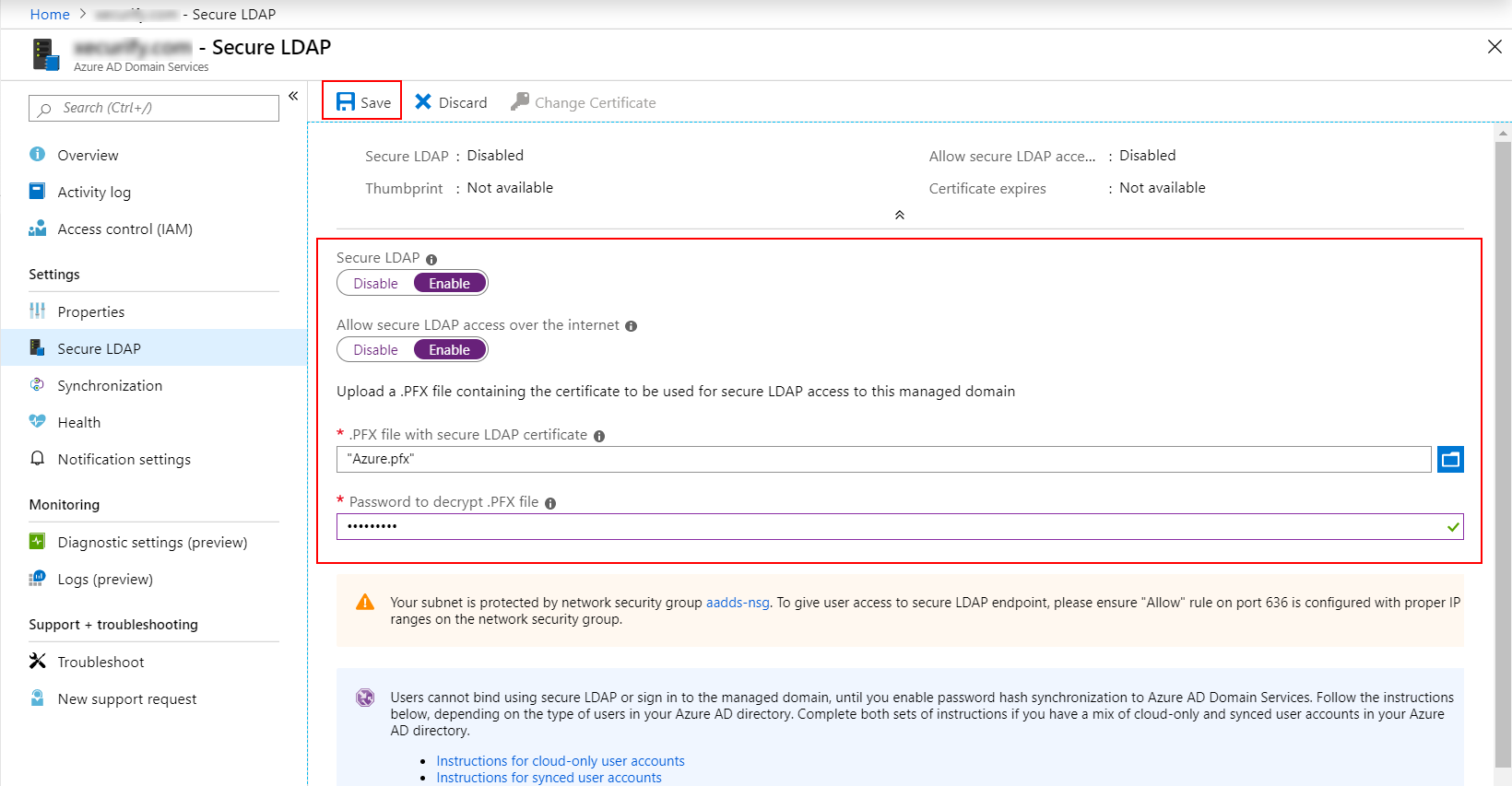
To interact with your Microsoft Entra Domain Services managed domain, the Lightweight Directory Access Protocol (LDAP) is mostly used. By default, the LDAP traffic isn't encoded, which is a security concern for many environments. With Microsoft Entra Domain Services, you can configure the managed domain to use secure Lightweight Directory Access Protocol (LDAPS). When you use secure LDAP, the traffic is encrypted. Secure LDAP is also known as LDAP over Secure Sockets Layer (SSL).

Employees in organization can log into a VPN that supports Radius (OpenVPN, Fortinet, Palo Alto, Pulse Secure etc) using their Microsoft Entra (AD) Credentials.
Two-factor Authentication (2FA) is used to log in into various application using your Active Directory (AD) Credentials as the first factor and OTP as a second factor on the Application Side.
Here Microsoft Entra acts as an Identity Provider to SSO into different Office 365 Applications where miniOrange IdP acts as a broker.
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, OpenLDAP, AWS etc), Identity Providers (like Microsoft Entra ID, Okta, AWS), and many more. You can configure your existing directory/user store or add users in miniOrange.
(Skip this if you have already configured a AADDS instance for a subscription)
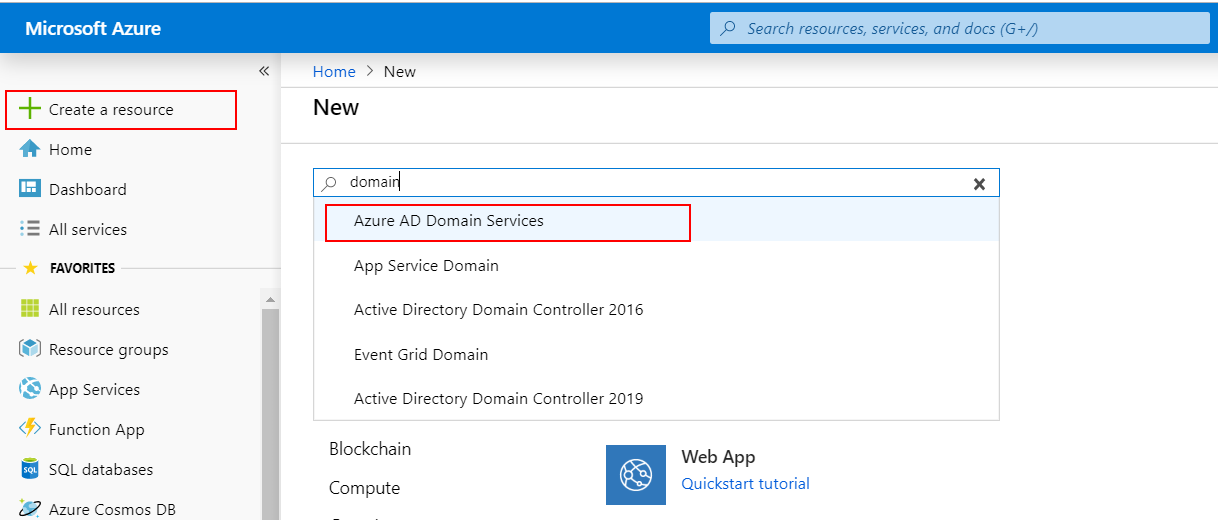
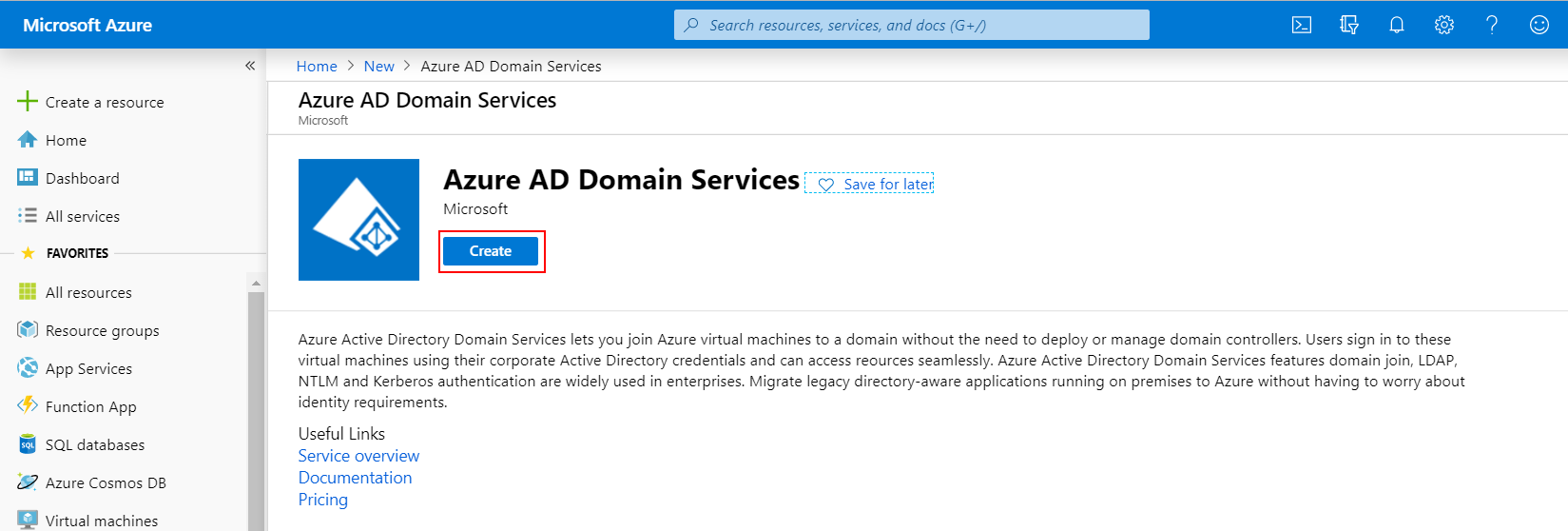
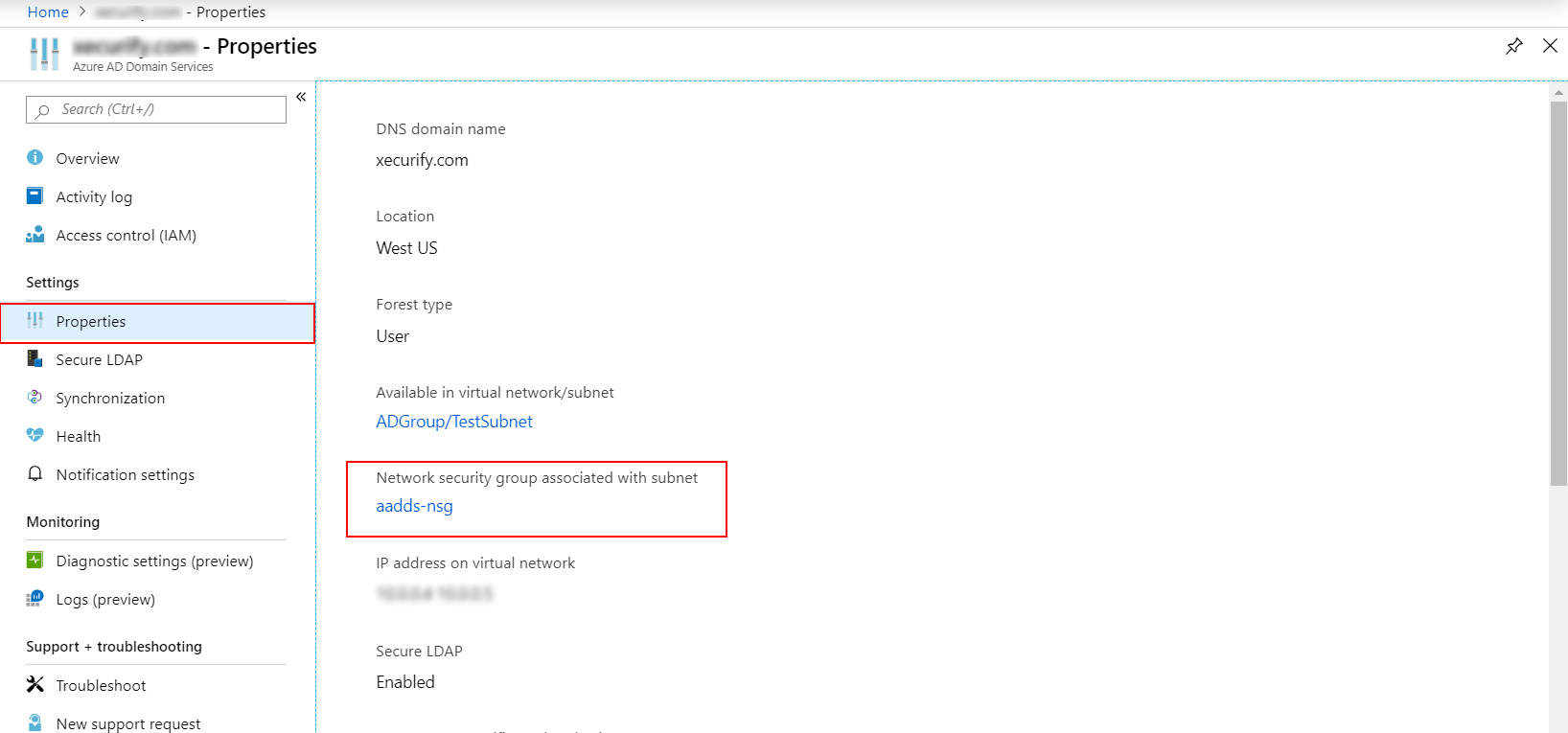
NOTE: During the provisioning process, Microsoft Entra DS creates two Enterprise Applications named Domain Controller Services and AzureActiveDirectoryDomainControllerServices in your directory. These Enterprise Applications are needed to service your managed domain. It's imperative that these applications are not deleted at any time.
# Define your own DNS name used by your Microsoft Entra DS managed domain
$dnsName="exampledomain.com"
# Get the current date to set a one-year expiration
$lifetime=Get-Date
# Create a self-signed certificate for use with Microsoft Entra DS
New-SelfSignedCertificate -Subject *.$dnsName `
-NotAfter $lifetime.AddDays(365) -KeyUsage DigitalSignature, KeyEncipherment `
-Type SSLServerAuthentication -DnsName *.$dnsName, $dnsName

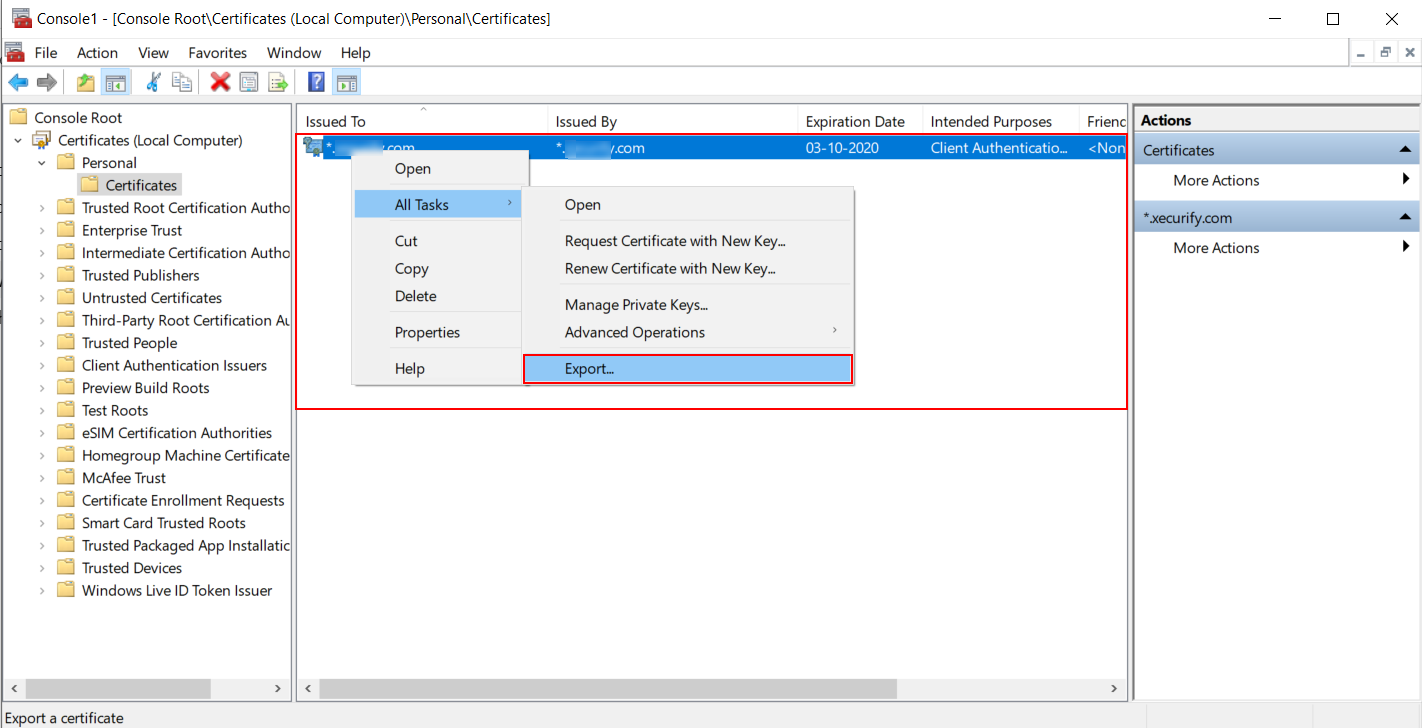
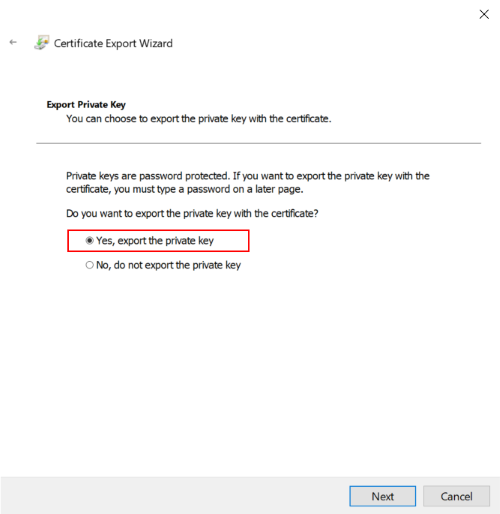
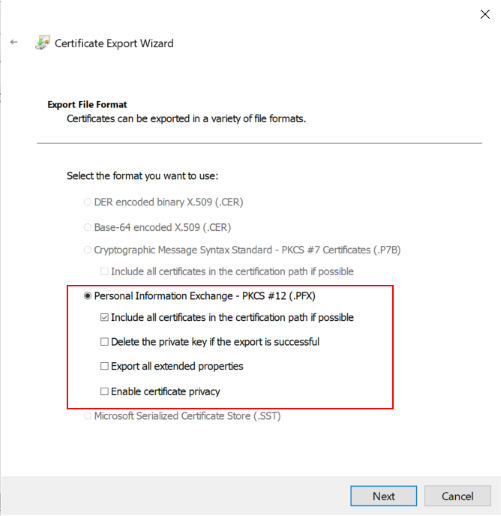
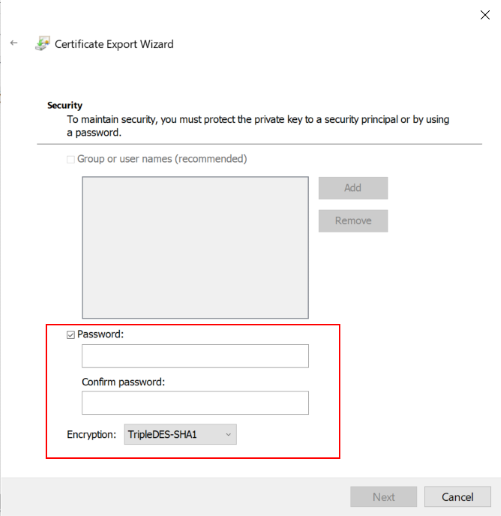
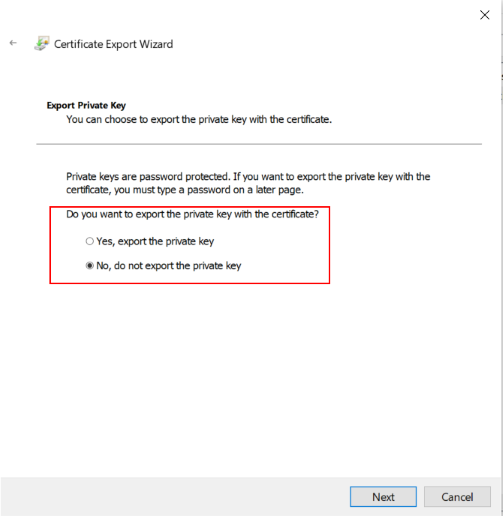
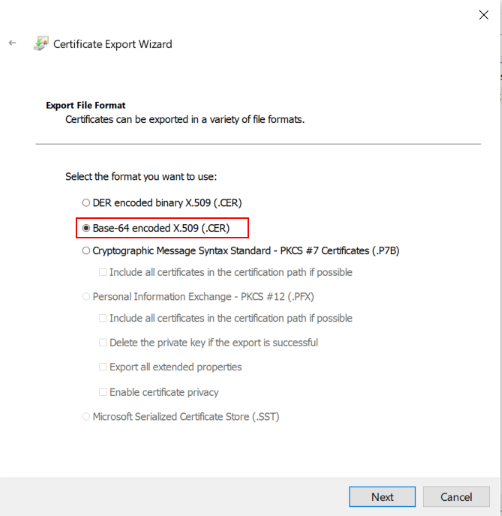
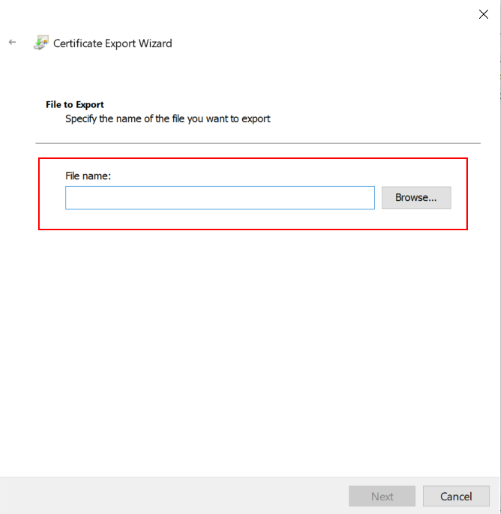
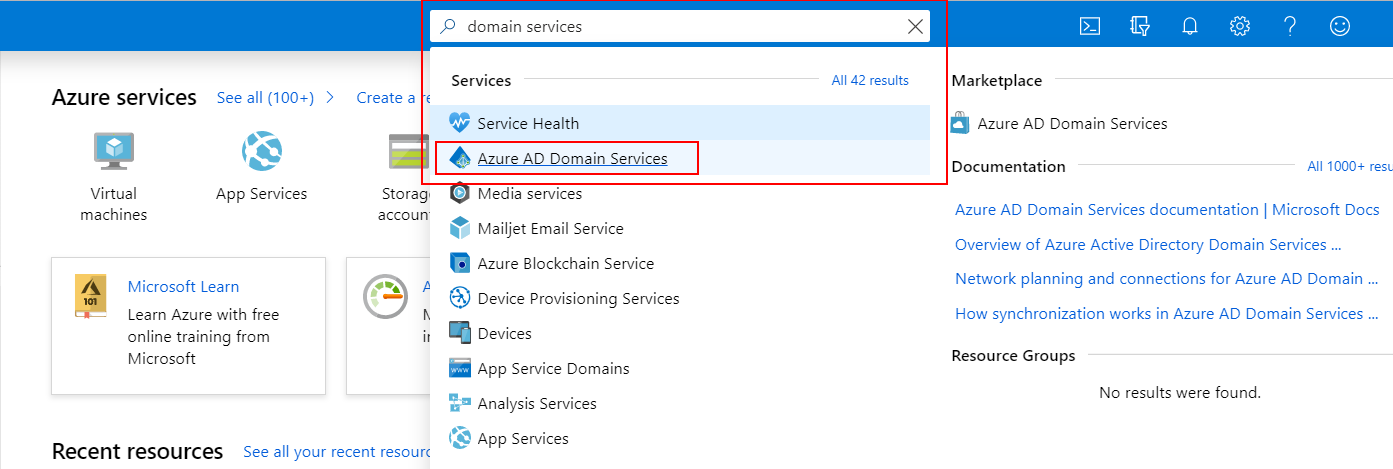
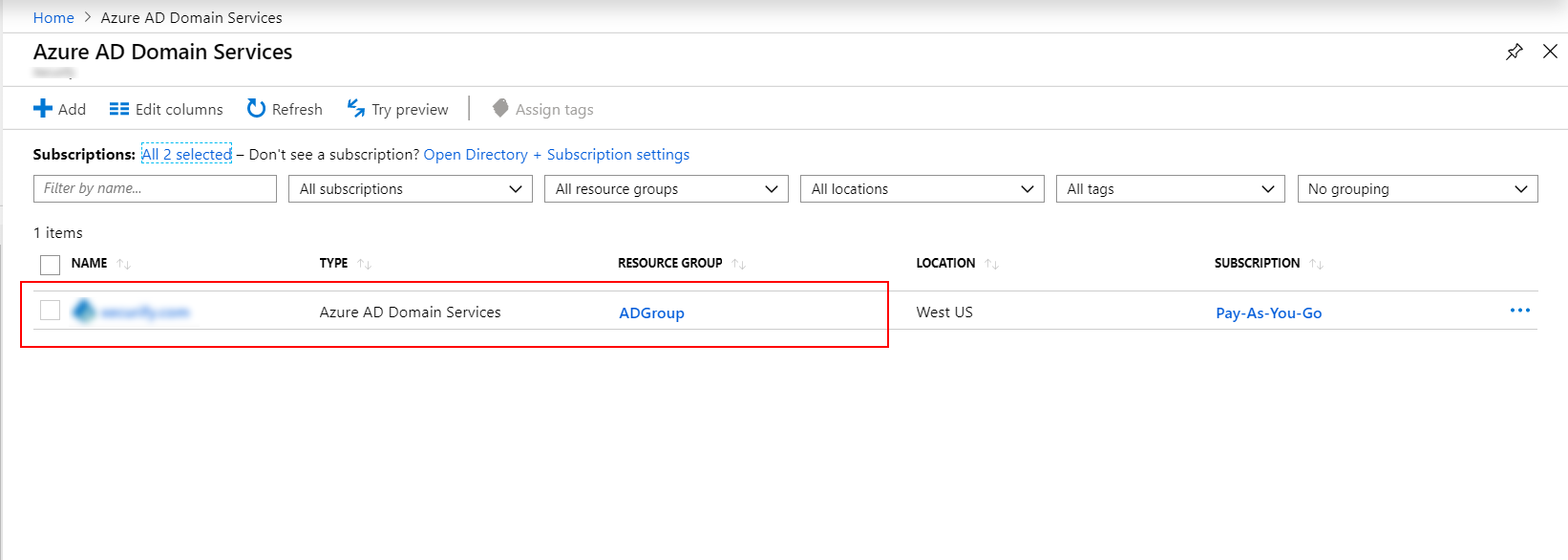
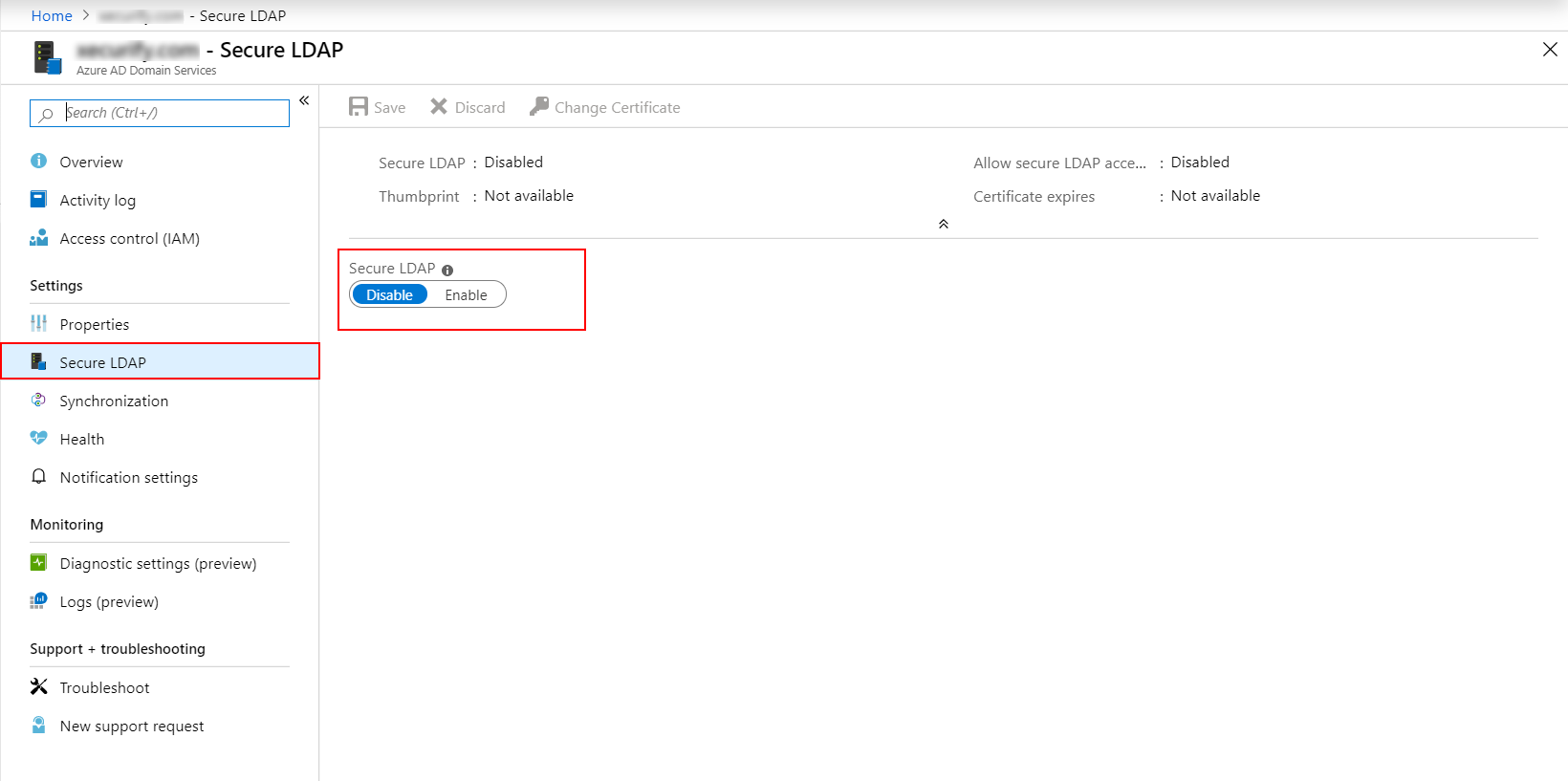
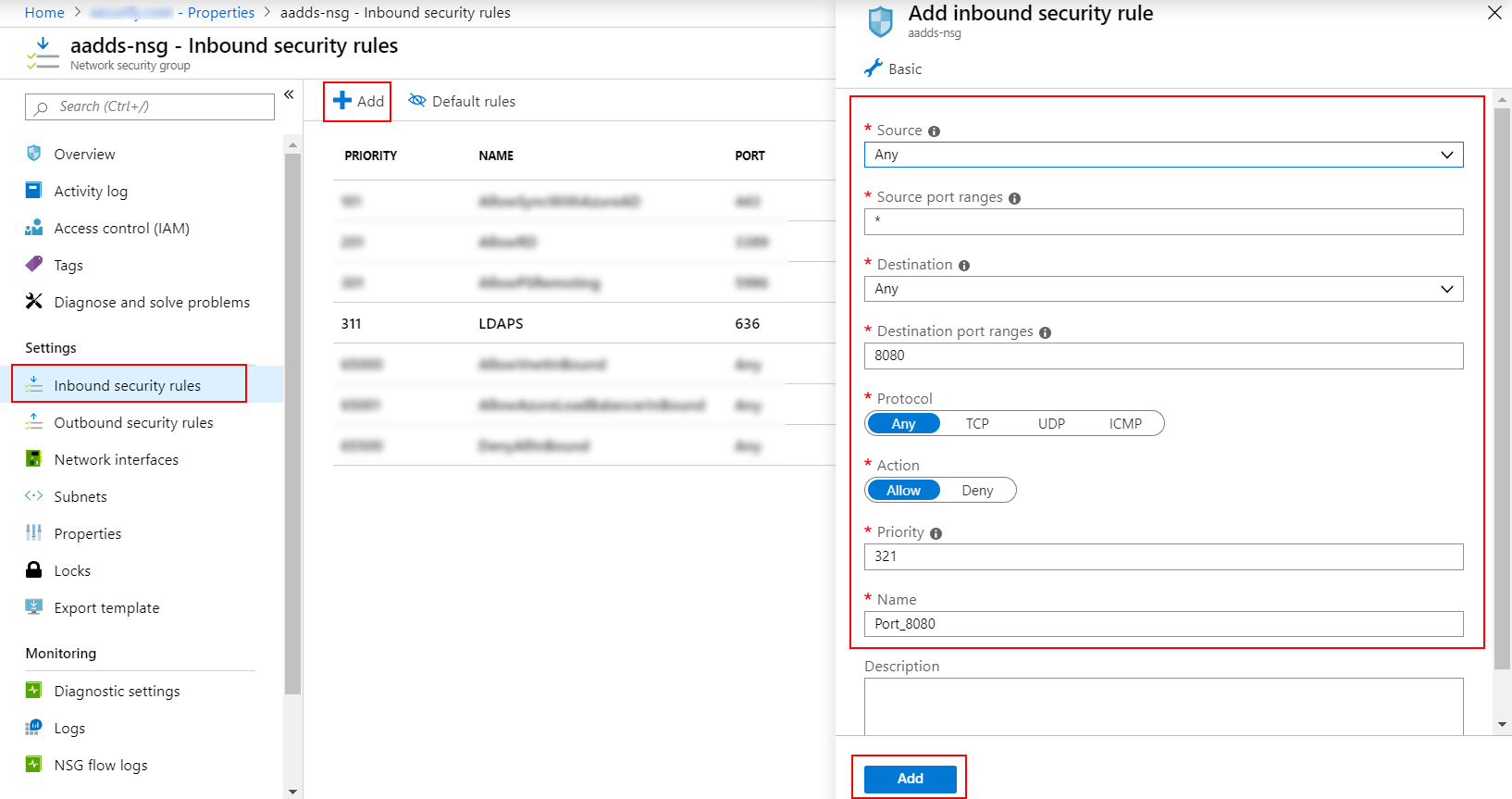
| Settings | Value |
|---|---|
| Source | Any |
| Source port ranges | * |
| Destination | Any |
| Destination port ranges | 636 |
| Protocol | TCP |
| Action | Allow |
| Priority | 401 |
| Name | AllowLDAPS |
| Settings | Value |
|---|---|
| Source | IP Addresses |
| Source IP addresses / CIDR ranges | Valid IP address or range for your environment. |
| Source port ranges | * |
| Destination | Any |
| Destination port ranges | 636 |
| Protocol | TCP |
| Action | Allow |
| Priority | 401 |
| Name | AllowLDAPS |
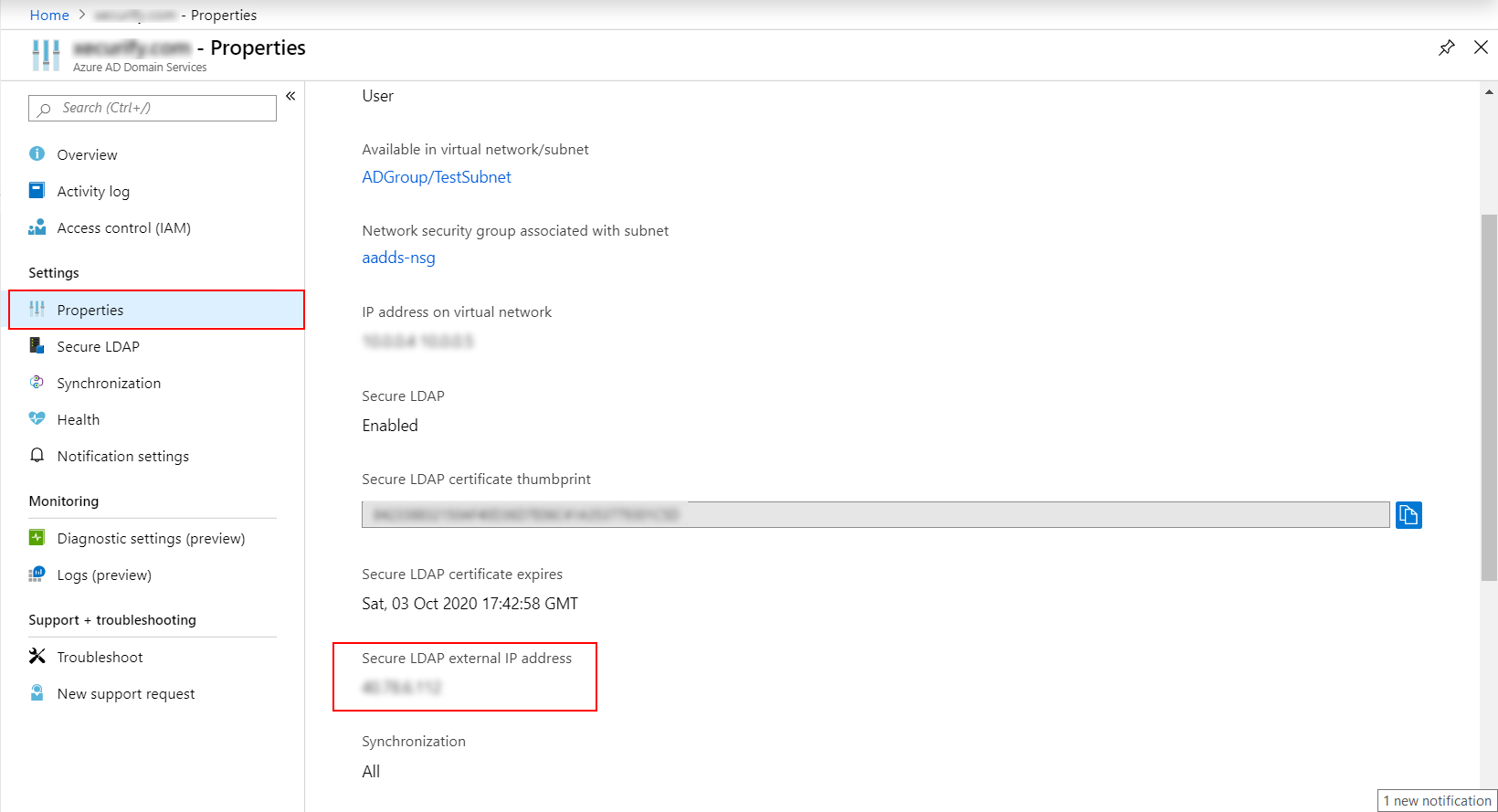
<Secure LDAP external IP address>ldaps.<domainname>
Replace <Secure LDAP external IP address> with the IP we get from azure portal and replace
&l;tdomainname> with the domain name for which the certificate was created.(Value used in $dnsName)
Eg: 99.129.99.939 ldaps.exampledomain.com
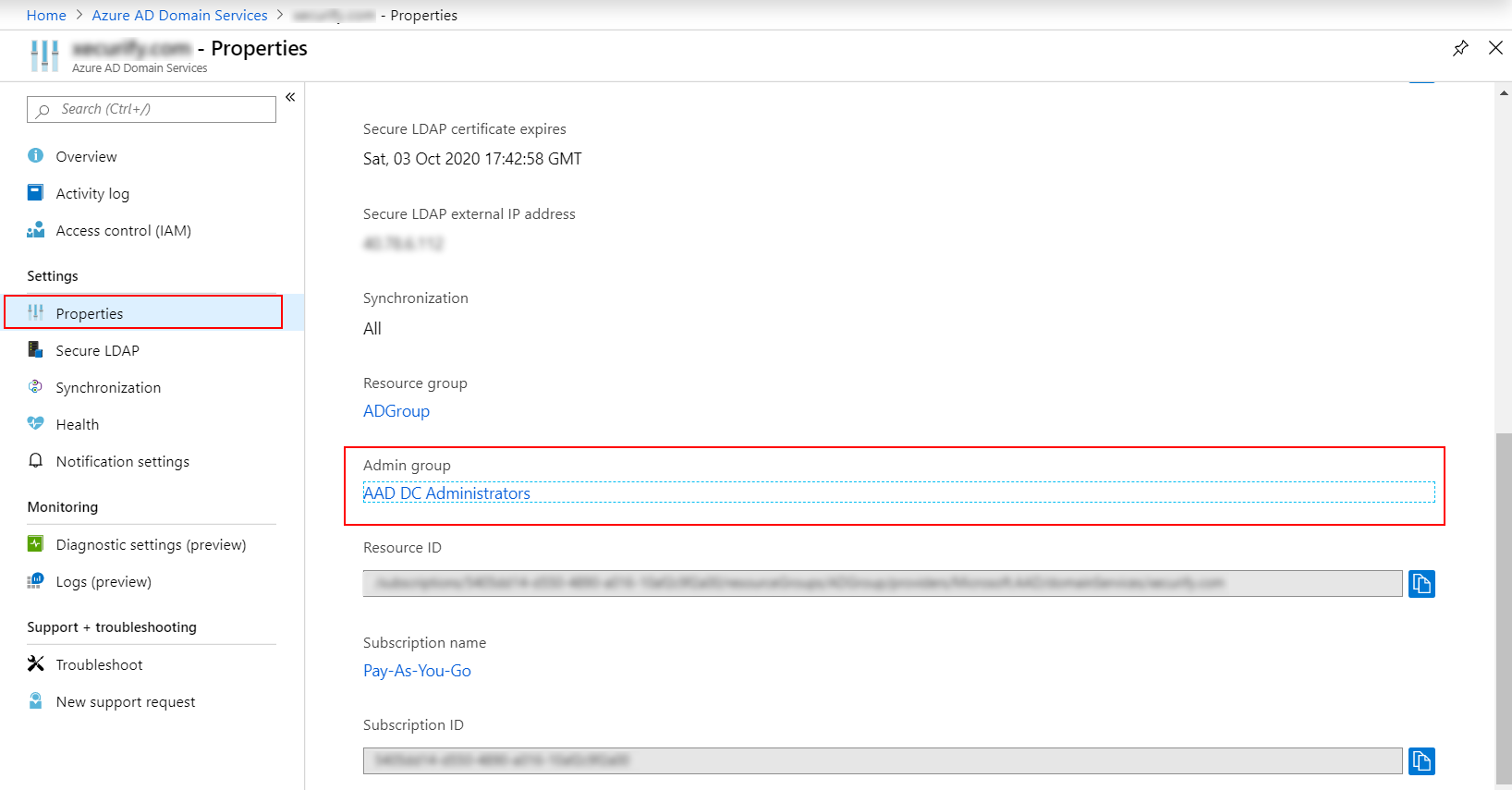
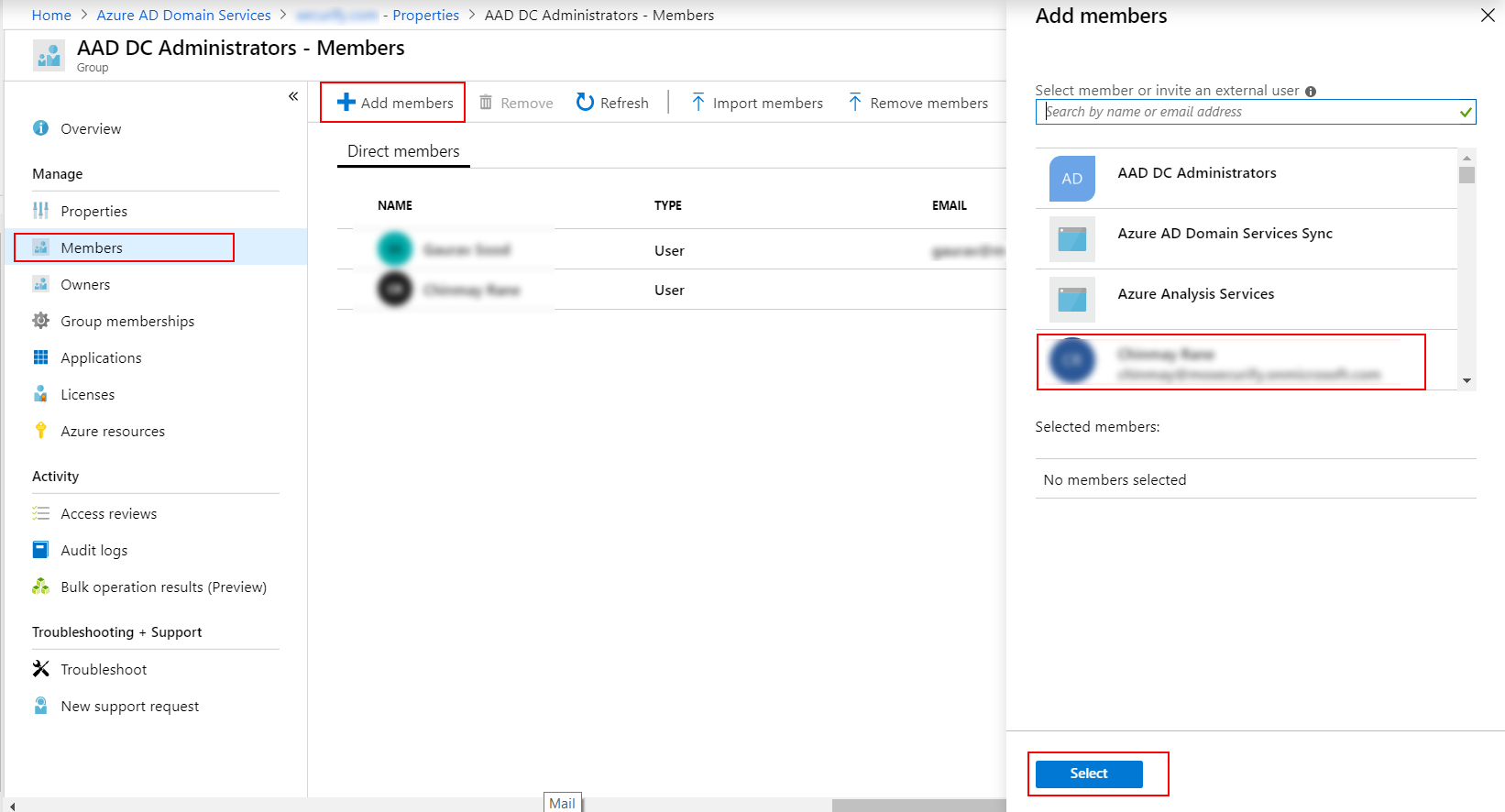

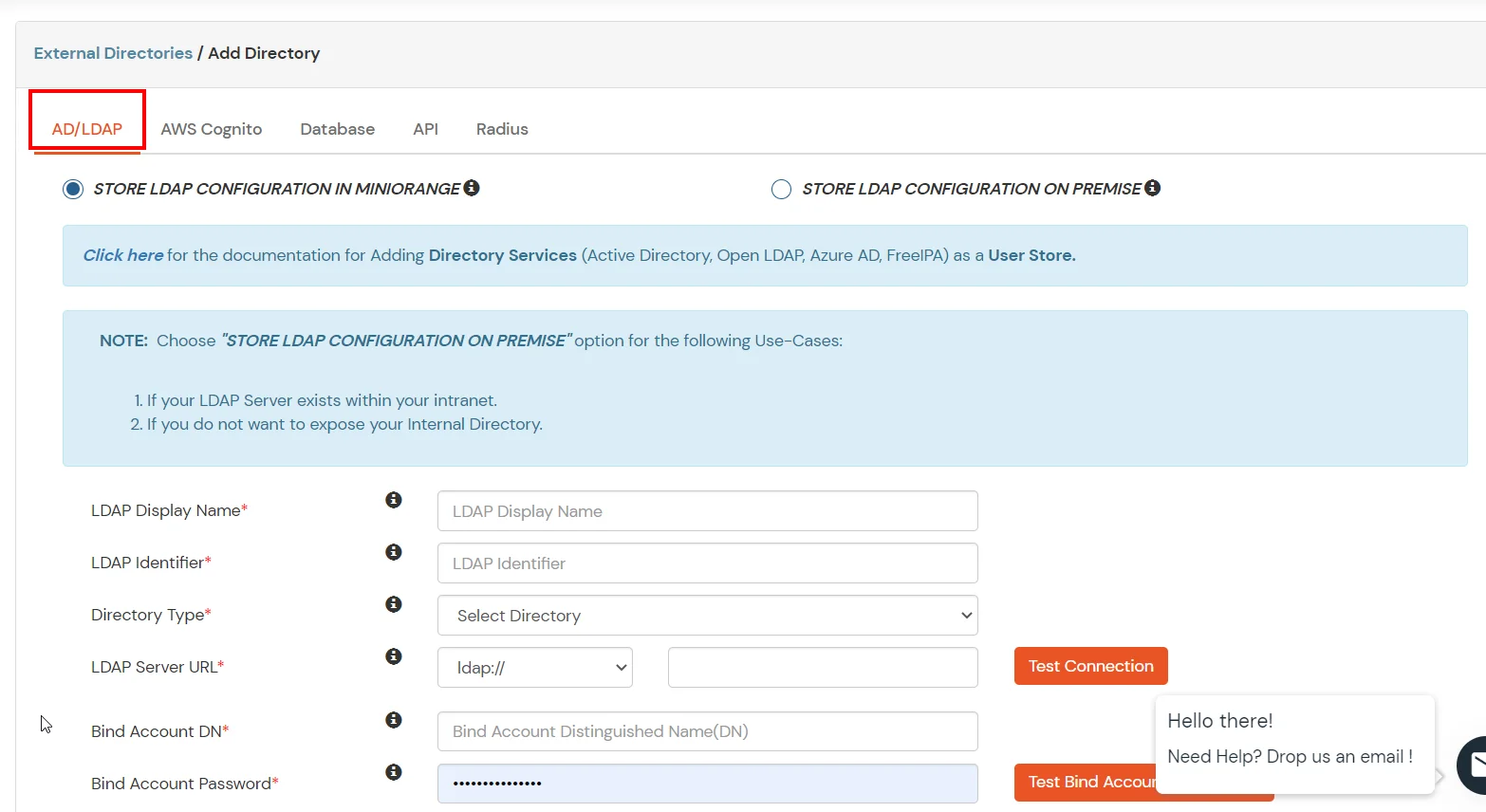
| Field | Value |
|---|---|
| LDAP display name | Any string that displays on this entry |
| LDAP Identifier | Unique identifier that identifies this specific entry |
| Directory Type | Active Directory |
| LDAP Server URL | Select ldaps:// as the pre filler followed by the domain entry added in the host file during configure DNS for external access. Eg: ldaps://ldaps.exampledomain.com |
| Bind Account DN | UserPrincipalName of the account eligible for binding operation. |
| Bind Account Password | Password for the account used for binding |
| Search Base | Provide distinguished name of the Search Base object Eg:cn=User,dc=domain,dc=com |
| Search Filter | Search filters enable you to define search criteria and provide a more efficient and effective searches. Eg: "(&(objectClass=*)(cn=?))" |
| Domain Name | Semi-colon separated list of domain. Eg: miniorange.in |
| LDAP Attribute List | Semi-colon separated list of attributes. Eg: cn;mail;givenName |
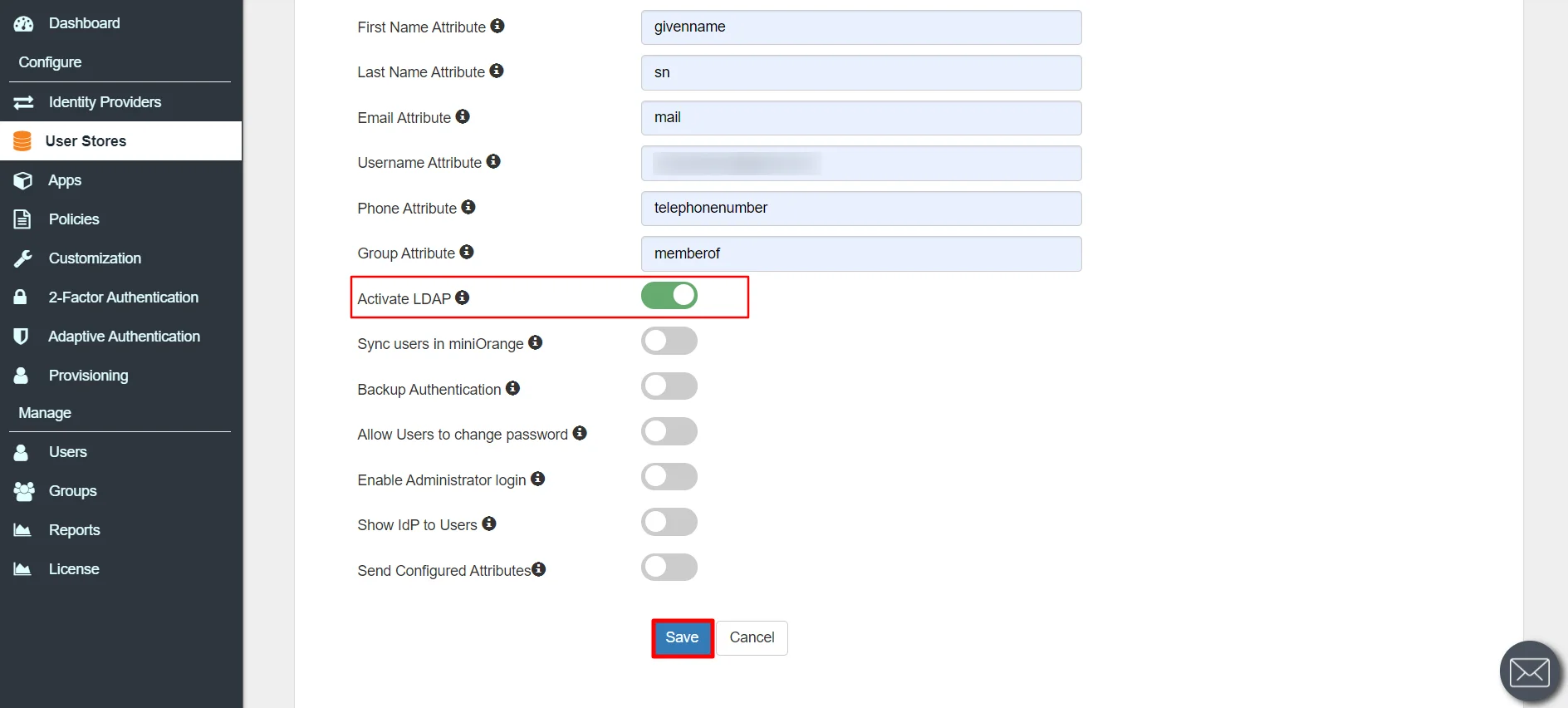
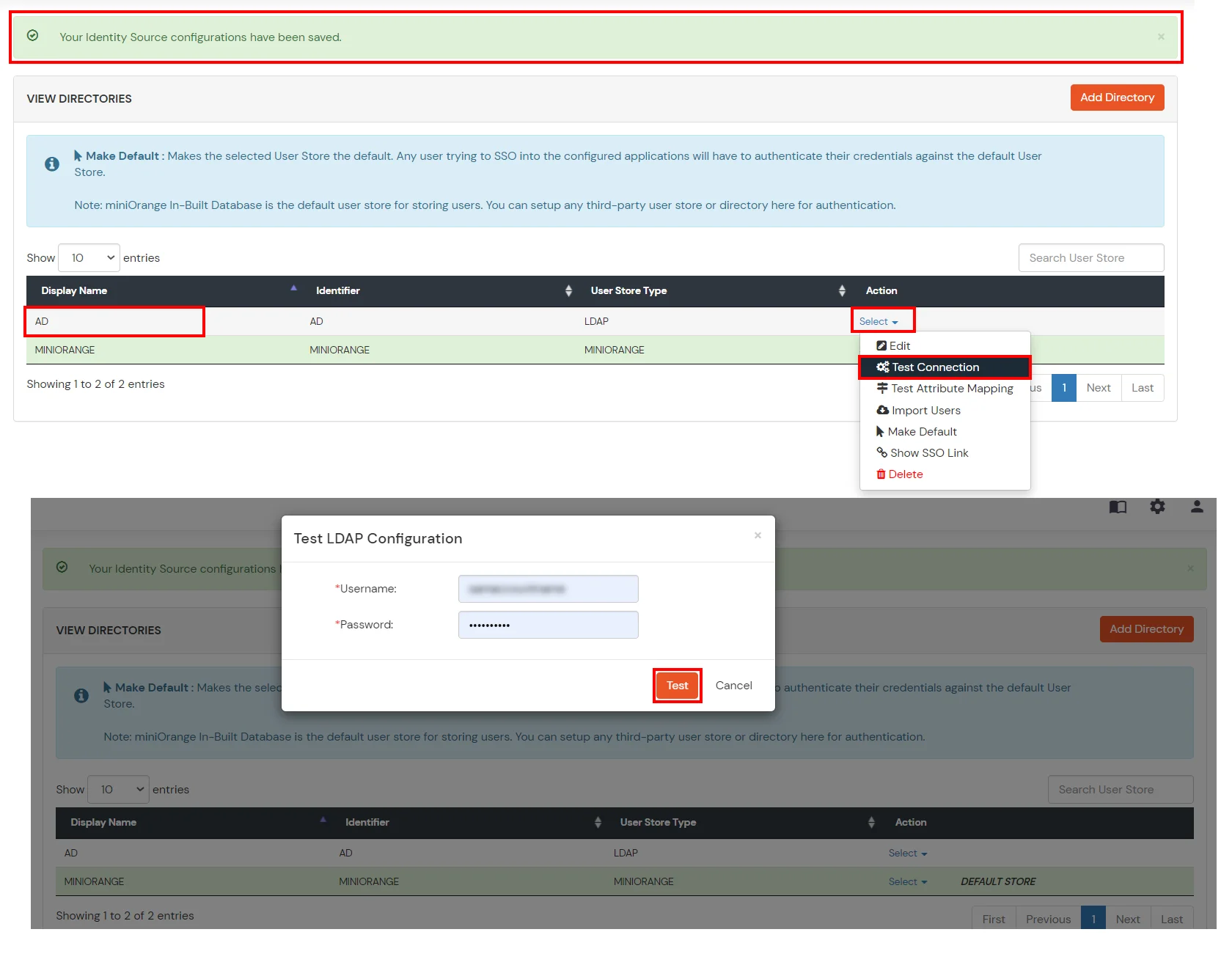
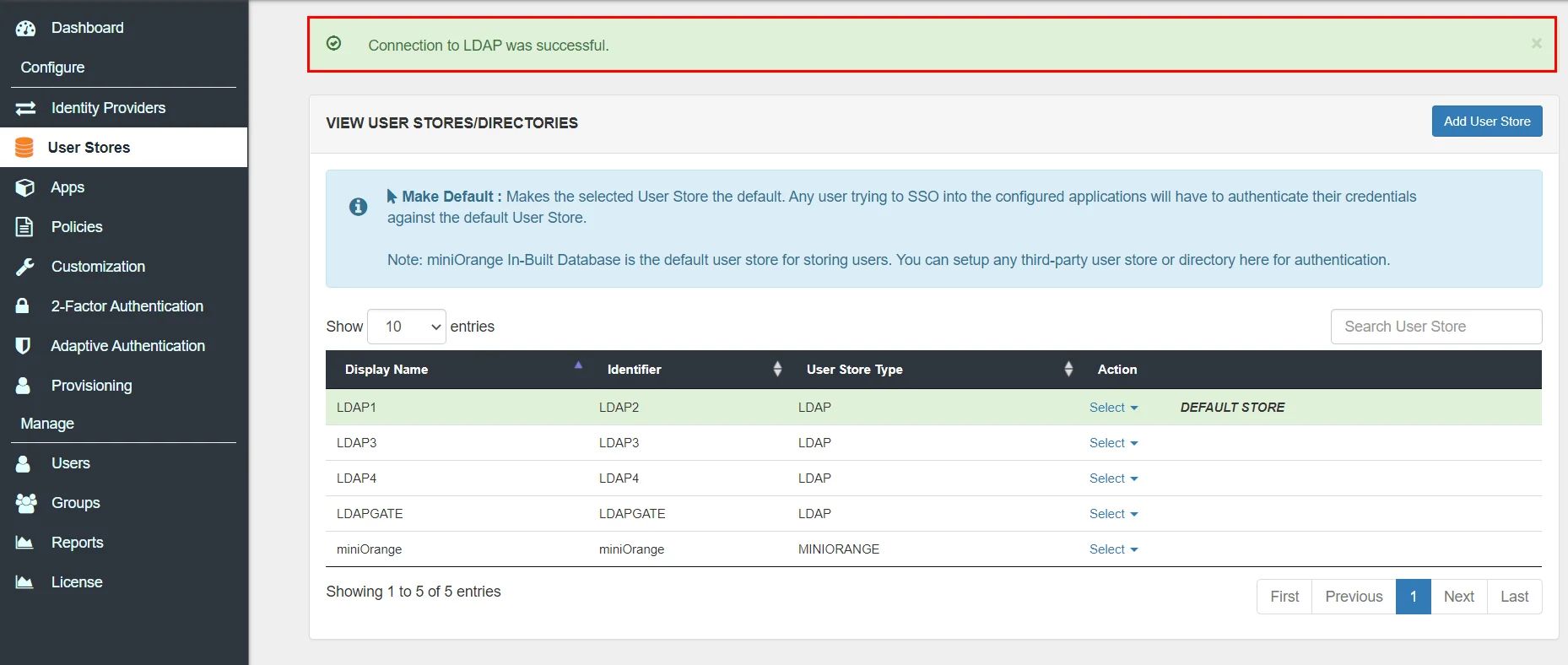
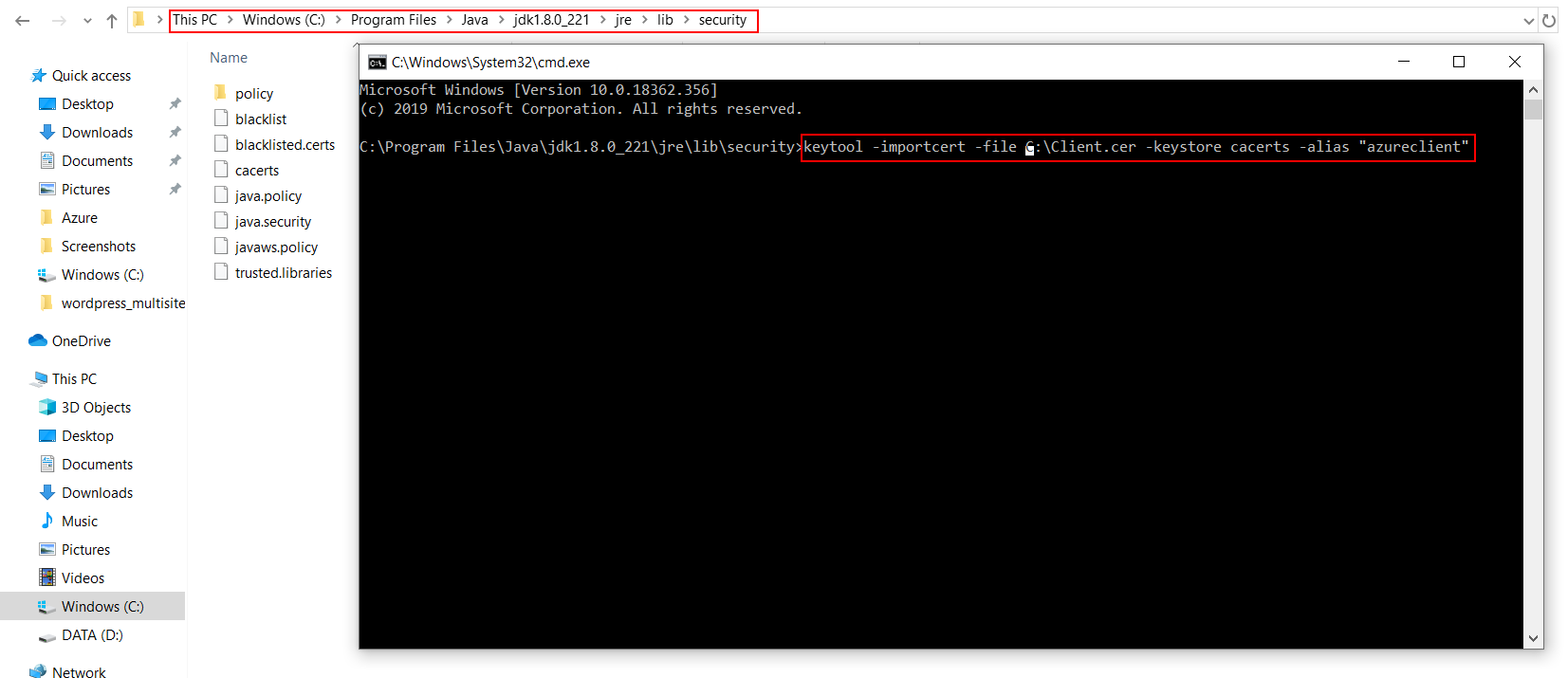
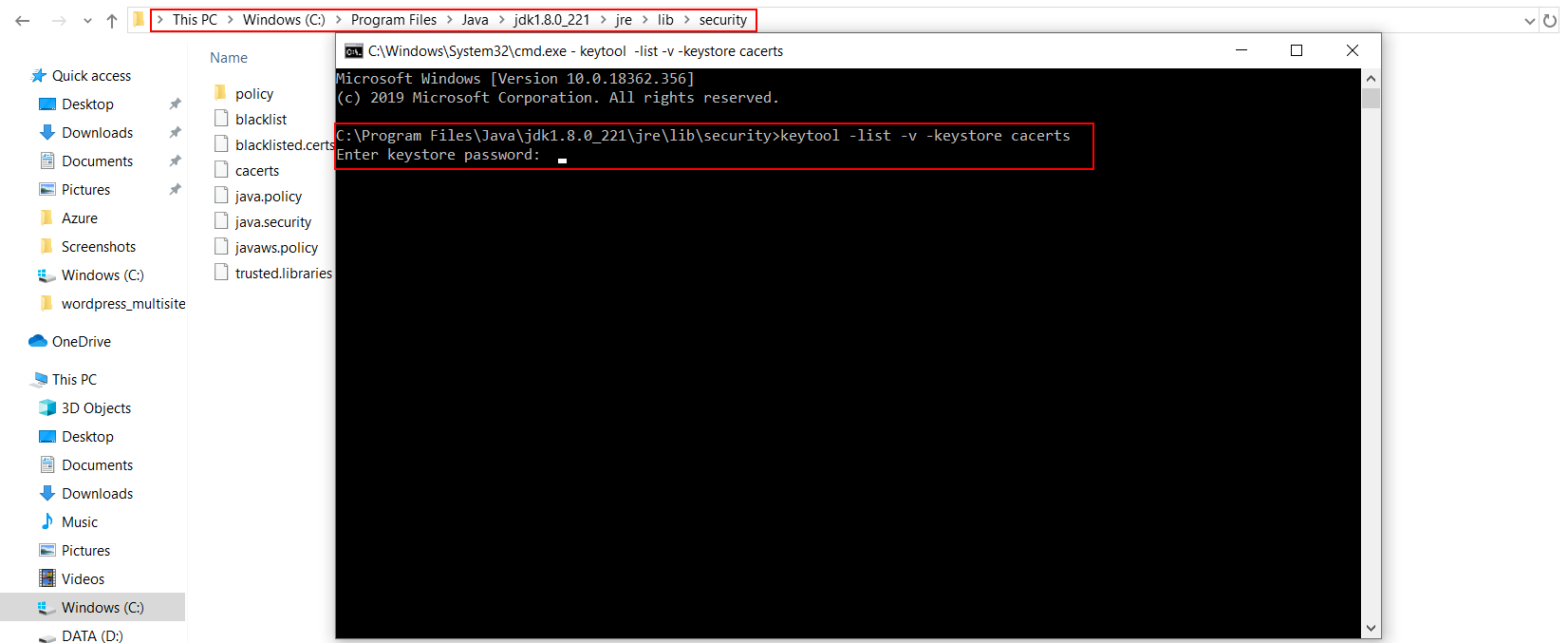
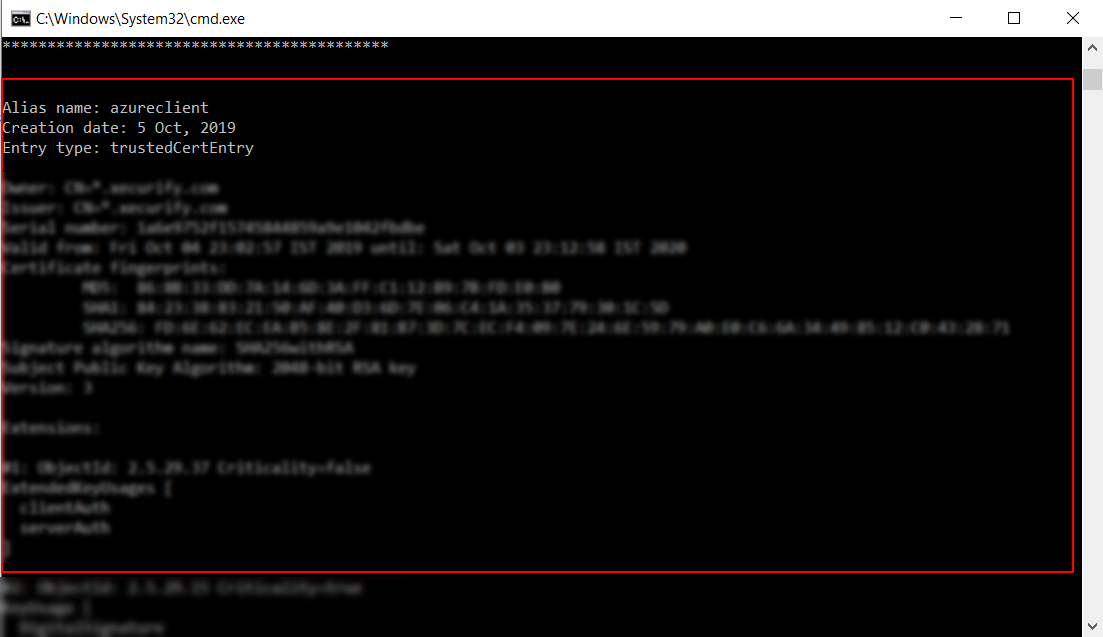
Install keytool for windows.(Its installed with java and is present in $JAVA_HOME\bin directory. To use it elsewhere add this directory to PATH variable.)

Our Other Identity & Access Management Products